Implementing One and Two Way SSL (Mutual Authentication) for MuleSoft Application
In this article, we will be going to learn how to set up the one-way SSL and two-way SSL for MuleSoft applications.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
In one-way SSL authentication, the server application shares its public certificate with the client. In a two-way authentication, the client application verifies the identity of the server application, and then the server application verifies the identity of the client application. Sometimes two-way SSL is also known as Mutual Authentication.
In this article, we will be going to learn how to set up the one-way SSL and two-way SSL for MuleSoft applications.
One Way SSL
As mentioned above in one way SSL only client verifies the server certificates. At the server end, there will be a Keystore that will hold the private and public certificate of the server whereas, at the client end, there will be a truststore that will hold the public certificate of the server.
- Clients will send Hello and request for the resources on the secure HTTPS protocol.
- The server will respond with its public certificate (.crt) and send Hello.
- The client will verify the server public certificate in its truststore.
- The client sends back symmetric session key generated using the server public certificate.
- The server will decrypt the symmetric session key using its private certificate and send back the encrypted session key to the client for establishing a secure connection.
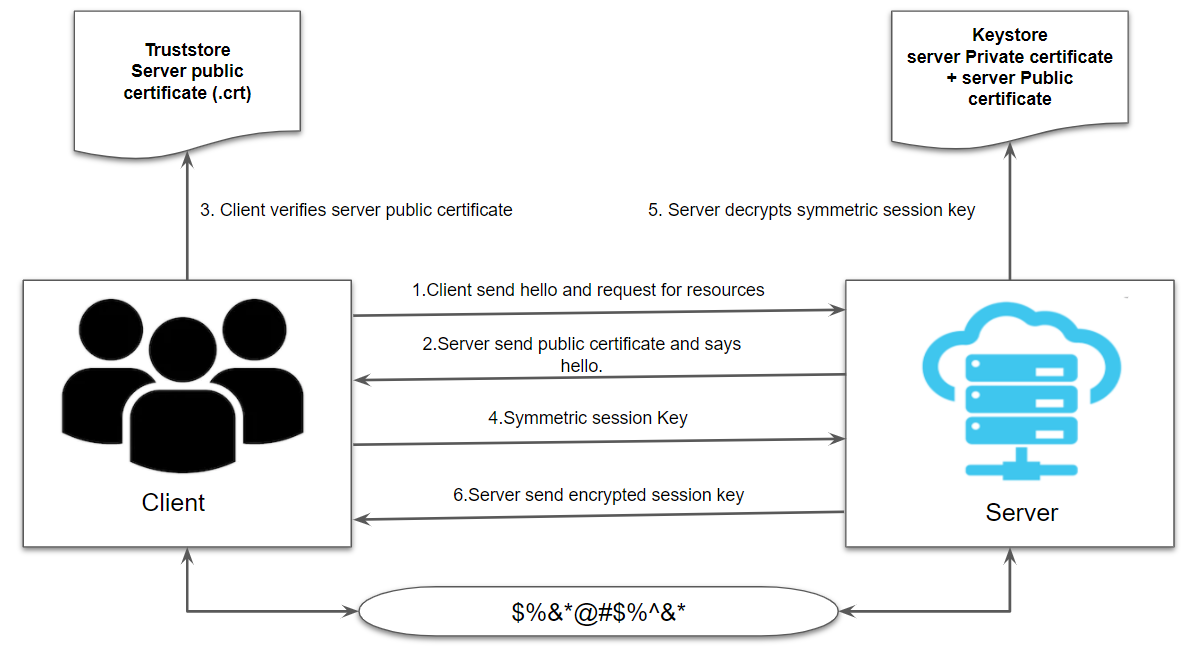
Implementing One Way SSL For MuleSoft Application
For generating Keystore and truststore, we can use OpenSSL or keytool utility. For this article, we will be using keytool which is part of your JDK.
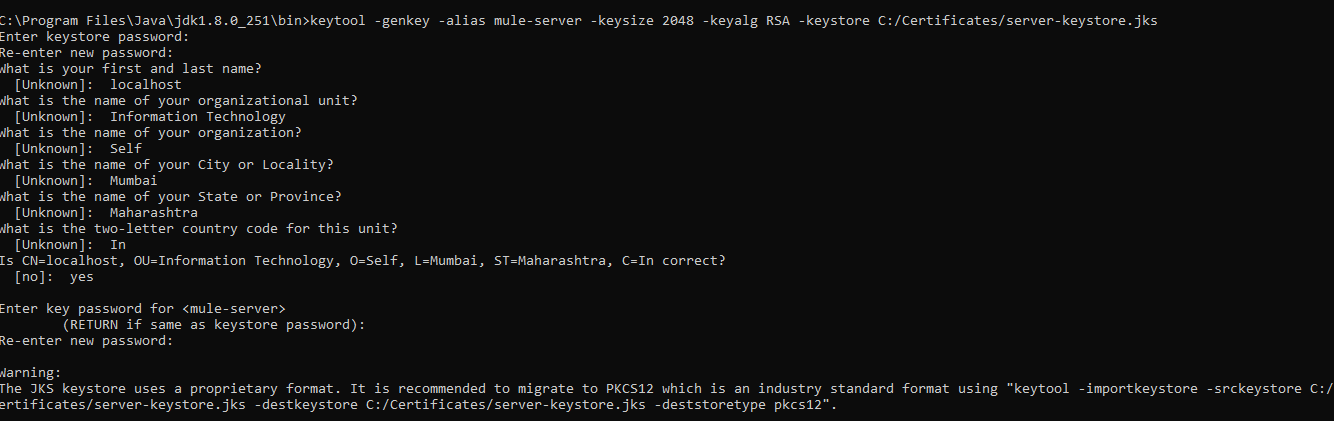
Step 1: Generate Server Keystore
For generating Keystore, we will be using the below command.
keytool -genkey -alias mule-server -keysize 2048 -keyalg RSA -keystore C:/Certificates/server-keystore.jks
Once we execute the above command, it will ask for the Keystore password, first and last name including other details and the key password.
alias in the above command is used to search the certificate in the Keystore as there can be multiple certificates in the same Keystore and alias is useful in identifying the right certificate.
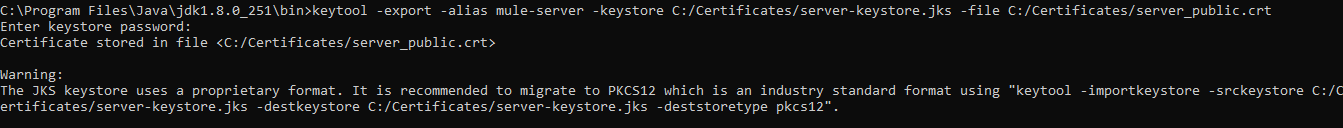
Step 2: Export the Public Certificate From Server Keystore
We will be requiring the server public certificate to be installed in the client truststore. So we need to extract the public key from the server Keystore.
For extracting the server public certificate, we will be using the below export command.
x
keytool -export -alias mule-server -keystore C:/Certificates/server-keystore.jks -file C:/Certificates/server_public.crt
This command will export the server public certificate and we will import that server public certificate in the client truststore.
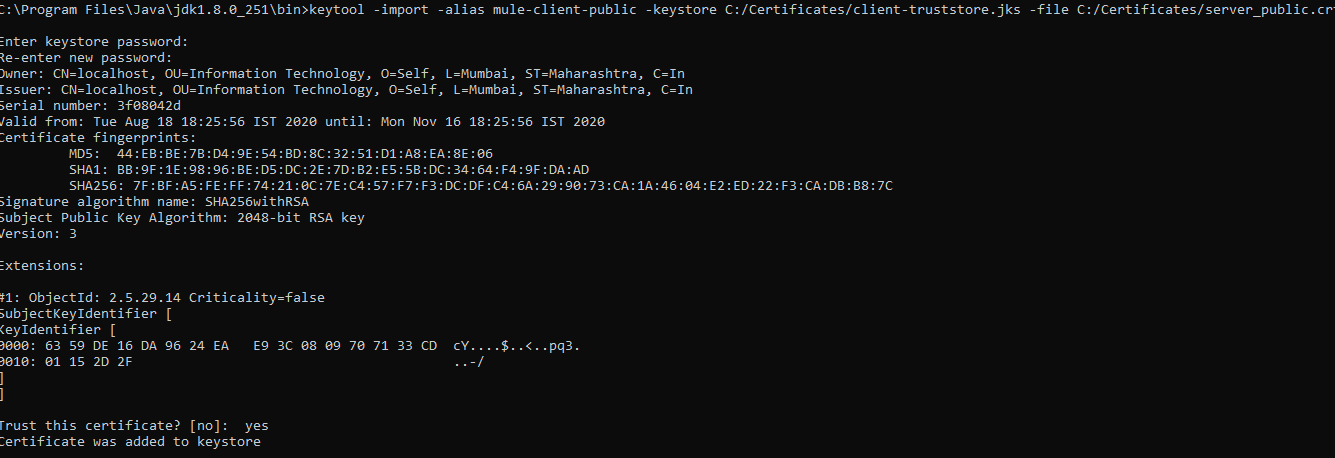
Step 3: Import Server Public Certificate Into Client Truststore
For importing the server public key into the client truststore, we will be using the below command.
x
keytool -import -alias mule-client-public -keystore C:/Certificates/client-truststore.jks -file C:/Certificates/server_public.crt
This above command will generate the client's truststore and import the server public certificate.
 Now, we have generated the server Keystore and client truststore.
Now, we have generated the server Keystore and client truststore.
Step 4: Configuring MuleSoft HTTP Listener and Requester
Let's see how we can configure Keystore and truststore on the MuleSoft application.
Now, we will configure the server-Keystore on the MuleSoft HTTP Listener. Under General Settings, the Protocol must be "HTTPS". We need to make sure server-Keystore.jks and client-truststore.jks that are generated in the above steps, must be copied under folder src/main/resources.
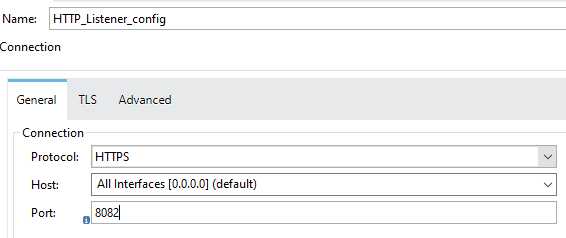
Now, we will perform a TLS Key Store configuration. Provider Type, Keystore Path, Keystore and key password, and alias name.
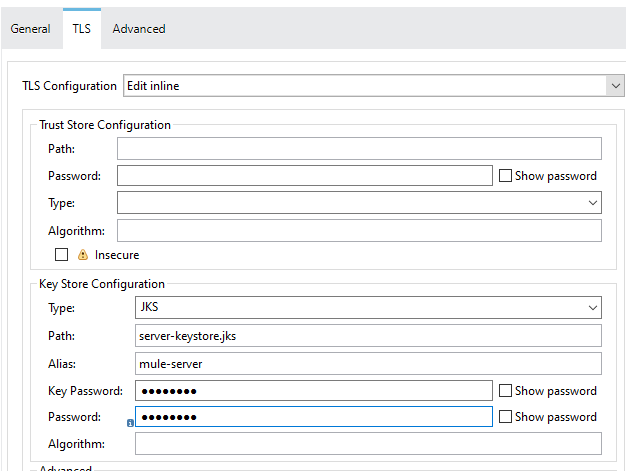
This is the configuration that needs to be done on the server-side.
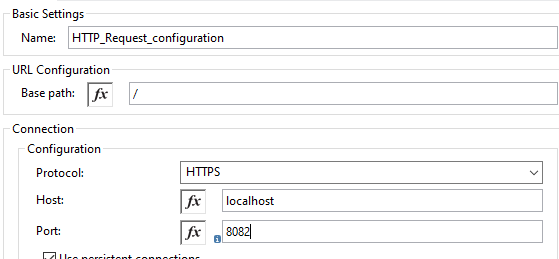
Now, we will see the client-side configuration. For that, we will be using the MuleSoft HTTP requester. Provide the connection settings on the HTTP requester.
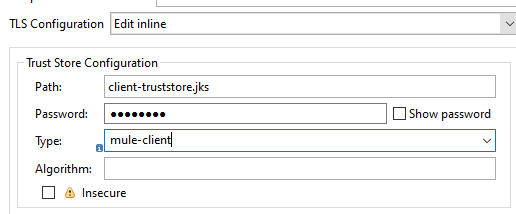
 Now, we will do the TLS configuration. Provide the client's truststore path, password, type, etc.
Now, we will do the TLS configuration. Provide the client's truststore path, password, type, etc.
For more details on the implementing one-way SSL for the MuleSoft application, please go through below video tutorial.
Two Way SSL (Mutual Authentication)
As mentioned above in two ways SSL client verifies the server certificates and the server verifies the client certificates.
At the server end, there will be a Keystore which will hold the private and public certificate of the server and truststore which will hold the public certificate of client whereas, at the client end, there will be a Keystore which will hold the private and public certificate of client whereas truststore which will hold the public key of the server.
- Clients will send Hello and request for the resources on the secure HTTPS protocol.
- The server will respond with its public certificate (.crt) and send Hello.
- The client will verify the server public certificate in its truststore.
- The client sends back symmetric session key generated using the server public certificate.
- The server will decrypt the symmetric session key using the server private certificate and request for the client certificate.
- The client will send its public certificate to the server and the server will verify the client public certificate in the server truststore.
- The server will generate a session key and encrypt using the client public certificate and send it to the client.
- The client will decrypt the session key using client private certificate and this way the key exchange between client and server. It will establish secure communication between client and server.
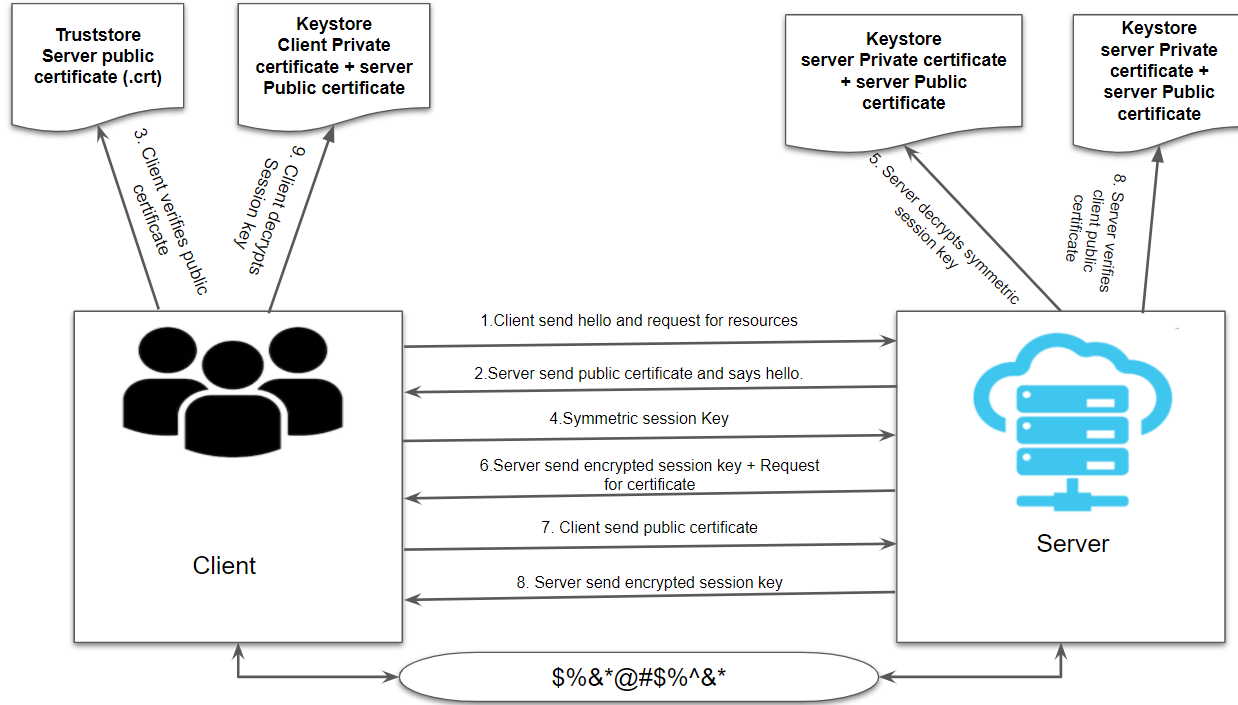
Implementing Two Way SSL For MuleSoft Application
For generating Keystore and truststore, we can use OpenSSL or keytool utility. For this article, we will be using keytool which is part of your JDK.
