Workload Protection in the Cloud: Why It Matters More Than Ever
Protecting cloud workloads is crucial as threats evolve and environments become more complex. Learn about effective Cloud Workload Protection (CWP) here.
Join the DZone community and get the full member experience.
Join For FreeThe swift progress in cloud technology has made data and application security an important requirement rather than just a preference. As more customer businesses are moving their operations to the cloud, safeguarding their cloud workloads — referring to all deployed applications and services — has become increasingly essential. Cloud Workload Protection (CWP) is important in this area because it ensures that these workloads remain secure and resilient against a growing range of threats.
Why CWP Is Essential
CWP is a necessity that must not be ignored. As the adoption of cloud technology grows, the scale and complexity of threats also escalate. Here are the reasons why CWP is critical:
- Increased threat environment: Cyber threats are becoming more complex and frequent. CWP tools are crafted to detect and counter these changing threats in real time, delivering enhanced protection for cloud workloads exposed across various networks and environments.
- Protection against data breaches and compliance: Data breaches can lead to severe financial and reputational harm. CWP tools assist organizations in complying with strict regulations like GDPR, HIPAA, and PCI-DSS by implementing strong security protocols and compliance checks.
- Maintenance of operational integrity: It is essential for businesses to maintain the uninterrupted operation of their cloud workloads without being affected by security incidents. CWP tools offer extensive threat detection and automated responses, minimizing disruptions and upholding operational integrity.
- Cost implications: Security breaches can incur substantial costs. Investing in CWP tools helps avert these risks by early identification of vulnerabilities and threats, finally protecting organizations from potential financial losses due to breaches and service interruptions.
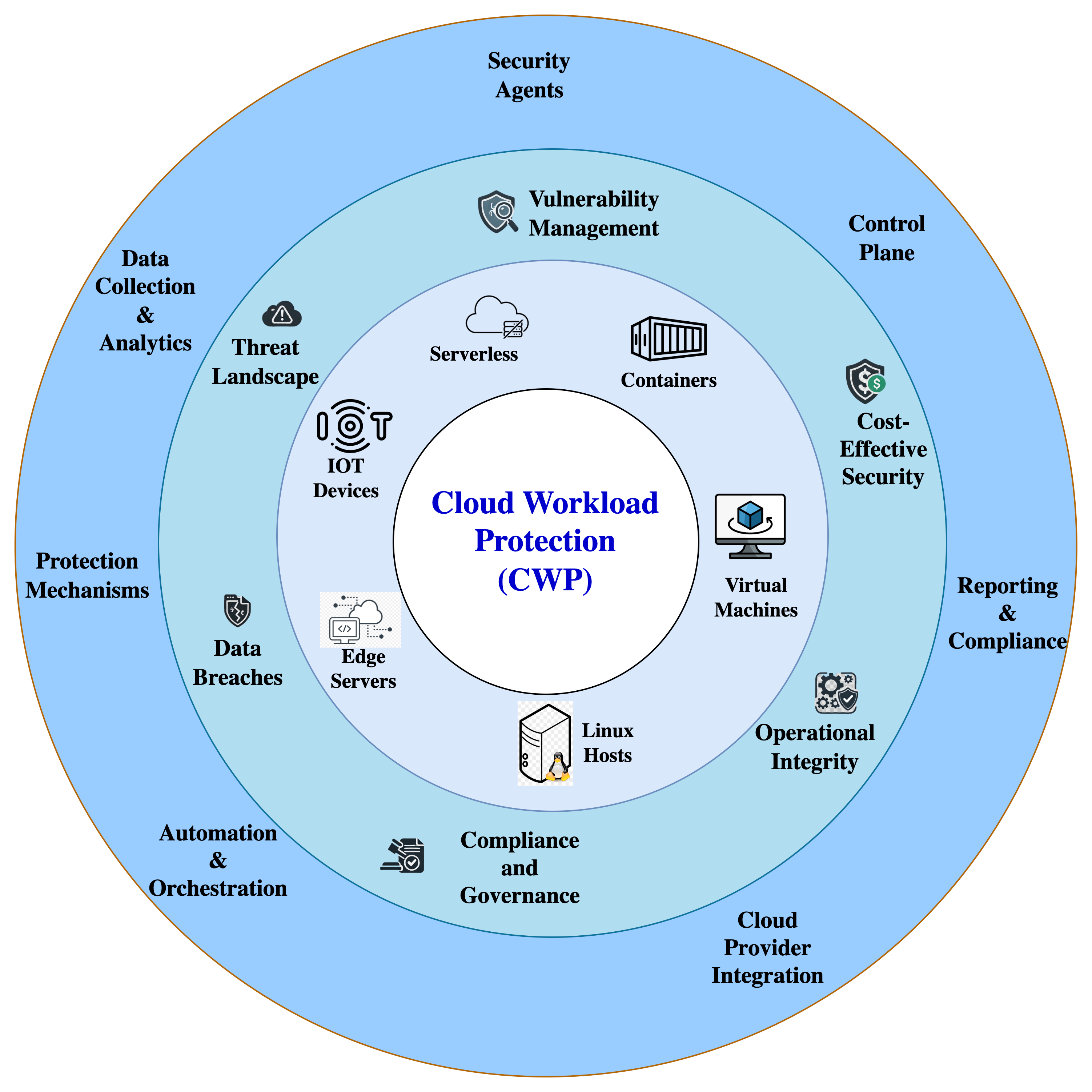
The below picture depicts the components, functionalities, and platforms supported by CWP.
![CWP overview graphic]() The Advantages of CWP
The Advantages of CWP
Investing in Cloud Workload Protection provides several important benefits:
- Advanced threat detection: CWP solutions use advanced technology to recognize and respond to potential threats in real-time, and provide a proactive defense strategy that adapts to emerging threats.
- Automated security updates: CWP tools regularly update themselves to tackle recent vulnerabilities, reducing the manual workload on IT teams and ensuring uninterrupted protection.
- Centralized management: A unified overview of security across all cloud workloads optimizes management and enhances oversight through intelligent insights and alerts.
- Flexibility and scalability: As cloud environments grow, CWP solutions can adapt accordingly, providing strong protection without compromising performance.
Compliance and CWP
Regulatory compliance is a key motivation for implementing CWP. Regulations such as GDPR, HIPAA, and PCI-DSS enforce stringent security criteria to protect sensitive information. CWP tools aid in fulfilling these requirements with:
- Data encryption: Guaranteeing that sensitive data is encrypted both at rest and when transmitted.
- Continuous monitoring: Maintaining constant surveillance of workloads, quickly identifying and addressing potential security concerns.
- Thorough auditing: Delivering comprehensive records and logs of data access and modifications for compliance reporting.
Distinguishing CWP from Application Security
While CWP and Application Security are both essential, they focus on different elements.
- CWP encompasses the entirety of the cloud environment, including infrastructure, virtual machines, and data. CWP aims to secure all parts of the cloud workload, outlining a comprehensive security strategy.
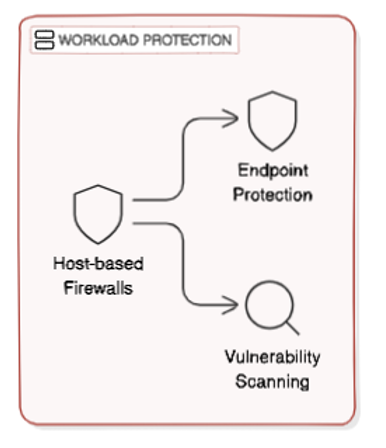
- Application Security concentrates on securing individual applications against vulnerabilities and attacks. This aspect is more concerned with protecting the code and functions of the applications themselves.
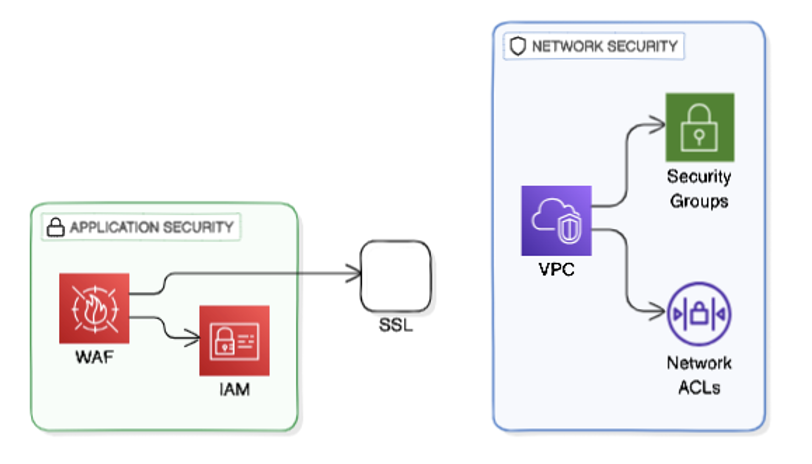
Essentially, CWP is like securing the entire structure, while Application Security pertains to locking and safeguarding each individual room within that structure.
Tools and Technologies for CWP
A variety of tools and technologies can deliver effective CWP. Here are some notable examples from leading cloud platforms:
IBM Cloud
- IBM Security QRadar: Offers advanced security analytics and threat intelligence
- IBM Cloud Hyper Protect: Provides sophisticated data encryption and secure key management
- IBM Security and Compliance Center (SCC): Supplies comprehensive tools to manage security and compliance across cloud environments, integrating threat intelligence, risk management, and compliance monitoring to enhance the overall security posture
Google Cloud
- Google Cloud Security Command Center: Provides insights into the cloud environment and identifies potential threats
- Chronicle Security: Analyzes large volumes of security data to swiftly detect and respond to threats
Microsoft Azure
- Azure Security Center: Offers unified security management and advanced threat protection
- Microsoft Sentinel: A cloud-native SIEM solution for intelligent security analytics and threat detection
Amazon Web Services (AWS)
- AWS Shield: Provides protection against DDoS attacks and enhances overall security
- AWS GuardDuty: Monitors for malicious activities and unauthorized actions
Role of CSPM and CWP in Modern Cloud Environments
Cloud Security Posture Management (CSPM) and CWP are complementary in nature but focus on different areas. CSPM aims to improve the overall security posture of the cloud environment by identifying configuration errors and compliance issues. CWP focuses specifically on the security of the workloads themselves, encompassing applications, data, and infrastructure.
Conclusion
It's becoming increasingly important to focus on protecting their workloads. This means keeping sensitive data safe, maintaining regulatory compliance, and making sure critical applications run smoothly. By embracing CWP and combining it with other essential tools and practices, companies can build a strong and secure cloud environment that stands up to today’s cyber threats.
Opinions expressed by DZone contributors are their own.

Comments