Effective Log Data Analysis With Amazon CloudWatch: Harnessing Machine Learning
The article explains how CloudWatch effectively handles key challenges in log data analysis, emphasizing volume management and anomaly detection.
Join the DZone community and get the full member experience.
Join For FreeIn today's cloud computing world, all types of logging data are extremely valuable. Logs can include a wide variety of data, including system events, transaction data, user activities, web browser logs, errors, and performance metrics. Managing logs efficiently is extremely important for organizations, but dealing with large volumes of data makes it challenging to detect anomalies and unusual patterns or predict potential issues before they become critical. Efficient log management strategies, such as implementing structured logging, using log aggregation tools, and applying machine learning for log analysis, are crucial for handling this data effectively.
One of the latest advancements in effectively analyzing a large amount of logging data is Machine Learning (ML) powered analytics provided by Amazon CloudWatch. It is a brand new capability of CloudWatch. This innovative service is transforming the way organizations handle their log data. It offers a faster, more insightful, and automated log data analysis. This article specifically explores utilizing the machine learning-powered analytics of CloudWatch to overcome the challenges of effectively identifying hidden issues within the log data.
Before deep diving into some of these features, let's have a quick refresher about Amazon CloudWatch.
What Is Amazon CloudWatch?
It is an AWS-native monitoring and observability service that offers a whole suite of capabilities:
- Monitoring: Tracks performance and operational health.
- Data collection: Gathers logs, metrics, and events, providing a comprehensive view of AWS resources.
- Unified operational view: Provides insights into applications running on AWS and on-premises servers.
Challenges With Logs Data Analysis
Volume of Data
There's too much log data. In this modern era, applications emit a tremendous amount of log events. Log data can grow so rapidly that developers often find it difficult to identify issues within it; it is like finding a needle in a haystack.
Change Identification
Another common problem we have often seen is the fundamental problem of log analysis that goes back as long as logs have been around, identifying what has changed in your logs.
Proactive Detection
Proactive detection is another common challenge. It's great if you can utilize logs to dive in when an application's having an issue, find the root cause of that application issue, and fix it. But how do you know when those issues are occurring? How do you proactively detect them? Of course, you can implement metrics, alarms, etc., for the issues you know about. But there's always the problem of unknowns. So, we're often instrumenting observability and monitoring for past issues.
Now, let's dive deep into the machine learning capabilities from CloudWatch that will help you overcome the challenges we have just discussed.
Machine Learning Capabilities From CloudWatch
Pattern Analysis
Imagine you are troubleshooting a real-time distributed application accessed by millions of customers globally and generating a significant amount of application logs. Analyzing tens of thousands of log events manually is challenging, and it can take forever to find the root cause.
That is where the new AWS CloudWatch machine learning-based capability can quickly help by grouping log events into patterns within the Logs Insight page of CloudWatch. It is much easier to identify through a limited number of patterns and quickly filter the ones that might be interesting or relevant based on the issue you are trying to troubleshoot. It also allows you to expand the specific pattern to look for the relevant events along with related patterns that might be pertinent.
In simple words, Pattern Analysis is the automated grouping and categorization of your log events.
Comparison Analysis
How can we elevate pattern analysis to the next level? Now that we've seen how pattern analysis works let's see how we can extend this feature to perform comparison analysis. "Comparison Analysis" aims to solve the second challenge of identifying the log changes.
Comparison analysis lets you effectively profile your logs using patterns from one time period and then compare them to the patterns extracted for another period and analyze the differences. This will help us answer this fundamental question of what changed to my logs. You can quickly compare your logs while your application's having an issue to a known healthy period. Any changes between two time periods are a strong indicator of the possible root cause of your problem.
CloudWatch Logs Anomaly Detection
Anomaly detection, in simple terms, is the process of identifying unusual patterns or behaviors in the logs that do not conform to expected norms.
To use this feature, we need to first select the LogGroup for the application and enable CloudWatch Logs anomaly detection for it. At that point, CloudWatch will train a machine-learning model on the expected patterns and the volume of each pattern associated with your application. CloudWatch will take five minutes to train the model using logs from your application, and the feature will become active and automatically start servicing these anomalies any time they occur.
So things like a brand new error message occurring that wasn't there before, a sudden spike in the volume, or if there's a spike in HTTP 400s are some examples that will result in an anomaly being generated for that.
Generate Logs Insight Queries Using Generative AI
With this capability, you can give natural language commands to filter log events, and CloudWatch can generate queries using Generative AI. If you are unfamiliar with CloudWatch query language or are from a non-technical background, you can easily use this feature to generate queries and filter logs. It's an iterative process; you need to learn precisely what you want from the first query. So you can update and iterate the query based on the results you see. Let's look at a couple of examples:
Natural Language Prompt: "Check API Response Times"
Auto-generated query by CloudWatch:
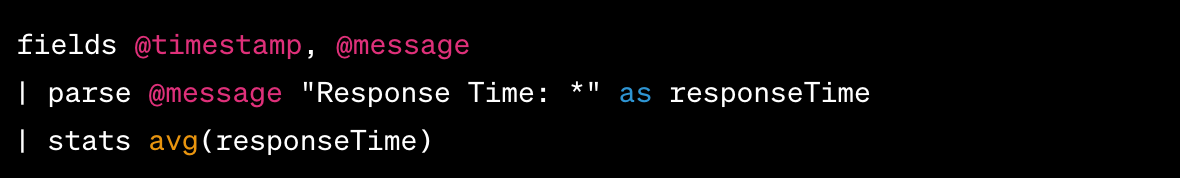
In this query:
- fields
@timestamp,@messageselects the timestamp and message fields from your logs. - | parse
@message "Response Time: *"as responseTime parses the@messagefield to extract the value following the text "Response Time: " and labels it as responseTime. - | stats
avg(responseTime)calculates the average of the extractedresponseTimevalues.
Natural Language Prompt: "Please provide the duration of the ten invocations with the highest latency."
Auto-generated query by CloudWatch
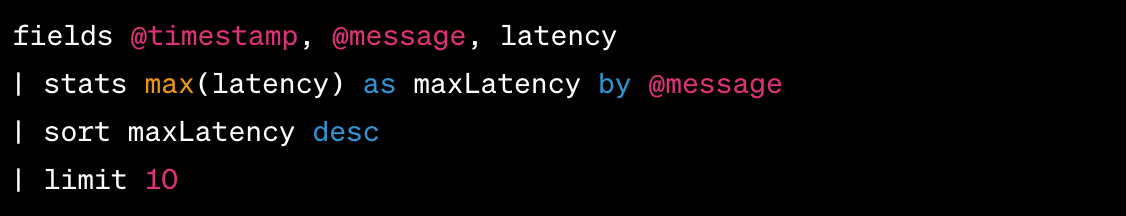
In this query:
- fields @timestamp, @message, latency selects the @timestamp, @message, and latency fields from the logs.
- | stats max(latency) as maxLatency by @message computes the maximum latency value for each unique message.
- | sort maxLatency desc sorts the results in descending order based on the maximum latency, showing the highest values at the top.
- | limit 10 restricts the output to the top 10 results with the highest latency values.
We can execute these queries in the CloudWatch “Logs Insights” query box to filter the log events from the application logs.
These queries extract specific information from the logs, such as identifying errors, monitoring performance metrics, or tracking user activities. The query syntax might vary based on the particular log format and the information you seek.
Conclusion
CloudWatch's machine learning features offer a robust solution for managing the complexities of log data. These tools make log analysis more efficient and insightful, from automating pattern analysis to enabling anomaly detection. The addition of generative AI for query generation further democratizes access to these powerful insights.
Opinions expressed by DZone contributors are their own.

Comments