How to Build Slack App for Audit Requests
This article provides a step-by-step process to set up self-serve audit applications in Slack and automate and shorten the approval process.
Join the DZone community and get the full member experience.
Join For FreeAuditing for any B2B software is crucial for understanding how teams utilize products, measuring efficiency created due to the product usage, security, and data compliance. Organizations may require different types of audits to ensure proper usage, identify potential risks, and support technical engagements.
This article will walk you through how to use a technical architecture designed for audits to create a Slack audit application that can facilitate various audit types in a flexible, efficient manner.
Overview of the Audit Slack Application
The core function of a Slack audit application is to monitor and assess the usage of Slack channels, teams, applications, and integrations. This application can be used to identify specific teams or workspaces, perform detailed audits, and generate reports that help with tasks such as migration or security reviews. The application enables users to interact directly within Slack through a bot interface, making the process seamless and real-time.
Types of Audits
While sales-focused audits are often part of customer success workflows, the system described can be generalized for any audit purpose. The audit framework can handle tasks such as:
- Product usage audits. Identifying product usage activity.
- Compliance audits. Understanding team structures, applications used, and how data flows between different users.
- Security audits. Monitoring the installation and usage of applications within Slack, assessing their access permissions, and ensuring they are used in compliance with security policies.
These audit types are vital for supporting various internal and external processes such as compliance checks, security reviews, or business operations audits.
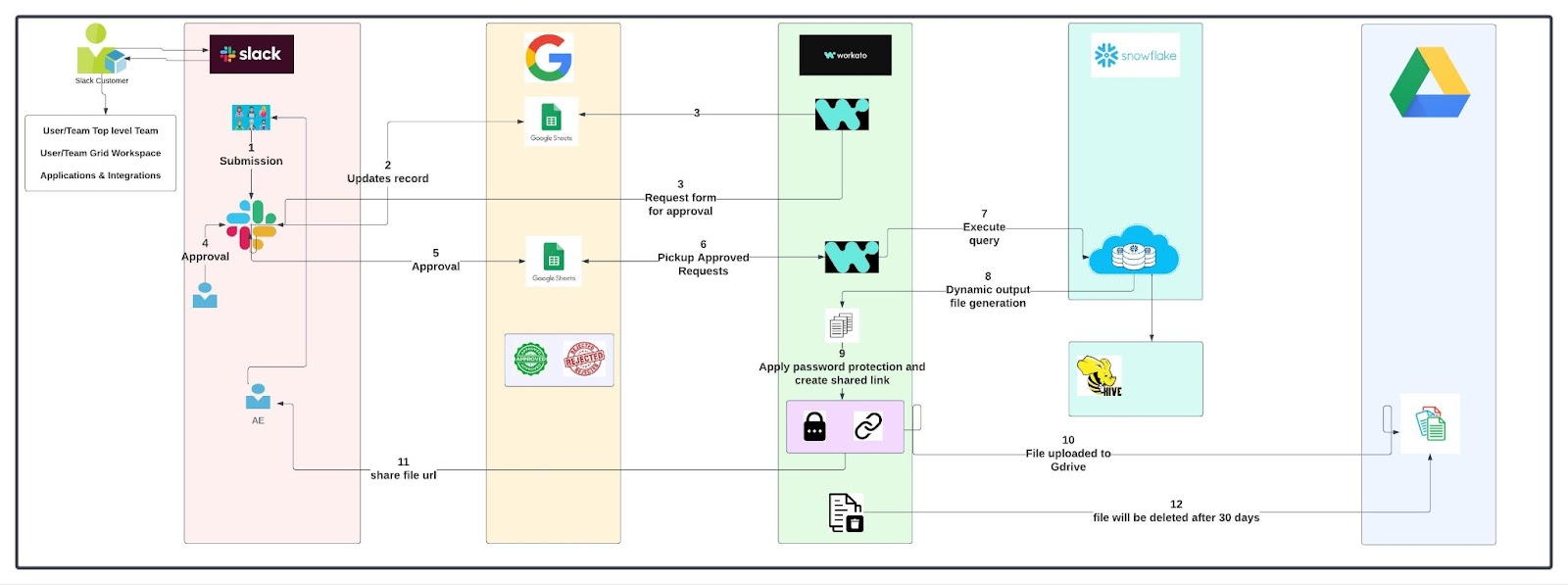
Architecture of the Slack Audit Application
The architecture that supports the audit functionality integrates several components to provide seamless access to audit data. Below are the key architectural components:
Data Access Layer
The audit system interacts with Slack data through secure APIs. It pulls information regarding channels, users, teams, and application usage. In the case of private or tiered data, specific permissions are needed to access restricted information. This data is typically housed in platforms like Salesforce’s Box instance, which provides robust security and large storage capacity for sensitive data.
Audit Workflow
Users initiate audits via a bot within Slack, reducing the need for external tools. The bot receives input on the audit scope, such as the specific workspace, team ID, or channel to be audited. For more granular control, users can filter the results based on parameters such as whether to include shared external members, channels, or specific user teams.
The bot prompts users to input relevant filters like:
- Team ID – Helps narrow down the scope to specific teams by their raw IDs.
- Specific channels – Allow users to focus audits on particular Slack channels.
- Shared members – Option to include external members who belong to Slack Connect channels.
After the required data is provided, users can submit their requests, which are processed by the system for analysis.
Data Processing
The audit requests are processed through a series of workflows that ensure the requested data is accurately retrieved and formatted for reporting. In this context, the architecture must handle large data volumes efficiently, as audits may generate millions of rows of data. To overcome the system’s default row limit (e.g., 400,000 rows), the architecture may need to be enhanced to export larger datasets.
In addition, processing sensitive data requires attention to privacy and security. The use of service layers like Uberproxy can help ensure that data is transmitted securely and access is controlled based on the user’s role.
Reporting and Access
Once the audit is complete, the results are made available to users in the form of reports, which can be accessed via the Slack interface or exported to other tools for further analysis. These reports typically include metadata about channels, team memberships, application usage, and other key insights. Access to the reports can be restricted to authorized users based on roles and permissions.
Challenges in Auditing Applications
- Data privacy and security. Slack audit applications often handle sensitive information, especially when working with external members or private workspaces. To address this, data access should be tightly controlled, ensuring only authorized users can initiate audits or view sensitive data. Solutions like Uberproxy are utilized to enforce security policies and track user activities.
- Data volume management. Slack’s native limits on the volume of data processed (e.g., 400,000 rows) pose challenges when dealing with large workspaces or high-volume audits. The system may need to be optimized to handle large datasets, either by segmenting the data or using external data stores to temporarily hold and process the results.
- Audit accuracy. To ensure the accuracy of audits, it is crucial that users input correct values and filters. The system should be designed to validate input before processing, minimizing errors that could delay the workflow or result in incomplete data.
Workflow Example
- Initiate audit. The user interacts with the Slack bot by typing a command like
/auditand providing necessary parameters, such as Team ID and the type of audit (channel, team, application). - Input filters. The user is prompted to specify additional filters, such as whether to include external members or narrow down the scope to certain channels.
- Data collection. The system queries the relevant data from Slack and any connected services (e.g., Salesforce Box). The application processes the data to gather details like channel activities, membership data, and integrations.
- Report generation. After processing, the audit results are compiled into a report and made available through Slack. The report provides actionable insights based on the audit type.
- Approval and review. Depending on the organization’s needs, the audit report may go through an approval process. The results are reviewed by the relevant stakeholders, and the necessary actions are taken based on the findings.
async def healthcheck(_req: web.Request):
if socket_mode_client is not None and await socket_mode_client.is_connected():
return web.Response(status=200, text="OK")
return web.Response(status=503, text="The Socket Mode client is inactive")
if __name__ == "__main__":
async def start_socket_mode(_web_app: web.Application):
handler = AsyncSocketModeHandler(app, secrets.SLACK_APP_TOKEN, ping_interval=60)
await handler.connect_async()
global socket_mode_client
socket_mode_client = handler.client
await start_scheduled_task(app.client)
async def shutdown_socket_mode(_web_app: web.Application):
await socket_mode_client.close()
secrets = Secrets()
# Initialization
app = AsyncApp(
token=secrets.SLACK_BOT_TOKEN,
signing_secret=secrets.SLACK_SIGNING_SECRET
)
register_listeners(app)
web_app = app.web_app()
web_app.add_routes([web.get("/health", healthcheck)])
web_app.on_startup.append(start_socket_mode)
web_app.on_shutdown.append(shutdown_socket_mode)
web.run_app(app=web_app, port=80)Conclusion
The architecture for building a Slack audit application described above offers a comprehensive, flexible solution for managing various types of audits within Slack. Using Slack’s API, external services, and secure data processing workflows, the system can efficiently track and analyze data across channels, teams, and applications.
Opinions expressed by DZone contributors are their own.

Comments