Building Secure Cloud Applications: A Developer’s Companion to NIST CSF
A developer's guide to building a secure cloud environment with the NIST Cybersecurity Framework.
Join the DZone community and get the full member experience.
Join For FreeThe National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) stands as a beacon of guidance for organizations navigating the intricate landscape of cybersecurity. In an era where cloud computing has become integral to software development, the fusion of NIST CSF principles with cloud security is paramount. This comprehensive guide is tailored specifically for developers, offering insights and actionable recommendations to fortify their endeavors in the cloud.
Core Functions
As developers navigate through the core functions, they gain a holistic understanding of how the NIST CSF can be applied to enhance security practices in the cloud. The guidance provided empowers developers to integrate security seamlessly into the software development lifecycle for cloud-based applications, fostering a resilient and secure computing environment.
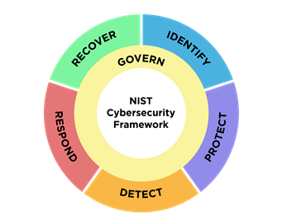
- Identify: The "Identify" function involves understanding and managing cybersecurity risks in the cloud. Developers will gain insights into how to identify assets, data, and potential risks specific to cloud environments.
- Protect: The "Protect" function focuses on implementing safeguards to ensure the security of cloud-based applications and data. Developers will receive guidance on protective measures such as encryption, access controls, and secure configurations tailored for cloud environments.
- Detect: Developers learn strategies for identifying and monitoring cybersecurity events and anomalies in cloud systems. This includes insights into cloud-specific threat detection methods, monitoring practices, and tools to enhance the ability to promptly detect and respond to security incidents in a cloud environment.
- Respond: The "Respond" function addresses the actions developers should take in the event of a cybersecurity incident in the cloud. This provides guidance on creating cloud-specific incident response plans, coordination strategies, and best practices for effectively responding to and containing incidents, minimizing potential damages.
- Recover: The "Recover" function helps explore strategies for recovering from cybersecurity incidents in the cloud. This includes continuity and recovery planning specific to cloud environments
Applicability of NIST CSF to Cloud Environments
It is imperative for developers to understand the specific cloud service and deployment models in use, aligning the NIST CSF's principles with the nuances of the cloud environment. Data classification and sensitivity play a pivotal role, guiding developers to implement security controls that safeguard crucial information. A comprehensive risk assessment, tailored to the intricacies of cloud computing, must be conducted, prioritizing risks identified in alignment with the CSF's "Identify" function. Integration with cloud security standards, diligent identity and access management practices, encryption for data protection, and incident response planning tailored for the cloud are paramount. Continuous monitoring tools and cross-functional collaboration ensure real-time detection and response, while adherence to regulatory compliance standards is vital for robust cloud security. By addressing these considerations, developers can seamlessly apply the NIST CSF to cloud environments, fortifying their applications against evolving cybersecurity challenges.
Guidelines and Best Practices
Identify (NIST CSF) in Cloud Environments
Identifying assets, data, and risks specific to cloud environments requires a strategic approach. Here are the top three guidelines:
- Comprehensive Cloud Asset Inventory: Maintain an up-to-date inventory of all cloud assets, including virtual machines, storage, databases, and network components. Leverage automated tools and cloud provider resources for accurate asset tracking.
- Data Classification and Mapping: Classify data based on sensitivity and relevance to the organization. Map data flows within the cloud ecosystem to understand how data moves between different cloud services and storage.
- Thorough Risk Assessment: Conduct regular and thorough risk assessments that account for both general cybersecurity risks and those specific to cloud environments. Prioritize risks based on their potential impact on cloud assets and data.
Protect (NIST CSF) in Cloud Security
By implementing protective measures, organizations can significantly enhance the security of their cloud-based systems, safeguarding against unauthorized access and potential data breaches. Here are the top three recommendations:
- Encryption Practices: NIST CSF emphasizes the importance of robust encryption practices to secure data both in transit and at rest within the cloud. Implementing strong encryption algorithms and adhering to recommended cryptographic protocols are key components of safeguarding sensitive information.
- Access Controls and Least Privilege: NIST advocates for the principle of least privilege and effective access controls. Ensuring that users have the minimum necessary access for their roles helps mitigate the risk of unauthorized access to cloud-based applications and data. Cloud provider Identity and Access Management (IAM) tools can be leveraged for precise control.
- Secure Configurations and Continuous Monitoring: NIST encourages organizations to follow secure configuration best practices provided by cloud services. Regularly auditing and updating configurations help address potential vulnerabilities. Additionally, continuous monitoring is crucial to detect and respond to security incidents promptly, aligning with NIST's emphasis on the "Detect" function.
Detect (NIST CSF) in Cloud Environments
Detecting cybersecurity events and anomalies in cloud systems requires strategic approaches to promptly identify potential threats. Here are the top three strategies:
- Implement Advanced Threat Detection Tools: Deploy advanced threat detection tools designed for cloud environments. These tools often leverage machine learning, behavioral analytics, and anomaly detection to identify unusual patterns of behavior that may indicate a cybersecurity incident.
- Utilize Cloud-Native Security Services: Leverage cloud-native security services provided by cloud service providers. These services often include features such as cloud security information and event management (SIEM), which can aggregate and analyze logs and events from various cloud resources to detect anomalies.
- Establish Continuous Monitoring: Implement continuous monitoring practices to track activities and events in real-time within the cloud environment. This proactive approach allows organizations to quickly detect deviations from normal behavior and respond promptly to potential security threats.
Respond (NIST CSF) to Cloud Security Incidents
Organizations can develop a robust and tailored approach to responding to and containing cybersecurity incidents in cloud environments, fostering resilience and minimizing potential damages.
- Develop and Test Cloud-Specific Incident Response Plans: NIST CSF emphasizes the importance of creating incident response plans tailored specifically for cloud environments. These plans should outline procedures for identifying, responding to, and recovering from incidents in the cloud. Regular testing and simulation exercises ensure the effectiveness of these plans.
- Coordinate and Collaborate Across Stakeholders: The framework underscores the need for coordination and collaboration among various stakeholders, including cloud service providers, internal teams, and external partners. Establishing clear communication channels and response protocols enhances the organization's ability to contain and mitigate incidents in a timely manner.
- Leverage Continuous Monitoring for Early Detection: NIST encourages the implementation of continuous monitoring practices in the cloud. Continuous monitoring helps detect cybersecurity incidents at an early stage, enabling a faster response and containment. Integrating automated tools for real-time threat detection enhances the organization's overall incident response capabilities.
Recover (NIST CSF) in Cloud Security
To strengthen the ability to recover from cybersecurity incidents in the cloud, the following approaches ensure a resilient and adaptive cybersecurity posture.
- Develop and Test Cloud-Specific Recovery Plans: NIST CSF emphasizes the importance of having recovery plans specifically tailored for cloud environments. These plans should outline steps for restoring systems and data in the cloud after a cybersecurity incident. Regular testing and validation of these plans ensure their effectiveness and the organization's ability to resume normal operations.
- Prioritize Cloud-Based Continuity and Resilience: The framework encourages organizations to prioritize continuity and resilience planning in the cloud. This involves identifying critical cloud services and data, implementing backup and redundancy measures, and ensuring the availability of resources needed for recovery. By prioritizing cloud-based continuity, organizations enhance their ability to recover swiftly from incidents.
- Integrate Lessons Learned for Continuous Improvement: NIST CSF advocates for a continuous improvement mindset in the recovery phase. Organizations should conduct post-incident reviews, analyze the effectiveness of their response and recovery efforts, and integrate lessons learned into future recovery plans. This iterative approach helps refine and enhance recovery capabilities over time.
Integrating NIST CSF Into the SDLC for Cloud-Based Applications
Integrating the NIST CSF into the Software Development Lifecycle (SDLC) for cloud-based applications is paramount.
- Begin by embedding security seamlessly across all SDLC phases, from planning to maintenance, treating it as an integral aspect of development. Align NIST CSF functions with SDLC stages, mapping Identify, Protect, Detect, Respond, and Recover to corresponding development steps.
- Implement secure coding practices specific to cloud environments, addressing encryption, access controls, and configurations. Integrate automated security testing into the continuous integration/continuous deployment (CI/CD) pipeline to identify vulnerabilities early.
- Provide comprehensive developer training on NIST CSF principles, fostering a deep understanding of security best practices in cloud contexts.
