Oracle Maximum Security Architecture
In this article, we will explore the various components of Oracle MSA, how it works, and how it can help businesses protect their sensitive data.
Join the DZone community and get the full member experience.
Join For FreeIn today's world, databases are valuable repositories of sensitive information, and attackers are always on the lookout to target them. This has led to a rise in cybersecurity threats, making it essential to have proper protection measures in place. Oracle Maximum Security Architecture (MSA) is one such solution that provides end-to-end security for databases.
In this article, we will explore the various components of Oracle MSA, how it works, and how it can help businesses protect their sensitive data. We will also look into the different types of attacks that target databases and how Oracle MSA can help prevent them.
Understanding Oracle Maximum Security Architecture
Oracle Maximum Security Architecture (MSA) is a comprehensive solution that provides end-to-end security for databases. It is designed to protect sensitive data and ensure compliance with regulatory requirements. Oracle MSA combines various security features, such as access control, encryption, and auditing, to provide a complete security solution for databases.
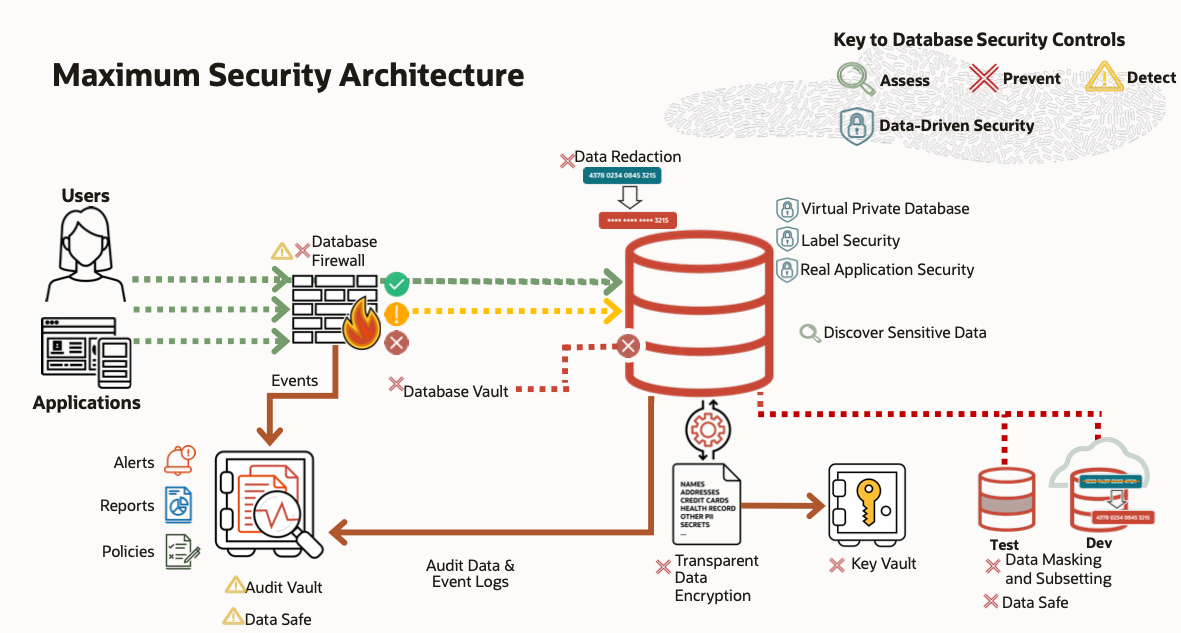
Oracle MSA is built on a foundation of secure hardware, software, and firmware, which are designed to work together seamlessly. It includes different security components like Oracle Database Vault, Oracle Advanced Security, Oracle Key Vault, and Oracle Audit Vault and Database Firewall. These components work together to provide a comprehensive security solution for databases.
Components of Oracle Maximum Security Architecture
Oracle MSA includes several security components that work together to provide a comprehensive security solution for databases. Let's take a closer look at each of these components:
Oracle Advanced Security
Oracle Advanced Security is a database encryption solution that provides data-at-rest encryption. It uses industry-standard encryption algorithms to protect sensitive data stored in databases.
Advanced Security also provides strong authentication and secure communication capabilities, ensuring that data is protected both in transit and at rest.

