Survey Reveals Rapid Growth in Kubernetes Usage, Security Still a Concern
What happens when you gather 400 DevOps, Security, and Product professionals in a room?
Join the DZone community and get the full member experience.
Join For Free
The rapid adoption of container technology, DevOps practices and principals, microservices application architectures, and the rise of Kubernetes as the de facto standard for container orchestration are the key drivers of modern digital transformation. Whether an application is built in the cloud, on-premises, or in hybrid environments using container technologies, or it's being ported to a containerized infrastructure, containerization has clear advantages in terms of scalability, portability, and continuous development and improvement.
In a medium article, Tinder's Engineering Team recently announced their move to Kubernetes to solve scale and stability challenges. Twitter is another company that has announced their own migration from Mesos to Kubernetes. New York Times, Reddit, Airbnb, and Pintrest are just a few more examples.
While the reasons behind such a rapid adoption of Kubernetes has been well-documented, security issues remain one of the biggest concerns for organizations.
When it comes to containers and Kubernetes, the security mission has remained the same — harden your environment during build stage and detect and remediate threats during runtime — the nature of containerization requires new security tooling. And when container and Kubernetes security is ignored, companies have found themselves in the headlines for all the wrong reasons. Just ask Tesla.
To better understand the market trends in container and Kubernetes adoption and how organizations are managing their security obligations, we conducted a survey of over 200 IT security and operations decision-makers in November of 2018. We, at StackRox, recently repeated the same survey across nearly 400 individuals in Security, DevOps, Product, and Engineering teams to gain additional insights into how organizations are adopting containers and Kubernetes and how their security concerns have evolved.
The results are in close alignment with how Gartner sees the market developing: by 2022 more than 75% of global organizations will be running containerized applications in production, a significant increase from fewer than 30% today.
Kubernetes Experiences 50% Growth in Just 6 Months
Originally a brainchild of Google — and inspired by the Borg and Omega projects — Kubernetes was open-sourced in 2014 as an all-in-one platform for automating deployment, scaling, and management of containerized applications. Google partnered with the Linux Foundation to form the Cloud Native Computing Foundation (CNCF) that today manages the Kubernetes open-source project, along with several other projects.
Most people still remember the fanbase frenzy that followed the launch of Niantic's Pokémon Go in 2016. In an early sign of Kubernetes going mainstream, Niantic built their massively popular game in Kubernetes and deployed it in Google Container Engine. At launch, the game experienced scale and stability issues caused by tremenduous user interest in the U.S — the number of active users ended up being 50x the original estimation, and 10x the prediction for the worst-case scenario. By leveraging the inherent scalability advantages of Kubernetes, Pokémon Go was successfully launched in Japan two weeks later despite traffic tripling what was experienced during the U.S launch.
By 2017, both AWS and Azure had announced their own managed flavors of Kubernetes (EKS and AKS respectively). Since then, Kubernetes usage has taken off. When we first conducted the survey in November of 2018, 57% of respondents were using Kubernetes. By mid-2019, the percentage of survey respondents who said they use Kubernetes as their orchestrator grew from 57% to 86% – a 50% increase.
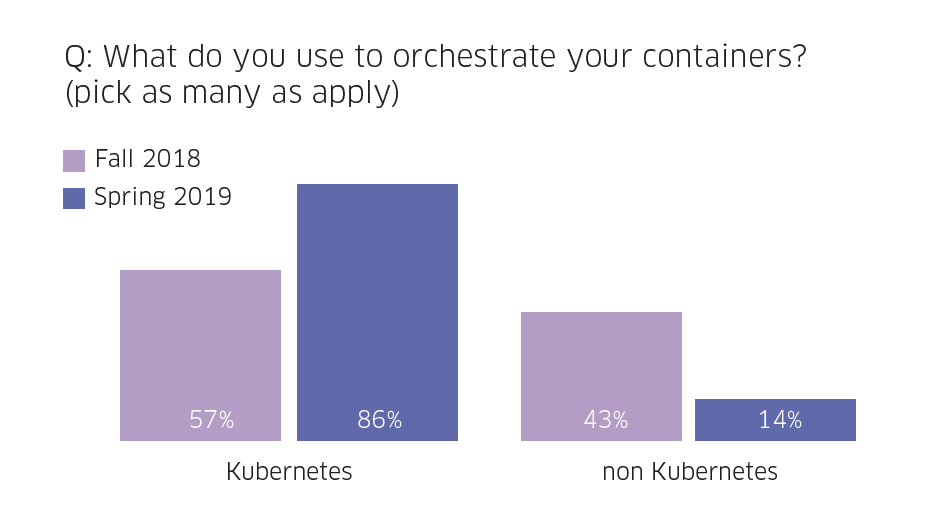
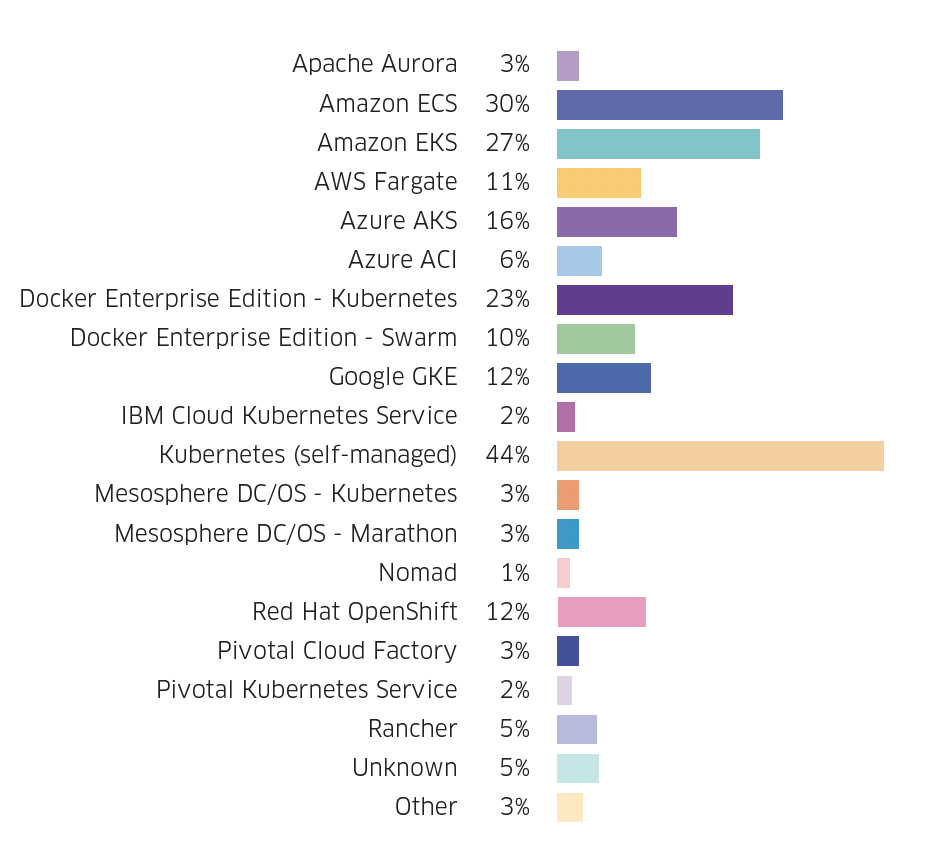
Over the last few years, while several cloud and infrastructure providers have started to offer their own managed Kubernetes services including Google (GKE), Amazon (EKS), Microsoft (AKS), Red Hat (Red Hat OpenShift), and Docker Enterprise Edition - Kubernetes, a large portion of Kubernetes users prefer to self-manage their clusters. One explanation could be that self-managed Kubernetes allows for greater flexibility in porting an existing Kubernetes application to another environment.
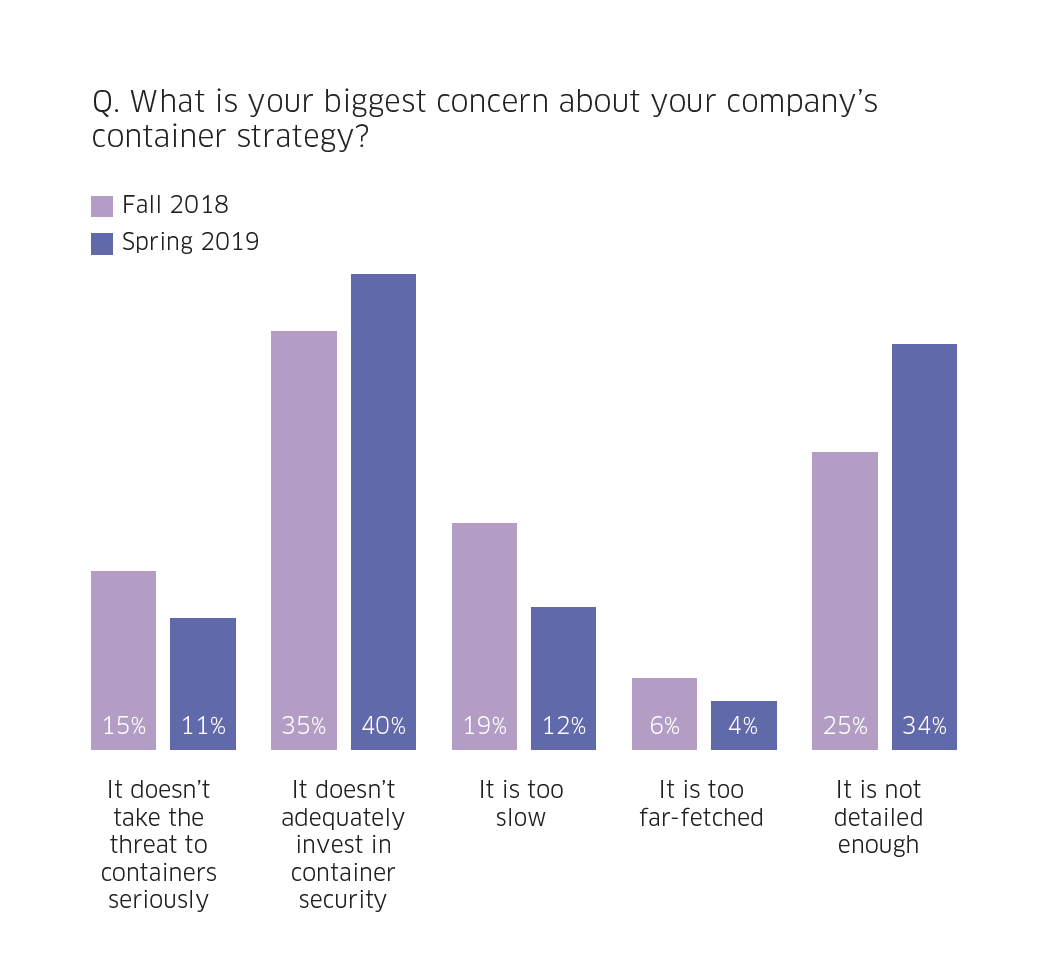
Container and Kubernetes Security Concerns on The Rise
According to a recent Gartner report, security concerns continue to be one of the primary constraints for using containers and Kubernetes in production. 2019 saw the discovery of several high-severity container and Kubernetes vulnerabilities, including the runC vuln, a K8s privilege escalation flaw, a DoS vuln, and several other vulns that were announced earlier this month as part a CNCF audit.
Most respondents identify inadequate investment in security as their biggest concern about their company’s container strategy. Migrating to a containerized/microservices architecture introduces several new container and Kubernetes security considerations and risks for the cloud-native stack, and existing security tooling isn’t suitable to address them. For example, containers talk to each other and to other endpoints in order to achieve their goal, so network segmentation and firewalling is completely different in a containerized environment. Further complicating container and Kubernetes security is the fact that unlike traditional waterfall method of application development, modern app dev methodologies rely on continuous integration and continuous delivery (CI/CD) where security controls must be deeply embedded in the CI/CD pipeline for it to be effective.
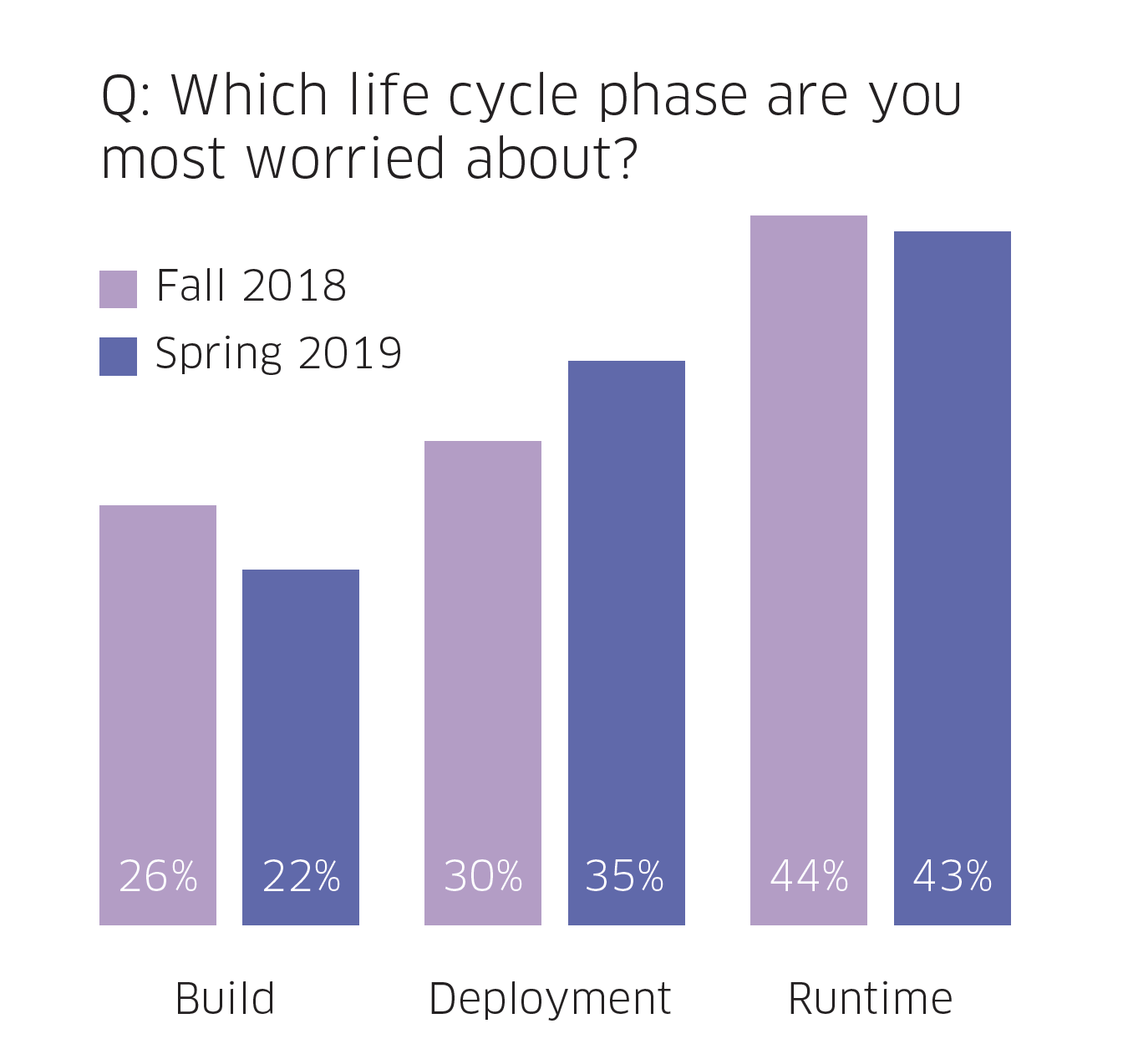
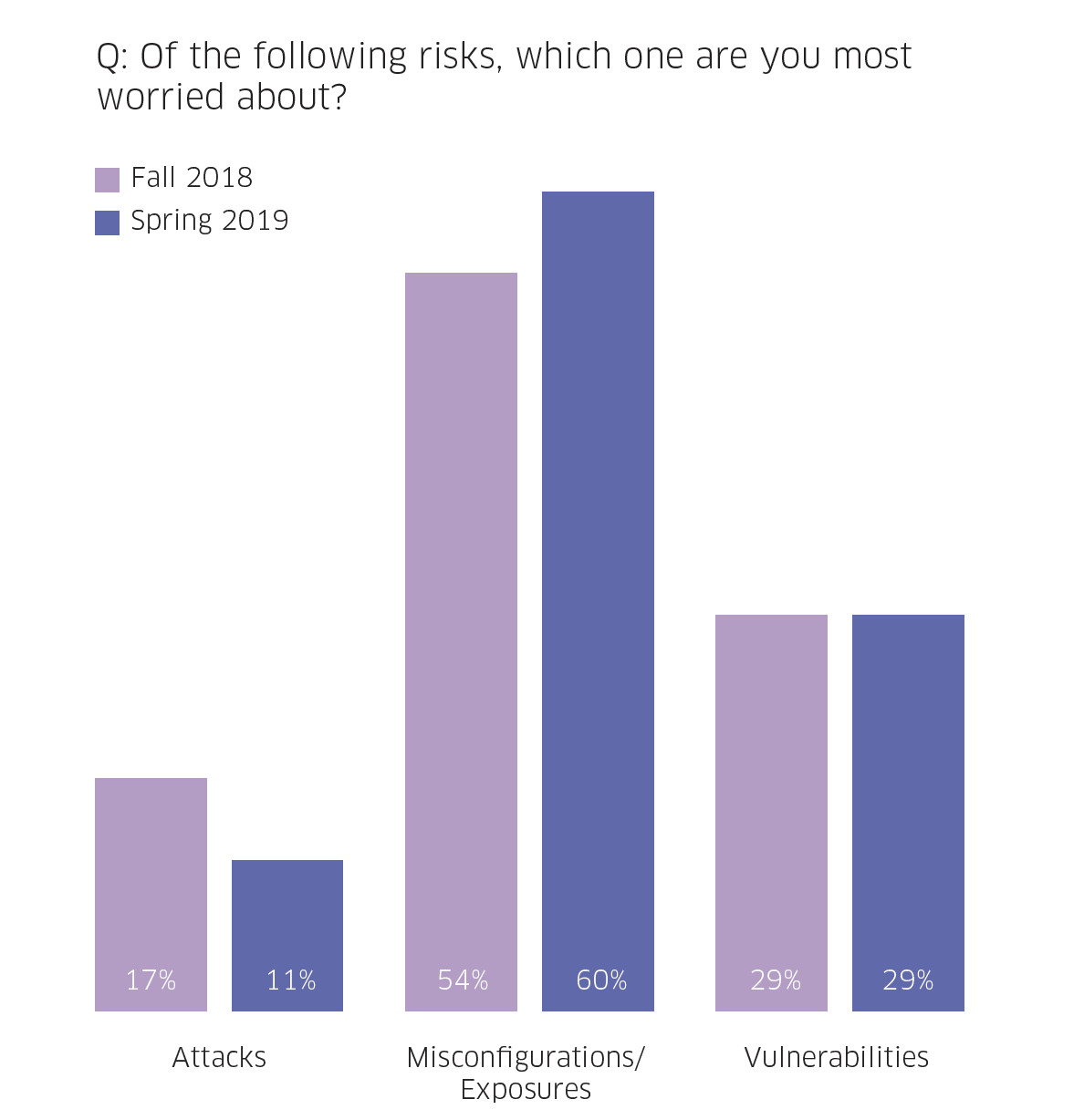
Runtime was once again the container life cycle phase that respondents were most concerned about. At the same time, organizations are beginning to realize that runtime security failures are caused by missed security best practices in the build and deploy phases. For that reason, more than half (57%) of survey respondents are more worried about the build and deploy phases, with misconfigurations and vulnerabilities being areas that pose the greatest risk.
