A Practical Guide for Container Security: Trends and Strategies for 2023
Explore container security's fundamental principles and strategies, learn 2 specific methods, and examine tools and techniques for securing keys, tokens, and passwords.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2023 Containers Trend Report.
For more:
Read the Report
As containerized architecture gains momentum, businesses are realizing the growing significance of container security. While containers undeniably offer profound benefits, such as portability, flexibility, and scalability, they also introduce unprecedented security challenges. In this report, we will address the fundamental principles and strategies of container security and delve into two specific methods — secrets management and patching. Additionally, we will examine tools and techniques for securing keys, tokens, and passwords.
Current Trends in Container Security
Developers and DevOps teams have embraced the use of containers for application deployment. In a report, Gartner stated, "By 2025, over 85% of organizations worldwide will be running containerized applications in production, a significant increase from less than 35% in 2019." On the flip side, various statistics indicate that the popularity of containers has also made them a target for cybercriminals who have been successful in exploiting them.
According to a survey released in a 2023 State of Kubernetes security report by Red Hat, 67% of respondents stated that security was their primary concern when adopting containerization. Additionally, 37% reported that they had suffered revenue or customer loss due to a container or Kubernetes security incident. These data points emphasize the significance of container security, making it a critical and pressing topic for discussion among organizations that are currently using or planning to adopt containerized applications.
Strategies for Container Security
Container security can be most effectively handled using a comprehensive multi-level approach, each involving different strategies and principles. Employing this approach minimizes the risk of exposure and safeguards the application against threats.
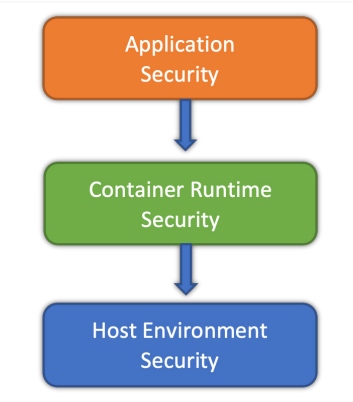
Figure 1: Multi-layer approach to container security
Application security focuses on securing the application that is executed within the container, which can be achieved by implementing input validation, secure coding practices, and encryption. In contrast, the container runtime environment should undergo regular vulnerability scans and patching. Finally, the host layer is considered the most critical security layer because it is responsible for running the containers. It can be secured by implementing baseline configurations to harden the host operating system, deploying firewalls, implementing network segmentation, and using intrusion detection and intrusion prevention systems.
Each layer of the container infrastructure provides an opportunity to apply a set of overarching principles and strategies for security. Below, we've outlined some key strategies to help provide a better understanding of how these principles can be put into action.
|
SECURING CONTAINERIZED ENVIRONMENTS
|
|
|---|---|
| Core Principles and Strategies | Description |
| Secure by design | Least privilege, separation of duty, defense in depth |
| Risk assessment | Vulnerability scanning and remediation, threat modeling, security policy |
| Access management | RBAC, MFA, centralized identity management |
| Runtime security | Network segmentation, container isolation, intrusion detection and prevention |
| Incident management and response | Log management, incident planning and response, continuous monitoring |
Container Segmentation
To secure communication within a container segment, containers can be deployed as microservices, ensuring that only authorized connections are allowed. This is achieved using cloud-native container firewalls, container zones, service mesh technologies, etc., that control the traffic to the virtual network using granular policies. While network segmentation divides the physical network into sub-networks, container segmentation works on an overlay network to provide additional controls for resource-based identity.
Image Scanning
Before deploying containers, it is important to analyze the container base images, libraries, and packages for any vulnerabilities. This can be accomplished by utilizing image scanning tools, such as Anchore and Docker Scout.
Runtime Protection
To identify and respond to potential security incidents in real time, it is crucial to monitor activities within the container. Runtime security tools can assist in this task by identifying unauthorized access, malware, and anomalous behavior.
Access Control
To minimize the possibility of unauthorized access to the host machine, only authorized personnel should be granted access to the containerized environment. Strong authentication and authorization mechanisms, such as multifactor authentication, role-based access control (RBAC), and OAuth, could be deployed for this purpose.
Secrets Management in Container Security
Secrets management protects against both external and internal threats and simplifies credential management by centralizing it. It attempts to protect sensitive information (keys, tokens, etc.) that controls access to various services, container resources, and databases. Ultimately, it ensures that sensitive data is kept secure and meets regulatory compliance requirements.
Due to the importance of secrets, they should always be encrypted and stored securely. Mishandling of this information can lead to data leakage, breach of intellectual property, and losing customer trust. Common missteps include secrets being stored in plain text, hardcoding them, or committing them to source control system/repository.
Overview of Common Types of Secrets
To ensure the security of secrets, it's crucial to have a clear understanding of the various types:
- Passwords are the most commonly used secret. They are used to authenticate users and provide access to web services, databases, and other resources in the container.
- Keys serve multiple purposes, such as encrypting and decrypting data and providing authentication for devices and services. Common key types include SSH keys, API keys, and encryption keys.
- Tokens are used to provide temporary access to resources or services. Authentication tokens, such as access tokens, OAuth, and refresh tokens, are used to authenticate third-party services or APIs.
- Database credentials could be usernames, passwords, and connection strings that are used to access the database and database-specific secrets.
Overview of Popular Secrets Management Tools
When evaluating a security solution, it's important to consider a range of factors, such as encryption, access control, integration capabilities, automation, monitoring, logging, and scalability. These are all desirable traits that can contribute to a robust and effective security posture. Conversely, pitfalls such as lack of transparency, limited functionality, poor integration, and cost should also be considered.
In addition to the above-listed capabilities, a comprehensive evaluation of a security solution also takes into account the specific needs and requirements of a company's current infrastructure (AWS, Azure, Google Cloud, etc.) and compatibility with its existing tools to ensure the best possible outcome.
Below is the list of some proven tools in the industry for your reference:
- HashiCorp Vault – An open-source tool that provides features like centralized secrets management, secrets rotation, and dynamic secrets.
- Kubernetes Secrets – A built-in secrets management tool within the Kubernetes environment that allow users to store sensitive information such as Kubernetes objects. It is advised to use encryption, RBAC rules, and other security best practices for configuration when using Kubernetes Secrets.
- AWS Secrets Manager – A cloud-based tool that is both scalable and highly available. It supports containers running on Amazon ECS and EKS, provides automatic secret rotation, and can integrate with AWS services, like Lambda.
- Azure Key Vault – Usually used by containers running on Azure Kubernetes Service. It can support various key types and integrates with most Azure services.
- Docker Secrets – A built-in secrets management tool that can store and manage secrets within Docker Swarm. Note that this tool is only available for Swarm services and not for standalone containers.
Short-Lived Secrets
An emerging trend in the field of secrets management is the use of short-lived secrets that have a limited lifespan, are automatically rotated at regular intervals, and are generated on demand. This is a response to the risk associated with longlived, unencrypted secrets, as these new secrets typically only last for a matter of minutes or hours and are automatically deleted once they expire.
Patching in Container Security
To reduce exposure risk from known threats, it is important to ensure that containers are using the latest software versions. Patching ensures that the software is regularly updated to address any open vulnerabilities. If patching is not applied, malicious actors can exploit vulnerabilities and cause malware infections and data breaches. Mature organizations use automated patching tools to keep their container environments up to date.
Patching Tools
To keep container images up to date with the latest security patches, there are many tools available in the market. Kubernetes and Swarm are the most widely used orchestration tools that provide a centralized platform and allow users to automate container deployment. Ansible and Puppet are other popular automation tools used for automated deployment of patches for Docker images.
Best Practices for Implementing Patching
Applying patches in a container environment can significantly enhance the security posture of an organization, provided they follow industry best practices:
- Scan containers on a periodic basis to identify vulnerabilities and keep the base images up to date.
- Use an automatic patching process with automated tools as much as possible to reduce manual intervention.
- Use official images and test patches in a testing environment before deploying into production.
- Track the patching activity, monitor logs, and act on alerts or issues generated.
- Create automated build pipelines for testing and deploying containers that are patched.
Conclusion
As more organizations adopt containerized environments, it's vital to understand the potential security risks and take a proactive approach to container security. This involves implementing core security principles and strategies, using available tools, and prioritizing the security of containerized data and applications. Strategies like multi-layered security, secrets management, and automated patching can help prevent security breaches.
Additionally, integrating patching processes with CI/CD pipelines can improve efficiency. It's important for organizations to stay up to date with the latest container security trends and solutions to effectively protect their containerized environments.
This is an article from DZone's 2023 Containers Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments