Secure Mule API by Auth0 (External Identity Provider)
In this article, take a look at how to secure a Mule API with Auth0.
Join the DZone community and get the full member experience.
Join For FreeJWT-Based API Authentication Using Auth0 and Mulesoft
Web API security is concerned with the transfer of data through APIs that are connected to the internet. Auth0 is an external identity provider that enables systems to give access to REST API resources (exposes via MuleSoft) without having to share passwords.
What Is an Identity Provider?
It is a service that creates and maintains identity information and then provides authentication services to your applications. Identity Providers can significantly reduce sign-in and registration friction, which allows your users to easily access applications without needing to create new passwords or remember usernames
Mulesoft
Provides exceptional business agility to companies by connecting applications, data, and devices, both on-premises and in the cloud with an API-led approach. By leveraging Anypoint Platform.
Auth0
Provides a flexible and drop-in solution to add authentication and authorization services to the applications.
M2M Token-Based Approach to Secure API
API developed in MuleSoft can be secured using machine-to-machine (M2M) applications, such as CLIs, daemons, or services running on our back-end, the system authenticates and authorizes the app rather than a user. For this scenario, typical authentication schemes like username + password or social logins don't make sense. Instead, M2M apps use the Client Credentials Flow (defined in OAuth 2.0 RFC 6749, section 4.4), in which they pass along their Client ID and Client Secret to authenticate themselves and get a token.
Account Setup in Auth0
- Create an account in Auth0
- Login into the account using account credential
- Click the CREATE button to create the application
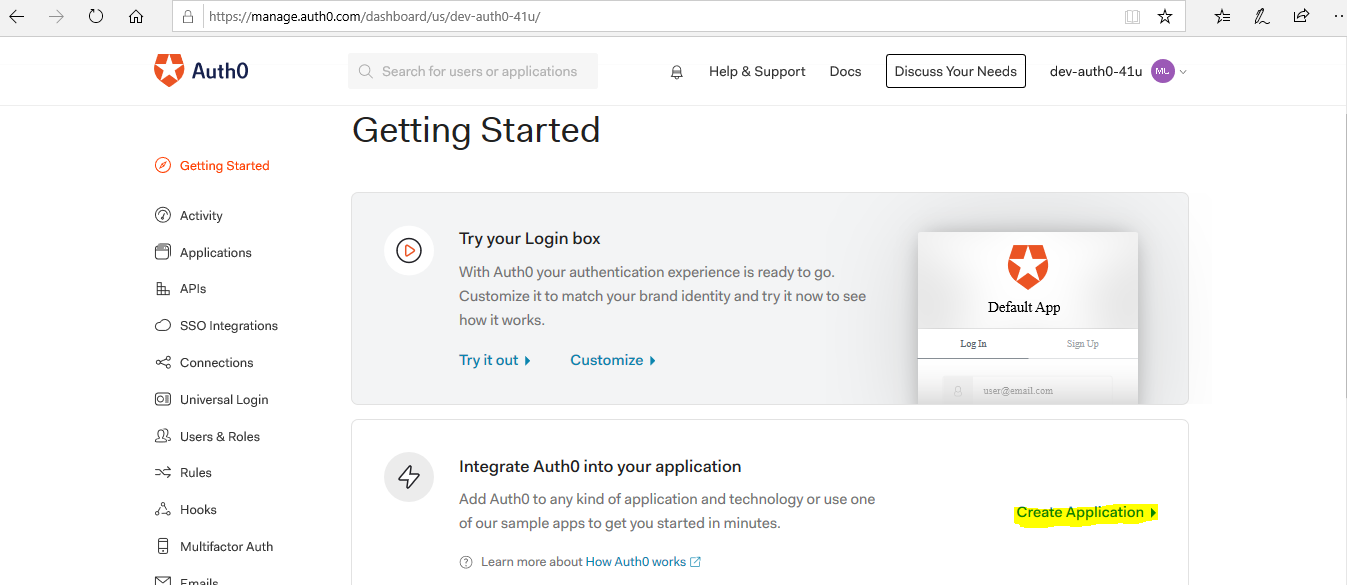
- Name the application, choose application type as machine to machine.
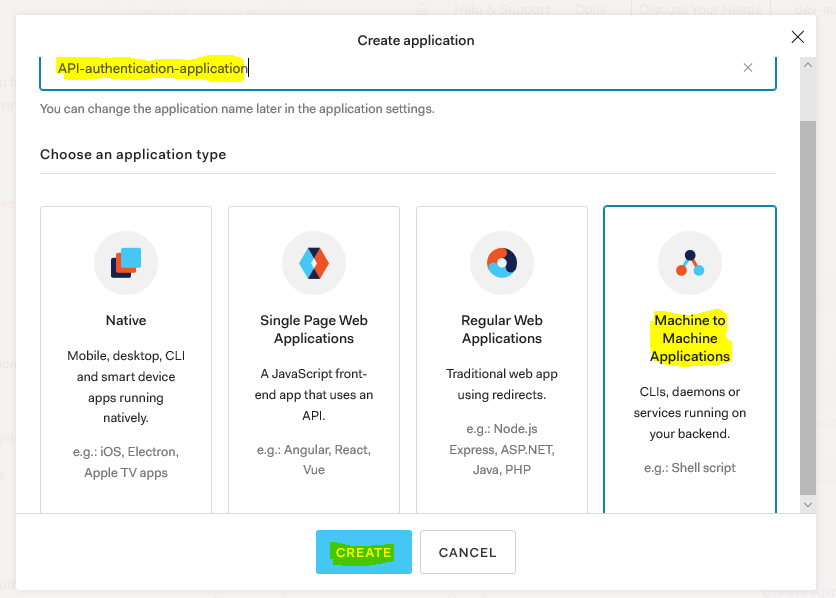
- Add API name, select scope, and click on Authorize
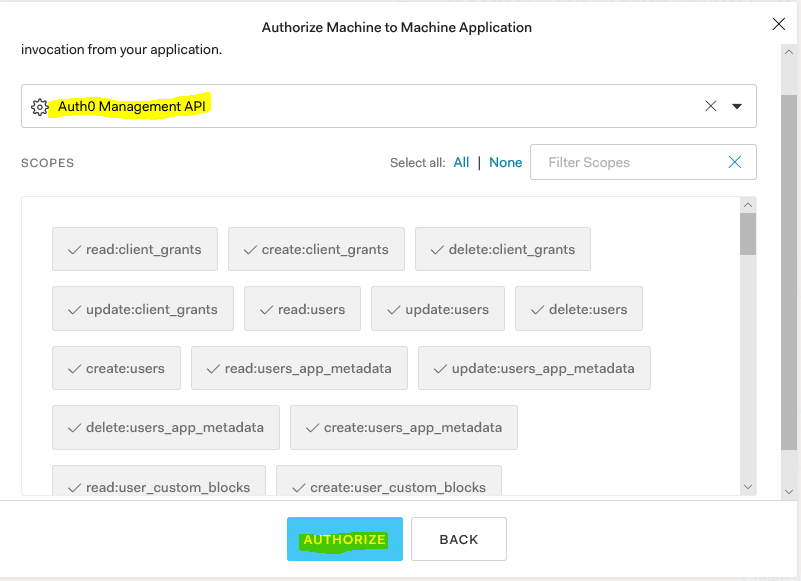
Note: Scopes depends on need
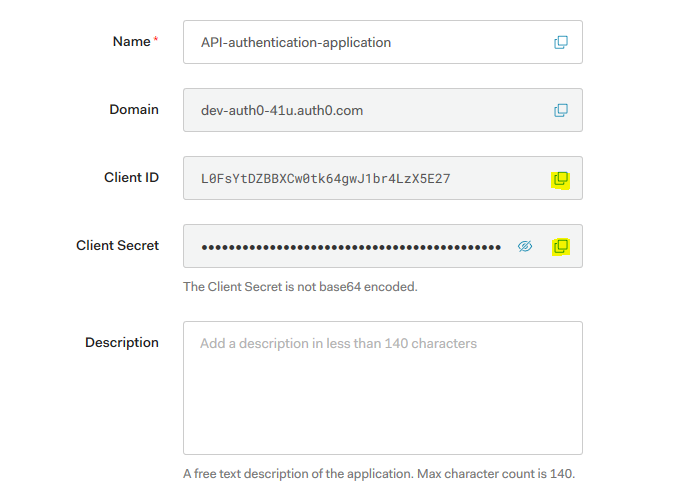
- Copy the client_id and client_secret of the application that would need when we generate security token
- Scroll down to the bottom and select advanced settings. In the Grant Type, make sure only Client Credentials is selected. Click Save Changes to save the changes.