Containers and Kubernetes Are Deployed in All Environments
One of the interesting findings of the survey report was how diverse container and Kubernetes environments have become. While 70% of respondents run at least some of their containers on-premises, 75% of those running on-premises are also running some workloads in the cloud.
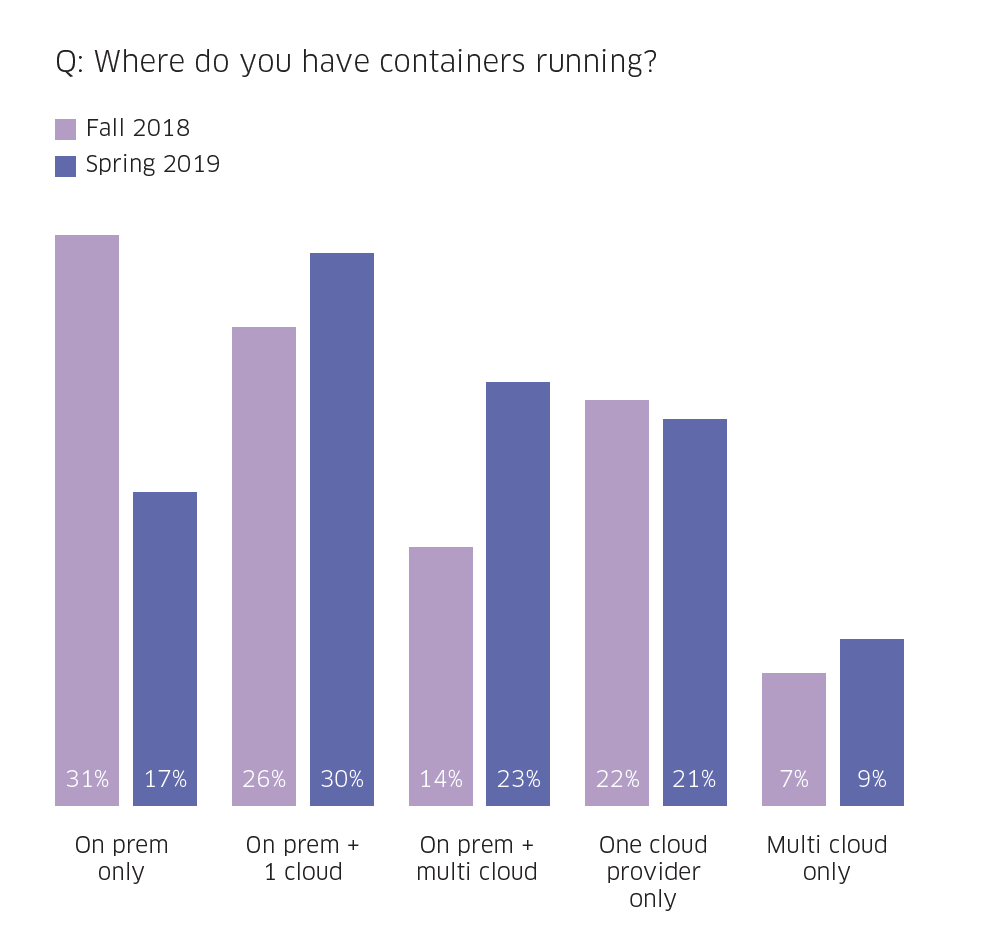
Our data reveals that hybrid mode is the preferred mode of deployment, with more than half of respondents (53%) running in hybrid mode compared to 40% at the end of 2018. This trend has come at the expense of on-premises only deployments, with the percentage of organizations running containers only on-premises dropping nearly in half (from 31% to just 17%), and cloud-only deployments remaining the same.
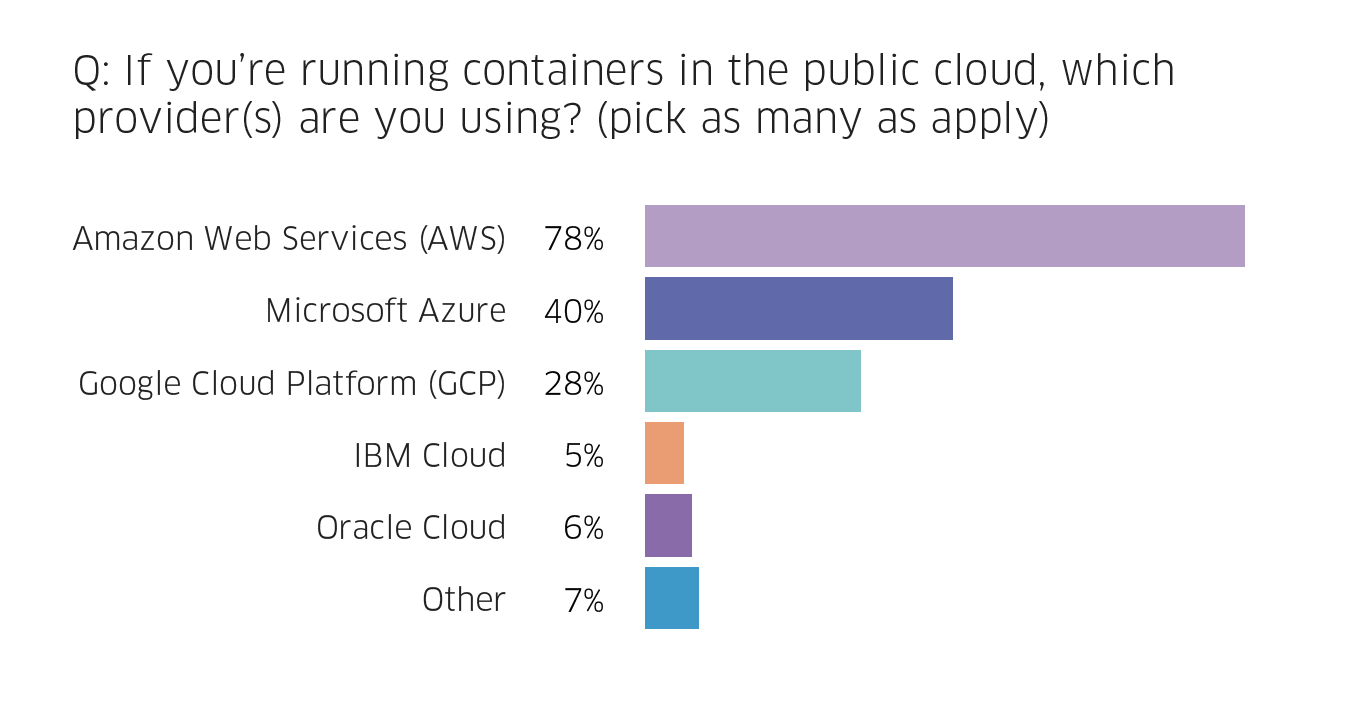
Not surprisingly, the same big three continue their market dominance in container deployments, with AWS leading the pack, followed by Azure. Google comes in third but has gained considerable market share, growing from 18% to 28% over six months.
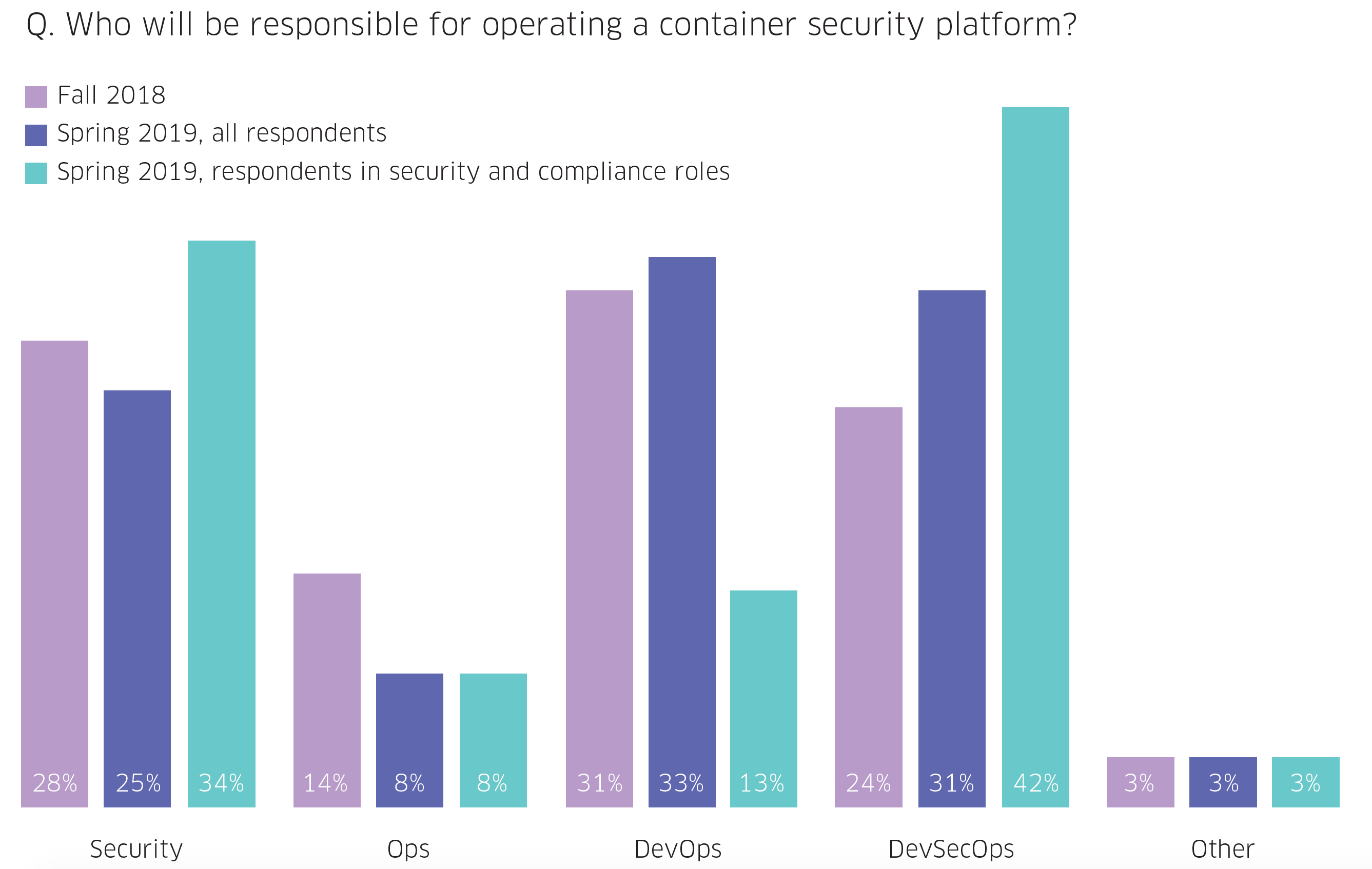
DevSecOps – More than Just a Trendy Word
While few people have an official title of DevSecOps, it's clear that this role is growing in prominence, especially within Security Teams. When respondents were asked who should be responsible for container and Kubernetes security projects, there was a close-to-even distribution between Security (25%), DevOps (33%), and DevSecOps (31%). Interestingly, however, when we isolated responses from individuals in security/compliance roles, DevSecOps (42%) was identified as the responsible party for managing container security.
Final Thoughts
Containerization is not slowing down. The advantages of leveraging containers and Kubernetes—allowing engineers and DevOps teams to move fast, deploy software efficiently, and operate at unprecedented scale—is clearly overcoming the anxiety of security concerns.
Organizations shouldn’t treat security as an afterthought. Unlocking the benefits of cloud-native technologies while maintaining strong security for mission critical application development infrastructure requires protecting the full container life cycle – across build, deploy and runtime phases.
Further Reading
Opinions expressed by DZone contributors are their own.

Comments