Step 1: Generate Server Keystore
For generating the server Keystore, we will be using the below command.
xxxxxxxxxx
keytool -genkey -alias mule-server -keysize 2048 -keyalg RSA -keystore C:/Certificates/server-keystore.jks
Once we execute the above command, it will ask for the Keystore password, first and last name including other details and the key password.
alias in the above command is used to search the certificate in the Keystore as there can be multiple certificates in the same Keystore and alias is useful in identifying the right certificate.

Step 2: Export the Public Certificate From Server Keystore
We will be requiring the server public certificate to be installed in the client truststore. So we need to extract the public key from the server Keystore. For extracting the server public certificate, we will be using the below export command.
x
keytool -export -alias mule-server -keystore C:/Certificates/server-keystore.jks -file C:/Certificates/server_public.crt
This command will export the server public certificate and we will import that server public certificate in the client truststore.

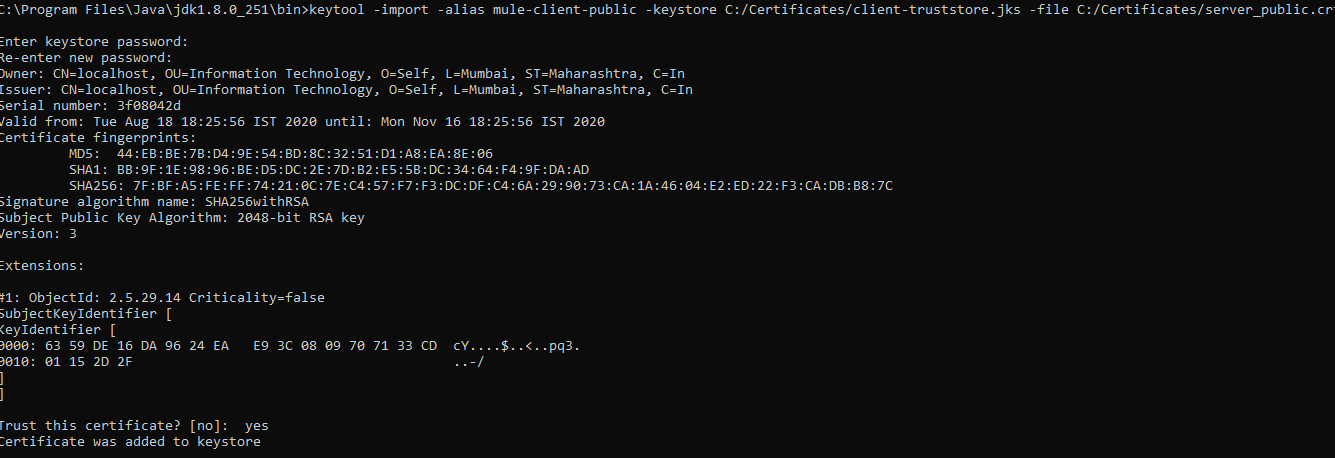
Step 3: Import Server Public Certificate Into Client Truststore
For importing the server public key into the client truststore, we will be using the below command.
x
keytool -import -alias mule-client-public -keystore C:/Certificates/client-truststore.jks -file C:/Certificates/server_public.crt
This above command will generate the client's truststore and import the server public certificate.
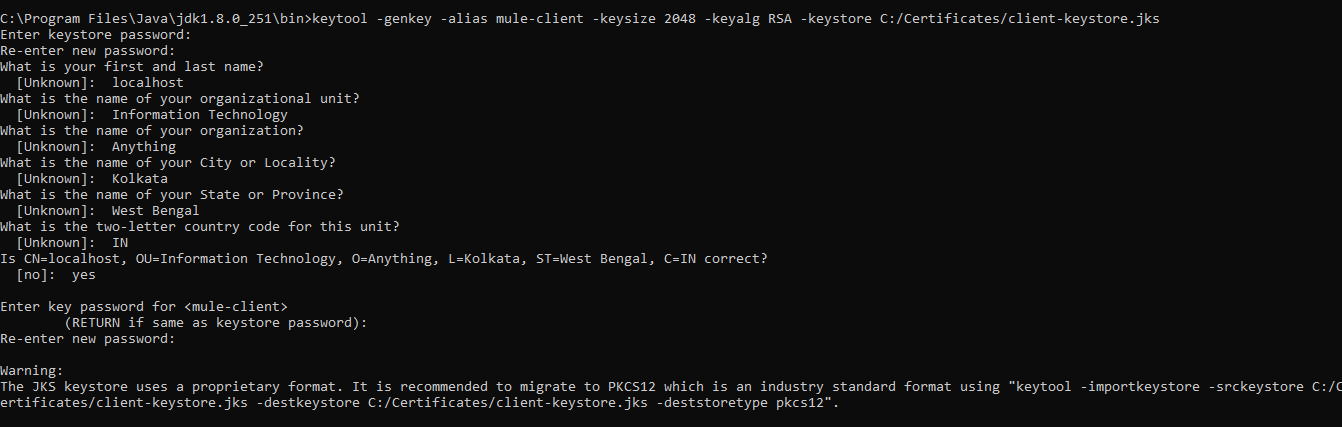
Step 4: Generate Client Keystore
For generating the client Keystore, we will be using the below command.
xxxxxxxxxx
keytool -genkey -alias mule-client -keysize 2048 -keyalg RSA -keystore C:/Certificates/client-keystore.jks
Once we execute the above command, it will ask for the Keystore password, first and last name including other details and the key password.
Alias in the above command is used to search the certificate in the Keystore as there can be multiple certificates in the same Keystore and alias is useful in identifying the right certificate.
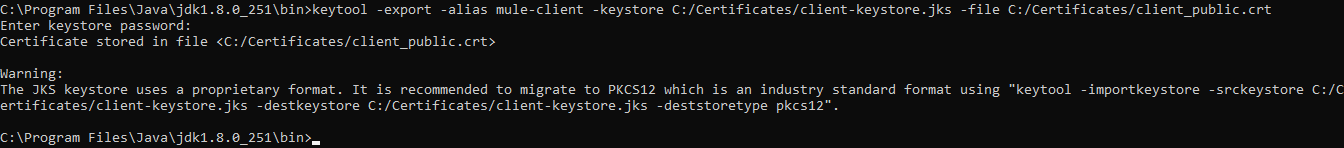
Step 5: Export the Public Certificate From Client Keystore
We will be requiring the client public certificate to be installed in the server truststore. So we need to extract the public key from the client Keystore. For extracting the client public certificate, we will be using the below export command.
xxxxxxxxxx
keytool -export -alias mule-client -keystore C:/Certificates/client-keystore.jks -file C:/Certificates/client_public.crt
This command will export the client public certificate and we will import that client public certificate in the server truststore.
Step 6: Import Client Public Certificate Into Server truststore
For importing the client public certificate into the server truststore, we will be using the below command.
x
keytool -import -alias mule-server-public -keystore C:/Certificates/server-truststore.jks -file C:/Certificates/client_public.crt
This above command will generate the server truststore and import the client public certificate.
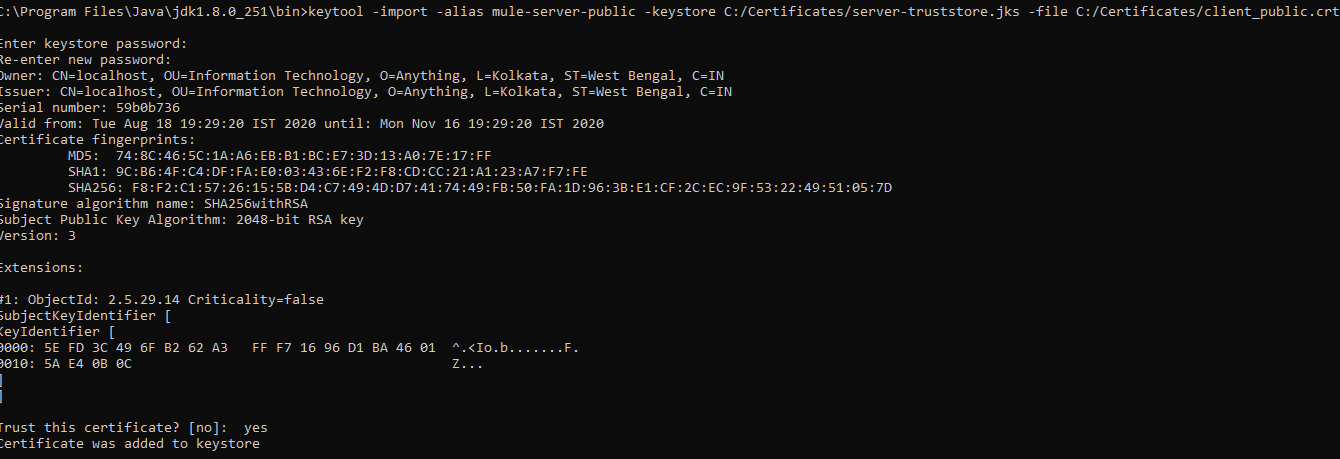
Now, we have generated the server Keystore, server truststore, client Keystore and client truststore.
Step 7: Configuring MuleSoft HTTP Listener and Requester
Let's see how we can configure Keystore and truststore on the MuleSoft application.
Now, we will configure server-Keystore and client-truststore on the MuleSoft HTTP Listener. Under General Settings, the Protocol must be "HTTPS". We need to make sure of the server-Keystore.jks, server-truststore.jks, client-Keystore.jks, and client-truststore.jks that are generated in the above steps, must be copied under folder src/main/resources.
Now, we will perform TLS Key Store. Provide Type, Keystore Path, Keystore, and key password and alias name. Perform the Trust Store Configuration. Provide Path, Password, and Type.

This is the configuration that needs to be done on the server-side.
Now, we will see the client-side configuration. For that, we will be using the MuleSoft HTTP requester. Provide the connection settings on the HTTP requester.

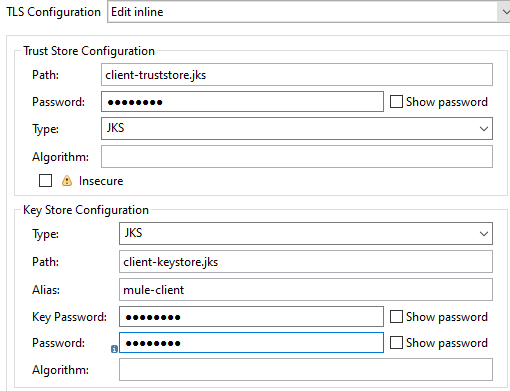
Now, we will do the TLS configuration. Provide the client Trust Store Path, Password, and Type. Provide the Key Store Path, Password, Type, and Path.
For more details on the implementing two-way SSL for the MuleSoft application, please go through below video tutorial.
Now, you know how to implement one way and two way SSL for MuleSoft applications.
Opinions expressed by DZone contributors are their own.

Comments