- Conduct regular security reviews and assessments aligned with NIST CSF recommendations, emphasizing continuous monitoring for cloud security throughout the SDLC.
- Clearly document and communicate security requirements, ensuring adherence and awareness among development teams.
This holistic approach enhances the security resilience of cloud-based applications and mitigates risks throughout the development lifecycle.
Challenges and Considerations
Applying the NIST CSF in cloud security introduces specific challenges and considerations that organizations must address to ensure effective implementation. Here are some challenges and potential ways to overcome them:
- Dynamic Cloud Environment:
- Challenge: Cloud environments are dynamic and scalable, making it challenging to maintain a comprehensive and up-to-date inventory of assets.
- Overcoming Obstacles: Leverage automated tools provided by cloud service providers for asset discovery. Implement continuous monitoring to dynamically adjust security measures in response to changes in the cloud environment.
- Shared Responsibility Model:
- Challenge: Cloud security operates under a shared responsibility model where both the cloud service provider and the customer have specific security responsibilities. Coordinating these responsibilities can be complex.
- Overcoming Obstacles: Clearly define and understand the delineation of responsibilities between the cloud provider and the organization. Implement strong communication channels to address security aspects collaboratively.
- Data Privacy and Compliance:
- Challenge: Navigating data privacy regulations and compliance requirements in different jurisdictions can be complex, especially when data is stored and processed in the cloud.
- Overcoming Obstacles: Stay informed about regional and industry-specific compliance requirements. Work closely with legal and compliance teams to ensure cloud security practices align with regulatory standards.
- Integration With DevOps:
- Challenge: Integrating NIST CSF into DevOps processes requires aligning security practices with the speed and agility of continuous integration and continuous deployment (CI/CD) pipelines.
- Overcoming Obstacles: Implement DevSecOps practices to embed security into the development lifecycle seamlessly. Use automation to incorporate security checks into CI/CD pipelines without impeding development speed.
- Vendor Management:
- Challenge: Organizations often rely on multiple cloud service providers, each with its security measures and interfaces.
- Overcoming Obstacles: Standardize security controls across cloud providers when possible. Develop a consistent approach to vendor risk management, including security assessments and due diligence.
- Identity and Access Management (IAM):
- Challenge: Managing user identities and access controls in dynamic cloud environments can be challenging, leading to the risk of unauthorized access.
- Overcoming Obstacles: Implement robust IAM practices, such as the principle of least privilege, multi-factor authentication, and regular reviews of access permissions. Leverage cloud provider IAM tools effectively.
- Incident Response in the Cloud:
- Challenge: Adapting incident response plans to the cloud requires considerations for the unique characteristics of cloud environments.
- Overcoming Obstacles: Develop and test cloud-specific incident response plans. Ensure coordination with the cloud service provider and incorporate cloud-native monitoring and detection tools.
Future Trends
The evolution of the NIST CSF to address future challenges is likely to involve updates and enhancements to keep pace with the dynamic nature of cybersecurity threats and technology advancements.
- Integration With Emerging Technologies: As new technologies, such as artificial intelligence, machine learning, and the Internet of Things (IoT), become more prevalent, the NIST CSF may evolve to provide specific guidance on integrating these technologies securely.
- Deeper Focus on Supply Chain Security: This may involve providing organizations with guidelines for assessing and mitigating cybersecurity risks throughout the supply chain, from third-party vendors to interconnected partners
- Enhanced Threat Intelligence Integration: The NIST may evolve to provide guidance on leveraging threat intelligence feeds, collaborating with cybersecurity information-sharing organizations, and implementing effective threat detection and response strategies.
- International Collaboration and Standardization: The NIST CSF may continue to foster international collaboration and standardization efforts. This could involve aligning the framework with global cybersecurity standards and frameworks, promoting interoperability, and addressing the challenges of cross-border cybersecurity threats.
- Cloud-Native Security Considerations: With the continued adoption of cloud computing, the NIST CSF might offer more granular guidance on cloud-native security considerations. This could include recommendations for securing serverless architectures, containerized applications, and other cloud-native technologies, as well as addressing the challenges associated with shared responsibility models.
Opinions expressed by DZone contributors are their own.

Comments