Honeytokens for Peace of Mind: Using Cyber Deception To Buy Time to Remediate at Scale
Honeytokens bring peace of mind that you are safe from leaks and attacks while tackling secrets sprawl, no matter how many repos or developers you have.
Join the DZone community and get the full member experience.
Join For FreeNo matter what part of the organization you work in, there is one thing everyone wants: a good night's sleep. Everybody, from operations to security to development, wants peace of mind that all the doors are locked, all the networks are protected, and the organization and customers are safe. We also rest easier when we know that if anything does go wrong, there is a process in place that will alert you only in the correct circumstances and make remediation straightforward.
If you have been tackling the realities of secrets sprawl, getting a handle on all the hardcoded credentials in your organization, then we understand the stress and the restless nights that can bring. Even a small team can add hundreds of secrets a year, so when it is time to prioritize and start working to resolve the known incidents, it can seem overwhelming.
What we need is a way to get some peace of mind that we are still protected while working to remediate the problem at scale. This is where cyber deception, in the form of honeytokens, can be a game changer.
Honeytokens Can Protect You While You Remediate
In an ideal world, you could remediate all your incidents in just a few minutes with little manual effort. In the real world, though, this process can take weeks, months, or, in the worst cases, years of dedicated work. What can you do to ensure that you stay safe in the meantime in the event of a code leak or breach? No matter how you structure or prioritize your response plan, the best first step you can take, "step zero" of remediation if you will, to protect yourself as much as you can as quickly as you can is to deploy honeytokens to every repo with a secret leak occurrence.
Deploy Honeytokens First, Ask Questions Later
Deploying honeytokens to any repos or environments where you have identified an issue can give you some breathing room. Knowing you have intrusion detection and an alerting system in place, you can progress with your remediation plan, adjusting if something does go wrong. If someone has breached your perimeter and has accessed your code, your alert will tell you to escalate, rotating the secrets they likely found. Similarly, if what you think is a private code repo suddenly has public scanners hitting it, meaning it has now become a public repo, you will want to move that to the top of the response queue.
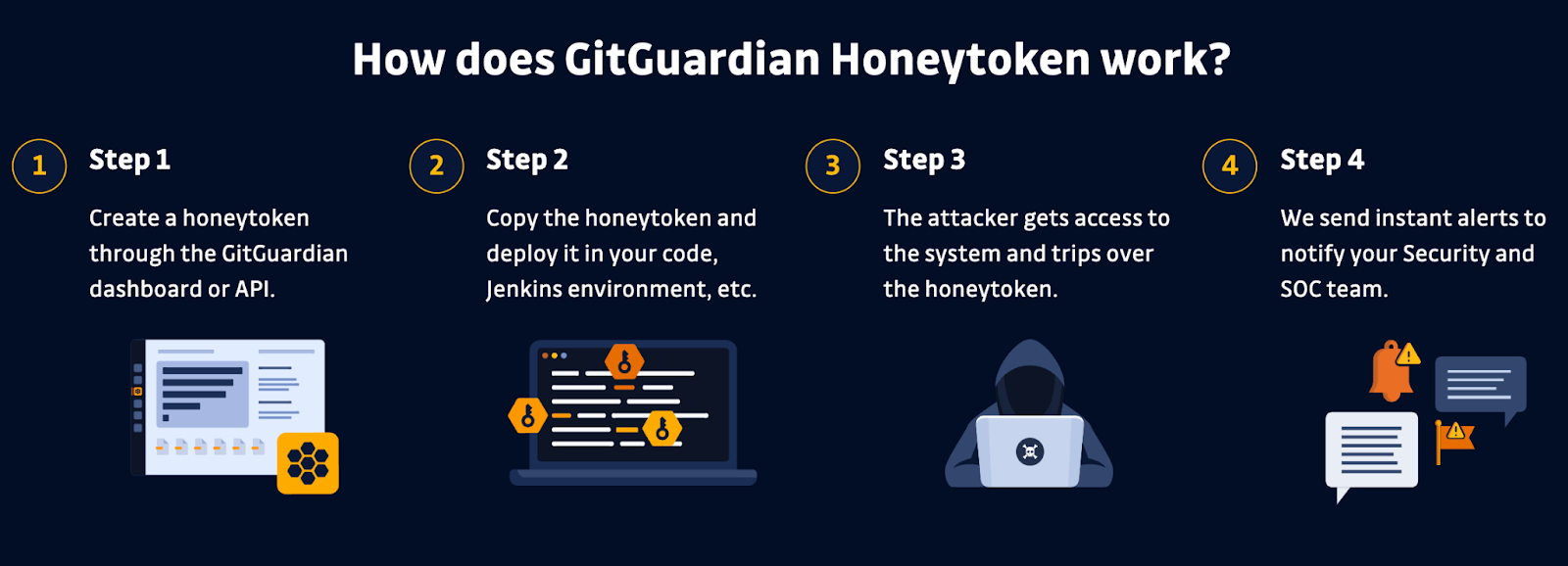
What Is a Honeytoken?
Honeytokens, such as GitGuardian honeytokens, are decoy credentials that don't provide any access to data or systems but instead trigger alerts to let you know someone has attempted to use it. A good honeytoken will provide a timestamp, the IP address, the user agent, and the action the user was attempting. Alerts can be delivered via email or through custom webhooks, meaning it is possible to automate responses.
When a honeytoken is first triggered, you should be alerted immediately by email. The email will contain all the information gathered from the attempted use. You can also commonly set up custom webhooks to send alerts to any system you choose that can parse JSON. This lets you integrate and manage the information directly within your SIEM or other security systems and automate or speed up your response.
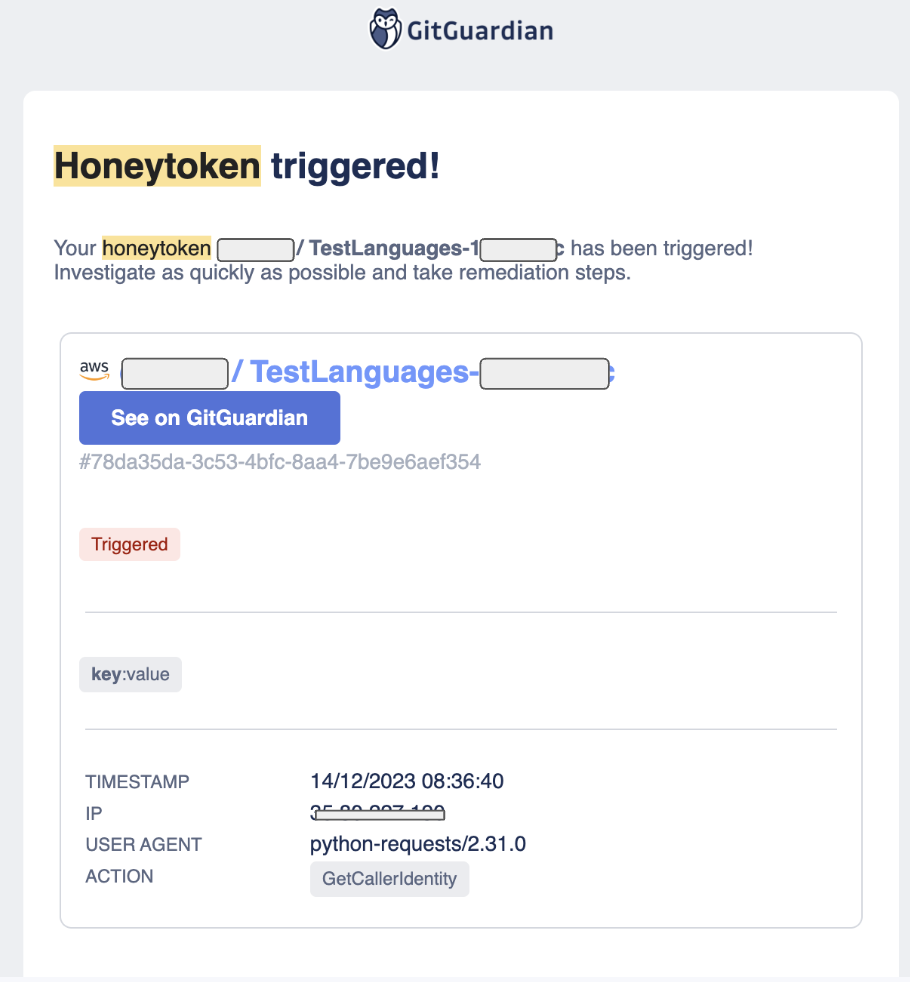
An example alert from the GitGuardian Honeytoken system
In most attacks, the adversarial actors do not manually look through each file, line by line, to find secrets. They very much use your secrets to move laterally throughout your system, but most of the time, they use scanning tools as they gain a lay of the land. Very commonly, these scans will immediately attempt to use any credentials to test if they are active, which will trigger the honeytoken. Once you know they are there, you can react before they can do much damage or exfiltrate anything.
Once you have their IP address and user agent, you can kick them out of your network and systems and quickly look for any unauthorized actions they have taken. If there were any valid secrets in the codebases where a honeytoken was triggered, then you will be able to escalate appropriately and invalidate those credentials as soon as possible.
For When Your Code Gets Leaked
Unfortunately, as we have seen in so many cases, private code repositories can unexpectedly become public repos. When that happens, any and all secrets in that codebase can be seen by anyone outside your organization to be used for any number of potentially nefarious purposes. You want to know right away that a leak has occurred, not waiting five years, as was the case with Toyota. A large number of public scans are continually being performed to try to find new commits and any secrets they contain.
Fortunately, we can use these public scanners to our advantage and leverage honeytokens to detect when private code becomes public. Get alerted immediately when eyes outside your org can see your secrets. If you have legitimate, valid secrets in that repo, then you know it is time to rotate those secrets as quickly as you can.
Prioritizing Your Action Plan
Now that you have a way to know if a repo is under attack or being shared in public, you can prioritize your action plan to tackle secrets sprawl. You need to gather all the needed data in one place, perform validity checks, and assign severity scores.
Since there is no legitimate use for honeytokens other than as traps, you can safely leave them in any cleaned repo, giving you the same protection for repos with all the real secrets removed. Setting it once produces the long-term benefit without any additional work. Hopefully, though, your honeytokens will never be triggered.
Cleaning Up Technical Debt Takes Time
We know that security is challenging and causes a lot of headaches as you are endlessly playing defense. We are here to help you tackle secrets sprawl at scale, no matter how many devs you have or how much legacy code you have to deal with. Honeytokens can make sure that if someone is snooping around, they will trigger an alert. They can also let you know if your private code becomes public.
Honeytokens provide protection long after you resolve all your secrets-related incidents, helping you continuously improve your response times.
Published at DZone with permission of Dwayne McDaniel. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments