Using Client Certificates Vs Passwords and MFA for Authentication
COVID-19 has precipitated the widespread adoption of remote work across all industries and sectors and many employees believe that it is here to stay.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
Identity is the new perimeter, and it is becoming increasingly challenging to secure thanks to distributed workforces and unprecedented levels of remote work forced by COVID-19. Security used to consist simply of using firewalls to defend your network’s perimeter. Now, with today’s complex IT ecosystem including multi-cloud environments, IoT, DevOps, and BYOD mobile phones and other devices, securing the identities of people, devices, and systems is more difficult than ever.
The 2020 Data Breach Investigations Report by Verizon found that more than 80% of breaches tied to hacking involve the use of lost or stolen credentials or brute force, a fact that highlights the weaknesses of password-based authentication in the WFH era. While COVID-19 has precipitated the widespread adoption of remote work across all industries and sectors that rely on knowledge workers, many believe that it is here to stay. In fact, 38% of respondents to the recent Voice of the Enterprise Digital Pulse flash survey from 451 Research (S&P Global) believe that working from home will likely be long-term or permanent.
Overworked IT teams have had to scramble to protect their organizations and their newly-remote employees during the pandemic, even as the threat landscape has expanded. According to the FBI, “As of May 28, 2020, the Internet Crime Complaint Center received nearly the same number of complaints in 2020 (about 320,000) as they had for the entirety of 2019 (about 400,000).” Attacks have become more sophisticated and effective, too—particularly socially engineered attacks, which have preyed on employees and have exploited new work behaviors. This has major implications for businesses as they work to secure their perimeter-less enterprises and remote workforces, especially if traditional passwords or multi-factor authentication (MFA) are their main methods of identity authentication.
As a result of weaker authentication methods, enterprises are increasingly taking a Zero Trust approach to secure their people, devices, data, and systems, in which trust is never granted implicitly and must be continually evaluated. Public key infrastructure (PKI) is the gold standard for identity authentication and information encryption and signing, and the National Institute of Standards and Technology (NIST) recently named PKI a key element of a Zero Trust architecture. PKI doesn’t just provide increased identity security—it can simplify the experience for employees and administrators and can reduce the total cost of ownership (see Figure 1).
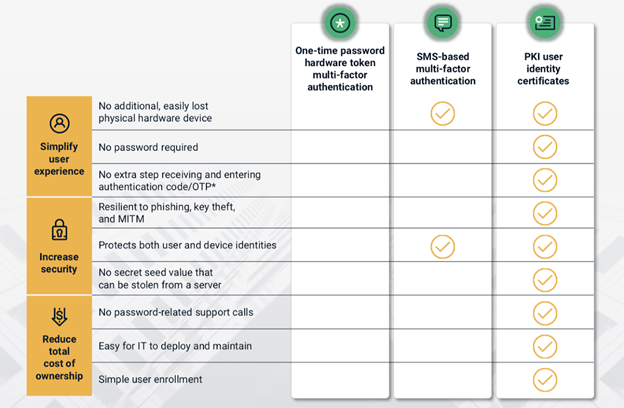
Figure 1. While SMS-based MFA provides a degree of extra security, PKI user identity certificates are the strongest form of identity authentication.
Passwords Are Easily Stolen and Costly To Maintain
All enterprises rely on passwords, but malicious actors have become highly adept at stealing them. The degree of security provided by passwords is no longer enough to keep your organization safe using a Zero Trust model.
The human factor associated with passwords, i.e., that individuals reuse, share, and routinely forget them, compounds the risk in today’s threat landscape. And the cost to an organization for maintaining these passwords is significant—both due to the potential for data loss, outages, and compromised information, and because passwords must regularly be reset or undergo complex changes.
Passwords have always been painful for employees to use and remember, impacting productivity and requiring significant support costs. According to Gartner, between 20% to 50% of all help desk calls are for password resets, while Forrester Research states that the average help desk labor cost for a single password reset is about $70. Data published by Microsoft indicates that their annual cost of password reset was $9M a few years ago.
MFA Is Not as Secure as You Think
Many organizations and services look to boost security by replacing passwords with MFA that uses extra phone or token-based steps. But typical MFA is not as secure as you think, and it still leaves security vulnerabilities. NIST and the FBI have recently warned about using MFA due to the potential of compromised one-time passwords (OTP) delivered via SMS. Attackers can simply port a phone number to a device they control and gain access to OTPs. Compromised SMS-based authentication methods are just as easy to steal at scale as passwords.
Attackers are also using non-SMS-based methods to steal OTPs. In March 2020 it was discovered that the TrickBot Trojan was gaining access to Android users’ phones in Germany via social engineering attempts that encouraged users to download a malicious app that had app-specific recording capabilities. TrickBot was then able to record screens in order to access the push notification OTPs for MFA used by European banks in an attempt to avoid SMS interception of OTPs.
