Implementing MuleSoft AnyPoint Platform Identity Management Using AWS Cognito Authorization Code
Join the DZone community and get the full member experience.
Join For FreeIn the last article, we have seen how we can do client management for MuleSoft API using AWS Cognito Client Credentials. Here, we will see how we can use AWS Cognito for MuleSoft AnyPoint Platform Identity Management.
The authorization code grant is the preferred method for authorizing end users. Instead of directly providing user pool tokens to an end-user upon authentication, an authorization code is provided. This code is then sent to a custom application that can exchange it for the desired tokens. Because the tokens are never exposed directly to an end-user, they are less likely to become compromised.
Creating AWS Cognito User Pool
Now, we will create an AWS Cognito User Pool. Log in to the AWS Console. Navigate to Cognito -> Manage User Pools -> Create a user pool.
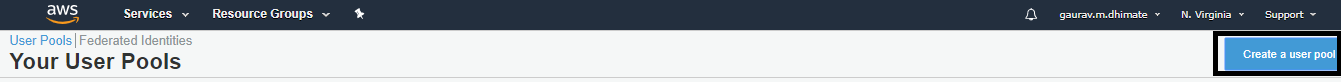
Provide a Pool Name and click on Step through settings.
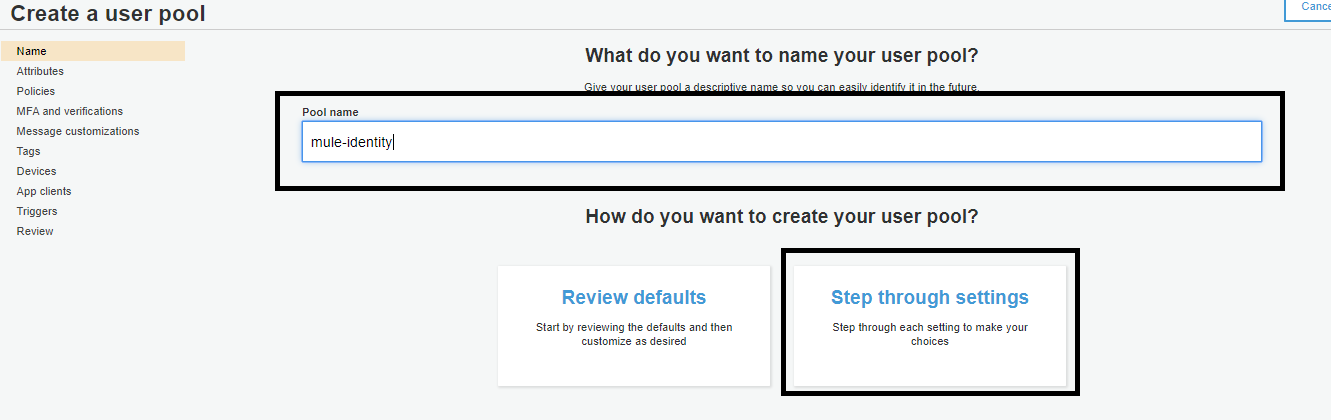
Select the attributes. Then, click Next step.
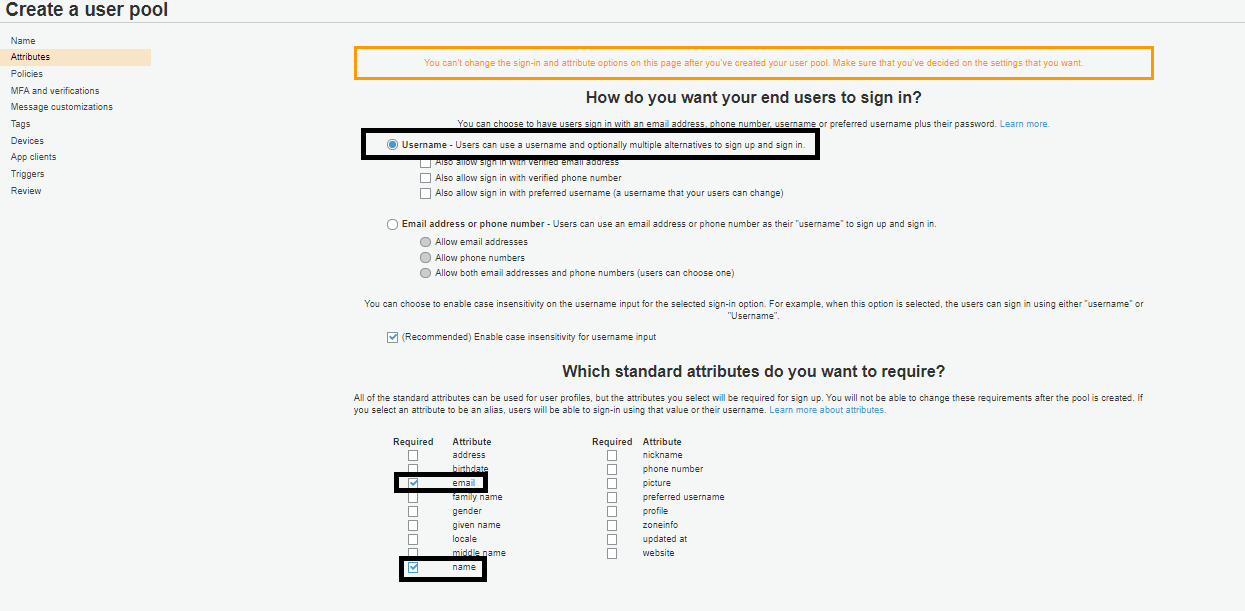
Select the Password Policies, like password strength, expiry period, etc. Then, click Next step.
Select Multi-Factor Authentication, and we will use no MFA verification. Then, click Next step.
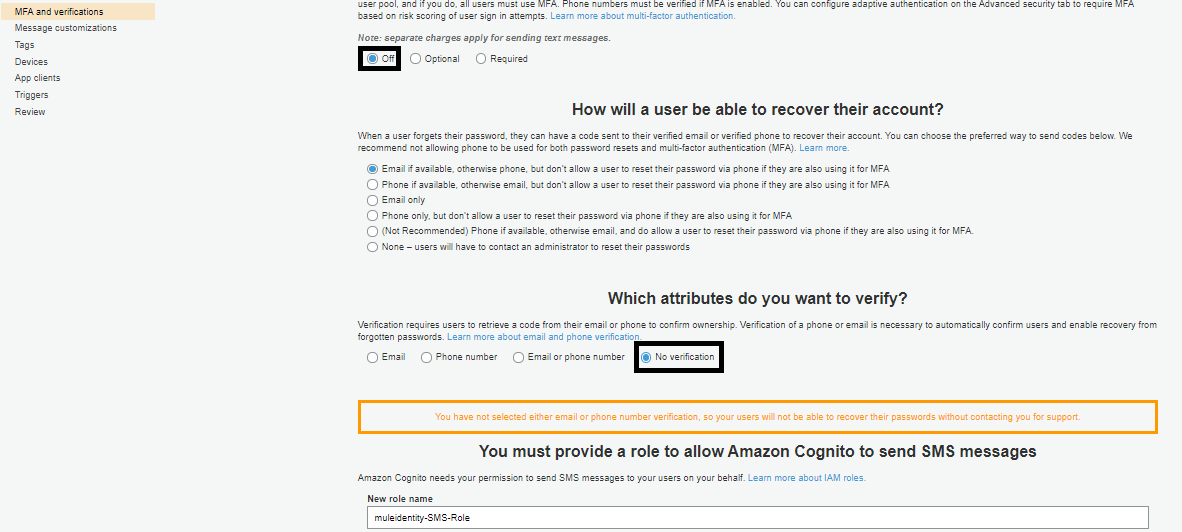
Go to App clients -> Add an app clients. Provide an app client name. Click Create app client.
Now, you can save the user pool.
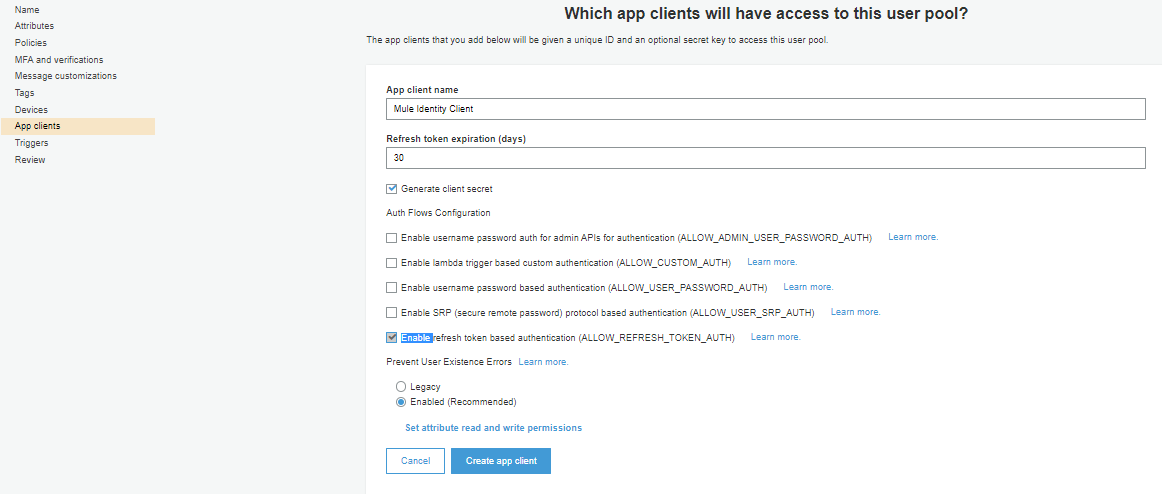
Log in to MuleSoft AnyPoint Platform and fetch the redirect url. Navigate to Access Management -> External Identity -> Identity Management -> OpenID Connect. Use Manual Registration to get a redirect URL.
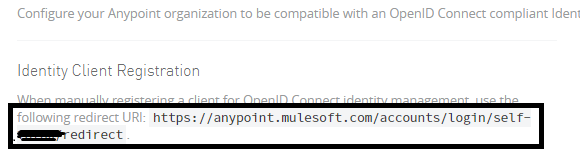
Now, update the redirect URL in the app's client settings in the AWS Cognito User Pool. Click Save changes.
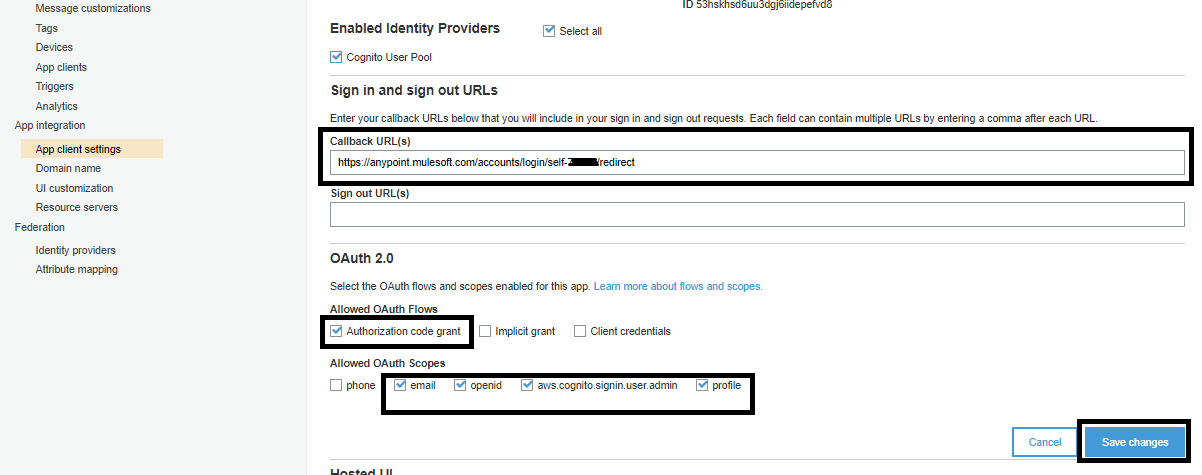
Now, you need to update the Domain name, and you can provide any meaningful domain name. Click Save changes.
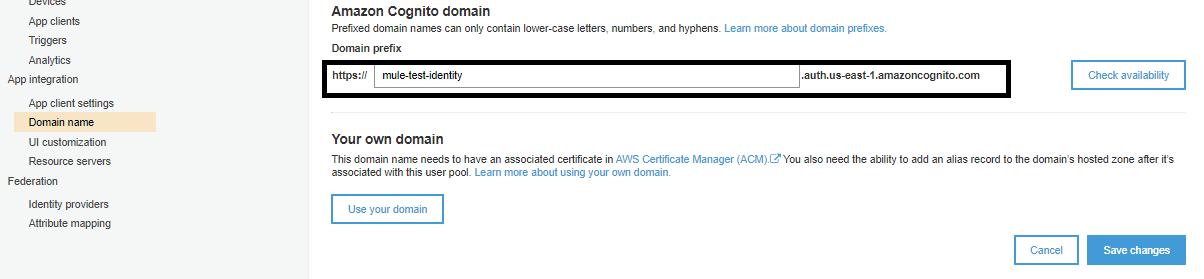
OIDC Url Format: https://region.amazozaws.com/user-pool-id/.well-known/openid-configuration.
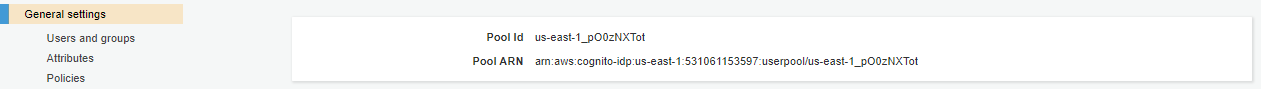
You can get the region and user-pool-id from the General settings of the AWS user pool.
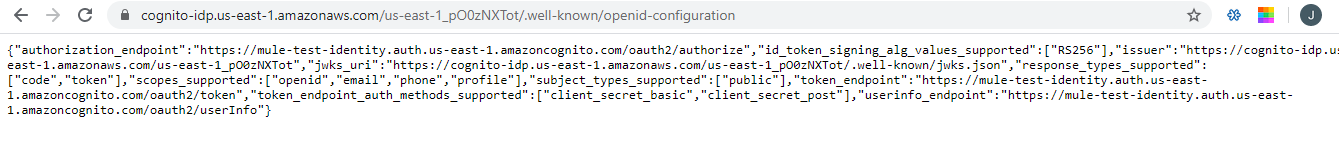
In this case, the OIDC URL will be https://cognito-idp.us-east-1.amazonaws.com/us-east-1_pO0zNXTot/.well-known/openid-configuration
This URL will give the metadata, like Authorization Server, Issuer URLs, etc., and this will be required to configure in the AnyPoint Platform for Identity Management.
Configuring Anypoint Platform Identity Management
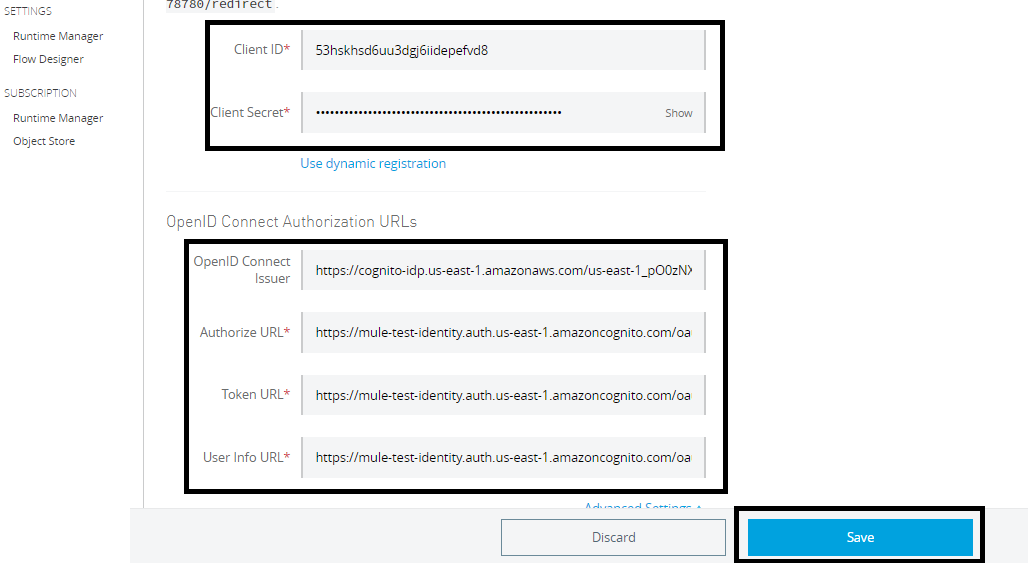
For configuring Anypoint Platform Identity Management, navigate to Access Management -> External Identity -> Identity Management -> OpenID Connect. Use Manual Registration.
You can get Client Id and Client Secret from AWS Cognito User Pool App Client.
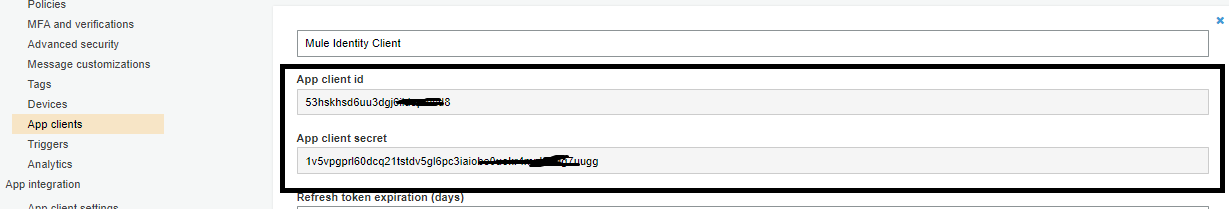
You can get Issuer, Authorization, Token, and UserInfo URL using the above URL, which provides the metadata. Configure those in AnyPoint Platform Identity Management. Click Save.
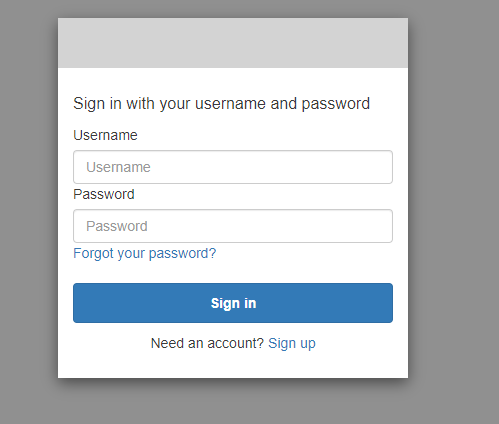
Now, login with the SSO URL (https://anypoint.mulesoft.com/accounts/login/{OrganizationDomain}).
It will redirect you to the AWS Cognito login page, and you can provide username and password if you have an account otherwise you can Sign Up.
Sign up for AWS Cognito Account for Identity Management.
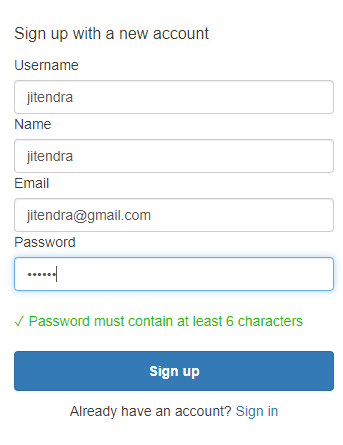
Once you have signed up, a verification code will be sent over email. It will show a screen where you need to put add that verification code. Once it's done, then you can again try to log in using the AnyPoint Platform URL and use the username and password that were created.
Once you provide the correct username and password, it will redirect you to the AnyPoint Platform.
You can find your user in AWS Cognito User Pool in Users and groups.
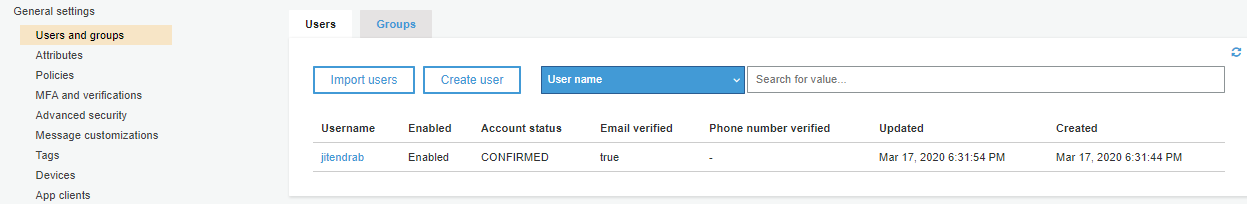
This is how you can enable Identity Management for AnyPoint Platform Using AWS Cognito User Pool Authorization Code.
References
https://dzone.com/articles/authorizing-the-mulesoft-api-using-aws-cognito-use.
https://dzone.com/articles/guide-to-setting-up-mulesoft-dynamic-client-regist.
https://dzone.com/articles/setup-mulesoft-anypoint-platform-identity-using-ok.
https://dzone.com/articles/integrating-okta-oauth-20-oidc-with-mulesoft-anypo.
Opinions expressed by DZone contributors are their own.

Comments