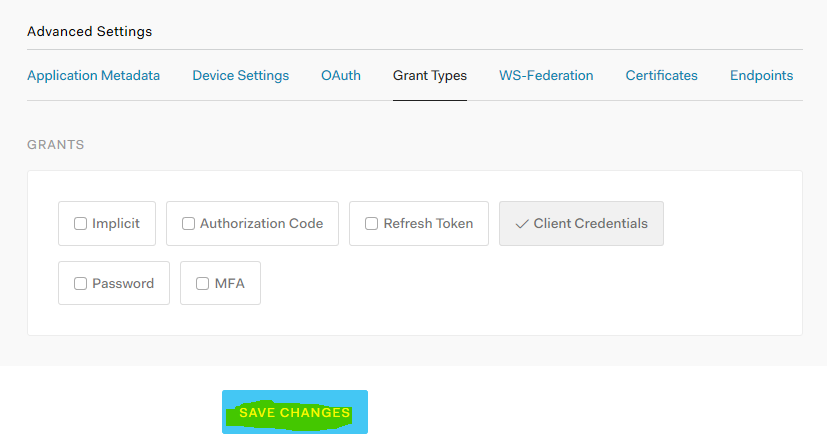
Test Auth0 configuration
- Click on Test and copy code snippet and generate token
xxxxxxxxxx
{
"client_id":"L0FsYtDZBBXCw0tk64gwJ1br4LzX5E27",
"client_secret":"ScNEfHMCtaxkbLRWznc6Zc2dxqF-sVhwUdLQmiXqc6mIXoAXEPkk-nBi_laQKZi2",
"audience":"https://dev-auth0-41u.auth0.com/api/v2/",
"grant_type":"client_credentials"
}
Configuration in Anypoint Platform
JWT Policy in API Manager of Anypoint Platform
To create a policy in API Manager, an API must be created from RAML/OAS/SOAP or available in exchange to import
- Login to Anypoint Platform and select API Manager
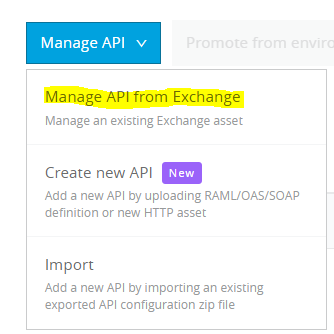
- Click on Manage API from Exchange
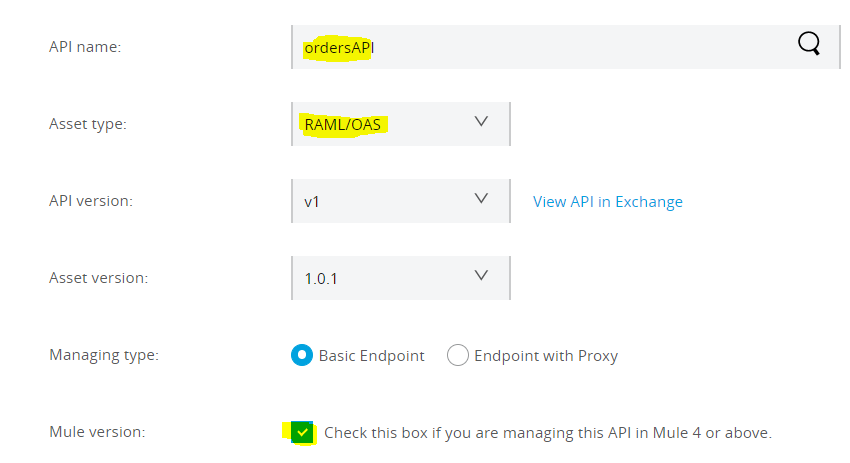
- Search API name, select Asset type, and check mule version and click Save
- On success, API page display and Copy Autodiscovery(API ID). It would be used in actual implementation flow to refer policy from Mule instance.
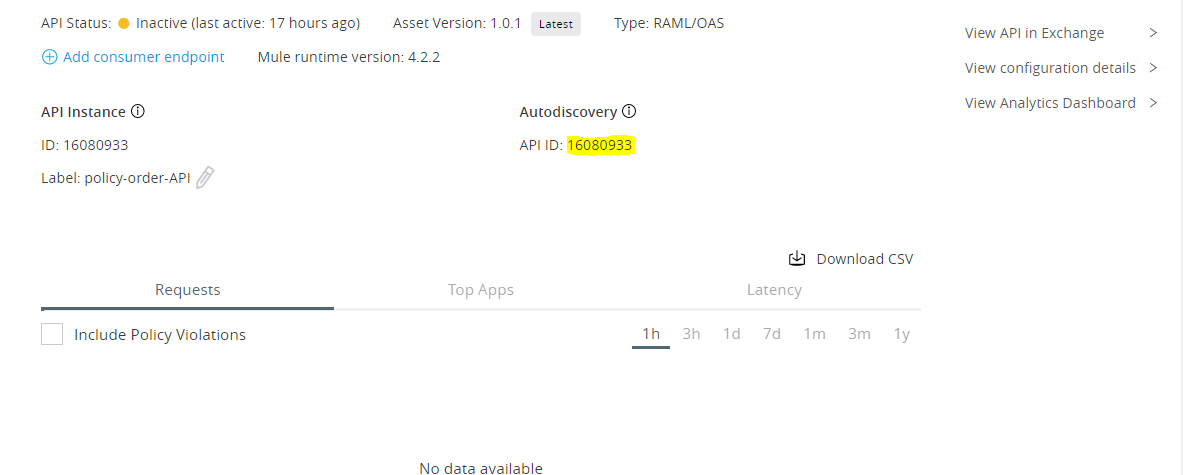
- Click on Policies > Appy New policy > Select policy
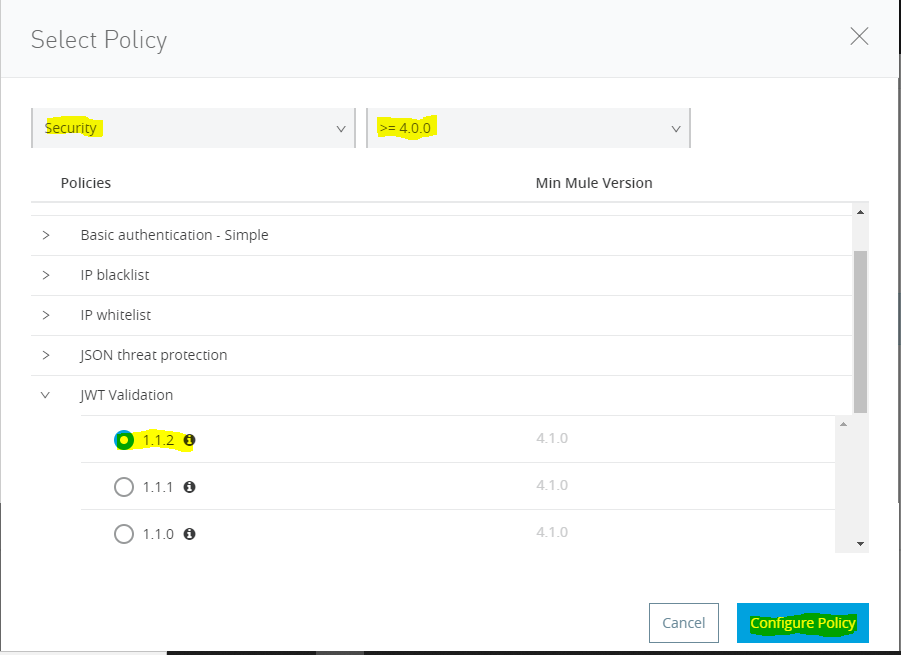
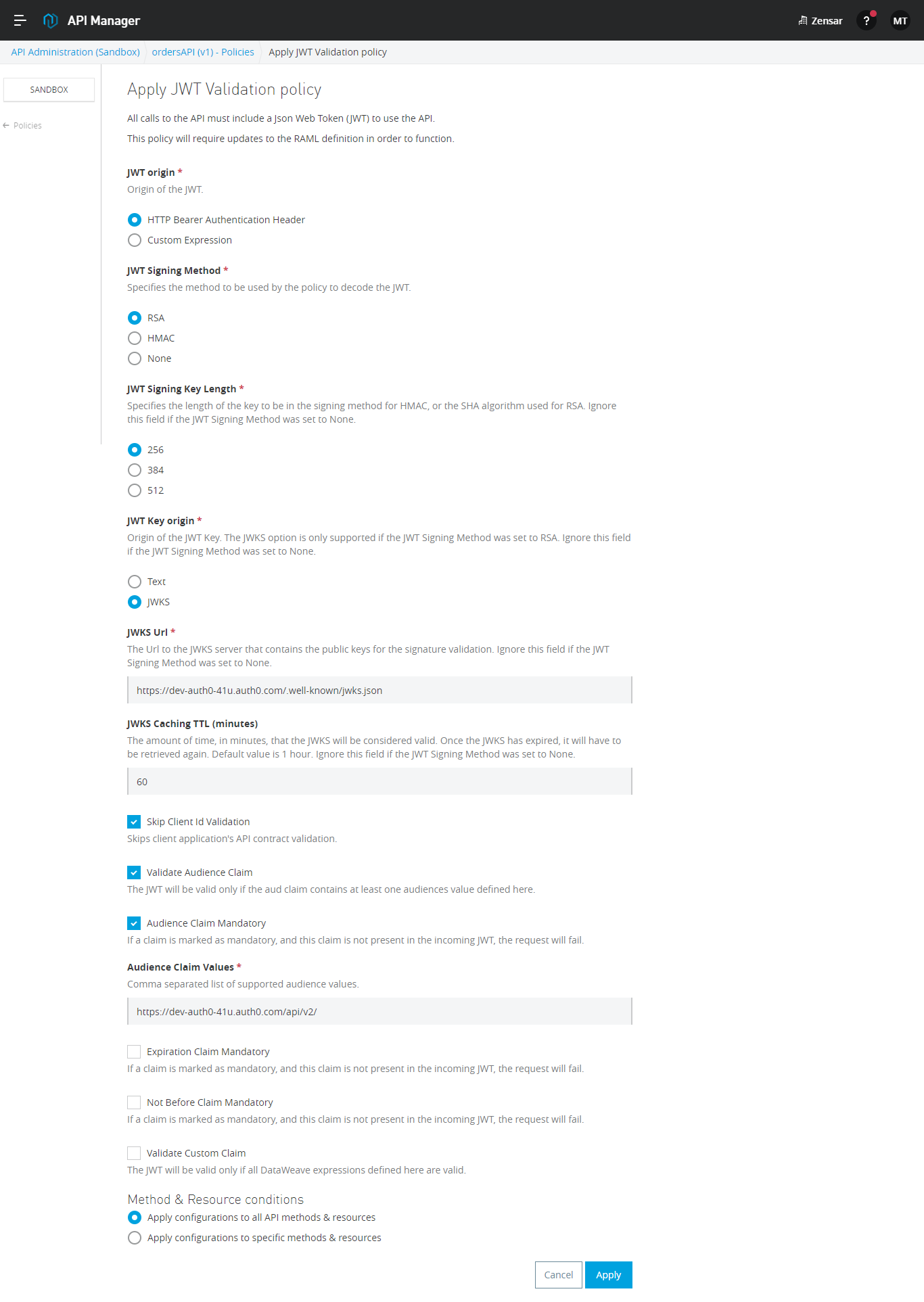
- Configure JWT Policy
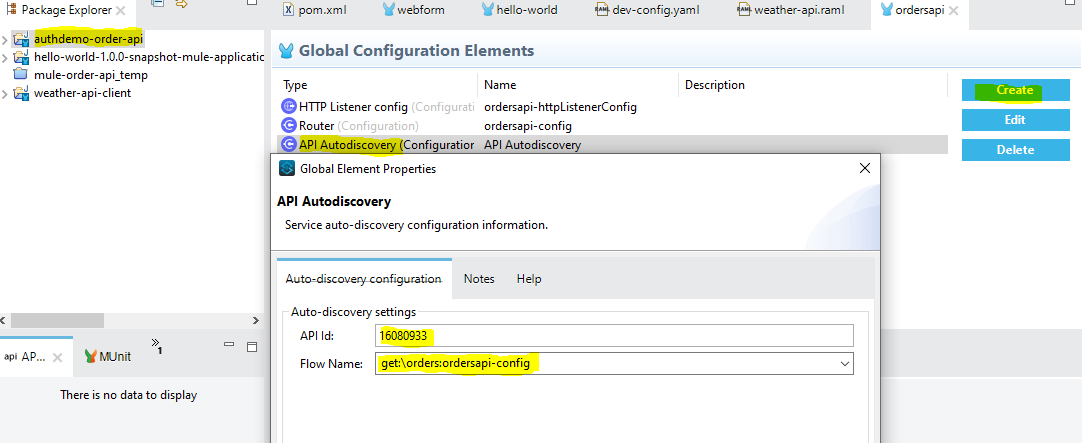
Configure Autodiscovery in API Implementation
- Add API ID, which copied from API manager, and select the flow on which policy to be applied
- Deploy API instance to CloudHub
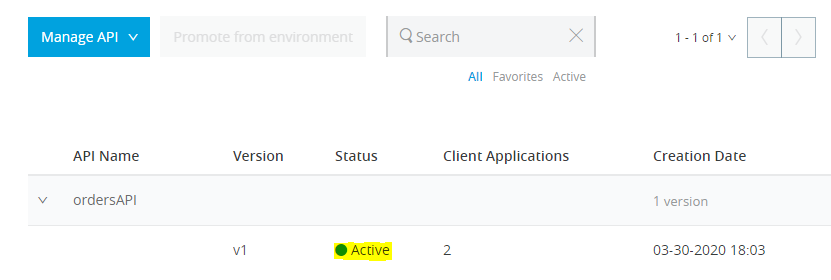
- Verify Policy in API Manager. If status turns to green, it means policy has been applied
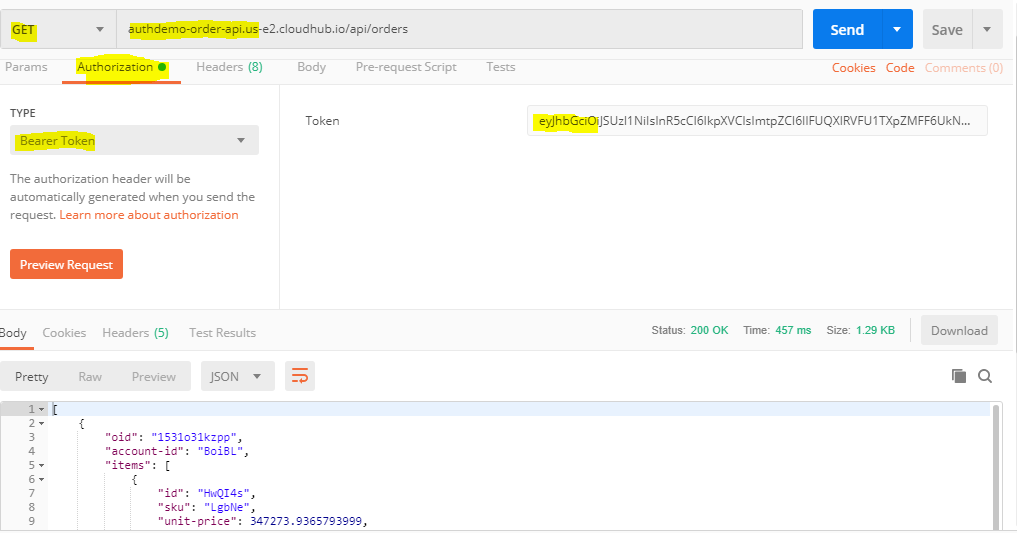
Test API
Generate Auth token as discussed in the above steps
- Call Get : authdemo-order-api.us-e2.cloudhub.io/api/orders & pass bearer token as Authorization
- You would get API response
Summary
This demonstration shows the way to secure your API. We can control a user to access the particular APIs and manage the client by creating a contract in API Manager. We are going to publish those demonstrations soon, so stay tuned for further extension.
Repository
- Source code: mule application
- API specification: RAML
Published at DZone with permission of Mukesh Thakur. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments