Securing Secrets: A Guide To Implementing Secrets Management in DevSecOps Pipelines
Secure secrets management in DevSecOps is crucial to prevent breaches. Implement best practices, automate rotation, and use tools for robust security.
Join the DZone community and get the full member experience.
Join For FreeIntroduction to Secrets Management
In the world of DevSecOps, where speed, agility, and security are paramount, managing secrets effectively is crucial. Secrets, such as passwords, API keys, tokens, and certificates, are sensitive pieces of information that, if exposed, can lead to severe security breaches. To mitigate these risks, organizations are turning to secret management solutions. These solutions help securely store, access, and manage secrets throughout the software development lifecycle, ensuring they are protected from unauthorized access and misuse. This article aims to provide an in-depth overview of secrets management in DevSecOps, covering key concepts, common challenges, best practices, and available tools.
Security Risks in Secrets Management
The lack of implementing secrets management poses several challenges. Primarily, your organization might already have numerous secrets stored across the codebase. Apart from the ongoing risk of exposure, keeping secrets within your code promotes other insecure practices such as reusing secrets, employing weak passwords, and neglecting to rotate or revoke secrets due to the extensive code modifications that would be needed. Here below are some of the risks highlighting the potential risks of improper secrets management:
Data Breaches
If secrets are not properly managed, they can be exposed, leading to unauthorized access and potential data breaches.
Example Scenario
A Software-as-a-Service (SaaS) company uses a popular CI/CD platform to automate its software development and deployment processes. As part of their DevSecOps practices, they store sensitive credentials, such as API keys and database passwords, in a secrets management tool integrated with their pipelines.
Issue
Unfortunately, the CI/CD platform they use experiences a security vulnerability that allows attackers to gain unauthorized access to the secrets management tool's API. This vulnerability goes undetected by the company's security monitoring systems.
Consequence
Attackers exploit the vulnerability and gain access to the secrets stored in the management tool. With these credentials, they are able to access the company's production systems and databases. They exfiltrate sensitive customer data, including personally identifiable information (PII) and financial records.
Impact
The data breach leads to significant financial losses for the company due to regulatory fines, legal fees, and loss of customer trust. Additionally, the company's reputation is tarnished, leading to a decrease in customer retention and potential business partnerships.
Preventive Measures
To prevent such data breaches, the company could have implemented the following preventive measures:
- Regularly auditing and monitoring access to the secrets management tool to detect unauthorized access.
- Implementing multi-factor authentication (MFA) for accessing the secrets management tool.
- Ensuring that the secrets management tool is regularly patched and updated to address any security vulnerabilities.
- Limiting access to secrets based on the principle of least privilege, ensuring that only authorized users and systems have access to sensitive credentials.
- Implementing strong encryption for storing secrets to mitigate the impact of unauthorized access.
- Conducting regular security assessments and penetration testing to identify and address potential security vulnerabilities in the CI/CD platform and associated tools.
Credential Theft
Attackers may steal secrets, such as API keys or passwords, to gain unauthorized access to systems or resources.
Example Scenario
A fintech startup uses a popular CI/CD platform to automate its software development and deployment processes. They store sensitive credentials, such as database passwords and API keys, in a secrets management tool integrated with their pipelines.
Issue
An attacker gains access to the company's internal network by exploiting a vulnerability in an outdated web server. Once inside the network, the attacker uses a variety of techniques, such as phishing and social engineering, to gain access to a developer's workstation.
Consequence
The attacker discovers that the developer has stored plaintext files containing sensitive credentials, including database passwords and API keys, on their desktop. The developer had mistakenly saved these files for convenience and had not securely stored them in the secrets management tool.
Impact
With access to the sensitive credentials, the attacker gains unauthorized access to the company's databases and other systems. They exfiltrate sensitive customer data, including financial records and personal information, leading to regulatory fines and damage to the company's reputation.
Preventive Measures
To prevent such credential theft incidents, the fintech startup could have implemented the following preventive measures:
- Educating developers and employees about the importance of securely storing credentials and the risks of leaving them in plaintext files.
- Implementing strict access controls and auditing mechanisms for accessing and managing secrets in the secrets management tool.
- Using encryption to store sensitive credentials in the secrets management tool, ensures that even if credentials are stolen, they cannot be easily used without decryption keys.
- Regularly rotating credentials and monitoring for unusual or unauthorized access patterns to detect potential credential theft incidents early.
Misconfiguration
Improperly configured secrets management systems can lead to accidental exposure of secrets.
Example Scenario
A healthcare organization uses a popular CI/CD platform to automate its software development and deployment processes. They store sensitive credentials, such as database passwords and API keys, in a secrets management tool integrated with their pipelines.
Issue
A developer inadvertently misconfigures the permissions on the secrets management tool, allowing unintended access to sensitive credentials. The misconfiguration occurs when the developer sets overly permissive access controls, granting access to a broader group of users than intended.
Consequence
An attacker discovers the misconfigured access controls and gains unauthorized access to the secrets management tool. With access to sensitive credentials, the attacker can now access the healthcare organization's databases and other systems, potentially leading to data breaches and privacy violations.
Impact
The healthcare organization suffers reputational damage and financial losses due to the data breach. They may also face regulatory fines for failing to protect sensitive information.
Preventive Measures
To prevent such misconfiguration incidents, the healthcare organization could have implemented the following preventive measures:
- Implementing least privilege access controls to ensure that only authorized users and systems have access to sensitive credentials.
- Regularly auditing and monitoring access to the secrets management tool to detect and remediate misconfigurations.
- Implementing automated checks and policies to enforce proper access controls and configurations for secrets management.
- Providing training and guidance to developers and administrators on best practices for securely configuring and managing access to secrets.
Compliance Violations
Failure to properly manage secrets can lead to violations of regulations such as GDPR, HIPAA, or PCI DSS.
Example Scenario
A financial services company uses a popular CI/CD platform to automate their software development and deployment processes. They store sensitive credentials, such as encryption keys and API tokens, in a secrets management tool integrated with their pipelines.
Issue
The financial services company fails to adhere to regulatory requirements for managing and protecting sensitive information. Specifically, they do not implement proper encryption for storing sensitive credentials and do not maintain proper access controls for managing secrets.
Consequence
Regulatory authorities conduct an audit of the company's security practices and discover compliance violations related to secrets management. The company is found to be non-compliant with regulations such as PCI DSS (Payment Card Industry Data Security Standard) and GDPR (General Data Protection Regulation).
Impact
The financial services company faces significant financial penalties for non-compliance with regulatory requirements. Additionally, the company's reputation is damaged, leading to a loss of customer trust and potential legal consequences.
Preventive Measures
To prevent such compliance violations, the financial services company could have implemented the following preventive measures:
- Implementing encryption for storing sensitive credentials in the secrets management tool to ensure compliance with data protection regulations.
- Implementing strict access controls and auditing mechanisms for managing and accessing secrets to prevent unauthorized access.
- Conducting regular compliance audits and assessments to identify and address any non-compliance issues related to secrets management.
Lack of Accountability
Without proper auditing and monitoring, it can be difficult to track who accessed or modified secrets, leading to a lack of accountability.
Example Scenario
A technology company uses a popular CI/CD platform to automate its software development and deployment processes. They store sensitive credentials, such as API keys and database passwords, in a secrets management tool integrated with their pipelines.
Issue
The company does not establish clear ownership and accountability for managing and protecting secrets. There is no designated individual or team responsible for ensuring that proper security practices are followed when storing and accessing secrets.
Consequence
Due to the lack of accountability, there is no oversight or monitoring of access to sensitive credentials. As a result, developers and administrators have unrestricted access to secrets, increasing the risk of unauthorized access and data breaches.
Impact
The lack of accountability leads to a data breach where sensitive credentials are exposed. The company faces financial losses due to regulatory fines, legal fees, and loss of customer trust. Additionally, the company's reputation is damaged, leading to a decrease in customer retention and potential business partnerships.
Preventive Measures
To prevent such lack of accountability incidents, the technology company could have implemented the following preventive measures:
- Designating a specific individual or team responsible for managing and protecting secrets, including implementing and enforcing security policies and procedures.
- Implementing access controls and auditing mechanisms to monitor and track access to secrets, ensuring that only authorized users have access.
- Providing regular training and awareness programs for employees on the importance of secrets management and security best practices.
- Conducting regular security audits and assessments to identify and address any gaps in secrets management practices.
Operational Disruption
If secrets are not available when needed, it can disrupt the operation of DevSecOps pipelines and applications.
Example Scenario
A financial institution uses a popular CI/CD platform to automate its software development and deployment processes. They store sensitive credentials, such as encryption keys and API tokens, in a secrets management tool integrated with their pipelines.
Issue
During a routine update to the secrets management tool, a misconfiguration occurs that causes the tool to become unresponsive. As a result, developers are unable to access the sensitive credentials needed to deploy new applications and services.
Consequence
The operational disruption leads to a delay in deploying critical updates and features, impacting the financial institution's ability to serve its customers effectively. The IT team is forced to troubleshoot the issue, leading to downtime and increased operational costs.
Impact
The operational disruption results in financial losses due to lost productivity and potential revenue. Additionally, the financial institution's reputation is damaged, leading to a loss of customer trust and potential business partnerships.
Preventive Measures
To prevent such operational disruptions, the financial institution could have implemented the following preventive measures:
- Implementing automated backups and disaster recovery procedures for the secrets management tool to quickly restore service in case of a failure.
- Conducting regular testing and monitoring of the secrets management tool to identify and address any performance issues or misconfigurations.
- Implementing a rollback plan to quickly revert to a previous version of the secrets management tool in case of a failed update or configuration change.
- Establishing clear communication channels and escalation procedures to quickly notify stakeholders and IT teams in case of operational disruption.
Dependency on Third-Party Services
Using third-party secrets management services can introduce dependencies and potential risks if the service becomes unavailable or compromised.
Example Scenario
A software development company uses a popular CI/CD platform to automate its software development and deployment processes. They rely on a third-party secrets management tool to store sensitive credentials, such as API keys and database passwords, used in their pipelines.
Issue
The third-party secrets management tool experiences a service outage due to a cyber attack on the service provider's infrastructure. As a result, the software development company is unable to access the sensitive credentials needed to deploy new applications and services.
Consequence
The dependency on the third-party secrets management tool leads to a delay in deploying critical updates and features, impacting the software development company's ability to deliver software on time. The IT team is forced to find alternative ways to manage and store sensitive credentials temporarily.
Impact
The dependency on the third-party secrets management tool results in financial losses due to lost productivity and potential revenue. Additionally, the software development company's reputation is damaged, leading to a loss of customer trust and potential business partnerships.
Preventive Measures
To prevent such dependencies on third-party services, the software development company could have implemented the following preventive measures:
- Implementing a backup plan for storing and managing sensitive credentials locally in case of a service outage or disruption.
- Diversifying the use of secrets management tools by using multiple tools or providers to reduce the impact of a single service outage.
- Conducting regular reviews and assessments of third-party service providers to ensure they meet security and reliability requirements.
- Implementing a contingency plan to quickly switch to an alternative secrets management tool or provider in case of a service outage or disruption.
Insider Threats
Malicious insiders may abuse their access to secrets for personal gain or to harm the organization.
Example Scenario
A technology company uses a popular CI/CD platform to automate their software development and deployment processes. They store sensitive credentials, such as API keys and database passwords, in a secrets management tool integrated with their pipelines.
Issue
An employee with privileged access to the secrets management tool decides to leave the company and maliciously steals sensitive credentials before leaving. The employee had legitimate access to the secrets management tool as part of their job responsibilities but chose to abuse that access for personal gain.
Consequence
The insider threat leads to the theft of sensitive credentials, which are then used by the former employee to gain unauthorized access to the company's systems and data. This unauthorized access can lead to data breaches, financial losses, and damage to the company's reputation.
Impact
The insider threat results in financial losses due to potential data breaches and the need to mitigate the impact of the stolen credentials. Additionally, the company's reputation is damaged, leading to a loss of customer trust and potential legal consequences.
Preventive Measures
To prevent insider threats involving secrets management, the technology company could have implemented the following preventive measures:
- Implementing strict access controls and least privilege principles to limit the access of employees to sensitive credentials based on their job responsibilities.
- Conducting regular audits and monitoring of access to the secrets management tool to detect and prevent unauthorized access.
- Providing regular training and awareness programs for employees on the importance of data security and the risks of insider threats.
- Implementing behavioral analytics and anomaly detection mechanisms to identify and respond to suspicious behavior or activities involving sensitive credentials.
Best Practices for Secrets Management
Here are some best practices for secrets management in DevSecOps pipelines:
- Use a dedicated secrets management tool: Utilize a specialized tool or service designed for securely storing and managing secrets.
- Encrypt secrets at rest and in transit: Ensure that secrets are encrypted both when stored and when transmitted over the network.
- Use strong access controls: Implement strict access controls to limit who can access secrets and what they can do with them.
- Regularly rotate secrets: Regularly rotate secrets (e.g., passwords, API keys) to minimize the impact of potential compromise.
- Avoid hardcoding secrets: Never hardcode secrets in your code or configuration files. Use environment variables or a secrets management tool instead.
- Use environment-specific secrets: Use different secrets for different environments (e.g., development, staging, production) to minimize the impact of a compromised secret.
- Monitor and audit access: Monitor and audit access to secrets to detect and respond to unauthorized access attempts.
- Automate secrets retrieval: Automate the retrieval of secrets in your CI/CD pipelines to reduce manual intervention and the risk of exposure.
- Regularly review and update policies: Regularly review and update your secrets management policies and procedures to ensure they are up-to-date and effective.
- Educate and train employees: Educate and train employees on the importance of secrets management and best practices for handling secrets securely.
Use-Cases of Secrets Management For Different Tools
Here are the common use cases for different tools of secrets management:
IBM Cloud Secrets Manager
- Securely storing and managing API keys
- Managing database credentials
- Storing encryption keys
- Managing certificates
- Integrating with CI/CD pipelines
- Compliance and audit requirements by providing centralized management and auditing of secrets usage.
- Ability to dynamically generate and rotate secrets
HashiCorp Vault
- Centralized secrets management for distributed systems
- Dynamic secrets generation and management
- Encryption and access controls for secrets
- Secrets rotation for various types of secrets
AWS Secrets Manager
- Securely store and manage AWS credentials
- Securely store and manage other types of secrets used in AWS services
- Integration with AWS services for seamless access to secrets
- Automatic secrets rotation for supported AWS services
Azure Key Vault
- Centralized secrets management for Azure applications
- Securely store and manage secrets, keys, and certificates
- Encryption and access policies for secrets
- Automated secrets rotation for keys, secrets, and certificates
CyberArk Conjur
- Secrets management and privileged access management
- Secrets retrieval via REST API for integration with CI/CD pipelines
- Secrets versioning and access controls
- Automated secrets rotation using rotation policies and scheduled tasks
Google Cloud Secret Manager
- Centralized secrets management for Google Cloud applications
- Securely store and manage secrets, API keys, and certificates
- Encryption at rest and in transit for secrets
- Automated and manual secrets rotation with integration with Google Cloud Functions
These tools cater to different cloud environments and offer various features for securely managing and rotating secrets based on specific requirements and use cases.
Implement Secrets Management in DevSecOps Pipelines
Understanding CI/CD in DevSecOps
CI/CD in DevSecOps involves automating the build, test, and deployment processes while integrating security practices throughout the pipeline to deliver secure and high-quality software rapidly.
Continuous Integration (CI)
CI is the practice of automatically building and testing code changes whenever a developer commits code to the version control system (e.g., Git). The goal is to quickly detect and fix integration errors.
Continuous Delivery (CD)
CD extends CI by automating the process of deploying code changes to testing, staging, and production environments. With CD, every code change that passes the automated tests can potentially be deployed to production.
Continuous Deployment (CD)
CD goes one step further than continuous delivery by automatically deploying every code change that passes the automated tests to production. This requires a high level of automation and confidence in the automated tests.
Continuous Compliance (CC)
CC refers to the practice of integrating compliance checks and controls into the automated CI/CD pipeline. It ensures that software deployments comply with relevant regulations, standards, and internal policies throughout the development lifecycle.
DevSecOps
DevSecOps integrates security practices into the CI/CD pipeline, ensuring that security is built into the software development process from the beginning. This includes performing security testing (e.g., static code analysis, dynamic application security testing) as part of the pipeline and managing secrets securely.
The following picture depicts the DevSecOps lifecycles:
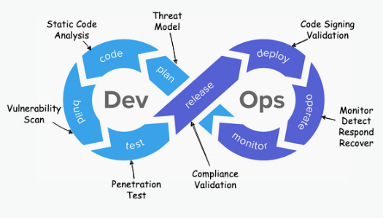
Implement Secrets Management Into DevSecOps Pipelines
Implementing secrets management into DevSecOps pipelines involves securely handling and storing sensitive information such as API keys, passwords, and certificates. Here's a step-by-step guide to implementing secrets management in DevSecOps pipelines:
Select a Secrets Management Solution
Choose a secrets management tool that aligns with your organization's security requirements and integrates well with your existing DevSecOps tools and workflows.
Identify Secrets
Identify the secrets that need to be managed, such as database credentials, API keys, encryption keys, and certificates.
Store Secrets Securely
Use the selected secrets management tool to securely store secrets. Ensure that secrets are encrypted at rest and in transit and that access controls are in place to restrict who can access them.
Integrate Secrets Management into CI/CD Pipelines
Update your CI/CD pipeline scripts and configurations to integrate with the secrets management tool. Use the tool's APIs or SDKs to retrieve secrets securely during the pipeline execution.
Implement Access Controls
Implement strict access controls to ensure that only authorized users and systems can access secrets. Use role-based access control (RBAC) to manage permissions.
Rotate Secrets Regularly
Regularly rotate secrets to minimize the impact of potential compromise. Automate the rotation process as much as possible to ensure consistency and security.
Monitor and Audit Access
Monitor and audit access to secrets to detect and respond to unauthorized access attempts. Use logging and monitoring tools to track access and usage.
Best Practices for Secrets Management Into DevSecOps Pipelines
Implementing secrets management in DevSecOps pipelines requires careful consideration to ensure security and efficiency. Here are some best practices:
- Use a secrets management tool: Utilize a dedicated to store and manage secrets securely.
- Encrypt secrets: Encrypt secrets both at rest and in transit to protect them from unauthorized access.
- Avoid hardcoding secrets: Never hardcode secrets in your code or configuration files. Use environment variables or secrets management tools to inject secrets into your CI/CD pipelines.
- Rotate secrets: Implement a secrets rotation policy to regularly rotate secrets, such as passwords and API keys. Automate the rotation process wherever possible to reduce the risk of human error.
- Implement access controls: Use role-based access controls (RBAC) to restrict access to secrets based on the principle of least privilege.
- Monitor and audit access: Enable logging and monitoring to track access to secrets and detect any unauthorized access attempts.
- Automate secrets retrieval: Automate the retrieval of secrets in your CI/CD pipelines to reduce manual intervention and improve security.
- Use secrets injection: Use tools or libraries that support secrets injection (e.g., Kubernetes secrets, Docker secrets) to securely inject secrets into your application during deployment.
Conclusion
Secrets management is a critical aspect of DevSecOps that cannot be overlooked. By implementing best practices such as using dedicated secrets management tools, encrypting secrets, and implementing access controls, organizations can significantly enhance the security of their software development and deployment pipelines. Effective secrets management not only protects sensitive information but also helps in maintaining compliance with regulatory requirements. As DevSecOps continues to evolve, it is essential for organizations to prioritize secrets management as a fundamental part of their security strategy.
Opinions expressed by DZone contributors are their own.

Comments