Good Application Security Posture Requires Good Data
Application Security Posture Management, ASPM, is only as good as the data sources. Learn about the pitfalls and what to look for in tools and scanners.
Join the DZone community and get the full member experience.
Join For FreeThe term 'security posture" is used to describe the state of an organization's overall security and response readiness. Multiple solutions are emerging that aggregate findings to provide a holistic view of enterprise security risks.
Security posture can also be seen as a way to prioritize security efforts, helping you answer the question, "What should we work on next?" based on balancing risks by analyzing in-context data and weighing the remediation efforts required.
But where does the needed in-context data come from? Does it require new scanners? Is a "rip-and-replace" strategy in order? We don't believe so; ASPMs are a new type of risk management tooling, best built on top of what already works for your enterprise.
ASPM
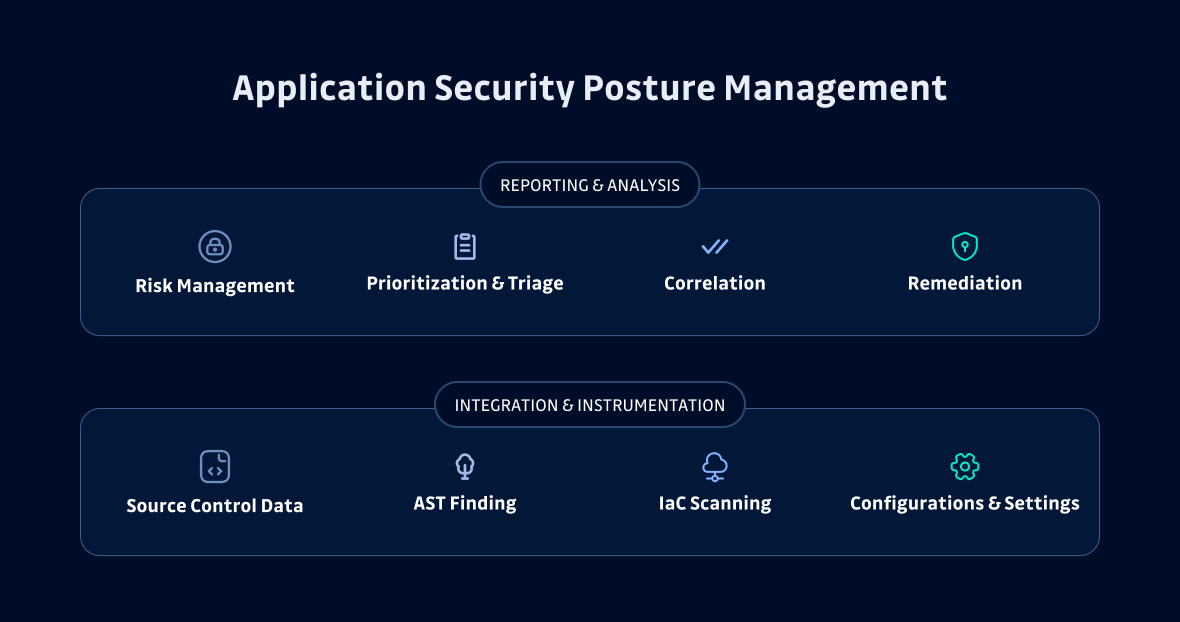
In May 2023, Gartner defined Application Security Posture Management as the newest segment of the Security Posture Management market, defining it as a system that "continuously manages application risk through collection, analysis, and prioritization of security issues across the software life cycle."
ASPM solutions aggregate application issues to help with your risk impact analysis. These issues include hardcoded secrets, unauthenticated APIs, unencrypted data flows, PII data issues, and multiple types of application vulnerabilities. This is a rapidly expanding market, with players including ArmorCode, Bionic (a CrowdStrike company), Cider Security (a Palo Alto Networks company), and Kondukto.
Your Security Posture Is Only as Good as Your Data
While ASPM solutions are not miracle cure-alls, they can provide a new way to quickly gain valuable insight. But like any technology, there are some pitfalls to watch out for.

False Positives
If a security tool has a high noise-to-signal ratio, with a large volume of false alarms, it will affect your ability to clearly understand what is happening. If those tools generate untagged or unscored incident reports, it becomes really hard to differentiate between critical and low-risk issues. While all tools will continue to improve their accuracy over time, not all have been battle-hardened to the same degree.
False Negatives
The absence of an alarm does not necessarily mean everything is good; it might mean the system is not checking for the right things. Misconfigured tools can report a test as passing when it does not actually perform a check. Thinking there are no problems can mean not noticing a growing issue until it becomes disruptive and costly.
Solution Complexity
Due to the nature of ASPM solutions, taking in data from multiple sources and scanners, there is an inherent complexity that comes with the approach. If you only manage a very small number of applications, then the costs of ASPM might outweigh the benefits. ASPMs are not a one-size-fits-all solution.
Remediation Is Key
ASPM should also surface a remediation path for identified issues. The amount of effort it will take to fix an issue is a serious consideration when weighing various tasks in a triage list. If a fix takes moments to implement and it will reduce risk significantly, that is an easy "fix now." If it will take weeks to fix but has lower risk, you might backlog that task for a future sprint.
In Addition, Not a Replacement
Recently, one security tools analyst said, "I don’t know a single security professional who wouldn’t be happy to drop all their old tools for a single better one if they didn’t sacrifice useful features in the process." (emphasis mine).
The reality is that even if an 'all-in-one' security tool could match usefulness and outperform tools addressing specific security concerns, a rip-and-replace solution is likely a non-starter for most enterprises. The cost and political will needed to replace existing and working technology with a 'promising' new tool is going to be high.
Get Ready for the Risks Ahead
The evolution of the security posture management market marks an evolution of the security industry. No longer can enterprises rely on unconnected sets of test results and massive security reports. We must get out of our information silos. Managing risks in the modern enterprise requires a more active and holistic approach. Underneath any ASPM approach is the need for good data and a clear path to remediation.
Published at DZone with permission of Dwayne McDaniel. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments