Essential Security Measures for PDF Documents
Learn essential security measures for PDFs. Explore common security threats that affect PDF files and delve into various techniques to secure PDFs programmatically.
Join the DZone community and get the full member experience.
Join For FreePortable Document Format (PDF) is a file format that contains a comprehensive representation of a document, encompassing elements like text, fonts, graphics, and other components. PDF is often considered a secure document format due to its inherent security features. These capabilities enable the incorporation of password protection, encryption, and digital signatures into a file.
PDF security is important for several reasons. Information is often shared over the internet, and ensuring the privacy and integrity of sensitive data during such exchanges is paramount. Whether the PDF contains a legal contract, a confidential business report, or personal information, proper PDF security ensures that only authorized individuals can access or modify the contents of these documents. PDF security not only protects intellectual property but can also help you comply with legal and regulatory requirements. This makes it an indispensable tool in today's interconnected world.
In this article, you'll learn about essential security measures for PDFs by exploring the common security threats that can affect PDF files and delving into various techniques to secure them programmatically.
Common Security Threats That Can Affect PDF Files
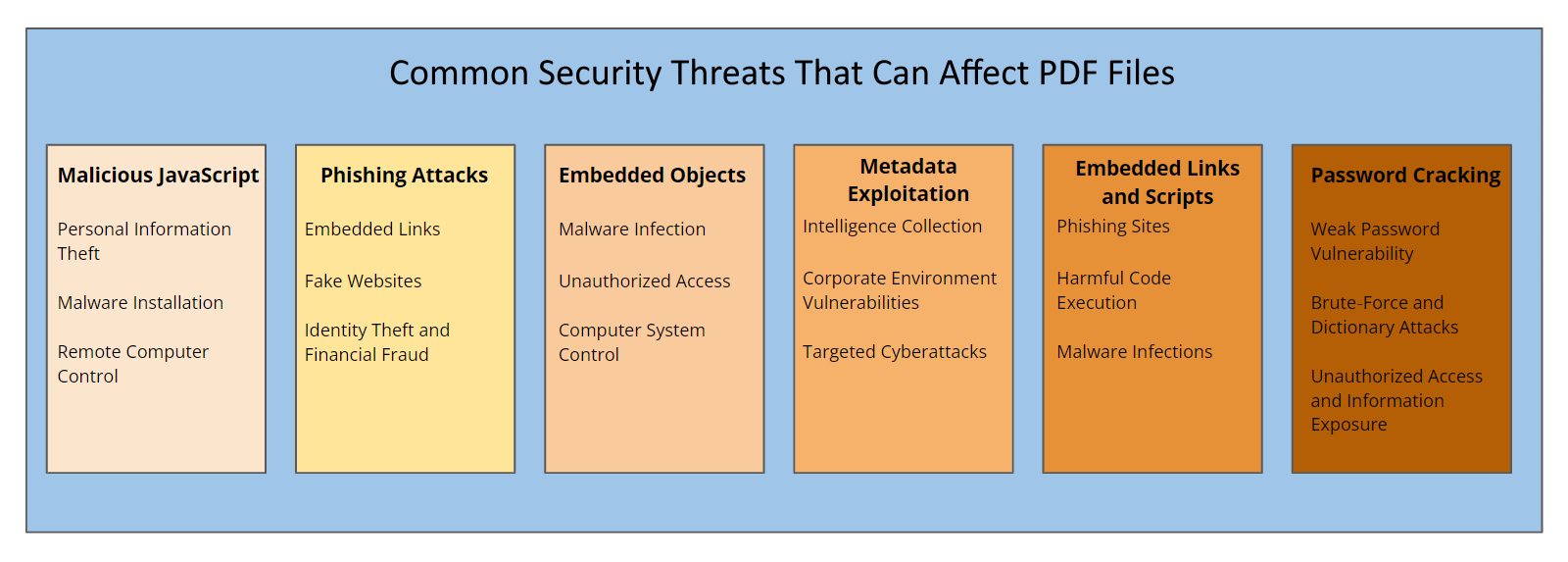
The following sections discuss some of the most common security threats that can affect PDF files, exploring the risks and mechanisms through which attackers can exploit vulnerabilities. Understanding these threats is the first step toward implementing robust security measures to protect PDF content.
Malicious JavaScript
Malicious JavaScript embedded in PDF files is a major security concern that can often go unnoticed. On the one hand, JavaScript within PDFs can be used for legitimate purposes like creating interactive forms or enhancing document functionality. On the other hand, JavaScript in PDFs can be exploited by cybercriminals.
The threat emerges when hackers insert malicious JavaScript code into a PDF. When a user opens the infected PDF file, the malicious JavaScript code can execute automatically. This can lead to various harmful activities, including:
- Stealing personal information: The malicious code can be used to extract personal or sensitive information from the computer of the user where the PDF file is opened. This sensitive information can include login credentials, credit card numbers, or personal identification details.
- Installing malware: Malicious JavaScript can trigger the download and installation of malware, spyware, or ransomware on the system of the user, which can lead to further exploitation.
- Taking control of a computer: In some instances, the code may even grant remote access to the user's system, allowing hackers to take full control of the computer. This could include access to files, the ability to monitor activities, or even using the computer for other cybercriminal activities.
Phishing Attacks
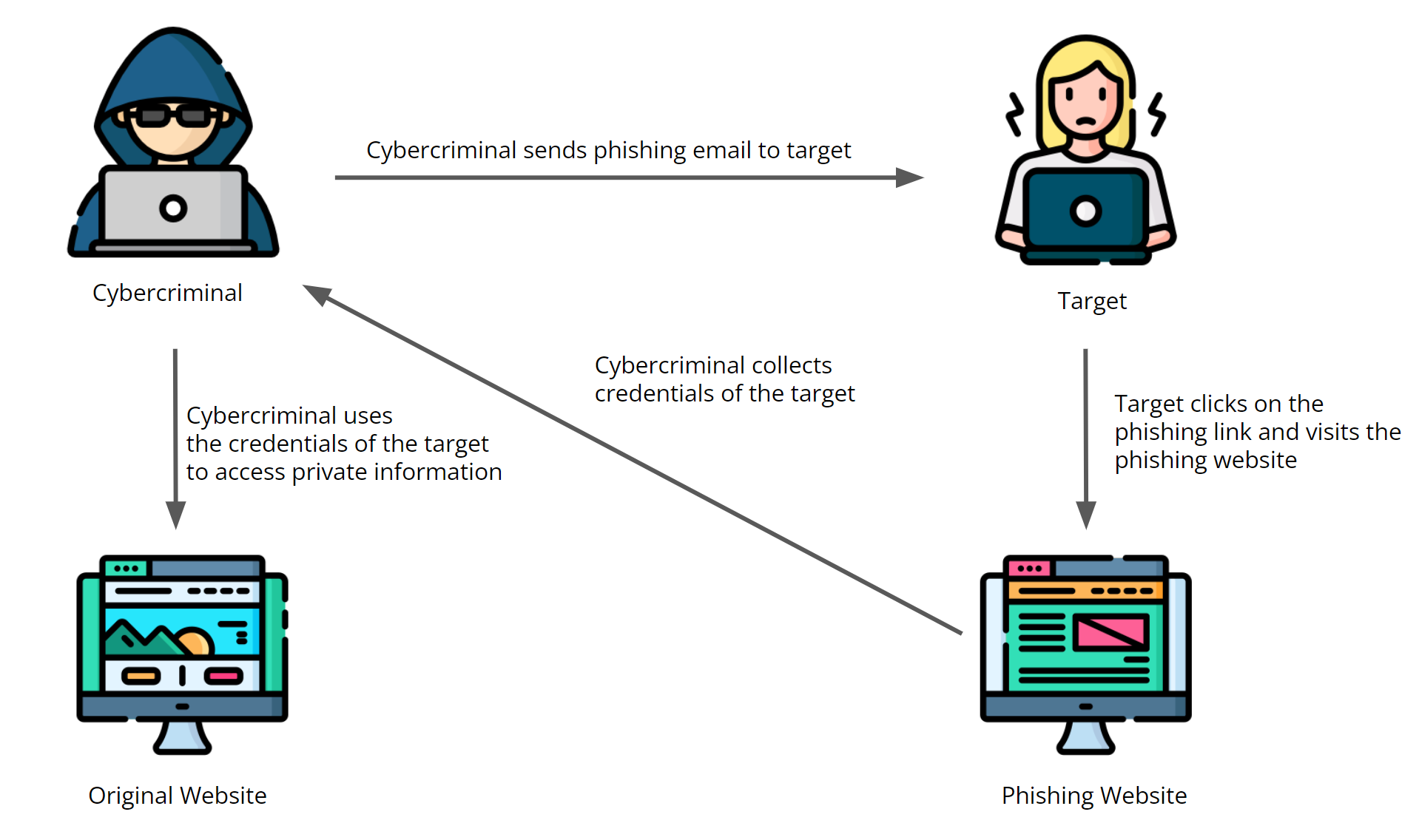
PDFs can also be used for phishing attacks. Hackers can create PDFs that closely resemble legitimate invoices or banking statements. This way, cybercriminals can leverage the trust commonly associated with PDFs to lure unsuspecting users into opening these seemingly benign files. There might be embedded links within the PDF that redirect the user to fraudulent websites that are purposely designed to mimic authentic sites. These fake sites then prompt the user to enter sensitive information like login credentials or financial details. This information can be collected by cybercriminals for malicious purposes like identity theft or financial fraud.
Embedded Objects
Embedded objects in PDF files can include images or videos. On the one hand, these objects provide versatility in content presentation, but on the other hand, they introduce a potential avenue for security breaches. Cybercriminals can stealthily infect these objects with malware. When a user opens a PDF file that contains such compromised objects, the embedded malware may be silently executed, leading to various cybersecurity issues. These issues range from unauthorized access to personal data to full control over the victim's computer system. The seemingly innocuous act of opening a PDF file can thus turn into a serious security issue. The complexity of detecting and defending against malware hidden within these embedded objects makes this a particularly concerning threat.
Document Metadata Exploitation
Exploitation of metadata in PDF files is an often overlooked but notable security concern. Metadata in a PDF file includes details like author names, creation dates, and revision histories. At first glance, this information may seem harmless. However, cybercriminals can use this information to collect intelligence about an individual or organization.
By analyzing this metadata, they can uncover patterns, relationships, and potential vulnerabilities. For example, understanding the software versions used to create or modify the document might lead them to discover unpatched security flaws that can be exploited. Especially in a corporate environment, metadata that contains information such as the name of the author of the PDF and the document's history can reveal internal structures, roles, and processes that could be used for more targeted exploits or cyberattacks.
Embedded Scripts
While embedded links in PDFs can be a security concern, as discussed in the phishing section, embedded scripts also represent advanced threats that can catch users off guard. Unlike simple links that redirect users to external websites, embedded scripts can execute code directly on the user's machine when the PDF is opened. This can lead to a range of malicious activities, including:
- Unauthorized file access: Scripts can be designed to access files on a user's computer without their knowledge. This can potentially lead to data theft.
- Keylogging: Malicious scripts can initiate keylogging activities to capture sensitive information like passwords and credit card numbers.
- Remote control: In extreme cases, scripts can even enable remote control of the computer. This can provide cybercriminals with unfettered access to the system.
- Exploiting vulnerabilities: Scripts can exploit known or zero-day vulnerabilities in the PDF reader software or the operating system, leading to further compromise of the system.
- Ransomware: Malicious code can encrypt files on the user's computer and demand the user pay a ransom for their release.
Password Cracking
When a PDF file is protected with a password, it adds a layer of security to prevent unauthorized access. However, if the chosen password is weak, can be guessed easily, or follows common patterns, it can be susceptible to cracking by attackers. Different tools and techniques, including brute-force attacks or dictionary attacks, can be used to guess or crack the password. Once the password is cracked, the attacker can gain unauthorized access to the PDF file. This can potentially expose sensitive information, intellectual property, or personal data contained within the document.
How To Secure PDFs Programmatically
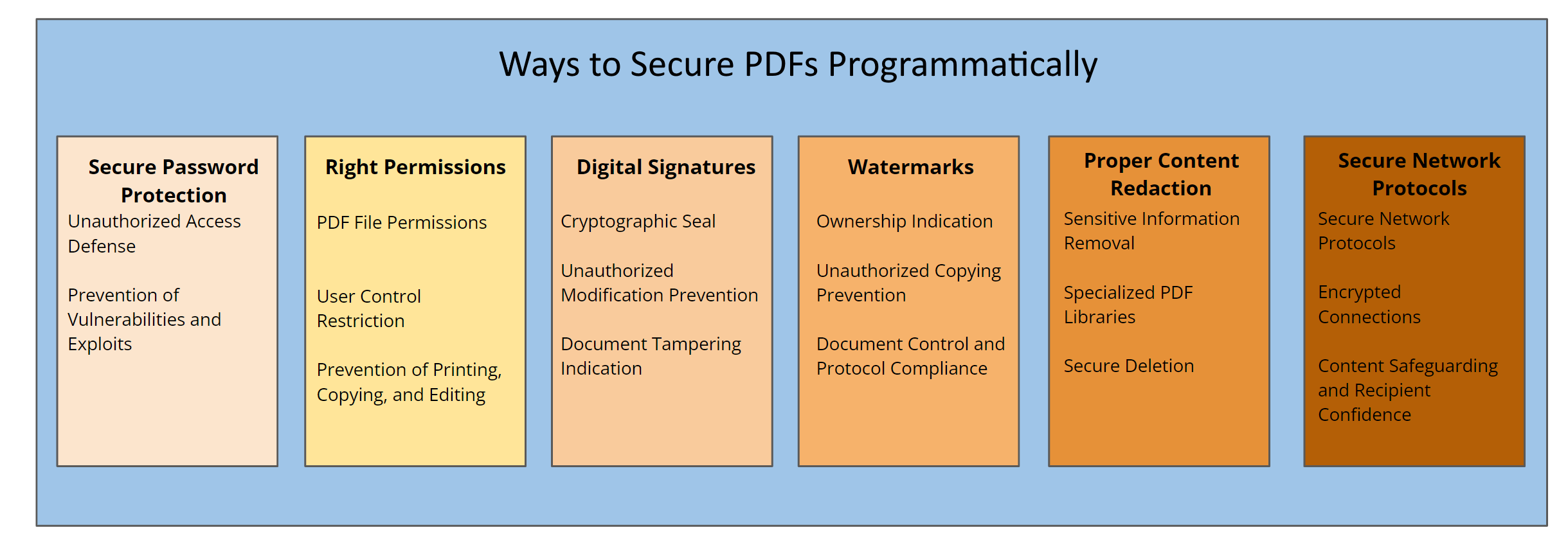
Enable Secure Password Protection
Secure password protection is an important aspect of PDF security. It serves as a frontline defense against unauthorized access. However, the effectiveness of this security measure depends on its correct implementation. For example, Adobe transitioned from AES-128 encryption in version 8 to AES-256 in version 9 of its PDF software. Ironically, Adobe later announced that version 9 was actually less secure against brute-force attacks compared to version 8. The issue wasn't with AES encryption itself, which is a robust encryption standard, but rather with how it was implemented. The lesson here is that even strong encryption algorithms like AES can only be rendered effective if implemented correctly.
Set the Right Permissions
Setting the right permissions is an important step in securing PDF files. Default permissions often grant users extensive control over a PDF file. By carefully configuring these permissions, the PDF author can restrict what other users can do with the document. This can include preventing printing, copying, editing, or extracting content from the PDF. Reducing permissions to only what is necessary for the user significantly limits the potential for malicious exploitation or inadvertent mishandling of the document.
You should review and tailor the permissions of each PDF file rather than relying on broad default settings. Your review should take into account the sensitivity of the content within the document. Additionally, the specific user actions that are required must be considered. Relying on wide-ranging default settings should be avoided, as they may not provide adequate protection for the particular contents and usage of the file.
Use Digital Signatures
Digital signatures are an effective way to secure PDF files. A digital signature provides a cryptographic seal that verifies the identity of the author and confirms that the document has not been altered since it was signed. By employing digital signatures, the user can prevent unauthorized modifications to the document and assure recipients that the content originates from a verified source. This process involves creating a unique digital ID, often linked to a trusted certificate authority, and then applying this signature to the PDF file. Any subsequent changes to the document would invalidate the signature. This would provide a clear indication of tampering with the PDF.
Add Watermarks to Indicate Status and Ownership
Adding watermarks to PDF files is a strategic method to indicate the status and ownership of the PDF and can further enhance the security of the document. Watermarks can be customized text or images that are overlaid on the pages. The watermarks often display information such as the name of the company, a logo, or a statement like "Confidential."
The watermark basically acts as a visual deterrent against unauthorized copying or distribution of the PDF, as it clearly associates the document with a specific owner. Furthermore, it can provide contextual information about the status of the document, such as whether it is a draft or the final version. Including watermarks in a PDF provides greater control over documents and discourages misuse at the same time.
Use PDF Libraries for Content Redaction
Content redaction in PDF files refers to the process of permanently removing or obscuring sensitive information. Simply overlapping content in the PDF file using visual PDF editors is not secure. This approach might visually hide the information but can leave the underlying data intact and accessible to someone with the knowledge to extract it. So, it's recommended that you use specialized PDF libraries that are specifically designed to handle the secure deletion of sensitive content. Such libraries provide programmatic methods to redact content, ensuring that the information is completely removed and cannot be retrieved.
Use Secure Network Protocols for Transmitting PDF Files
Transmitting PDF files over a network requires careful attention to security, especially when the documents contain sensitive or confidential information. You should use secure network protocols to ensure that PDF files are transmitted safely.
Protocols such as Hypertext Transfer Protocol Secure (HTTPS) or Secure File Transfer Protocol (SFTP) provide encrypted connections. This can make it more difficult for attackers to intercept or tamper with the files during transmission. In addition to secure protocols, you can also use virtual private network (VPN) services that provide an extra layer of security. While VPNs themselves are not network protocols, they create a secure tunnel for data transmission over public networks. This can further safeguard the integrity and confidentiality of your PDF files.
Conclusion
This article highlighted some common security threats that can affect PDF files, including malicious JavaScript, phishing attacks, embedded objects, and many more. It also explored a series of strategies for securing PDF files.
By understanding the potential risks to the security of PDF files and implementing the robust security measures described, you can ensure that your PDFs maintain integrity, confidentiality, and authenticity. The seemingly simple task of managing PDF files has become a significant part of general cybersecurity, meaning these security measures are essential for any individual or business handling sensitive information.
Opinions expressed by DZone contributors are their own.

Comments