Top 6 Cybersecurity Threat Detection Use Cases: How AI/ML Can Help Detect Advanced and Emerging Threats
Learn how to get started to design and build AI/ML solutions that are capable of revolutionizing the cybersecurity threat detection landscape.
Join the DZone community and get the full member experience.
Join For FreeAI/ML tools and technologies heavily influence the modern digital landscape by introducing numerous use cases involving AI-based malware detection, preventing social engineering attacks, and threat identification and remediation. Many organizations have acknowledged AI/ML's prominence in the cybersecurity threat landscape and have started to leverage AI/ML in their business and security requirements. AI/ML-based solutions assist employees to complete their day-to-day tasks more efficiently and in no time. However, at the same time, we have also witnessed an exponential increase in the cybersecurity threat landscape. Hence, cybersecurity professionals and software developers have also started using AI/ML to build more innovative, adaptive, and robust systems and applications to protect an organization's IT and network infrastructure.

Statistics: AI/ML in Cybersecurity
In recent times, we have witnessed the widespread adoption and exponential growth of AI and ML technologies. Below are the statistics taken after thorough research highlighting the impact of AI/ML tools and techniques on cybersecurity threat detection and increasing overall cybersecurity performance.
- Statistics show that the global AI software market currently generates around $100 billion in revenue, which is expected to grow in the coming years.
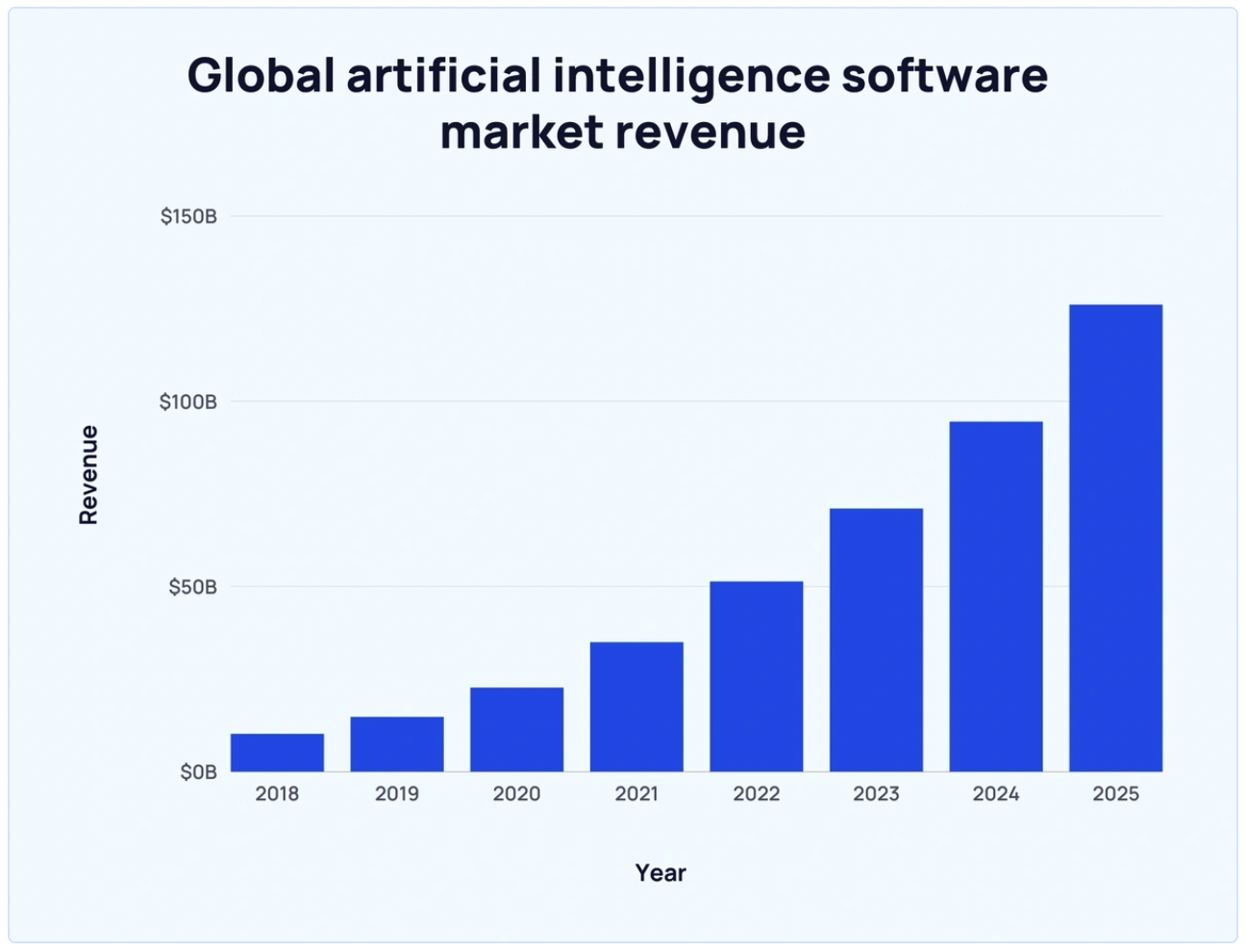
(Source: Exploding Topics)
- According to the Global State of Security Operations report, AI/ML powers 93% of SOCs (Security Operations Centres) for threat detection.
- According to a report by Capgemini, 69% of organizations believe they won't be able to respond to critical threats without AI. Additionally, 73% of organizations already use AI to assist in security operations.
- According to a report presented by Statista, the market for AI in cybersecurity is expected to show considerable growth in the coming years, from around 24 billion U.S. dollars in 2023 to roughly 134 billion U.S. dollars by 2030.
- According to a Cisco 2024 Data Privacy Benchmark Study, 79% of organizations are getting very significant or significant value from GenAI.
AI/ML in Cybersecurity Threat Detection: Use Cases
No one can deny the significant impact that AI and ML solutions are going to have on cybersecurity threat detection. AI/ML helps swiftly detect and respond to cybersecurity threats in a dynamic and complex cyber landscape. These advanced methodologies offer key benefits like automated workflow, reduced human intervention, accuracy, minimizing false positives, and much more. Let's explore some key use cases of AI-driven security solutions in enhancing cybersecurity threat detection.
1. AI-Driven Security Operations Centers (SOCs)
A SOC's day-to-day tasks include threat monitoring, researching varied log datasets, detecting and identifying threats, and providing remediation steps to lower the impact of security incidents. AI/ML solutions can help automate and streamline these substantial processes, overall increasing the effectiveness, resiliency, and accuracy of SOC systems. Developers and security professionals can work on developing and training AI/ML solutions that can detect advanced threats, including zero-day attacks and complex malware, and analyze the malware against unknown attack signatures and/or anomalies that traditional systems are bound to miss.
2. Identification of Social Engineering and Phishing Attacks
AI is revolutionizing the detection and prevention of social engineering and phishing attacks. Anti-phishing tools are now evolving by leveraging AI/ML to recognize patterns and behaviors. These models play a crucial role in predicting and preventing phishing attacks while analyzing large datasets (both structured and unstructured) to analyze patterns and create attack signatures, consequently easing the early identification and remediation of such attacks.
3. Attack Signature and Anomalies Identification
Attack signature identification requires a unique set of methodologies and techniques for which AI/ML models are tailored. These models are excellent at identifying attack signatures by analyzing massive amounts of historical and real-time data curated from varied sources, including structured and unstructured data. They help recognize known attack patterns while also adapting to identify previously unknown signatures, helping security systems stay ahead of emerging threats. AI can be used to detect anomalous activities like unauthorized data access or privilege escalation, helping prevent data breaches from internal actors.
4. AI leveraged Predictive Analytics and Threat Intelligence
AI/ML solutions, when leveraged with predictive analytics and threat intelligence techniques, can enable organizations to forecast potential threats and/or cybersecurity incidents. These systems are well-trained against datasets revolving around tactics used in past attacks to predict future vulnerabilities, allowing for proactive threat identification and mitigation and strengthening overall security posture.
- AI/ML solutions can also substantially reduce the number of false positives and allow security researchers to focus on the legitimate threat. These models train themselves on historical data, increasing their accuracy with each phase.
- AI-powered solutions help organizations stay ahead of dynamic threats by incorporating AI-driven predictive analytics and threat intelligence, which can anticipate potential attacks by analyzing vast amounts of data already available
5. Earlier Malware Detection
Earlier, anti-virus or malware detection systems heavily relied on known patterns or behaviors depicted by malware, explicitly known as "attack signatures." However, this methodology makes these solutions less effective against zero-day malware attacks. AI models can analyze millions of samples of malicious and benign files and can detect even the subtle indicators of virus activities or new malware variants that have not yet been cataloged. AI/ML tools can significantly enhance the pace of response results when encountering cybersecurity incidents, as they automate real-time threat detection and mitigation strategies.
6. Insider Threat Detection
AI/ML-based solutions can easily be leveraged to detect and identify the potential presence of insider threats. These models can help monitor user behavior and identify anomalies that seem suspicious in nature when compared to established patterns. Attempts to suspicious activities like unauthorized access, data exfiltration, insider-driven breaches, etc., can be detected in real-time, significantly minimizing the impact of cybersecurity incidents. These solutions can scale up to greater depths effortlessly and seamlessly, handling huge volumes of data to analyze and respond to any internal threats.
Final Words
At the approaching end, one cannot deny the optimum and refined results produced by AI and ML tools and technologies when exposed to cybersecurity threat detection tasks and overall enhancement of security posture. These technologies offer unparalleled advantages such as resilient cyber threat detection capabilities, faster response times, reduced false positives, and curation of reliable and optimum attack signatures to identify existing (known) cybersecurity threats. We can stay one step ahead of emerging risks and threat vectors by leveraging concepts of AI/ML in our end-to-end business operations. This dependence on AI/ML solutions is bound to increase in the upcoming years as these cyber threats continue to grow and evolve, eventually becoming an essential business component for modern cybersecurity strategies.
Opinions expressed by DZone contributors are their own.

Comments