Going on a Threat Hunt: Advanced Strategies for Defending the Digital Frontier
By seeking out and identifying hidden threats, security teams can neutralize advanced attacks that might evade automated systems.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, Enterprise Security: Reinforcing Enterprise Application Defense.
Threat hunting is a proactive cybersecurity strategy that actively searches for hidden threats throughout an organization's entire digital environment. Unlike traditional security measures that primarily react to incidents, threat hunting assumes a breach has already occurred and aims to identify malicious activity before it escalates. By analyzing vast amounts of data from networks, endpoints, and cloud environments, organizations can uncover suspicious patterns, neutralize threats, and significantly reduce their risk of a successful cyberattack.
This article sets the overall context and scope for implementing threat detection and hunting in software systems. We will explore new-age practices, advanced tooling, and the integration of AI in threat detection, equipping organizations with the knowledge and tools to bolster their security defenses.
Threat Hunting
Conventional cybersecurity measures — like intrusion detection system, intrusion prevention system, antivirus, and malware supervision — primarily operate reactively, relying on predefined signatures and alerts to detect known threats such as common malware and viruses. In contrast, threat hunting is a proactive manual or semi-automated process that actively seeks out hidden threats, including advanced persistent threats (APTs), zero-day vulnerabilities, and insider threats.
While traditional tools provide automated, broad coverage, they often miss sophisticated threats that evade detection. Threat hunting involves deep, hypothesis-driven investigations to uncover unknown threats, focusing on behavioral anomalies and indicators of compromise (IOCs). This proactive approach enhances an organization's security posture by decreasing the time that threats remain undetected and adapting to the evolving threat landscape.
Threat Modeling vs. Threat Hunting
Threat modeling is a proactive process that identifies potential vulnerabilities in a system before it's built. It helps prioritize security controls. Threat hunting is both proactive and investigative, focusing on identifying active threats within identified compartments or scope. While different, they complement each other. Threat modeling informs threat hunting by highlighting potential targets, while threat hunting can reveal vulnerabilities missed in modeling.
Table 1. Threat modeling vs. threat hunting
| Features | Threat Modeling | Threat Hunting |
| Intent | Dry run — identify potential risks and vulnerabilities in a system or application | Threat simulation — proactively detect anomalies and vulnerability threats within an environment |
| Approach | Preventive, theoretical approach | Proactive, detective approach |
| Phase | Performed during the design and early development phases | Conducted toward the end of implementation and during maintenance |
| Methodology | Threat identification, risk assessment, mitigation planning | Hypothesis-driven, data-driven analysis, anomaly detection |
| Result | Mitigation strategies, security controls | Threat identification, incident response, and security measure enhancements |
| Modeling tools | Threat modeling frameworks (STRIDE, PASTA, LINDDUN, VAST), diagramming mapping | Endpoint detection, network analysis, security information, event management, etc. |
| Expertise | ISO consultant, security architects, developers, analysts | ISO consultant, security analysts, incident responders, threat intelligence analysts |
| Relationship | Threat modeling identifies potential vulnerabilities that can be targeted by threat hunting | Threat hunting can uncover vulnerabilities that were not previously identified through threat modeling |
AI: The Double-Edged Sword of Threat Hunting
Threat hunting is increasingly becoming an arena for AI competition. The cyber threat landscape is a continuous arms race, with AI serving as a powerful tool for both attackers and defenders. Malicious actors leverage AI to automate attacks and develop sophisticated, adaptive malware. In response, organizations are turning to AI-powered threat hunting solutions to proactively detect and respond to these evolving threats.
AI tools excel at analyzing vast amounts of data in real time, uncovering hidden patterns and anomalies that would be challenging for humans to detect. By integrating machine learning (ML) with threat modeling, AI continuously learns and adapts, enhancing threat detection and enabling the proactive identification and prediction of future attacks. Combining continuous learning from ML models with human expertise and traditional security controls creates a robust defense that is capable of outsmarting even the most sophisticated adversaries.
