A Practical Approach to Vulnerability Management: Building an Effective Pipeline
This article aims to provide a practical approach to vulnerability management by proposing a pipeline that can help manage vulnerabilities at scale.
Join the DZone community and get the full member experience.
Join For FreeVulnerability management has become a critical aspect of application security. The consequences of inadequate vulnerability management can be severe, as demonstrated by several high-profile breaches. In 2021, the Equifax data breach, caused by an unpatched Apache Struts vulnerability (CVE-2017-5638), resulted in a $700 million settlement after exposing sensitive data of 147 million people.
More recently, in 2022, the compromise of LastPass's development environment through an unpatched Plex vulnerability led to the theft of password vaults, causing significant reputational damage and customer exodus. The 2021 exploitation of the Log4Shell vulnerability (CVE-2021-44228) affected companies like Microsoft, Amazon, and Apple, with estimated remediation costs exceeding $10 billion globally.
The importance of investing in vulnerability management is underscored by several authoritative studies:
- IBM's Cost of a Data Breach Report reveals that organizations with fully deployed security automation (including vulnerability management) experienced breach costs that were on average $3.05 million lower than those without automated security processes.
- Gartner's research on vulnerability management best practices suggests that organizations that take a risk-based approach experience 80% fewer breaches than those that rely solely on periodic scanning.
- The Ponemon Institute's "State of Vulnerability Management" study revealed that organizations taking more than 30 days to patch critical vulnerabilities are 50% more likely to be breached.
- NIST's National Vulnerability Database (NVD) statistics show a continuous increase in new vulnerabilities, highlighting the growing need for robust vulnerability management.
Despite these cautionary tales, many organizations still struggle with implementing an effective vulnerability management process that scales with their development lifecycle. A VMware report revealed that 78% of surveyed organizations encountered at least two ransomware attacks in 2021, with unpatched vulnerabilities being the primary attack vector. This article presents a practical approach to building and automating a vulnerability management pipeline that identifies security issues and helps prioritize and remediate them effectively.
Understanding Modern Vulnerability Management
Modern vulnerability management goes beyond simple scanning and patching. It requires a systematic approach that integrates seamlessly with your development lifecycle, providing continuous monitoring, assessment, and remediation of security vulnerabilities that can keep up with the speed of new vulnerabilities popping up. An effective vulnerability management pipeline should address three key aspects:
- Continuous vulnerability detection across all layers of your application
- Smart prioritization based on risk assessment
- Automated remediation where possible
Building the Vulnerability Management Pipeline
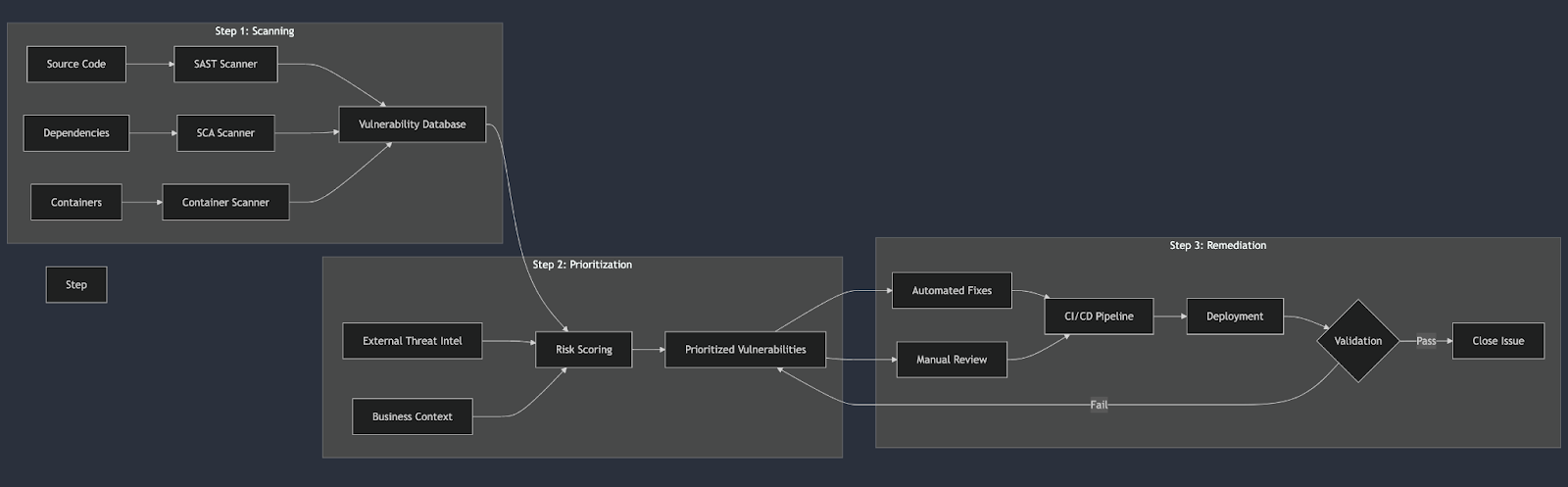
Step 1: Comprehensive Scanning Strategy
Key Points
- Implement multi-layer scanning across source code, dependencies, and containers.
- Configure scanners for automated execution during the CI/CD pipeline.
- Ensure comprehensive coverage with both SAST and SCA tools.
The foundation of any vulnerability management pipeline is a robust scanning strategy that encompasses multiple layers of your application stack. Source code scanning forms the first line of defense, where Static Application Security Testing (SAST) tools like SonarQube, Checkmarx, or Snyk analyze your codebase during pull requests. These tools should be configured for incremental scanning to reduce scan times while maintaining effectiveness, examining both security vulnerabilities and code quality issues that could lead to security problems.
Dependency scanning is equally crucial in modern applications that rely heavily on third-party packages. Software Composition Analysis (SCA) tools provide insights into both direct and transitive dependencies, examining the packages you explicitly include and their dependencies. This comprehensive approach helps identify vulnerable components that might be several layers deep in your dependency tree. Modern SCA tools can also assist with license compliance checking, providing an additional layer of risk management.
Container security cannot be overlooked in today's cloud-native environments. Implementing container image scanning in your CI/CD pipeline ensures that vulnerabilities in base images and added layers are detected before deployment. Tools like Trivy, Aqua Security, or Snyk Container can identify known vulnerabilities in both the operating system packages and application dependencies within your containers.
Step 2: Smart Prioritization Framework
Key Points
- Integrate external threat intelligence with internal risk metrics.
- Focus on exploitability and business impact rather than just CVSS scores.
- Implement custom scoring based on your organization's specific context.
With the increasing volume of detected vulnerabilities, effective prioritization becomes crucial for maintaining security without overwhelming development teams. A smart prioritization framework begins with external threat intelligence integration, incorporating CVE scores and CVSS metrics while considering real-world exploit attempts. This data should be continuously updated to reflect the latest threat landscape and exploit availability.
Risk-based scoring forms the core of the prioritization framework. This involves evaluating the business impact of affected components and their exposure level, whether they're internal- or external-facing. The framework should account for compensating controls and calculate custom risk scores based on multiple factors. These include the CVSS base score, asset criticality, exploit availability, patch availability, and business context. This comprehensive scoring helps security teams focus on vulnerabilities that pose the greatest real-world risk to their organization.
Step 3: Automated Remediation
Key Points
- Deploy automated dependency update tools with testing safeguards.
- Implement automated patch management workflows with rollback capabilities.
- Integrate security fixes into existing development processes.
Automation is essential for scaling vulnerability management effectively across large codebases and organizations. Tools like Dependabot or Renovate can implement automated dependency updates, automatically creating pull requests for non-breaking updates. These tools should be configured to run automated tests to validate updates and implement gradual rollout strategies for critical dependencies.
Patch management automation goes beyond simple updates. It involves creating automated workflows for patch application, testing, and rollback procedures. This automation should integrate seamlessly with your development workflow, automatically creating branches for fixes and managing the entire lifecycle of security updates. Integration with issue tracking systems ensures proper visibility and tracking of security issues, with automated ticket creation and assignment based on code ownership.
Key Metrics for Success
Before concluding, it's important to establish metrics that indicate the effectiveness of your vulnerability management pipeline:
- Mean Time to Detect (MTTD): Track how quickly new vulnerabilities are identified.
- Mean Time to Remediate (MTTR): Measure the average time from detection to fix.
- Fix Rate: Monitor the percentage of vulnerabilities remediated within SLA.
- Risk Reduction: Track the reduction in overall risk score over time.
Conclusion
Building an effective vulnerability management pipeline is no longer optional in today's threat landscape. The approach outlined in this article — implementing comprehensive scanning, smart prioritization, and automated remediation — provides a framework that organizations can adapt to their specific needs. The key to success lies in treating vulnerability management not as a periodic task but as a continuous process integrated into the development lifecycle.
Organizations must recognize that the cost of implementing a robust vulnerability management pipeline is significantly lower than the potential impact of a security breach. As demonstrated by the real-world examples and industry studies cited earlier, unpatched vulnerabilities continue to be a primary attack vector, leading to substantial financial and reputational damages.
Getting Started
To begin improving your vulnerability management process:
- Start with an assessment of your current security posture and tooling
- Implement basic scanning and prioritization before moving to automation
- Focus on quick wins by addressing high-risk, easily fixable vulnerabilities first
- Gradually expand coverage and automation as processes mature
Remember that vulnerability management is not just a security team responsibility — it requires collaboration between security, development, and operations teams. By following the practical approach outlined in this article and maintaining a continuous focus on improvement, organizations can significantly reduce their security risk while maintaining development velocity.
The future of vulnerability management lies in further automation, better integration with development workflows, and more sophisticated prioritization using AI and machine learning. However, the fundamental principles outlined in this article will remain crucial for building a strong security foundation.
Opinions expressed by DZone contributors are their own.

Comments