Penetration Testing: A Comprehensive Guide
Penetration testing is a security testing technique that incorporates launching unauthorized attacks to gain access to sensitive data.
Join the DZone community and get the full member experience.
Join For FreeCybersecurity threats are real, and with the enhanced proliferation of digitization in the business landscape today, websites have become an integral part of business communication with customers and partners. Therefore, companies look for new and secure ways to protect their web applications. Penetration testing or popularly termed Pen testing, is acknowledged as a reliable methodology to protect web applications from cyber attacks.
The critical factor is that vulnerabilities in web applications have enhanced in the last few years, mainly because of the lack of validation and sanitization of the input data. Detecting the existing vulnerabilities in the web application is crucial before its release to ensure its reliability and build high-quality and secure web applications.
What Is Penetration Testing?
Penetration testing is a security testing technique that incorporates launching unauthorized attacks to gain access to sensitive data. It mainly focuses on testing the web application and doesn’t incorporate the entire network of a business organization. It checks the vulnerabilities in the existing web application, including all the components; source code, back-end network, and database. There is the simulation of internal and external attacks on the web application to ascertain the existing vulnerabilities. The fundamental purpose of conducting these tests is to ensure that the developer prioritizes safety parameters in the application with a strategic approach to mitigate the risks successfully.
Why Is Pen Testing Relevant?
These days all businesses across industries are interacting with customers and making their niche with an authoritative online presence via a website application. Customers prefer to interact with fast, secure, and easy-to-use web applications for online shopping, gaining information about the company’s products, reading reviews, establishing a first level of contact, and, once satisfied, moving towards making payments to meet their requirements. Now, when customers enter their personal and sensitive information into the website portal to gain further information or make a purchase, strict security parameters are much needed.
Let’s dig into the vital purpose of Pen Testing:
- To identify existing vulnerabilities.
- Assessment of web application security protocols.
- Identify the most vulnerable path that could lead to a cyber attack.
- Verifying the credibility of publicly available components like routers, DNS, and firewalls.
- Explore any potential vulnerabilities leading to data theft.
Types of Penetration Testing
Penetration tests are done in two ways: by simulating internal attacks or opting for an external attack. So, let’s take an insider’s look into both these types of testing in detail below:
Internal Penetration Testing
It is a common misconception that threats can come from external sources. Internal threats are equally critical. Therefore, web applications need to be tested internally via Local Area Network and include all applications on the intranet as well. Internal attacks can be triggered by internal people who have access to passwords, bank details, and other sensitive business information. There could be malicious emails triggering phishing attacks or getting access to user privileges either through hacking or stealing sensitive information like passwords. The internal Pen tests are directed towards countering these loopholes without password information to understand the possible routes for the attack to strengthen the security of the web application.
External Penetration Testing
In this scenario, the attacks are launched externally by the testers, popularly known as ethical hackers. These hackers don’t have any information about the company’s existing systems, security layers, and protocols. All they have is the IP address of the given company to ethically hack the system, unleash the route for a potential attack, and flesh out all vulnerabilities. The testers also attack the firewalls, servers, and DNS to infiltrate the existing systems.
Testing Methodology of Penetration Testing
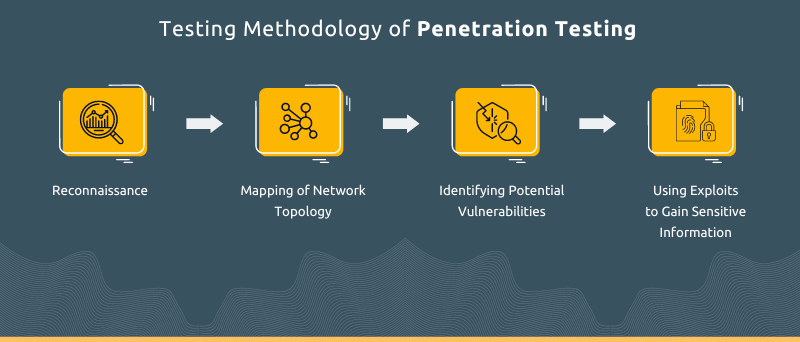
The testers follow a cyclic methodology of pen testing, and it continues till they are able to gauge any vulnerabilities in the web application.
