The Role of Kubernetes Security in the Immediate Future of Computing
As the leading container orchestration tool in the cloud infrastructure today, Kubernetes security must be taken seriously when using container infrastructure.
Join the DZone community and get the full member experience.
Join For FreeWith an almost 25% share, Kubernetes is only second to Docker as the indisputable leader in the global containerization market. Over the past few years, the container management market has grown rapidly, from almost half a billion dollars in 2020 to a forecasted one billion dollars in 2024.
However, security issues persist as Kubernetes plays an increasingly prominent role in public cloud development. According to a report, as of 2023, 38% of respondents believe that security investment in containerized operations is inadequate. That is a 7% increase from the 2022 edition of the report.
In addition, security concerns have led to 67% of leaders slowing down their cloud-native adoption process. So, despite cloud-native technologies enabling flexibility, speed, and adaptability, maintaining reliability remains a major hurdle to cross.
Hence, in the immediate future of cloud computing and on Kubernetes specifically, there must be a renewed focus on security, especially as Kubernetes solutions get increasingly deployed in AI algorithms and other innovative solutions.
Kubernetes Security Concerns in 2024 and Beyond
Kubernetes does possess built-in security features, but more is needed for robust protection. After all, the entire goal of containerization is customization, which means users must be able to adapt their own security needs and requirements. These needs grow and become more complex as the organization develops.
Here are four Kubernetes security concerns in 2024:
Misconfiguration
According to IBM’s Cost of a Data Breach Report 2023, misconfiguration remains one of the leading causes of cloud data breaches. Although it sounds like such a simple problem, running container environments comes with great responsibility, which makes it a persistent threat.
One common vulnerability occurs when containers grant more permissions than required, granting privileges to shadow users that can be exploited by malicious actors.
To avoid misconfiguration vulnerabilities, there must be continuous monitoring and scanning of all activity logs across containers to ensure that role access is granted according to organizational policy.
Malicious activities can often go undetected due to insufficient logging and monitoring, even in cases when RBAC fails. So, logging should also be centralized, and regular audits should be conducted from time to time.
AI and ML Integration
This is the period when AI technologies are permeating everything we do, and the potential of AI-powered Kubernetes is being realized. Deploying AI and ML techniques in Kubernetes applications enables smarter application deployment and predictive analytics.
It also delivers enhanced security, especially via automation, which is a way to combat the persistent threat of misconfiguration. At the same time, introducing AI to your Kubernetes environment can come with challenges.
One is the black box problem; many users deploying Kubernetes are not fully aware of how the system works, and thus remain oblivious of possible threats.
Organizations must review their risk assessment, including AI as an additional, and primary factor. It’s always better to err on the side of caution, especially since AI is a double-edged sword.
Zero Trust Security
Zero Trust security is based on a combination of principles including multi-factor authentication, continuous monitoring, role-based access control (RBAC), and the principle of least privilege.
These are features that have seen greater emphasis over the years, as traditional implicit trust-based approaches have faded. Zero Trust has also emerged as a major factor in securing Kubernetes environments, and this trend will continue in 2024.
According to Gartner’s 2023 Hype Cycle for Zero Trust Networking, container security is one of the technologies along the slope of enlightenment.
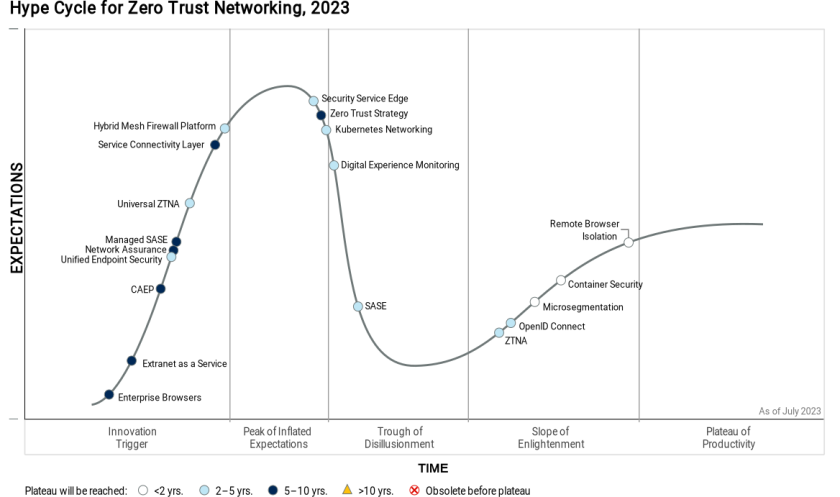
Yet, as Gartner itself admits, progress in implementing zero trust has proven slower than expected, predicting that by 2026, only 10% of large organizations will have a mature and measurable zero trust program in place.
CISOs need to take note of these trends and set realistic expectations to implement various principles that make up the zero-trust architecture.
Regulatory Compliance
With governments across the world recently introducing new standards and frameworks for enforcing data safety on behalf of users, data privacy and security have come to the forefront of cybersecurity discussions in recent years.
As a Kubernetes user, your infrastructure and deployment, of course, must align with relevant regulatory requirements and security standards, particularly with a focus on protecting sensitive data.
A major consideration for Kubernetes compliance is access control and authorization policies. Determining who has access to what data requires clearly defined policies and automated authentication mechanisms.
In addition, there must be centralized monitoring of activities in the environment to detect security incidents and investigate compliance violations. With all these in place, an incident response plan can be as effective as it needs to be, ensuring that nothing escapes notice and quick action.
Kubernetes Security Must Be Taken Seriously
As the leading container orchestration tool in cloud infrastructure today, Kubernetes has a critical role to play in the future of computing. So, its security must be taken seriously.
Kubernetes doesn’t have the most secure-by-default architecture, and responsibility for securing systems must be taken if individual users (organizations) are using container infrastructure.
Furthermore, without sufficient defenses, it becomes impossible to maximize the benefits that Kubernetes offers, because the more popular it becomes, the greater the security threats.
Opinions expressed by DZone contributors are their own.

Comments