Key Features
- Transparent Data Encryption
- Encryption of application data in database columns or entire tablespaces
- Built-in encryption key lifecycle management, with assisted key rotation
- Industry-standard algorithms including AES (128, 192, and 256 bit keys)
- Hardware acceleration from Intel® AESNI and Oracle SPARC T-Series
- Oracle Exadata integration, and direct integration with database technologies such as Oracle RMAN, ASM, RAC, Advanced Compression, Active Data Guard, and GoldenGate
- Data Redaction
- On-the-fly redaction to limit exposure of sensitive information in applications
- Declarative redaction policies managed centrally in the database
- Multiple redaction transformations for different application scenarios
- Policy administration using Oracle Enterprise Manager, and direct integration with Oracle SQL Developer
Key Benefits
- Transparent and consistent data security across current and legacy applications
- High-speed implementations
- Easy to deploy and manage
- Fully supports Oracle Multitenant option
Oracle Key Vault
Oracle Key Vault is a key management solution that provides secure storage and management of encryption keys. It helps ensure that encryption keys are properly managed and protected, which is essential for maintaining the security of encrypted data.
Key Vault also provides centralized key management for multiple databases, making it easier to manage encryption keys across an organization.
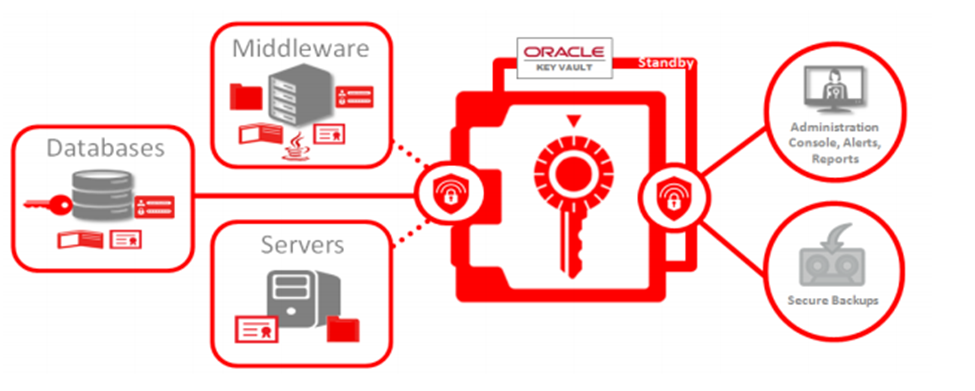
Key Features
- Manages keys, Oracle Wallets, Java Keystores, and credential files in a modern and robust key management platform
- Securely shares keys across authorized endpoints in an enterprise
- Manages key lifecycle stages including creation, rotation, and expiration
- Optimized for Transparent Data Encryption (TDE) master keys
- Easily enrolls and provisions endpoints
- Automates endpoint enrollment using protected RESTful interfaces
- Supports primary and standby for availability and disaster recovery
- Schedules automatic backup to a remote location
- Supports prior database versions without requiring database patching
- Supports Linux, Solaris, AIX, and HP-UX(IA) endpoint platform
Key Benefits
- Monitor key management activity with reports and alerts
- Separate administrator duties for increased security
- Maintain availability and disaster recovery for continuous uptime
- Support OASIS KMIP standard for integration flexibility
Oracle Audit Vault and Database Firewall
Oracle Audit Vault and Database Firewall is a comprehensive auditing and firewall solution for databases. It provides real-time monitoring and alerts for suspicious activity, helping to prevent unauthorized access and data breaches.
Audit Vault and Database Firewall also provides centralized auditing and reporting capabilities, making it easier to maintain compliance with regulatory requirements.
Key Features
- Accurately detects and blocks unauthorized database activity including SQL injection attacks by monitoring traffic to Oracle and non-Oracle databases
- Consolidates audit data and logs generated by databases, operating systems, directories, file systems, and custom sources into a secure centralized repository
- Provides enterprise security intelligence and efficient compliance reporting by combining monitoring and audit data
- Utilizes a unique SQL grammar analysis engine and easy-to-define whitelists and blacklists to ensure high accuracy and performance
- Delivers horizontal and vertical scalability through easy-to-deploy "software appliances"
Key Benefits
- First line of defense: Transparently detect and block SQL injection attacks, privilege escalation, and other threats against Oracle, Microsoft SQL Server, IBM DB2, SAP Sybase, and MySQL databases
- Faster response: Automatically detect unauthorized database activities that violate security policies, and thwart perpetrators from covering their tracks
- Simplified compliance reporting: Easily analyze audit and event data and take action in a timely fashion with out-of-the-box compliance reports
Data Masking and Sub-Setting Packs
The growing security threats have increased the need to limit the exposure of sensitive information. At the same time, copying production data for nonproduction purposes such as test and development is proliferating sensitive data expanding the security and compliance boundary, and increasing the likelihood of data breaches. Oracle Data Masking and Subsetting Pack provide a flexible solution that masks and subsets sensitive production data, allowing the data to be safely shared across non-production environments.