Furthermore, for security to be effective, it must be easy for employees to use. MFA is notoriously difficult for users and doesn’t even eliminate the burden of passwords. While MFA certainly provides an added measure of security beyond that of simple passwords, it also increases friction for the employee and complicates life for IT administrators.
PKI-Based Certificates Provide the Best Security and Are Seamless To Use
The best security investment is one that is easily deployed and used by employees. Using PKI, authentication is seamless to end-users and can be easily deployed to every employee device and system using automated tools.
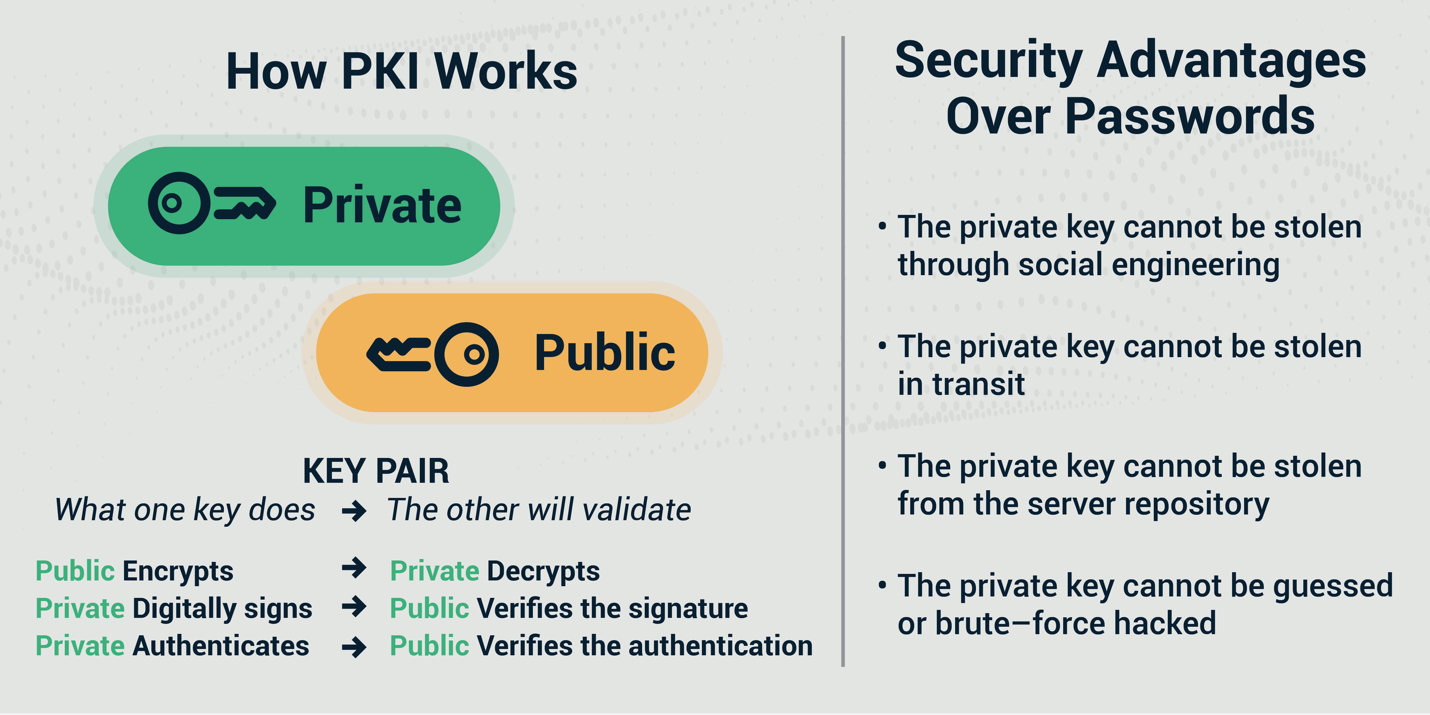
Figure 2. PKI-based certificates are easily deployed and used and provide the strongest form of identity authentication.
Especially for employees working from home, PKI-based certificates not only offer the strongest form of identity authentication but also simplify the process for employees to connect. The employee’s identity certificate key is stored directly in their computer, laptop, or mobile phone, meaning they are authenticated without requiring any action. Authentication can be easily deployed to every employee's device and system using automation tools, and the employee can simply access applications and start working. No tokens need to be shipped to employees. A streamlined, automated approach to securing employee devices and systems through PKI makes life easier for IT teams, helping them avoid the labor-intensive, technically demanding, and error-prone process of supporting passwords, MFA, or manually handling certificates for employees.
Passwords and MFA may have provided sufficient enterprise security in years past, but it’s clear that today’s threat landscape requires a more robust solution to secure the perimeter-less enterprise. As remote work continues to be widely adopted, and the enterprise ecosystem continues to expand, companies need Zero Trust authentication, powered by PKI, for the identity of people, devices, and systems.
Opinions expressed by DZone contributors are their own.

Comments