So, let’s take a look at the methodology of Pen Testing:
- Reconnaissance: The first step, popularly known as recon, comprises accumulating information about the target application that needs to be tested for vulnerabilities. There can be usage of active or passive reconnaissance depending upon the target web application and the outcomes needed from tests.
- Mapping of Network Topology: Once the target application is decided, the next step is to understand its network topology using the name and IP address of the target. It encompasses network threat modeling that primarily gauges the different networks connected to the target in place and includes mapping of the security protocols that are being utilized.
- Identifying Potential Vulnerabilities: This step involves exploring existing vulnerabilities that could be leveraged to trigger an attack.
- Using Exploits to Gain Sensitive Information: Once the vulnerability is identified, the next step is to utilize exploits like SQL injections, or there can be usage of buffer overflows that help testers to gain access to sensitive data.
Process of Launching An Attack

1. Using Active and Passive Reconnaissance: The active reconnaissance means deriving information directly from the target web application using Nmap fingerprinting, Shodan network scanner, DNS forward and reverse lookup, DNS zone transfer, using Burp suite covers to identify the flow of traffic between target and external websites.
There is scrutiny of head and option requests with Burp suite covers and gaining information about the server and the version on which the website is running from error pages like 404. There is also an exploration of source code to understand the environment in which web applications are running and documenting all data points to make the attack more robust to steer clear of all vulnerabilities.
2. Launching the Attack: The attack is triggered based on the data points gathered. It also helps to identify the tools best suited to launch the attack successfully.
3. Documentation: After testing, a detailed report is prepared on the findings of the Pen testing. The data validate all the points, and there is a critical evaluation of all the results to dig deeper into the possibility of more severe attacks in the future.
Penetration Testing Tools
Plenty of tools are available for Pen Testing in the market, but a careful analysis of the same is needed to make a smart choice.
Here are the different tools:
- AirCrack-ng: A wireless LAN testing tool that has been around for quite a long time. It is primarily used to recover WEP/WPA/WPA2 keys. Testers mainly use it to identify vulnerabilities in the wireless network, but it also incorporates other use cases, such as finding networks with no strong security layers and decrypting traffic mainly on Wi-Fi networks that are fully encrypted. This tool also caters to the exploit the Open Wi-Fi that is not supported by strong passwords or any encryption layer.
- Nmap: This tool supports network discovery and security auditing by using a scripting module that uses the backdoor to exploit any vulnerability in the target web application, along with providing basic inputs.
- Metaspoilt: It is not just a tool but a framework that can be employed to create custom tools designated for specific tasks. It comes with lots of possibilities, like selecting and configuring the exploit to target or payload to be employed, encoding schema, and finally, supporting the execution of the exploit.
- SQLmap: This tool supports the successful execution of SQL injection attacks. Primarily, a tool based on the command line that helps in exploiting any discrepancies in the SQL injections. It can be used against both error-based and blind SQL injection vulnerabilities.
- Nessus: A tool that helps to scan and identify vulnerabilities in the web application, including configuration concerns or any malware in the system. This tool’s main role is supporting the testers in the reconnaissance phase.
The choice of tool depends on the ease of usage, functionality, performance, and integration of tools with the existing testing tools, reporting, and cost involved.
Conclusion
To sum up, digitizing processes across industries and businesses has made websites a crucial part of modern-day business. There is a need to have strict data protection protocols in place, and pen testing is essential to ensure that a company supports a web application that is safe, robust, and security-proof. And the sensitive customer and business data is secure, which enhances customer satisfaction and brand reputation. So, having a reliable testing partner can help businesses to keep their applications safe and continue to have a robust relationship with customers and partners alike.
Opinions expressed by DZone contributors are their own.

Comments