Application Security in Technical Product Management
Application security is the practice of designing, developing, and deploying applications with security in mind, which is essential for protecting applications.
Join the DZone community and get the full member experience.
Join For FreeIn recent years, the number of cyberattacks has been steadily increasing, and applications have become increasingly targeted. According to a report by Verizon, web applications were the most common target of data breaches in 2022, accounting for over 40% of all breaches.
The cost of cyberattacks is also significant. According to a report by IBM, the average cost of a data breach in 2022 was $4.35 million. This includes the cost of containment, eradication, recovery, and reputational damage.
What Does Application Security Constitute?
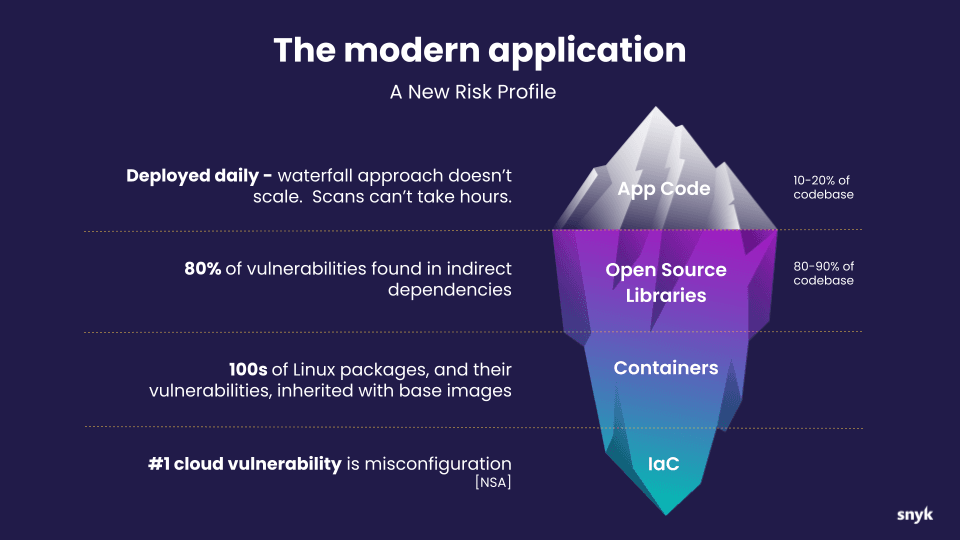
Image Credits: Snyk
Application security encompasses a wide range of activities, including:
- Threat modeling: Identifying and assessing the security risks facing an application.
- Secure coding practices: Writing code in a way that minimizes security vulnerabilities.
- Input validation: Validating user input to prevent attacks such as SQL injection and cross-site scripting (XSS).
- Session management: Managing user sessions securely to prevent unauthorized access to sensitive data.
- Authentication and authorization: Implementing strong authentication and authorization mechanisms to ensure that only authorized users can access the application and its resources.
- Security monitoring and logging: Monitoring the application for security threats and logging events for auditing and forensic purposes.
Why Is Application Security Important for Technical Product Managers?
Technical product managers (TPMs) play a critical role in application security. They are responsible for defining the vision and strategy for new products and features, and they work with engineering teams to bring those products and features to market.
TPMs must have a deep understanding of application security risks and how to mitigate them. They must also be able to communicate the importance of security to other stakeholders, such as executives and sales teams.
Application Security Best Practices for Developers and Engineers
In the dynamic world of software development, security is often a moving target. As developers and engineers build and maintain the technological backbone of our digital infrastructure, they must also safeguard against an ever-evolving array of cyber threats. Best practices in application security serve as the guidelines that, when integrated into the software development lifecycle (SDLC), can significantly reduce the risk of vulnerabilities and breaches. These practices are not merely recommendations; they are critical steps in creating robust applications that can withstand the onslaught of modern cyber-attacks. By adhering to these principles, developers can ensure that security is not an afterthought but a foundational element of their development process.
Here are some application security best practices for developers and engineers:
- Use a secure development framework (SDF): An SDF provides a set of guidelines and tools to help developers build secure applications.
- Keep your software up to date: Software vendors regularly release security updates to patch vulnerabilities. It is important to apply these updates promptly.
- Use strong passwords and multi-factor authentication: Strong passwords and multi-factor authentication help to protect user accounts from compromise.
- Validate user input: Validate all user input to prevent attacks such as SQL injection and XSS.
- Use encryption: Encrypt sensitive data at rest and in transit.
- Monitor your application for security threats: Use security monitoring tools to detect and respond to security threats promptly.
Mitigating Vulnerabilities
The landscape of cyber threats is one of constant change and adaptation. In response, the strategies to mitigate these threats must be equally adaptable and robust. Beyond the confines of code, vulnerability mitigation extends into the design, deployment, and maintenance phases of an application's lifecycle. The proactive management of vulnerabilities often leads to the avoidance of hasty patchwork.
Below is a simple example of code that employs parameterized queries, a method that helps prevent SQL injection, a common security vulnerability.
#Using parameterized queries to avoid SQL injection
import sqlite3
def get_user_details(user_id):
with sqlite3.connect('application.db') as conn:
cursor = conn.cursor()
cursor.execute('SELECT * FROM users WHERE id=?', (user_id,))
return cursor.fetchone()
Let’s look at another example. In this extended example, we will write a Python Flask web application snippet that:
- Validates and sanitizes user input for a profile update form.
- Uses parameterized queries to interact with a PostgreSQL database to prevent SQL injection.
Implements error handling to manage potential security events effectively.
from flask import Flask, request, jsonify, abort
from flask_sqlalchemy import SQLAlchemy
import re
app = Flask(__name__)
#Configuration for the PostgreSQL database connection
app.config['SQLALCHEMY_DATABASE_URI'] = 'postgresql://username:password@localhost/dbname'
db = SQLAlchemy(app)
# Define a User model for SQLAlchemy
class User(db.Model):
id = db.Column(db.Integer, primary_key=True)
username = db.Column(db.String(80), unique=True, nullable=False)
email = db.Column(db.String(120), unique=True, nullable=False)
def __repr__(self):
return '<User %r>' % self.username
# Sanitize input data function
def sanitize_input(input_string):
# Remove potential script tags or SQL injection attempts
sanitized_string = re.sub(r'[;\'"<>]', '', input_string)
return sanitized_string
# Update user profile route
@app.route('/update_profile', methods=['POST'])
def update_profile():
user_id = request.form.get('user_id')
new_username = request.form.get('username')
new_email = request.form.get('email')
if not user_id or not new_username or not new_email:
# Missing user ID, username, or email
abort(400, description="Please provide user_id, username, and email")
# Sanitize the inputs
user_id = sanitize_input(user_id)
new_username = sanitize_input(new_username)
new_email = sanitize_input(new_email)
# Using parameterized queries to avoid SQL injection
try:
user = User.query.get(user_id)
if user:
user.username = new_username
user.email = new_email
db.session.commit()
return jsonify({"message": "Profile updated successfully"}), 200
else:
abort(404, description="User not found")
except Exception as e:
# Handle unexpected errors
db.session.rollback()
abort(500, description="An error occurred while updating the profile")
if __name__ == '__main__':
db.create_all() # Create database tables
app.run(debug=True)
This code demonstrates several best practices for secure web application development:
- Input sanitization: Before any processing, input strings are sanitized to remove any characters that could be used maliciously.
- Use of ORMs and parameterized queries: SQLAlchemy ORM is used to handle database interactions, which uses parameterized queries internally to prevent SQL injection.
- Error handling: Proper error handling not only prevents crashes but can also mitigate certain types of security vulnerabilities that rely on error messages to glean information about the database structure.
- Abort with descriptions: Instead of providing detailed error descriptions that might leak sensitive information, the abort function is used to stop the process and return a generic error message.
This example reinforces the importance of defensive programming in managing security risks and should be a part of the Technical Product Manager's mandate when overseeing the product development life cycle.
Real-World Case Study: The Equifax Data Breach
In September 2017, Equifax, one of the largest credit bureaus in the United States, announced a massive data breach affecting over 147 million consumers. Personal information, including Social Security numbers, birth dates, addresses, and in some instances, driver's license numbers, were compromised. The breach was a stark reminder of the devastating consequences of security oversights and the importance of stringent application security measures.
The Breach Breakdown
The Equifax breach was traced back to a vulnerability in Apache Struts, an open-source web application framework for developing Java EE web applications. A patch for this vulnerability had been available for months before the breach occurred, yet Equifax failed to update their systems promptly. This oversight provided hackers with a window of opportunity to exploit the vulnerability and gain unauthorized access to Equifax's customer data.
Security Shortcomings
Several critical security failings contributed to the breach:
- Delayed patch management: The lack of timely application of known security patches allowed for the exploitation of a known vulnerability.
- Inadequate segmentation: Poor network segmentation meant that once the attackers gained access to one part of the network, they could move laterally with ease.
- Insufficient encryption: Sensitive data was not adequately encrypted, making it easier for attackers to make use of the data once it was accessed.
- Lack of robust authentication: Weak internal authentication measures failed to protect against unauthorized access.
Lessons Learned
The Equifax breach serves as a cautionary tale for technical product managers, developers, and engineers alike. The lessons learned from this incident emphasize several key aspects of application security:
- Timeliness is critical: Security patches must be applied as soon as they become available. Delaying updates opens a window for attackers.
- Defense in depth: Security should be layered and not reliant on a single point of protection. Network segmentation and data encryption are vital.
- Continuous monitoring: Regular and continuous monitoring can detect breaches early before they escalate into major crises.
- Security as a priority: Security should be an integral and prioritized component of the product development lifecycle, from conception through deployment and maintenance.

The Equifax data breach underscores the need for a security-first approach in technical product management. By integrating security best practices into every phase of the development and operational process, organizations can mitigate the risks of such breaches. This incident reinforces the importance of a proactive security posture and the potential cost of complacency.
Applying Security Principles to the Development Process
DevSecOps
DevSecOps is a set of practices that integrates security into the software development lifecycle (SDLC). This means that security is considered at every stage of development, from planning to production. DevSecOps helps to identify and fix security vulnerabilities early on, before they can be exploited by attackers.
There are many benefits to using DevSecOps, including:
- Improved security: DevSecOps helps to improve the security of software applications by integrating security into all phases of development. This helps to identify and fix security vulnerabilities early on, before they can be exploited by attackers.
- Reduced costs: RDevSecOps can help to reduce the costs of security by identifying and fixing security vulnerabilities early on. This can help to prevent costly data breaches and other security incidents.
- Increased agility: DevSecOps can help to increase the agility of software development teams by automating security tasks and integrating security into the CI/CD pipeline. This helps teams to release software more quickly and securely.
Security Testing
Security testing is the process of evaluating the security of an application. There are many different types of security testing, each with its own focus. Some of the most common types of security testing include:
- Penetration testing: Penetration testing involves simulating an attack on an application to identify security vulnerabilities.
- Vulnerability scanning: Vulnerability scanning involves using automated tools to scan for known security vulnerabilities in an application.
- Static analysis: Static analysis involves analyzing code to identify potential security vulnerabilities.
Security testing is an important part of the SDLC. It helps to identify and fix security vulnerabilities early on, before they can be exploited by attackers.
Security Compliance
Many organizations are required to comply with security regulations such as PCI DSS and HIPAA. These regulations set forth requirements for how organizations must protect their data and systems. Technical product managers must ensure that their products meet these compliance requirements.
There are a number of things that technical product managers can do to ensure that their products meet security compliance requirements, including:
- Identify the relevant security regulations: The first step is to identify the security regulations that apply to the product.
- Assess the product's compliance: Once the relevant security regulations have been identified, the next step is to assess the product's compliance with those regulations.
- Implement a compliance plan: If the product is not compliant with the relevant security regulations, a compliance plan must be developed and implemented.
- Monitor compliance: Compliance is an ongoing process. Technical product managers must monitor the product's compliance on an ongoing basis and make any necessary changes to ensure that the product remains compliant.
Security compliance is important for protecting organizations from data breaches and other security incidents. By ensuring that their products meet security compliance requirements, technical product managers can help protect their organizations and their customers.
Risk Management Strategy
According to Verizon’s data breach report, outsiders know the value of various files on company databases more than an insider.

As per IBM report, a Proactive incident management strategy could minimize the impact on the organization’s bottom line and, hence, reputation. An incident response plan for the team as the team sails through various phases, from detection to remediation, is critical for compliance reasons.

Conclusion
Application security is essential for protecting businesses and individuals from cyberattacks. Technical product managers (TPMs) play a critical role in application security by defining the vision and strategy for new products and features and by working with engineering teams to bring those products and features to market.
Opinions expressed by DZone contributors are their own.

Comments