Security Governance Simplified: Protecting Your Microservice Applications
A practical guide to implementing effective security governance in microservices, focusing on key strategies, policies, and tools to protect distributed applications.
Join the DZone community and get the full member experience.
Join For FreeMicroservices architecture has transformed how applications are developed, deployed, and scaled. Coupled with containerization, microservices enable faster delivery, greater scalability, and flexibility. However, this architectural shift brings new security challenges that require specialized governance strategies. Security governance for microservices demands robust policies, consistent monitoring, and specific tools to address the complex, distributed nature of these environments. Here, we explore the key strategies, practices, and tools needed to secure microservices effectively.
Understanding Security Governance in Microservices
Security governance ensures that security is an integral part of the microservices lifecycle. It involves setting policies, defining roles and responsibilities, managing risks, and ensuring compliance with industry standards. In the context of microservices, security governance becomes more complex due to the decentralized nature of these architectures, where services operate independently, often on different platforms and cloud environments.
Why Security Governance Is Crucial for Microservices
In microservices, security governance must address the following:
- Service Isolation: Each service operates independently, often across different platforms or cloud environments.
- Decentralized Communication: Services communicate over networks, increasing exposure to threats.
- Dynamic Environments: Microservices frequently scale up or down based on demand, complicating traditional security models.
For containerized microservices, security governance adds layers of complexity due to the rapid provisioning and destruction of containers and the shared resources they rely on.
Challenges of Security Governance in Microservices
Microservices architectures are inherently more complex than monolithic applications, which amplifies certain security challenges:
- Decentralized Management: Microservices may be managed by separate teams, making unified security governance challenging.
- Dynamic Network Topologies: Microservices communicate over the network, exposing them to potential threats and increasing the attack surface.
- Service-to-Service Communication: Unlike traditional applications, microservices rely on APIs and messaging for inter-service communication, necessitating secure and authenticated interactions.
- Diverse Technology Stacks: Different services may use various languages, frameworks, and databases, requiring versatile security controls.
- Frequent Changes and Scaling: With CI/CD pipelines, microservices are updated frequently, necessitating robust security governance to keep pace.
- API Security: Microservices communicate primarily through APIs, making API security critical.
- Inter-Service Authentication: Each service requires secure authentication mechanisms to trust and communicate safely with other services. Methods like mutual TLS (mTLS) can secure those connections.
- Distributed Access Control: With multiple microservices, managing permissions for each service, user, and API endpoint becomes complex.
Containerized microservices introduce further challenges:
- Ephemeral Nature: Containers can be created or destroyed in seconds, requiring dynamic security controls.
- Host Kernel Vulnerabilities: Containers share the host OS kernel, so a breach in one container could impact others.
- Image Security and Dependency Management: Vulnerabilities in container images and dependencies can introduce risks across the microservices ecosystem.
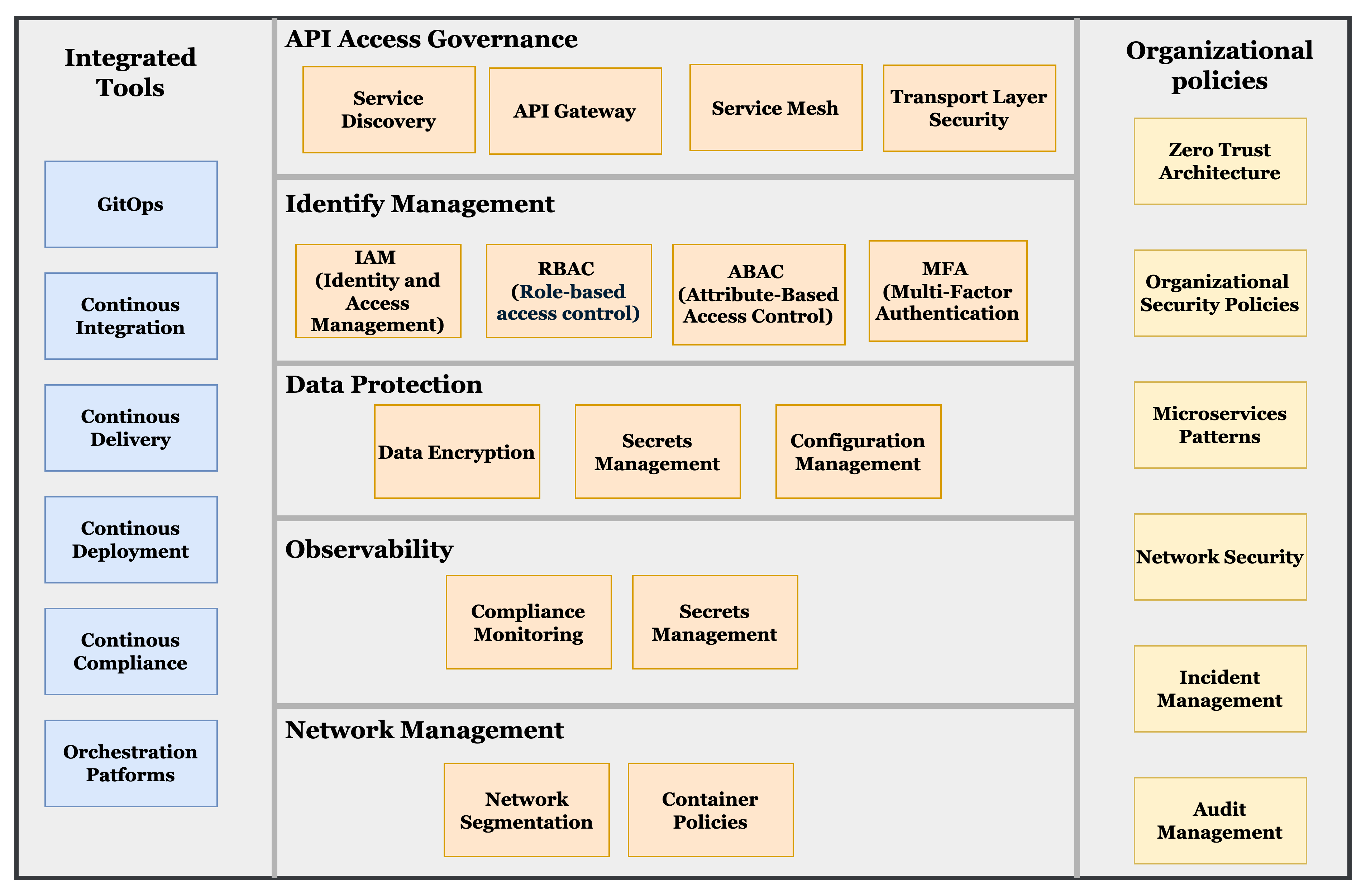
Core Pillars of Security Governance for Microservices
To build a secure and resilient microservices environment, companies should focus on these core governance pillars:
Identity and Access Management (IAM)
Securely manage identities and control access to resources. Implement role-based access control (RBAC) and fine-grained permissions for each microservice.
Data Protection
Use data encryption for both in-transit and at-rest data. Apply strict controls to access sensitive data and regularly audit data access logs.
Network Security
Secure inter-service communication with mTLS, network segmentation, and firewall policies. Implement service mesh solutions, such as Istio or Linkerd, for secure traffic management.
API Security
Enforce API security using rate limiting, validation, and authentication mechanisms such as OAuth2 or API gateways. Establish security policies to govern API usage and monitor API traffic for anomalies.
Observability and Monitoring
Continuously monitor services for security threats and ensure visibility into service behavior. Use logging, tracing, and monitoring tools to quickly detect and respond to incidents.
Compliance Management
Align with industry standards and regulations, such as GDPR, HIPAA, and PCI DSS. Regularly audit services to ensure compliance and adapt governance policies as regulatory requirements evolve.
Key Strategies for Implementing Security Governance in Microservices
Implementing effective security governance requires a combination of technical controls, processes, and policies tailored to the unique needs of microservices. Here are essential strategies:
Secure Service-to-Service Communication
Implement strong authentication and encryption between services. Mutual TLS (mTLS) can help establish secure communication in general and containerized microservices. In containerized environments, a service mesh like Istio or Linkerd can enforce mTLS and centralized access control policies.
API Gateway for Centralized Security Control
An API gateway centralizes API traffic, enforcing authentication, authorization, and rate limiting. It acts as a security checkpoint for all incoming requests, ensuring that only authenticated users and applications interact with the microservices.
API Gateway Security
Use the API gateway to enforce security policies, monitor traffic, and filter potentially malicious requests before they reach backend services.
Container Runtime Security
In containerized microservices, runtime security detects anomalies during container operation, such as privilege escalation or unauthorized access. Tools like Falco or Sysdig monitor container activity, helping to enforce governance policies and prevent breaches.
Security Policies and Standards
Define and enforce security policies across all microservices. This includes standardizing secure coding practices, setting up incident response protocols, and ensuring consistent use of encryption. Governance teams should regularly review and update policies to address new threats and regulatory requirements.
Automated Security in CI/CD Pipelines
Automating security checks within CI/CD pipelines is critical to maintaining security throughout the development lifecycle. Integrate tools for static code analysis, dependency scanning, and vulnerability assessments. By enforcing security checks at every stage, security teams can identify and mitigate vulnerabilities before deployment.
Service Mesh for Enhanced Security Controls
A service mesh can enforce secure communication between services with features like mTLS, policy enforcement, and observability. It also simplifies managing security policies across services, reducing the burden on individual development teams while ensuring secure communication.
Zero Trust Architecture
Adopt a Zero Trust approach where services must authenticate and authorize each request, regardless of its source. Implementing Zero Trust in microservices involves securing service-to-service communication, requiring identity verification for every interaction, and eliminating implicit trust between services. With Zero Trust, no service trusts another by default. Every service needs to prove who it is before accessing anything, no matter where it’s coming from.
Configuration Management and Secret Storage
Effective governance involves secure configuration management. Store sensitive data such as API keys and database credentials securely, ideally using secrets management tools like IBM Cloud Secrets Manager, HashiCorp Vault, or AWS Secrets Manager. Limit container access to secrets by following the principle of least privilege.
Network Segmentation and Container Network Policies
In general microservices, isolate sensitive services to prevent unauthorized access. In containerized microservices, Kubernetes network policies or tools like Calico provide fine-grained control over inter-container communication, ensuring that only authorized traffic flows between containers.
Continuous Monitoring and Incident Response
Implement robust monitoring to detect and respond to security incidents in real time. Use tools like Prometheus, Grafana, and ELK Stack for logging and observability. Establish an incident response plan that provides clear steps for identifying, containing, and resolving security incidents.
Best Practices for Security Governance in Microservices
To further strengthen security governance, adhere to these best practices:
- Shift Security Left: Integrate security early in the development cycle, reducing the chances of vulnerabilities making it to production.
- Principle of Least Privilege (PoLP): Restrict access permissions to the minimum necessary for both services and users.
- Regular Vulnerability Scanning and Patching: Frequently scan services and dependencies for vulnerabilities and apply patches promptly.
- Maintain a Security-Aware Culture: Educate development and operations teams about security practices and potential risks.
- Audit and Compliance Checks: Regularly audit services to ensure compliance with governance policies and regulatory requirements. Documentation and consistent auditing are essential to maintaining long-term security.
- Incident Response Automation: Implement automated responses for common security events, such as unauthorized access or container drift, to mitigate risks in real time.
- Security Chaos Engineering: Intentionally simulating security threats, failures, and misconfigurations to identify weaknesses, test responses, and strengthen system resilience against real-world attacks.
Tools and Technologies for Microservices Security Governance
Several tools are available to enhance security governance in a microservices architecture:
- IAM Solutions: Okta, Auth0, and IBM Cloud IAM provide robust identity and access management capabilities.
- API Gateways: Kong, and NGINX, offer security, traffic management, and policy enforcement for APIs.
- Service Mesh: Istio, Linkerd, and Consul connect secure service-to-service communication within a mesh.
- Secrets Management: HashiCorp Vault, IBM Cloud Secrets Manager, Azure Key Vault
- Container Security: Aqua Security, Twistlock, Falco
- CI/CD Security Tools: Snyk, Aqua Security, and Checkmarx integrate security checks in CI/CD pipelines.
- Monitoring and Logging Tools: Prometheus, Grafana, ELK Stack, and Datadog provide observability, logging, and alerting to detect security incidents.
- Security Chaos Engineering: Tools like Gremlin can simulate attacks so users can see how their systems hold up under pressure. IBM QRadar Suite helps monitor and analyze chaos experiments by collecting and analyzing logs and network activity in real time.
Conclusion
Security for microservices isn’t something we set and forget. It’s an ongoing effort to stay ahead of new threats, keep policies updated, and monitor everything closely. Security governance for microservices is a multi-faceted discipline that requires proactive policies, continuous monitoring, and a culture of security. By establishing robust security governance practices, organizations can build secure microservices environments that protect sensitive data, ensure compliance, and withstand evolving threats.
The path to effective microservices security governance lies in automation, consistent policies, and a Zero Trust approach that embraces the unique challenges of modern, distributed architectures. By integrating these strategies, you can create a resilient security framework that supports innovation and agility without compromising security.
Opinions expressed by DZone contributors are their own.

Comments