Top 3 Chatbot Security Vulnerabilities in 2022
In this article, we'll learn about the top 3 chatbot security vulnerabilities, possible attack vectors, and their defenses. We'll also discuss the risk mitigation best practices.
Join the DZone community and get the full member experience.
Join For FreeChatbots Are Here To Stay
Security Risks, Threats, and Vulnerabilities
The words risk, threat, and vulnerability are often confused or used interchangeably when reading about computer security, so let’s first clarify the terminology:-
Vulnerability refers to a weakness in your software (or hardware, or in your processes, or anything related). In other words, it’s a way hackers could find their way into and exploit your systems.
-
A threat exploits a vulnerability and can cause loss, damage, or destruction of an asset - threats exploit vulnerabilities.
-
Risk refers to the potential for lost, damaged, or destroyed assets - threats + vulnerability = risk!
Vulnerability 1: XSS - Cross-Site Scripting
A typical implementation of a chatbot user interface:- There is a chat window with an input box.
- Everything the user enters in the input box is mirrored in the chat window.
- Chatbot response is shown in the chat window.
The XSS vulnerability is in the second step — when entering text including malicious Javascript code, the XSS attack is fulfilled when the web browser is running the injected code:
<script>alert(document.cookie)</script>
Possible Attack Vector
For exploiting an XSS vulnerability the attacker has to trick the victim to send malicious input text. It can be done through one of the following ways:- An attacker tricks the victim to click a hyperlink pointing to the chatbot including some malicious code in the hyperlink
- The malicious code is injected into the website, reads the victims cookies, and sends it to the attacker without the victim even noticing
- The attacker can use those cookies to get access to the victim’s account on the company website
Defense
This vulnerability is actually easy to defend by validating and sanitizing user input, but still, we are seeing this happening over and over again.
Vulnerability 2: SQL Injection
A typical implementation of a task-oriented chatbot backend:- The user tells the chatbot some information item.
- The chatbot backend queries a data source for this information item.
- Based on the result a natural language response is generated and presented to the user.
With SQL Injection, the attacker tricks the chatbot backend to consider malicious content as part of the information item:
my order number is "1234; DELETE FROM ORDERS"
Possible Chatbot Attack Vector
When the attacker has personal access to the chatbot, an SQL injection is exploitable directly by the attacker (see example above), doing all kinds of SQL (or no-SQL) queries.Defense
Developers typically trust their tokenizers and entity extractors to defend against injection attacks. Additionally, simple regular expression checks of user input will in most cases close this vulnerability.Vulnerability 3: Denial of Service
Artificial intelligence requires high computing power, especially when deep learning as in state-of-the-art natural language understanding (NLU) algorithms is involved. The Denial of Service (DoS) attack is focused on making a resource unavailable for the purpose it was designed, and it is not hard to imagine that chatbots are more vulnerable to Denial of Service (DoS) attacks than the usual backends based on highly optimized database systems.Possible Chatbot Attack Vector
A typical DoS attack sends a large number of large requests to the chatbot to intentionally exhaust the available resources. It will happen that the computing resources are not available anymore to legitimate users.But there is an additional risk to consider: it is quite common for chatbot developers to use cloud-based services like IBM Watson or Google Dialogflow. Depending on the chosen plan there are usage limits and/or quotas in effect which can be exhausted pretty quickly.
Defense
The established methods for defending against Denial of Service attacks apply to chatbots as well.Mitigation Strategies
Apart from the defense strategies from above, there are general rules for mitigating the risks of system breaches.Software Developer Education
Naturally, the best way to defend against vulnerabilities is to not even let them occur in the first place. Software developers should get special training to consider system security as part of their day-to-day development routine. Establishing the mindset and processes in the development team is the first and most important step.Continuous Security Testing
Security testing should be part of your continuous testing pipeline. The earlier in the release timeline a security vulnerability is identified, the cheaper the fix is.
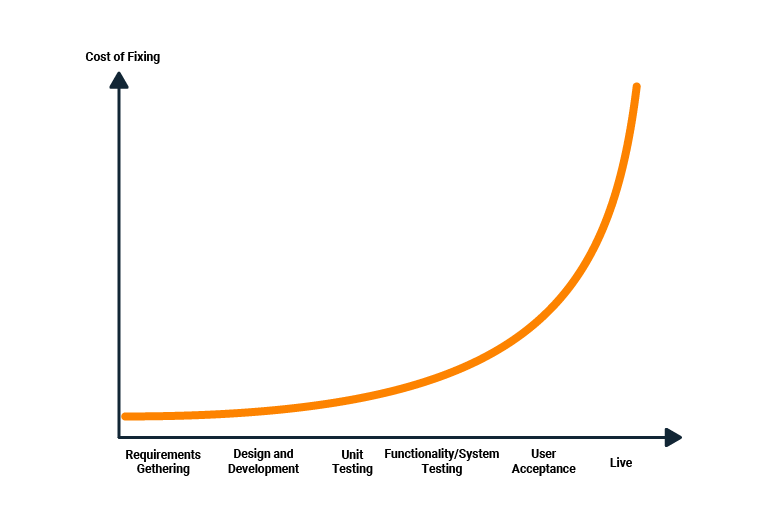
Basic tests based on the OWASP top 10 should be done on API level as well as on end-to-end level. Typically, defense against SQL Injections is tested best on API level (because of speed), while defense against XSS is tested best on the end-to-end level (because of Javascript execution).
Specialized tools like Botium help in setting up your continuous security testing pipeline for chatbots.
Conclusion
Chatbots open the same kind of vulnerabilities, threats, and risks as other customer-facing web applications. Due to the nature of chatbots, some vulnerabilities are more probable than others, but the well-established defense strategies will work for chatbots regardless.
Published at DZone with permission of Florian Treml. See the original article here.
Opinions expressed by DZone contributors are their own.


Comments