AI-Driven Integration of Open-Source Intelligence in Threat Modeling
The integration of AI and continuous open-source intelligence in threat modeling has revolutionized the ability to detect and respond to emerging threats. However, it also introduces new challenges and potential threats. Below is a summary of these aspects:
Table 2. Threats and challenges introduced by AI-driven threat modeling
| Aspects | Examples | |
| New threats introduced by AI | AI-powered attacks | Sophisticated phishing, evasion techniques, automated attacks |
| Automation of attacks | Speed and scale, targeting and personalization | |
| Challenges to threat modeling | Dynamic threat landscape | Evolving threats, predicting AI behaviors and AL/ML opacity of intermediate state of models |
| Data overload | Volume of data, quality, and relevance | |
| Bias and false positives | Training data bias, false alarms | |
| Complexity and transparency | Algorithm complexity, lack of transparency | |
| Addressing challenges | Regular hypothesis tuning | Continuous AI model updates with diverse data |
| Human-AI collaboration | Human-AI integration for validated results | |
| Advanced filtering techniques | Filtering and prioritization focused on context | |
| Adoptable, transparent, and governed | Development of transparent, governed AI models with audits |
By addressing these challenges and leveraging AI's strengths, organizations can significantly enhance their threat modeling processes and improve their overall security posture. While AI plays a crucial role in processing vast amounts of open-source intelligence, its integration also introduces new challenges such as AI-powered attacks and data overload. To effectively counter these threats, a balanced approach that combines human expertise with advanced AI is essential. Furthermore, continuous learning and adaptation are vital for maintaining the effectiveness of threat modeling in the face of evolving cyber threats.
Enabling Threat Detection in Software
Effective threat detection demands a practical, end-to-end approach. Integrating security measures across the software lifecycle that cut across the enterprise technology stack is essential. By implementing a layered defense strategy and fostering a security-conscious culture, organizations can proactively identify and mitigate threats.
Key Steps of Threat Hunting
Below are dedicated stages of and steps for approaching an effective enterprise-wide threat detection strategy, along with practical examples, based on threat modeling.
