Security by Design: NIST Framework Implementation for Developers
Many organizations struggle with cybersecurity risk management, giving rise to security by design as an essential strategy for building resilient software systems.
Join the DZone community and get the full member experience.
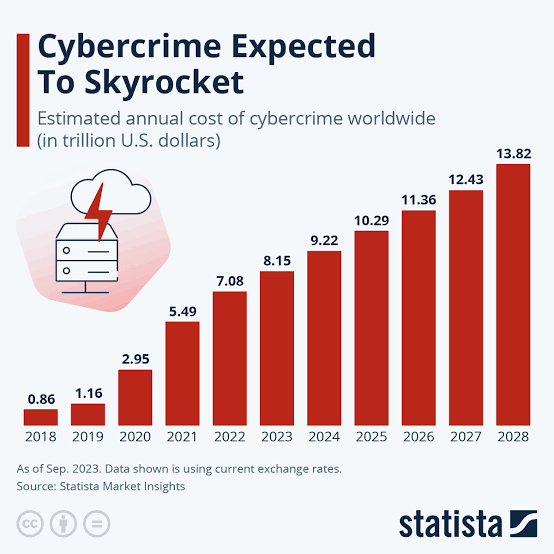
Join For FreeAccording to Statista, the global cost of cybercrime is over $9 trillion. This staggering sum, which has been rising for years and is poised to continue its upward trajectory, is despite the fact that cybersecurity spending keeps rising across the board.
Many organizations struggle with cybersecurity risk management and as a result, security by design has become an essential strategy for mitigating risks and building resilient software systems.
In this article, we'll explore the concept of security by design through the lens of the NIST Cybersecurity Framework (CSF) 2.0, a widely recognized set of guidelines for managing and mitigating cybersecurity risks.
As a developer, being aware of the role you play in organizational resilience is critical for building reliable applications.
Understanding the NIST CSF
The NIST CSF 2.0, released in 2024, provides a valuable framework for implementing security by design principles. Its first version was released a decade ago and was primarily designed for critical infrastructure sectors, but wider industries found use for its adoption.
The latest version was released in February and does have an expanded scope, in addition to some new guidance on cybersecurity risk management.

The NIST CSF was originally organized around five major functions: Identify, Protect, Detect, Respond, and Recover, and all are designed to work in concert to provide a comprehensive view of cybersecurity risk management.
The Functions of CSF
For adequate risk management, you need to first gain adequate understanding of your organization’s cybersecurity risks related to systems, assets, data, and capabilities (Identify).
It’s only then that you can develop and implement the appropriate safeguards to ensure the uninterrupted delivery of services. So, the Protect function includes activities such as access control, data security, awareness and training, information security, maintenance, etc.
Yet, if there is any lesson that has been learned over the past few years, it is that the devil might work hard, but cyber threat actors certainly do work harder. That’s why it seems that even the most sophisticated protection mechanisms can be infiltrated, often through seemingly small risks.
As such, organizations need to have appropriate tools and mechanisms in place to identify the occurrence of cybersecurity events (Detect), as well as take action rapidly (Respond), and restore any capabilities or services impaired due to the incident (Recover).

The Govern Function
With the introduction of CSF 2.0, though, a sixth function, Govern, was added to the original list to emphasize the importance of aligning cybersecurity efforts with overarching business objectives. As the threat of cyberattacks grows, the corporate world has come to terms with ensuring executive-level involvement in cybersecurity risk management.
The responsibilities of executive leadership, according to the latest Framework, are, however, beyond providing strategic guidance and policy direction. Management must take an active part in maintaining oversight over risk management activities and outcomes. So, the Govern function is the backbone of CSF 2.0 and it ties all other functions together.
Implementing the NIST CSF for Developers
While the Govern function in NIST CSF 2.0 primarily targets organizational leadership, it indirectly influences how developers implement the framework’s recommendations.
It achieves this by setting the stage for a security-conscious organizational culture and providing developers with the necessary context, guidance, and support to integrate security into every stage of the software development lifecycle.
Incorporate Security in Early Design Stages
The NIST CSF emphasizes a proactive and iterative approach to cybersecurity risk management, and this principle is especially relevant for software development.
Incorporating threat-informed defense considerations from the earliest stages of software design is significantly more effective and less costly than trying to bolt on security measures later in the development lifecycle.
By "shifting left," developers can address vulnerabilities before they become exploitable weaknesses in a released product. One way to achieve this is through efficient threat modeling.
That is, analyzing the system from the attacker’s perspective, anticipating potential attack vectors, and identifying weaknesses that could be exploited. Examples of threat modeling practices for developers include the STRIDE, PASTA, and VAST models.
Secure Coding Practices
Secure coding is fundamental to building software that is resilient to attacks. However, data shows that not many developers prioritize it as much as they should.

Figure sourced from Secure Code Warrior
Some major secure coding practices highlighted in NIST guidelines include:
- Input validation: This involves verifying all data received by the software from external sources. This may be data entered by users, received from APIs, or obtained from databases. By validating input, developers can prevent a wide range of injection attacks.
- Output encoding: Transforming data before it is sent to an output stream (such as a web browser, database, or command-line interface) is good practice for preventing risks such as cross-site scripting (XSS) vulnerabilities. Data not adequately sanitized can compromise data integrity, whether at rest or in transit.
- Parameterized queries: These are also known as prepared statements and are a technique of interacting with databases securely by using placeholders for user-supplied values instead of embedding user input directly into SQL queries. The database then treats these values as data rather than executable code.
- Memory-safe programming languages: Memory-safe languages, like C#, Rust, and Go, incorporate features that prevent common memory-related vulnerabilities, such as buffer overflows and dangling pointers, which can lead to arbitrary code execution.
- Secure logging and error handling: Secure logging involves recording security-relevant events in a tamper-proof manner, providing an audit trail for incident response. Secure error handling ensures that errors do not reveal sensitive information to attackers or lead to unexpected application behavior.
Secure Software Development Framework
In addition to the CSF 2.0 guidelines, NIST has also provided the companion that developers can use to align their practices and activities with CSF goals. The SSDF divides these secure practices into four main groups:
- Prepare the organization by defining security requirements, establishing a secure software development environment, and defining the criteria for software security checks, etc.
- Protect the software from unauthorized access, use, modification, and release. This also includes verifying software release integrity.
- Focus on producing well-secured software through a variety of security considerations during the software design and development phases.
- Identify, assess, and respond to software vulnerabilities in a timely manner. This is all about incident response.
By adopting the secure software development practices detailed in the NIST SSDF, developers can directly contribute to their organization's ability to meet the outcomes outlined in the NIST CSF.
Conclusion
Clearly, developers are essential to risk management, and they play a crucial role in identifying, reporting, and remediating vulnerabilities.
Through secure coding practices, regular code reviews and analysis, rigorous testing procedures, and staying abreast of the latest security threats, developers can do a lot to reduce their organization’s risk exposure and enhance its overall security posture.
Don't forget that the CSF is designed to be a living document, constantly evolving to address new threats, technologies, and lessons learned. For developers, this means that security is not a one-time effort but an ongoing process of improvement.
Opinions expressed by DZone contributors are their own.

Comments