Kata Containers: From Kubernetes Pods to Secure VMs
Kata containers bridge the gap between Kubernetes pods and secure VMs, offering enhanced isolation without sacrificing performance.
Join the DZone community and get the full member experience.
Join For FreeIntroduction to Kata Containers
Kata Containers is an open-source project designed to deliver a secure container runtime environment by utilizing the virtualization layer provided by the server instance. Unlike traditional containers, Kata containers run within lightweight virtual machines (VMs) created using virtualization capabilities. This approach ensures robust isolation between the host operating system (OS) and the containers, making them a powerful choice for scenarios demanding heightened security.
The Core Difference: Kata vs. Conventional Containers
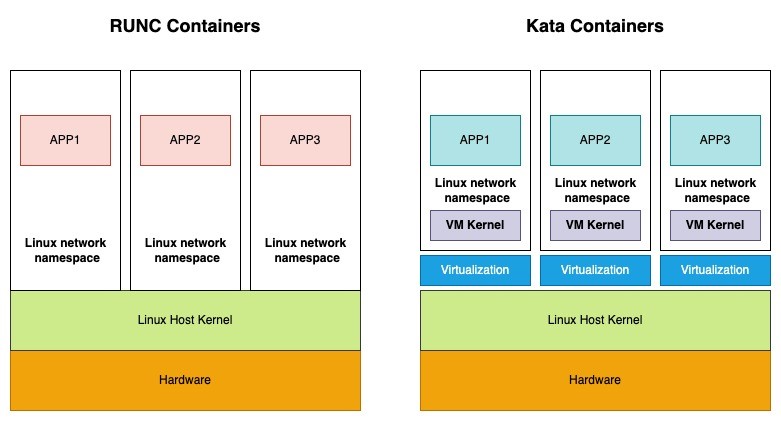
Conventional containers are software packages that share the host OS kernel for isolated execution. They achieve isolation using Linux technologies such as network namespaces and c-groups.
In contrast, Kata containers add an extra layer of isolation through virtualization. Each container runs within its own lightweight VM, complete with its own OS and kernel. This architecture significantly enhances security by creating a stronger separation between the container and the host system.
| Feature | Traditional Containers | KATA CONTAINERS |
|---|---|---|
|
Isolation |
Shares host kernel |
Dedicated VM and kernel |
|
Security |
Limited to namespaces and cgroups |
Strong isolation via VMs |
|
Performance |
High performance, low overhead |
Slightly higher overhead |
|
Attack Surface |
Broader due to shared kernel |
Narrower with kernel isolation |
Architectural Overview
Kata containers leverage a unique architecture that combines the lightweight nature of containers with the strong isolation provided by virtual machines (VMs).

Core Components
- Kata runtime. Acts as the interface between the container ecosystem (e.g., Docker, Kubernetes) and the underlying hypervisor. Implements the Open Container Initiative (OCI) runtime specification, ensuring compatibility with container orchestration tools. Responsible for launching a lightweight VM to encapsulate the container.
- Lightweight hypervisor. Provides the virtualization layer, ensuring strong isolation for the container by creating a dedicated VM. Optimized for speed and reduced overhead compared to traditional hypervisors.
- Guest kernel. Each container (or pod) runs inside its own VM with a dedicated kernel. Ensures complete isolation from the host and other containers, reducing the attack surface.
- Agent. A small process running inside the VM that manages the container lifecycle. Facilitates communication between the Kata Runtime (on the host) and the container workload inside the VM. Executes commands like starting, stopping, and monitoring the container.
Interaction Workflow
- Request initiation. A container creation request (e.g.,
docker runor a Kubernetes pod) triggers the Kata Runtime. - VM creation. The runtime communicates with the hypervisor to start a lightweight VM. A minimal guest kernel is loaded into the VM.
- Container setup. The runtime injects the container image into the VM and starts it using the agent.
- Lifecycle management. The agent within the VM handles container commands, such as starting processes, networking setup, and monitoring.
Benefits of Kata Containers
Below are some advantages of using Kata containers for secured containerized workflows.
- Strong isolation. Each container runs inside its own lightweight VM with a dedicated kernel. This helps prevent container escape vulnerabilities and provides multi-tenant workload isolation.
- Enhanced security. They reduce attack surfaces by isolating workloads at the kernel level.
- Compatibility with container ecosystems. They are fully compliant with OCI runtime standards.
- Lightweight virtualization. Each container uses lightweight hypervisors (e.g., QEMU, Firecracker) for minimal overhead.
- Multi-Tenant workload isolation. Kata containers prevent data leakage or interference between tenants.
- Improved compliance. They meet stringent compliance and regulatory requirements (e.g., GDPR, HIPAA).
- Open-source and community-driven. They are backed by an active open-source community under the Open Infrastructure Foundation (OpenStack).
Why Kata Containers Are Not Always the Right Fit
While they offer strong security and isolation, the unique architecture of Kata containers may not suit every workload or environment. Below are some examples.
- Applications requiring maximum performance. The VM-based architecture introduces additional overhead compared to traditional containers.
- Resource-constrained environments. Lightweight hypervisors consume more resources (e.g., memory and CPU) than traditional container runtimes.
- Lightweight, temporary workloads. For ephemeral or short-lived workloads, the overhead of starting a VM outweighs the security benefits.
- Cost-sensitive deployments. The increased resource consumption (e.g., memory and CPU) for each container results in higher infrastructure costs compared to traditional containers.
- Applications needing direct access to host hardware. The VM abstraction layer limits direct access to host devices like GPUs or specialized hardware.
- Environments with heavy networking requirements. Network performance can be slightly slower because of the added virtualization layer.
- Scenarios without compliance or security needs. If compliance and security isolation are not critical, traditional containers offer simpler and faster solutions.
Conclusion
Kata containers combine the speed and efficiency of Kubernetes pods with the strong security of virtual machines. They provide enhanced isolation, making them ideal for multi-tenant environments, sensitive applications, and compliance-driven workloads. They ultimately enable organizations to achieve operational efficiency and security by bridging the gap between containers and VMs.
Stay tuned for Part 2, where we’ll provide a step-by-step guide to deploying and validating Kata containers in a practical cloud environment.
Opinions expressed by DZone contributors are their own.

Comments