Stage One: Preparation and Planning
☑ Define scope: focus on specific areas such as network, endpoints, and cloud — e.g., protect transaction systems in a financial institution
☑ Identify critical assets: determine high-value targets — e.g., patient records in healthcare and payment card information
☑ Develop hypotheses: formulate educated guesses about potential threats — e.g., brute force attack indicated by failed login attempts
☑ Establish success criteria: set metrics for effectiveness — e.g., detect threats within 24 hours
☑ Assemble team: identify required skills and assign roles — e.g., include a network analyst, forensic investigator, and threat intelligence expert
Stage Two: Data Collection and Analysis
☑ Identify data sources: use SIEM, EDR, network logs, etc. — e.g., collect logs from firewalls and servers
☑ Collect and normalize data: standardize data for analysis — e.g., ensure consistent timestamping
☑ Enrich data with context: add threat intelligence — e.g., correlate IP addresses with known threats
☑ Analyze for anomalies: identify unusual patterns — e.g., use ML for behavior deviations
☑ Correlate data points: connect related data to uncover threats — e.g., link unusual login times with network traffic
Stage Three: Investigation and Response
☑ Validate findings: confirm identified threats — e.g., analyze files in a sandbox
☑ Prioritize threats: assess impact and likelihood — e.g., prioritize ransomware over phishing
☑ Develop response plan: outline containment, eradication, and recovery steps — e.g., isolate systems and restore from backups
☑ Implement countermeasures: mitigate threats — e.g., block malicious IP addresses
☑ Document findings: record details and lessons learned — e.g., document incident timeline and gaps
Stage Four: Continuous Feedback and Improvement
☑ Measure effectiveness: evaluate hunting success — e.g., improved detection and response times
☑ Adjust hypotheses: update based on new insights — e.g., include new attack vectors
☑ Update playbooks: refine hunting procedures — e.g., add new detection techniques
☑ Share knowledge: disseminate findings to the team — e.g., conduct training sessions
☑ Stay informed: monitor emerging threats — e.g., subscribe to threat intelligence feeds
Figure 1. Threat hunting process
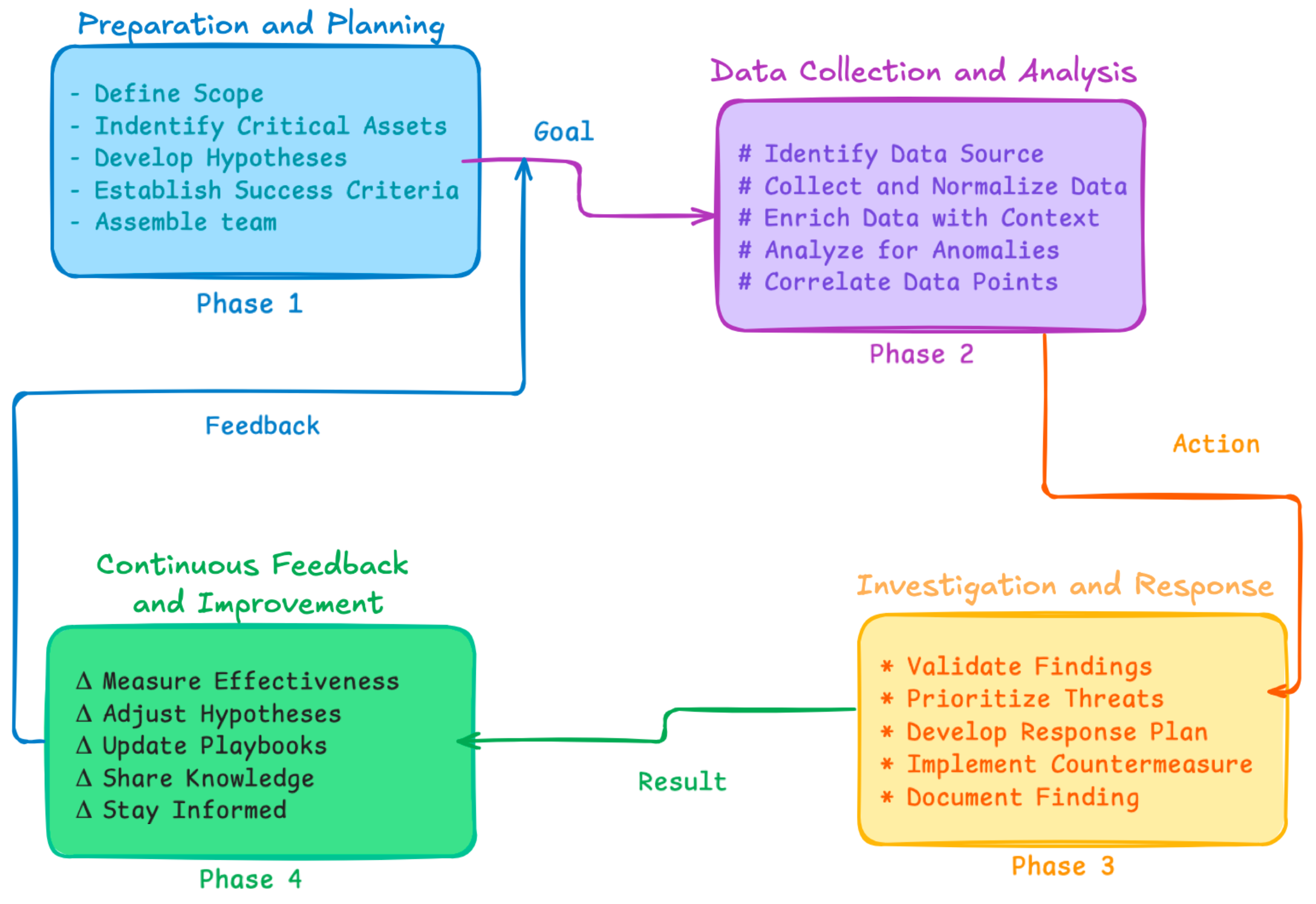
By following these steps, organizations can enhance their threat hunting capabilities and improve their overall security posture.
Bridging the Gap: How Detection Engineering Complements Threat Hunting
Detection engineering focuses on building a robust foundation of security controls to protect against known threats. By developing and refining detection rules, leveraging SIEM systems, and automating alerts, organizations can effectively identify and respond to malicious activity. Continuous testing and validation, along with the integration of threat intelligence, ensure that these defenses remain up to date and effective.
While detection engineering is vital for maintaining strong defenses, it is not foolproof. Even the most sophisticated detection systems can be bypassed by APTs and other stealthy adversaries. This is where threat hunting steps in: By proactively searching for hidden threats that have evaded existing defenses, threat hunting uncovers IOCs and behavioral anomalies that automated systems might miss. While detection engineering provides the necessary tools and infrastructure to recognize known threats, threat hunting extends this capability by exploring the unknown, investigating subtle signs of compromise, and validating the effectiveness of existing controls.
When detection engineering and threat hunting are combined, they create a powerful synergy that significantly enhances an organization's cybersecurity posture. Detection engineering provides a robust framework for identifying and responding to known threats efficiently, ensuring that security systems are well prepared to handle familiar risks. On the other hand, threat hunting takes a proactive stance, continuously challenging and improving these systems by uncovering previously unknown threats and refining detection strategies.
This dual approach not only strengthens defenses against a wide spectrum of cyberattacks but also promotes a culture of continuous improvement, allowing organizations to address both known and emerging threats with agility and precision. By integrating these two disciplines, organizations can build a comprehensive and adaptive defense strategy, greatly enhancing their overall resilience against evolving cyber threats.
Key Considerations Around Effective Threat Hunting
In a complex cybersecurity landscape, effective threat hunting requires more than just the right tools; it demands a strategic approach that considers various crucial aspects. This section delves into the key factors that contribute to successful threat hunting operations, including the roles and responsibilities of different team members, the importance of diverse data sources, and the balance between automation and human expertise. By understanding these elements and integrating them into your threat hunting strategy, organizations can proactively identify threats, reduce dwell time, and improve their overall incident response capabilities.
Table 2. Effective threat handling aspects
| Aspects | Details |
| Expected outcomes | Proactive threat identification, reduced dwell time, improved incident response |
| Roles and responsibilities | Threat hunters (who lead threats simulation), analysts (data analysis for hypothesis), responders (mitigate actors for threats) |
| Sources | Open-source data, commercial threat intelligence feeds, intelligence-sharing communities |
| Incorporation | Enriching threat hunting hypotheses, validating findings, updating hunting playbooks |
| Balance | Combine human expertise with automation for optimal results |
| Tools | SIEM, EDR, SOAR, AI-powered analytics platforms |
| Continuous learning | Attend industry conferences, webinars, and training |
| Community engagement | Participate in security forums and communities |
Conclusion
In today's increasingly complex cyber threat landscape, it is essential to anticipate and address threats before they materialize. By implementing the outcomes of threat modeling hypotheses, organizations can drive continuous improvement and identify key areas for enhancement. Collaboration is equally crucial — partnering with like-minded organizations for joint hackathons and drills fosters shared learning, best practices, and heightened preparedness. Regular chaos-themed drills further build resilience and readiness for real-world incidents.
Investing in AI-driven tools and integrating AI into threat simulation and anomaly detection are no longer optional but necessary. AI and ML models, with their ability to retain and learn from past patterns and trends, provide continuous feedback and improvement. This enhances threat detection by identifying subtle patterns and anomalies within vast datasets, keeping organizations one step ahead of emerging threats. Ultimately, continuous proactive threat hunting ensures a robust defense against the ever-evolving threat landscape.
Adopting these proactive threat hunting principles and practices is essential for staying ahead of threats and malicious stealth actors. By actively seeking out and identifying hidden threats before they can cause damage, organizations can maintain a robust defense. This proactive approach ensures that security teams can detect and neutralize advanced attacks that might evade automated systems, keeping organizations safe and resilient against evolving cyber threats.
This is an excerpt from DZone's 2024 Trend Report,
Enterprise Security: Reinforcing Enterprise Application Defense.
Read the Free Report
Opinions expressed by DZone contributors are their own.

Comments