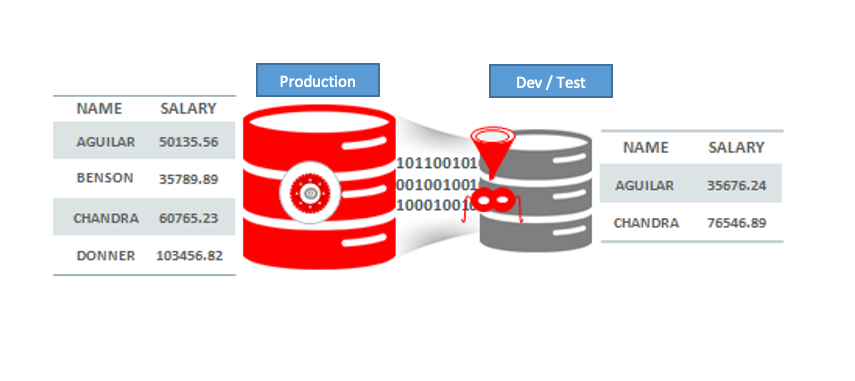
Key Features
- Automated discovery of sensitive columns and parent-child relationships
- Comprehensive and extensible built-in masking transformations
- Creation and reuse of custom templates for applications
- Integrated data subsetting
- Mask and subset in a database or by extraction
- Mask and subset on-premise or in the Oracle Cloud
- High-performance and repeatable process
Key Benefits
- Reduces sensitive data exposure in test and development environments
- Minimizes storage costs by subsetting data
- Improves compliance with information privacy laws and standards
Database Vault
Increase the security of existing applications and address regulatory mandates that call for separation of duties, least privilege, and other preventive controls. Oracle Database Vault proactively protects application data from being accessed by privileged database users. Oracle Database Vault can also help discover Oracle Database runtime privileges without disruption.

Key Features
- Implement preventive controls on privileged user access to application data
- Control database access with multifactor policies that are based on built-in factors such as time of day, IP address, application name, and authentication method
- Consolidate databases and privileged users securely to safeguard enterprise data
- Discover and report on captured runtime privileges and roles used in the database
Key Benefits
- Proactively safeguards application data stored in the Oracle database
- Restrict ad-hoc access to application data by preventing application bypass
- Use multifactor policies that are enforced in the database for high security and performance
- Certified default policies for Oracle E-Business Suite; Oracle’s PeopleSoft and Siebel CRM; and SAP applications
- Enables the reduction of attack surface without disrupting business activity
Label Security
Oracle Label Security (OLS) enables organizations to easily categorize and mediate access to data based on its classification. Designed to meet public-sector requirements for multilevel security and mandatory access control, Oracle Label Security provides a flexible framework that both government and commercial entities worldwide can use to manage access to data on a "need-to-know" basis.

Key Features
- Policy-based architecture
- A single policy can be easily applied to multiple tables
- No PL/SQL coding required
- An optional VPD clause can be added to the policy
- Flexible enforcement options
- Full Control, Read Control Only, Write Control Only
- Default, or function-defined, data classification assignment
- Flexible authorizations
- READ and WRITE levels, compartments, groups
- READ, FULL, Proxy privileges
- Trusted Stored Procedures
Key Benefits
- Ensure access to sensitive data is restricted to users with the appropriate clearance level
- Enforce regulatory compliance with a policy-based administration model
- Establish custom data classification schemes for implementing “need to know” access for applications
- Labels can be used as factors within Oracle Database Vault command rules for multifactor authorization policies
- Integrates with Oracle Identity Management, enabling centralized management of policy definitions
SQL Injection Attacks
SQL injection attacks are one of the most common types of attacks on databases. They involve injecting malicious code into a database query, which can be used to steal sensitive data or take control of the database.
Insider Threats
Insider threats are attacks that come from within an organization. They can be caused by employees with authorized access to sensitive data who abuse their privileges or accidentally expose sensitive data.
Data Breaches
Data breaches are attacks that involve stealing sensitive data from a database. They can be caused by a variety of factors, including weak passwords, unsecured network connections, and outdated software.
Conclusion
In conclusion, Oracle Maximum Security Architecture is a comprehensive security solution that provides end-to-end protection for databases. It combines various security components, such as access control, encryption, and auditing, to provide a complete security solution for databases.
By understanding the different types of database security threats and implementing Oracle MSA, businesses can protect their sensitive data and ensure compliance with regulatory requirements.
Opinions expressed by DZone contributors are their own.

Comments