Penetration Testing for Beginners: A Step-By-Step Guide
This guide provides beginners with a comprehensive understanding of penetration testing, offering a step-by-step approach to getting started in this critical field.
Join the DZone community and get the full member experience.
Join For FreeIn an era where digital transformation is rapidly advancing, the importance of cybersecurity cannot be overstated. One of the essential aspects of maintaining robust security is penetration testing, commonly known as pentesting. This guide aims to provide beginners with a comprehensive understanding of penetration testing, offering a step-by-step approach to getting started in this critical field.
Introduction to Penetration Testing
Penetration testing is a simulated cyber attack against a computer system, network, or web application to identify security vulnerabilities that an attacker could exploit. The primary goal is to find and fix these vulnerabilities before they can be leveraged by malicious actors. Penetration testing can be manual or automated and typically involves various methods and tools to evaluate the security of an organization’s IT infrastructure.
Why Penetration Testing Is Important
Penetration testing helps organizations:
- Identify security vulnerabilities before attackers do.
- Comply with industry regulations and standards.
- Protect sensitive data and maintain customer trust.
- Improve overall security posture and incident response strategies.
Getting Started With Penetration Testing
Step 1: Understanding the Basics
Before diving into penetration testing, it's crucial to understand some foundational concepts in cybersecurity:
- Threats and vulnerabilities: Understand the difference between threats (potential attacks) and vulnerabilities (weaknesses that can be exploited).
- Attack vectors: Familiarize yourself with common attack vectors, such as phishing, malware, and SQL injection.
- Security testing types: Learn about different types of security testing, including vulnerability assessment, security auditing, and penetration testing.
Step 2: Setting up Your Environment
To start penetration testing, you need a safe and controlled environment. This often involves setting up a lab that mimics real-world conditions but does not affect live systems.
- Virtual Machines (VMs): Use VMs to create isolated environments for testing. Tools like VMware or VirtualBox can help you set up multiple VMs on a single machine.
- Kali Linux: Kali Linux is a Debian-based distribution specifically designed for penetration testing. It comes pre-installed with numerous tools used for security testing.
- Network simulation tools: Tools like GNS3 or Cisco Packet Tracer can help you simulate complex network environments.
Step 3: Learning the Tools
Penetration testers rely on various tools to conduct tests. Some of the most popular tools include:
- Nmap: A network scanning tool used to discover hosts and services on a computer network.
- Metasploit: A framework for developing and executing exploit code against a remote target machine.
- Burp Suite: A comprehensive set of tools for web application security testing.
- Wireshark: A network protocol analyzer used to capture and interactively browse the traffic running on a computer network.
- John the Ripper: A password-cracking tool used to test the strength of passwords.
Step 4: Understanding Legal and Ethical Considerations
Penetration testing involves activities that, if done without permission, can be illegal and unethical. Always ensure you have explicit permission to test the target systems. Familiarize yourself with relevant laws and regulations, such as the Computer Fraud and Abuse Act (CFAA) in the United States.
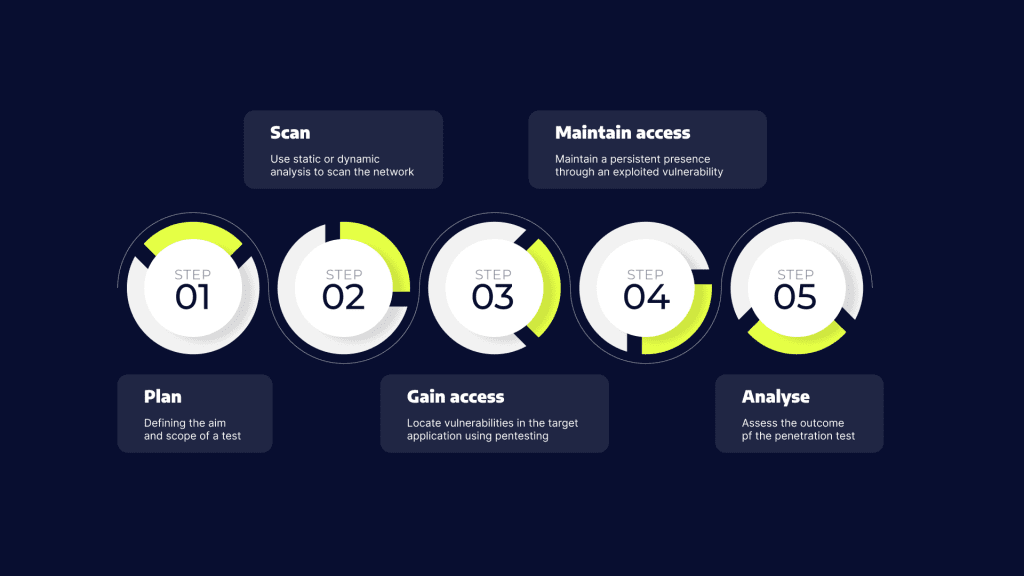
Step 5: Conducting a Penetration Test
A penetration test typically follows these phases:
1. Planning and Reconnaissance
- Define scope and goals: Clearly outline what will be tested and what the objectives are. This includes identifying target systems, testing methods, and success criteria.
- Gather information: Use passive and active reconnaissance techniques to collect as much information as possible about the target. Tools like WHOIS lookup, Google hacking, and social engineering can be useful.
2. Scanning
- Network scanning: Use tools like Nmap to identify open ports, services, and potential vulnerabilities on the target systems.
