Security at the Onset: Stabilizing CSPM and DevSecOps
Proactively integrating CSPM with DevSecOps strengthens security by continuously monitoring and addressing vulnerabilities from development to deployment.
Join the DZone community and get the full member experience.
Join For FreeThe time for rapid technology development and cloud computing is perhaps the most sensitive time when security issues are of great importance. It is here that security will have to be injected into a process right from the beginning — be it software development or cloud infrastructure deployment. Two concepts that are very influential in doing so are CSPM and DevSecOps.
Don't worry if these terms seem complicated — all they really mean is the inclusion of security within how companies build and manage their cloud environments and software pipelines.
So, let's break down what CSPM and DevSecOps are, how they fit together, and how they can assist with keeping systems secure in this article.
What Is Cloud Security Posture Management?
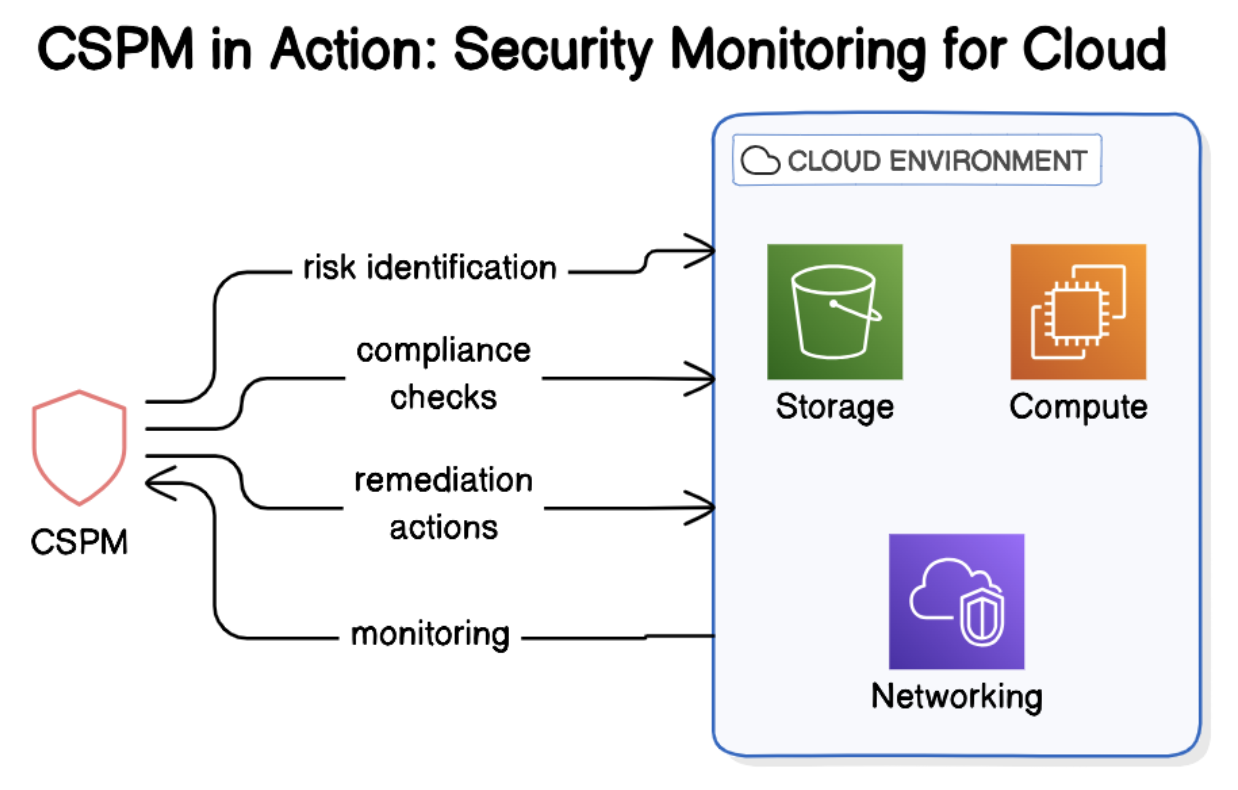
Imagine that there is this huge cloud environment, like a giant digital warehouse, containing data, services, and software. Keeping everything in such a huge environment secure is very difficult. It is here that companies find Cloud Security Posture Management or CSPM. CSPM assists the companies in the following.
- Track everything: There is now a bird's eye view of an entire cloud infrastructure for companies, which enables them to easily point out something that may be risky, such as misconfiguration or vulnerability.
- Being compliant: CSPM tools support the idea that everything in the cloud is governed whether it is in line with company policy or with regulatory compliance such as GDPR and HIPAA.
- Remediate issues in record time: If a problem arises, it will either automatically remediate the issue or suggest remediation.
CSPM acts like a thorough security guard in the cloud, ever vigilant and watchful, ensuring everything stays safe and sound.
Understanding DevSecOps
We'll introduce DevSecOps in simple terms. As the name suggests, we're describing an intersection of three core domains:
- Dev: The activity of writing and testing software
- Sec: The protection of software and infrastructure against malicious activities
- Ops: Ensuring that the software works well and reliably once it goes live
Security, before DevSecOps, tended to be an afterthought added simply at the very end of development. This meant that it had delays and would make the system more vulnerable, but with DevSecOps, security is actually integrated all the way through from when you first write a line of code to running the software in production.
Key Benefits of DevSecOps
- Catches issues early: Security checks happen throughout development, catching issues while they are still small problems rather than waiting until they develop into major issues.
- Delivers fast: Without security, it only tends to the end, so software will come faster and faster.
- Improves collaboration: Developers, security experts, and operations teams interact with each other more closely to minimize misunderstandings and delays.
How Does CSPM Relate to DevSecOps?
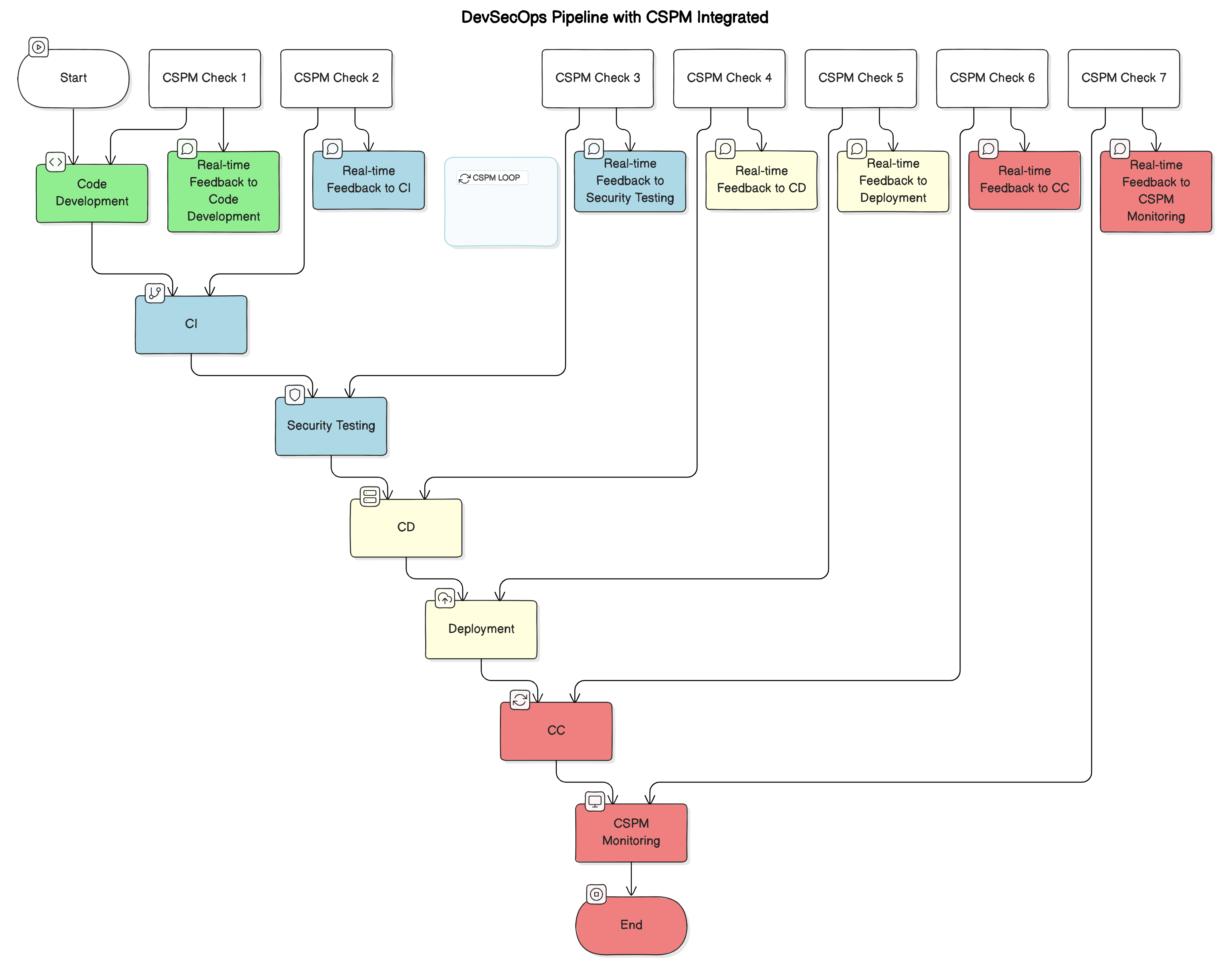
CSPM tools serve as the security guard for your cloud. When infused into DevSecOps, they ensure that every change in the cloud or during development is made with the best security practices from day one. In a nutshell, here is the integration of CSPM and DevSecOps:
- Continuous security monitoring: These CSPM tools continuously scan into their cloud environment for risk-readiness. Integration of this into the DevSecOps pipeline ensures security checks occur each and every time new infrastructure is deployed or updated.
- Automated compliance checks: As more features are added to their cloud infrastructure, CSPM automatically scans whether the concerned infrastructure is compliant with security rules and industry standards in real time.
- Infrastructure as Code security: DevSecOps teams use tools like Terraform to IaC, or automatically deploy cloud infrastructure. CSPM can scan the IaC templates before anything is live to ensure that configurations are secure from the get-go.
The below diagram shows stages of DevSecOps (development, testing, deployment) with continuous CSPM monitoring at each stage.
Empowering DevSecOps With CSPM
Here's why CSPM is so powerful when added to DevSecOps pipelines:
- Proactive security: The security solution will be proactive scanning continuously for risks. You don't have to wait till something breaks; you fix issues before they become a problem
- Speeder compliance: Instead of waiting for time to run checks through, CSPM automates checks to ensure newly deployed software and applications are meeting the security standards at an instance.
- Higher transparency: The teams of DevSecOps have visibility into all types of cloud assets, their configurations, and the risks. It is such transparency that it makes it easier to manage the cloud environment.
- Lesser manual patches: Some of the CSPM tools also include an auto-fix feature for most common security issues which saves time and effort for your team.
Common Challenges With DevSecOps in Implementing CSPM
Even though the benefits are clearly visible, implementing CSPM in DevSecOps pipelines is not very straightforward sometimes. Some of the frequent problems arising in this process are listed below.
- Complexity of tools: DevSecOps involves a large number of tools for development and deployment purposes. Hence, adding on the CSPM sometimes complicates things if not done very well.
- Too many alerts: Some of the tools used in CSPM often send too many notifications, which results in "alert fatigue." Thus, the alerts must be fine-tuned in order to make them meaningful.
- Team collaboration: DevSecOps is truly effective if and only if proper communication between development, security, and operations teams takes place; otherwise, implementing CSPM is going to be pretty challenging.
- Multi-cloud setups: In most organizations, a multi-cloud environment is implemented. Ensuring consistency in security across multiple clouds might be challenging, but that's exactly what CSPM tools are built for, given the right configurations in place.
Infrastructure as Code (IaC) and Pre-Certified Modules
The role of CSPM in IaC tools like Terraform is pretty important by scanning the code that expresses the cloud infrastructure. In one practical way, making sure that the deployment is secured can make use of pre-certified modules. Here again, the modules come with baked-in security best practices that enable DevSecOps to build environments from scratch securely. Compliance modules are only deployed here, and they will be continuously monitored.
CSPM Tools
Here’s a list of CSPM tools:
- IBM Cloud Security and Compliance Center (SCC) - Provides continuous compliance monitoring, risk management, and policy enforcement for IBM Cloud environments with in-depth audit capabilities
- Palo Alto Networks Prisma Cloud - Offers multi-cloud security posture management with threat detection, visibility, and automated compliance checks
- AWS Security Hub - A native AWS service that aggregates security alerts and enables compliance checks across AWS accounts
- Microsoft Defender for Cloud - Secures workloads across Azure and hybrid cloud environments by assessing security posture and providing real-time threat protection
- Check Point CloudGuard - Provides posture management, threat intelligence, and automated compliance enforcement for cloud-native applications and multi-cloud environments
- Aqua Security - Combines CSPM with container and Kubernetes security, offering end-to-end visibility and risk management for cloud infrastructures
- Wiz - A fast-growing CSPM solution offering deep security insights, prioritizing vulnerabilities and compliance risks across cloud platforms
- Orca Security - An agentless CSPM tool that provides real-time risk assessment and cloud workload protection for multiple cloud environments
CSPM and Beyond
In addition to CSPM, there are several other cloud security tools and frameworks designed to ensure the safety, compliance, and efficiency of cloud environments. Here are some of the key tools commonly used alongside or as alternatives to CSPM:
- Cloud Workload Protection Platform (CWPP)
- Secures cloud-based workloads, including virtual machines (VMs), containers, and serverless functions
- Includes vulnerability management, system integrity monitoring, runtime protection, and network segmentation
- Cloud Access Security Broker (CASB)
- Acts as a gatekeeper between users and cloud service providers, ensuring secure access to cloud services
- Provides visibility, compliance, data security, and threat protection for cloud applications.
- Cloud Infrastructure Entitlement Management (CIEM)
- Focuses on managing and securing permissions and access to cloud resources
- Helps with least privilege enforcement, identity governance, and mitigating risks of misconfigurations
- Cloud-Native Application Protection Platform (CNAPP)
- Provides a comprehensive suite that integrates CSPM, CWPP, and more to secure applications across development and production
- Encompasses vulnerability management, runtime security, and compliance for cloud-native applications like containers and Kubernetes
- Security Information and Event Management (SIEM)
- Centralized logging and analysis of security events from cloud infrastructure and applications
- Enables threat detection, incident response, and compliance reporting
- Runtime Application Self-Protection (RASP)
- Provides real-time protection for applications while they are running in the cloud
- Detects and mitigates attacks by monitoring the behavior of an application and blocking malicious activity
- Security Orchestration, Automation, and Response (SOAR)
- Automates security operations and workflows to reduce manual effort in threat detection and response. Coordinates multiple security tools to streamline threat management and incident response.
Conclusion: The Force of Security From the Start
This enables companies to build secure, compliant, and fast cloud environments. Companies are able to move fast while staying ahead of security threats by integrating security throughout every stage of development and cloud management. Tools like CSPM make sure no cloud misconfiguration slips through and with this approach, DevSecOps carries out this process — that of being collaborative and fast. The integration of security is essentially a core part of every decision.
If you're into cloud infrastructure, think about what kinds of such tools and practices you might bring into your processes. By putting security into your applications at the beginning, you save time, decrease risks, and give a more solid environment for your applications.
Opinions expressed by DZone contributors are their own.

Comments