Security Matters: Vulnerability Scanning Done Right!
Security has become the priority in every company these days. Let's see how vulnerability scanning is done the right way.
Join the DZone community and get the full member experience.
Join For FreeEvery company is a software company today, and things change drastically in the software industry. Therefore, organizations are required to be more agile to cope with the ever happening changes in the industry. While DevOps methodologies focused on software delivery speed, security left behind gave rise to so many security threats and exploits.
That is where we saw a movement of DevSecOps - security being the default and foremost aspect of the SDLC rather than an afterthought. When not appropriately handled, security vulnerabilities can ruin the organization's overall reputation, and hence it is important to understand how security vulnerabilities impact your organization.
Today, we will see what security vulnerabilities are and how to tackle them.
What is a security vulnerability?
Any software can have vulnerabilities, which can be introduced via mistakes done by developers creating the code or via dependencies that expose the software to vulnerabilities in external packages such as open-source libraries.
There are two types of vulnerabilities that developers should usually look for - Known vulnerabilities and unknown vulnerabilities. Uknown vulnerabilities, which, if found by attackers, may be exploited by them without being noticed for a long time and pose a huge security risk. On the other hand, Known vulnerabilities, that are important for developers to address, but the challenge is in getting an accurate list of all vulnerabilities based on the software composition, including all layers of dependencies.
A vulnerability in the cybersecurity world is considered a weakness that provides an opportunity for attackers to steal data or damage systems. Cyberattacks can have different aims, such as stealing customers' sensitive data, the tactic of injecting malicious code, blocking security cameras from capturing video, stopping critical infrastructure, hijacking the systems for other uses such as mining cryptocurrency, etc. Data breaches and supply chain attacks have been common in this space that cost millions of dollars to the company.
MITRE registers a public list of disclosed vulnerabilities in software packages. Each vulnerability is tracked as a Common Vulnerability Exposure (CVE) and is assigned a Common Vulnerability Scoring System (CVSS) score that indicates the possible risk for any organization exposed to this vulnerability. The central listing of these known CVEs is commonly used as a directory for vulnerability scanners for public use. Whereas, many companies exist that go beyond this and/or have their own data as well.
Vulnerability scanning in practice
The adoption of vulnerability scanning practices depend on factors such as compliance standards, policies, and security program objectives. Vulnerability scanning is increasingly becoming common practice or rather a requirement due to compliance requirements, policies, and security programs. Therefore, vulnerability scanning must be added to their security program as a DevSecOps best practice for any company looking to maintain high security standards.
Vulnerability scans are usually mixed or confused with penetration testing, yet they serve completely distinct purposes. In the security space, vulnerability scanning is an automated process intended to point out issues on a broad range of systems at high frequency. You will be able to detect security issues related to code, missing patches, licensing violations, etc.
When it comes to vulnerability scanning, there are various ways in which they can be done. The most common type of vulnerability scan is the automated scan that happens through the CI/CD pipeline where an automated software/tool automatically detects any problems and then produces data to indicate what needs fixing or updating.
Many software security vulnerabilities can be discovered by scanning for commonly exploited techniques such as buffer overflows and path traversals. Yet when it comes to identifying patches and updates, assessment with these techniques requires specialized skills and data sets that are rarely common across organizations. Hence, most companies use automated scanning techniques and software to handle this process. However, when vulnerability scanning is done right, it can also reveal potentially critical yet overlooked vulnerabilities that can have serious consequences.
Penetration testing vs. vulnerability scanning

Penetration testing is a security verification method executed by an external team of experts who think like hackers and use extremely offensive approaches to test any weaknesses in the product that can be exploited. The penetration testing is performed with either white-box or black-box approaches, having different levels of exposure to the internal documentation to the source code of the product.
Whereas vulnerability scanning is mainly automated and will be done by a trusted tool. A tool that is well researched and built by cybersecurity experts and penetration testers itself to fit the mind of an external hacker/attacker. Vulnerability scanning will be an accurate methodology to detect any weaknesses or vulnerabilities and get an in-depth analysis of the impact or the threats posed.
Causes for vulnerabilities
Vulnerabilities can be from different causes, and their effects vary accordingly. For example, poor security knowledge to developers, lack of collaboration between dev, ops, and security teams, insufficient training, flaws in the business logic, faulty and inadequate testing, deficiency of log tracking and audit trail, miscommunication between the teams, coding and design flaws, etc. are some of the main reasons why vulnerabilities happen and get unnoticed. Vulnerabilities will be introduced when security activities are not completely blended with the development culture. No proper planning on selecting languages in the development phase might sometimes pose a risk to different vulnerabilities. Re-usage of vulnerable code and components further increases the chances of vulnerabilities spreading across the development teams.
Whatever the cause is, it is the security team's job to identify the vulnerability and eliminate it as early as possible. But attackers are becoming more and more sophisticated (the threats are . always evolving), and manual security procedures won't scale to meet the increasing pace of development and hence a reliable vulnerability scanning tool is what every enterprise needs.
Why is vulnerability scanning necessary?
Cybersecurity is taken very seriously after malicious attacks such as SolarWinds, and every developer knows about this. However, attackers are always on the hunt for opportunities to find the vulnerabilities in the system to exploit them. Hence it is being stressed that security is everybody's job but can this happen in reality? A developer always focuses on writing clean code taking all the security precautions, but sometimes, mistakes happen, and they cost a lot. Therefore, it is imperative to cut the flow of vulnerabilities very early in the SDLC. Yes, it is happening through DevSecOps best practices and with security vulnerability scanning tools (for example, JFrog Xray).
There is also something called threat; a threat can be the actual or possible accident where the hackers make use of the vulnerability to install an attack and harm the systems, networks, or data. For example, the CodeRed worm discovered in 2001 attacked all the computers running Microsoft IIS. The vulnerability in IIS was used effectively to infect 300,000 targets and more. Such threats have induced huge financial losses throughout the globe.
Ponemon Institute conducted a survey about vulnerabilities and found that in the organizations affected by a breach, almost 60% of them originated due to an unpatched vulnerability and could have easily avoided such breaches with a simple vulnerability scanning tool/platform in place. Hence having a vulnerability tool is highly recommended because the vulnerability tool constantly checks for the vulnerabilities and helps alleviate or prevent any cybersecurity breaches. Without a proper vulnerability tool/software in place, it is impossible to find the security gaps, which might pose huge security risks later if untreated.
Vulnerability scanning is one of the best ways to mitigate the risk of an attack or data breach. Some of the many benefits include:
• Notifying developers of vulnerabilities in software that could lead to data breaches.
• Notifying law enforcement and other security forces of potential threats.
• Identifying likely target areas for attacks.
• Preventing users from unintentionally disclosing data to threats.
• Trained and educated users help identify and avoid a possible breach.
How to tackle the software vulnerabilities entering the system?
Binary scanning vs. Source code scanning
Binary scanning is a threat detection framework that is automated in the CI/CD pipeline at a binary level that helps development teams find and fix the vulnerabilities found in the artifacts and dependencies related to the application. Binary scanning is considered the first line of defense against security breaches. Source code scanning is done at the code level, where the focus is mainly on the quality of the code and analyzing if any security gaps are detected.
Uncompiled code is analyzed by a source code scanner, and the compiled code is analyzed by a binary scanner.
While source code scanners just analyze the code, the binary scanners go the extra mile by scanning the compiled code for vulnerabilities and detecting the vulnerabilities found in the third-party libraries, licensing mistakes, etc.
Today's software, on average, at least 60%, is composed of open-source software, there are a lot of open-source dependencies that we use in our code, and it has a lot of advantages. However, along with advantages, there are also risks introduced with these open source dependencies in the form of security vulnerabilities, license compliance issues, performance issues, etc.
It is crucial to address any vulnerabilities that occur during the software development stage so we can remove or negate them by entering the production systems that may cause substantial financial losses to the organizations. Xray from JFrog is one such tool that can help you protect your code by recognizing the vulnerabilities and associated security threats and preventing any risks from penetrating your software releases.
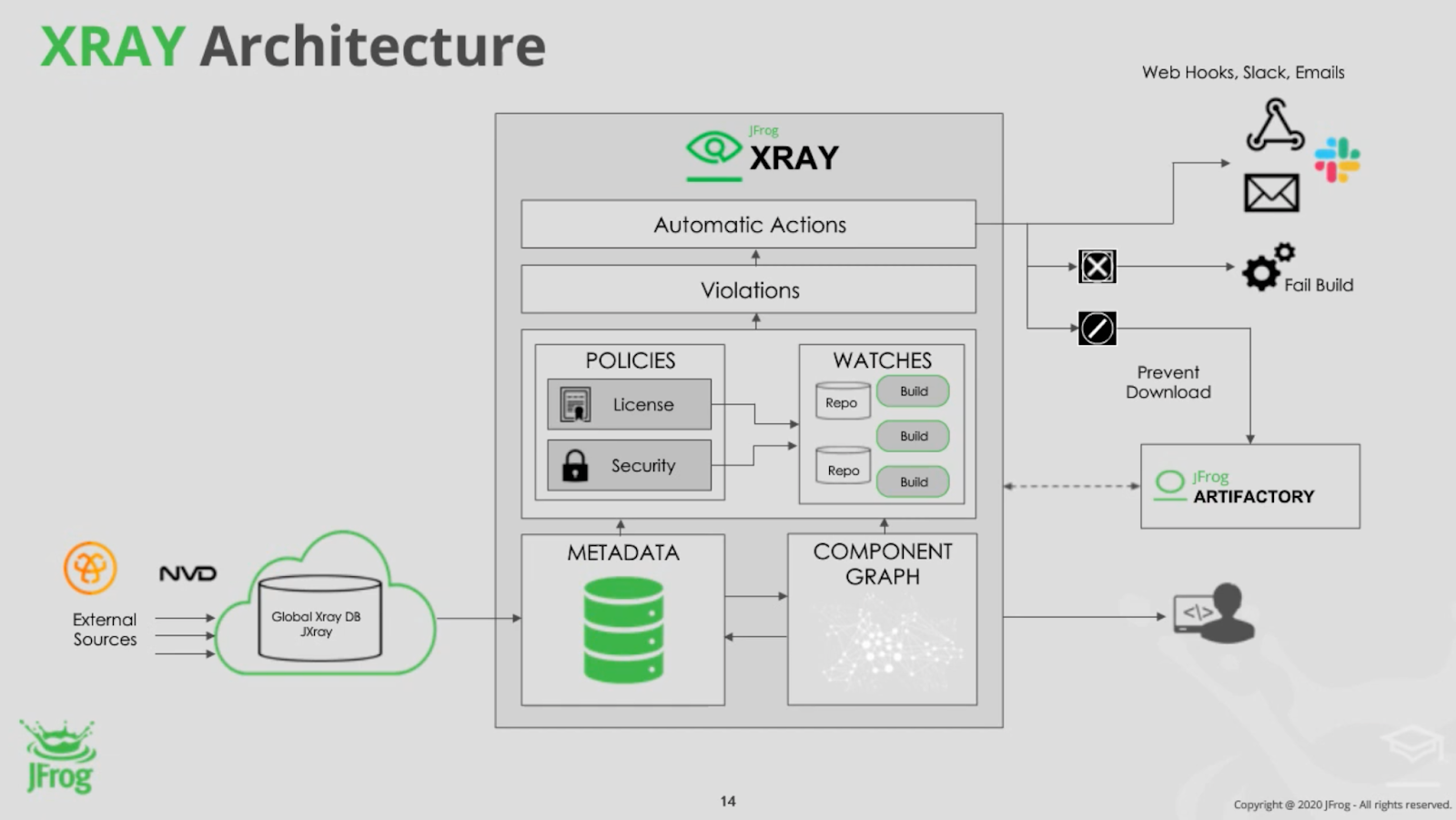
On the left-hand side, you can see that the metadata and database updates are being received on a daily basis. Artifactory is natively integrated with Xray, so all of the build projects and repositories will be accessible by Xray. It performs the software composition analysis, and the relevant component graph associated with these repositories and build projects is stored inside the db as a component graph. Once the indexing/software composition analysis is performed and is successful, the actual artifact will be deleted from Xray.
Once the metadata database updates and the component graph are available, Xray performs a mapping to deliver various results on what type of violations, security, or licensing issues are found in your organization. By configuring the policies (either security or licensing), you can control and customize what type of alerting and automatic actions to be triggered when a specific violation is found. You can also enforce fail build and prevent download capabilities to prevent the vulnerabilities from entering the active systems.
Conclusion
With DevSecOps being the talk of the town, security has become the priority in every organization that deals with software in one or the other ways. Well, every company is considered a software company today, and these security principles and strategies become highly beneficial to keep attackers away from the systems. The need for security professionals has increased along with automation and delivering software fast. A well-thought-out vulnerability scanning software/tool is also highly recommended because the manual process takes a lot of time and is prone to errors. Take care of security, and everything falls back to its place. I hope this article gave you some helpful insights on securing your SDLC.
Opinions expressed by DZone contributors are their own.

Comments