- Vulnerability scanning: Use automated tools like Nessus or OpenVAS to identify known vulnerabilities.
3. Gaining Access
- Exploitation: Use the information gathered to exploit vulnerabilities and gain access to the target system. Metasploit is a powerful tool for this phase.
- Privilege escalation: Once initial access is obtained, attempt to escalate privileges to gain full control of the system.
4. Maintaining Access
- Persistence: Implement backdoors or other methods to maintain access to the target system over a longer period.
- Covering tracks: Erase evidence of your presence to avoid detection and ensure the target system’s normal operations are not disrupted.
5. Analysis and Reporting
- Data analysis: Analyze the results of the penetration test, including the vulnerabilities exploited, data accessed, and the overall impact.
- Report writing: Create a detailed report that includes findings, evidence, and recommendations for remediation. A good report should be clear and concise, making it easy for the organization to understand the risks and take action.
Step 6: Post-Testing Actions
After completing a penetration test, it’s important to ensure that the organization addresses the identified vulnerabilities. This involves:
- Remediation: Work with the organization’s IT and security teams to fix the identified vulnerabilities.
- Re-testing: Conduct follow-up tests to ensure that the vulnerabilities have been properly addressed.
- Continuous improvement: Penetration testing should be part of an ongoing security strategy. Regularly update your skills, tools, and techniques to stay ahead of evolving threats.
Essential Skills for Penetration Testers
To be successful in penetration testing, you need a mix of technical and non-technical skills:
Technical Skills
- Networking: Understand network protocols, architectures, and devices.
- Operating systems: Proficiency in Windows, Linux, and other operating systems.
- Programming: Knowledge of scripting languages like Python, Bash, or PowerShell.
- Web technologies: Understanding of web application frameworks, databases, and APIs.
Non-Technical Skills
- Analytical thinking: Ability to think like an attacker and identify potential weaknesses.
- Problem-solving: Skills to overcome obstacles and find creative solutions.
- Communication: Ability to write clear reports and explain technical concepts to non-technical stakeholders.
- Ethical mindset: Commitment to ethical hacking practices and adherence to legal standards.
We can significantly enhance the effectiveness of penetration testing by providing automated cloud security solutions tailored to modern environments. Here's how we can complement and bolster the steps and processes outlined in the blog:
Integrating With Penetration Testing
1. Planning and Reconnaissance
Cloud Inventory and Discovery
We can automatically discover and inventory all cloud assets across multiple cloud platforms (AWS, Azure, GCP). This provides penetration testers with a comprehensive list of assets to target, ensuring no resource is overlooked.
Automated Reconnaissance
We can gather detailed information about your cloud infrastructure, such as security groups, VPCs, and IAM roles, streamlining the reconnaissance phase and providing valuable insights into potential attack vectors.
2. Scanning
Vulnerability Assessment
We conduct continuous vulnerability assessments of cloud resources, identifying misconfigurations, outdated software, and other security gaps. This complements traditional network scanning tools like Nmap, providing a more detailed view of cloud-specific vulnerabilities.
Compliance Checks
The platform includes built-in compliance checks for standards such as CIS, NIST, and GDPR. This helps identify non-compliant resources, which are often high-priority targets for penetration testing.
3. Gaining Access
Identifying Exploitable Weaknesses
By leveraging our automated scanning results, penetration testers can quickly pinpoint and prioritize vulnerabilities that are most likely to be exploited. This enhances the efficiency of the exploitation phase, allowing testers to focus on high-impact issues.
Role-Based Access Insights
We provide a detailed analysis of IAM roles and permissions, helping testers understand the potential for privilege escalation and lateral movement within the cloud environment.
4. Maintaining Access
Security Monitoring
We offer continuous monitoring of cloud environments, detecting and alerting on unusual activity. This can be used to evaluate the effectiveness of persistence techniques and to ensure that access can be maintained without detection.
Automated Remediation
The platform can automatically remediate certain issues, such as reverting malicious changes to configurations. This helps in understanding the resilience of the environment against persistent threats.
5. Analysis and Reporting
Comprehensive Reporting
We generate detailed reports of all findings, including vulnerabilities, misconfigurations, and compliance violations. These reports can be integrated into the final penetration testing report, providing a thorough overview of cloud-specific issues.
Actionable Insights
The platform not only identifies issues but also provides actionable recommendations for remediation. This helps organizations quickly address vulnerabilities identified during penetration testing.
Enhancing Penetration Tester Skills and Efficiency
Learning Resources
We offer documentation and support that can help penetration testers understand cloud-specific security challenges and solutions. This complements traditional learning resources and certifications mentioned in the blog.
Hands-On Practice
By using our service in a controlled lab environment, testers can gain hands-on experience with real-world cloud configurations and security issues, enhancing their practical skills.
Community Engagement
Participating in forums and discussions related to us, we can provide penetration testers with insights and best practices shared by other security professionals.
Conclusion
We can greatly enhance the penetration testing process by automating the discovery, assessment, and remediation of cloud-specific security issues. By integrating our services into your penetration testing workflow, you can ensure a more thorough and efficient evaluation of your cloud environment's security posture. This not only helps in identifying and fixing vulnerabilities but also in maintaining continuous compliance and security in dynamic cloud infrastructures.
Incorporating our services into the steps outlined in the blog can provide a more robust and comprehensive approach to penetration testing, particularly for organizations heavily reliant on cloud services.
Published at DZone with permission of Jim Paul. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments