Container Security: Don't Let Your Guard Down
To comprehend the security implications of a containerized environment, it is crucial to understand the fundamental elements of a container deployment network.
Join the DZone community and get the full member experience.
Join For FreeDevelopers and DevOps teams have embraced the use of containers for application development and deployment. They offer a lightweight and scalable solution to package software applications. The popularity of containerization is due to its apparent benefits, but it has also created a new attack surface for cybercriminals, which must be protected against.
Industry-leading statistics demonstrate the wide adoption of this technology. For example, a 2020 study from Forrester mentioned, "container security spending is set to reach $1.3 billion by 2024". In another report, Gartner stated, "by 2025, over 85% of organizations worldwide will be running containerized applications in production, a significant increase from less than 35% in 2019".
On the flip side, various statistics indicate that the popularity of containers has also made them a target for cybercriminals who have been successful in exploiting them. In the 2019 report, Aqua Security published that 94% of US organizations use containers for production applications, up from 68% in 2018. The same survey reported that 65% of organizations had experienced at least one container-related security incident, a steep increase from 60% in the previous year. A more recent study conducted by StackRox in 2021 found that 94% of surveyed organizations had experienced a security incident in their container environment in the past 12 months. Finally, in a survey by Red Hat, 60% of respondents cited security as the top concern when adopting containerization.
These data points emphasize the significance of container security, making it a critical and pressing topic for discussion among organizations that are currently using or planning to adopt containerized applications. To comprehend the security implications of a containerized environment, it is crucial to understand the fundamental elements of a container deployment network.
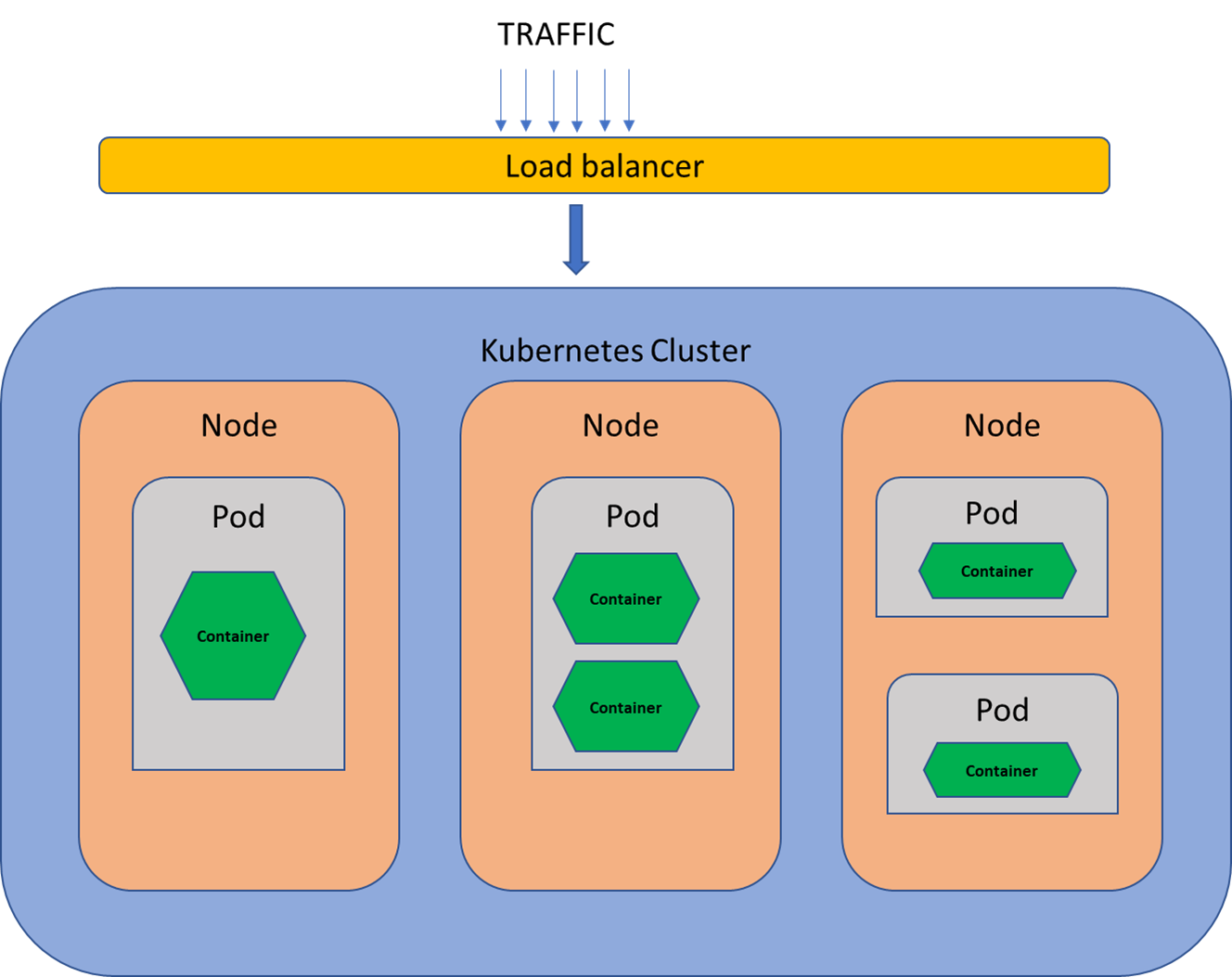
The above illustration outlines a standard container deployment using Kubernetes. However, before designing a strong security framework for this system, it is crucial to understand its basic components and how they interact with each other.
- Load Balancers are the entry point for the ingress traffic. They help in distributing incoming traffic to nodes that reside within a cluster. In general, their purpose is to maintain a balanced flow of requests inside the container environment.
- Kubernetes Cluster consists of a master node that manages the cluster, multiple worker nodes that run containerized applications, and a Kubernetes control plane that is utilized to manage all nodes. The cluster's primary job is managing, scaling, and orchestrating the containerized environment.
- Nodes are physical or virtual machines that use 'container runtime' to manage the containers. The nodes work in close coordination with the control plane using Kubelet (agent used to schedule and manage pods using the control plane), Kube Proxy (network proxy used to route traffic to the right pod), and cAdvisor (container monitoring tool used to send performance metrics from containers to control plane).
- Pods contain one or more containers within it. They are the smallest deployment units in Kubernetes that run on worker nodes.
- Container is an executable software package that provides everything to run an application or a service. It contains code, libraries, system tools, and settings. The system is built using container images, which are read-only templates that are utilized to run applications. They are isolated from other containers and also from the host operating system.
High-level container environment traffic flow:
- Load Balancer receives the ingress traffic and distributes it across various nodes.
- Based on the service or requested application, the cluster directs the traffic to the appropriate container.
- Once the container processes the request and generates a response, it is sent back to the requesting entity through the same route.
- For the egress traffic, the container sends information to the cluster and directs it to the load balancer.
- The balancer then transmits the request to the required entity.
Containers do provide some built-in security controls. Each containerized environment is isolated, and traffic does not travel within the host network. This prevents lateral movement of data that aids in improving overall security. These environments can be further segregated using network segmentation to control traffic flow within the container environment. However, this architecture may also introduce many security risks if adequate measures are not taken during its implementation. We should comprehend, use, and comply with the technical and design security requirements to ensure the security of containers.
Host Security
The host is considered to be one of the most crucial components from a security perspective. Although containers are kept isolated from one another, they are built on top of a host operating system (OS). Hence, the host OS needs to be free from any vulnerabilities. This will reduce the likelihood of unauthorized access. Here are some measures to ensure a secure connection between the container and the host:
- Periodically scan the host OS for security vulnerabilities, if any, and patch the system regularly.
- Disable unused or unnecessary services, protocols, or functionality. Replace insecure protocols like telnet with widely popular products like SSH.
- Review access to the host OS annually (or more frequently, depending on the risk level of the applications running on it) and limit it to authorized personnel only.
- Enable MFA (multi-factor authentication) and RBAC (Role-based access control).
- Use container isolation technologies like namespaces and cgroups to ensure that containers are isolated from each other and the host.
- Install host-based firewalls and virtual private networks (VPNs) for container network security.
- Log container activity using monitoring tools like Auditd, Sysdig, Falco, and Prometheus. They will help you track anomalous user behavior, detect known threats and address them.
- Create backups for data recovery in case of failures. Also, perform business impact analysis (BIA) testing at regular intervals to measure the backups' effectiveness.
Image Hardening
Containers are built using software, configuration settings, and libraries. These are collectively referred to as container images and stored in the form of read-only templates. Since these images are the source of truth, it is important to harden them, i.e., keep them free from malware and other vulnerabilities. Below are some ways to do it:
- First, remove packages that are not used or are unnecessary.
- Use only secure images (that come from a trusted source) to build a new container. Finally, configure them using secure defaults.
- Implement access controls for container images; limit user access to containers and use secure credential storage for container authentication.
- The trusted repository used within the organization should only allow the storage of hardened images. One method to implement this measure is to ensure that any images being uploaded to the secure repository have been signed and verified beforehand. Tools like Docker Content Trust or Docker Notary can be used for the same.
- Use and implement secure container image management, distribution, caching, tagging, and layering.
- Use tools like Clair or Trivy to perform vulnerability scanning in the container environment.
Container Security Configuration
Another important component is the configuration of the container where the application is running. Here are some settings that can be configured to reduce exposure:
- Run the containers with the least privileged access for all system resources, including memory, CPU, and network.
- Use tools like SELinux and AppArmor for container runtime security. These can prevent unauthorized access and protect container resources.
- Manage secure deployment of containers using orchestration tools like Kubernetes and Docker Swarm.
Network Security
The network is a critical component for all systems. Therefore, it is important to restrict network access and ensure that data at rest and in transit is always encrypted. A few specific network security requirements for containers are:
- Limit the attack surface by implementing network segmentation for container clusters.
- To limit access to a containerized application, it is recommended to employ a container firewall and HIDS on the container host while also setting resource limits for the container.
- Periodically scan the containers for vulnerabilities and conduct security testing.
- Monitor container network traffic and enable secure container logging. Generate alerts if any suspicious activity is detected.
- Use tools like Calico and Weave Net for securing network environments.
Container and Network Security Policy and Protocols
Policies are guidelines and rules for securing containerized applications and their associated networks. The policy may include protocols for deploying, monitoring, and managing containers to ensure that they operate securely and do not pose a threat to the host system or network.
- Store container images using the secure registry.
- Implement container backups and encrypt sensitive data to protect against loss of data.
- Implement a secure container by using only trusted certificates for container communication.
- Enable secure boot for containers and secure DNS resolution.
- Implement secure container network drivers, entry points, networking policies, network plugins, bridges, overlay networks, DNS configuration, and network load balancer.
- Implement secure container network virtual switches, routing policies, firewalls, routing protocols, security groups, access control lists, load balancing algorithms, service recovery, and service mesh.
- Use container configuration management and orchestration tools to enforce these policies.
Application and Platform Security
Container application uses several application programming interfaces (APIs) for connecting and gathering information from various systems. There are some basic container application security requirements that should be tested and validated in a timely fashion:
- Third-party libraries used in coding should be secure and free from vulnerabilities.
- Developers should be trained to implement only secure coding practices and secure container development practices.
- Use container orchestration tools alongside implementing secure application deployment and management processes.
- Implement container host and image - hardening, scanning, signing, verification, and management.
Compliance With Security and Regulatory Standards
Containers host multiple applications; hence, they must comply with regulatory requirements and security standards like PCIDSS and HIPAA. Some common requirements for container security to meet various compliance standards:
- Conduct periodic security risk assessments of the applications and the container environment.
- Set up incident response and change management procedures for container security.
- Implement backup and restore procedures along with disaster recovery plans.
- Organizations should have secure container lifecycle management policies and procedures. In addition, regular audits should be conducted to test their effectiveness.
- Mandate user training to create awareness about secure container practices.
- Utilize resources such as Open Policy Agent and Kyverno to verify compliance with relevant regulations and recommended security protocols.
It is crucial for organizations to implement security measures to mitigate potential risks posed by security breaches in containerization. This involves ensuring that both applications and container environments are thoroughly checked for vulnerabilities. In addition to that, adopting technical measures such as restricting access, implementing access controls, conducting regular risk assessments, and continuously monitoring container environments have proved very effective in minimizing potential security threats. This article outlines a proactive and strategic container security approach that is aimed at aligning all stakeholders, including developers, operations, and security teams. By implementing these requirements, organizations can ensure that their container security is well-coordinated and effectively managed.
Opinions expressed by DZone contributors are their own.

Comments