Deep Dive Into Architecture of MuleSoft Anypoint VPC, VPN and Dedicated Load Balancer
VPC stands for Virtual Private Cloud and it allows you to create logical or isolated networks in the cloud where you can deploy or run the resources securely.
Join the DZone community and get the full member experience.
Join For FreeWhat Is Anypoint VPC?
VPC stands for Virtual Private Cloud and it allows you to create logical or isolated networks in the cloud where you can deploy or run the resources securely. MuleSoft CloudHub is a multi-tenant integration platform as a service. AnyPoint VPC allows you to create an isolated network where you can host the workers or mule applications.
Anypoint VPC allows you to extend your corporate network and allows CloudHub workers to connect resources behind the firewalls. VPC connects CloudHub workers to an on-premise datacenter using below techniques
- Secure VPN Tunnel (IPSec Tunneling)
- Private AWS using VPC Peering.
- AWS Direct Connect.
Advantages of Anypoint VPC
- Create a secure virtual network within CloudHub.
- Connect CloudHub to assets behind the firewall.
- Deploy mule runtime securely.
- Connect Cloudhub to any public cloud or on-premise data center securely.
Anypoint VPC Characteristics
- Multiple VPC can be created in the same region.
- Always create VPC in the same region or near to your datacenter or AWS region (VPC peering).
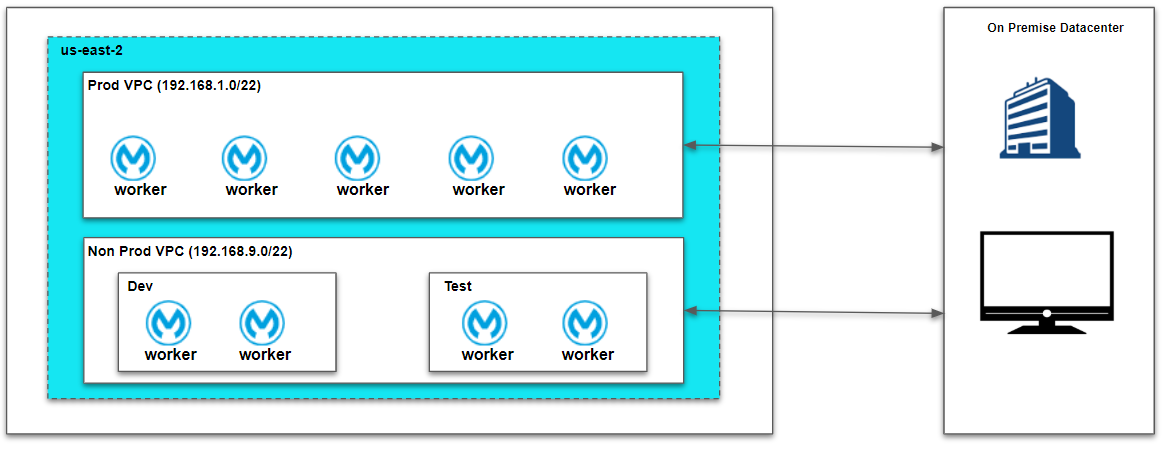
- All non-prod environments like dev, test, sit can be mapped to non-prod vpc and production environment to prod vpc.
- Multiple environments can be mapped to the same VPC’s.
- Always create the VPC in the parent business group and share it with sub-business groups.
VPC Sizing
It is very important to decide on a CIDR (Classless Inter Dynamic Routing) mask before we create VPC's. Please go through the video below which will explain how to perform VPC sizing and it will be useful to go through this article.
Anypoint VPC Best Practices
- Always create a VPC in the same region or close to your datacenter or AWS region (VPC Peering).
- Always choose a higher or appropriate range of CIDR masks because the CIDR mask cannot be updated once VPC is created. To change the CIDR mask, we need to re-create VPC and it requires downtime for your applications.
- Always choose a CIDR mask that doesn't overlap with your datacenter IP addresses or subnets.
- Always create a separate VPC for production and non-production environments.
- Always create VPC in parent business groups and share with child business groups.
Setting Up Anypoint VPC
For setting up VPC, you need to navigate to Runtime Manager => VPC and Create VPC.

Provider Name, CIDR Block and select environments that need to be part of the VPC (there can be multiple environments mapped to a single VPC). Generally, we can create separate VPC for prod and non-prod environments (Map non-prod environments like test, sandbox, uat to non-prod VPC, and production environments to prod VPC).
Select region which is near to your datacenter or AWS region (VPC peering).
Business Groups will be selected by default if your Anypoint Platform has a single business group. For multiple business groups, you can select from the drop-down and it is best practices to create VPC in the main business group and share with the child business group.
MuleSoft provides four firewall rules by default. You can add more firewall rules as per your requirements.
| Type | Port | Firewall Rule |
| http.port | 8081 | Accessible from anywhere outside VPC or public internet over HTTP |
| https.port | 8082 | Accessible from anywhere outside VPC or public internet over HTTPS. |
| http.private.port | 8091 | Accessible from anywhere within VPC over HTTP. |
| https.private.port | 8092 | Accessible from anywhere within VPC over HTTPS. |
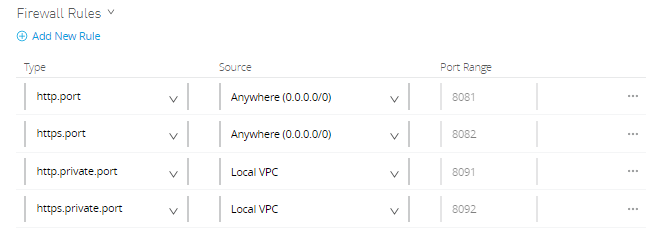
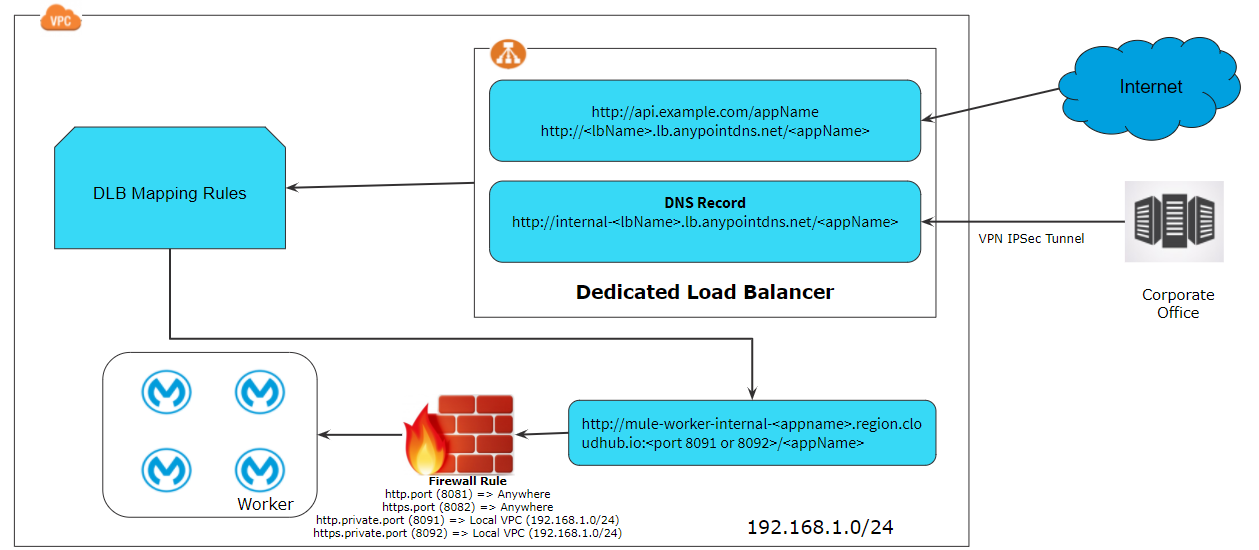
Whenever you deploy an application on port 8091 or 8092, it is accessible within VPC. This means the application cannot be accessible over the internet. To access such applications over the internet, you can create a dedicated load balancer within VPC and you can allow applications either to be accessed by everyone or you can whitelist the CIDRs.
Anypoint VPC [Video]
What Is Anypoint Dedicated Load Balancer?
Dedicated Load Balancer is an optional component in Anypoint Platform which allows the route of external HTTP/HTTPs traffic to multiple applications deployed to CloudHub within VPC.
Each Dedicated Load Balancer has a DNS A record lb-name.lb.anypointdns.net that resolves to the two public IP addresses of the two instances.
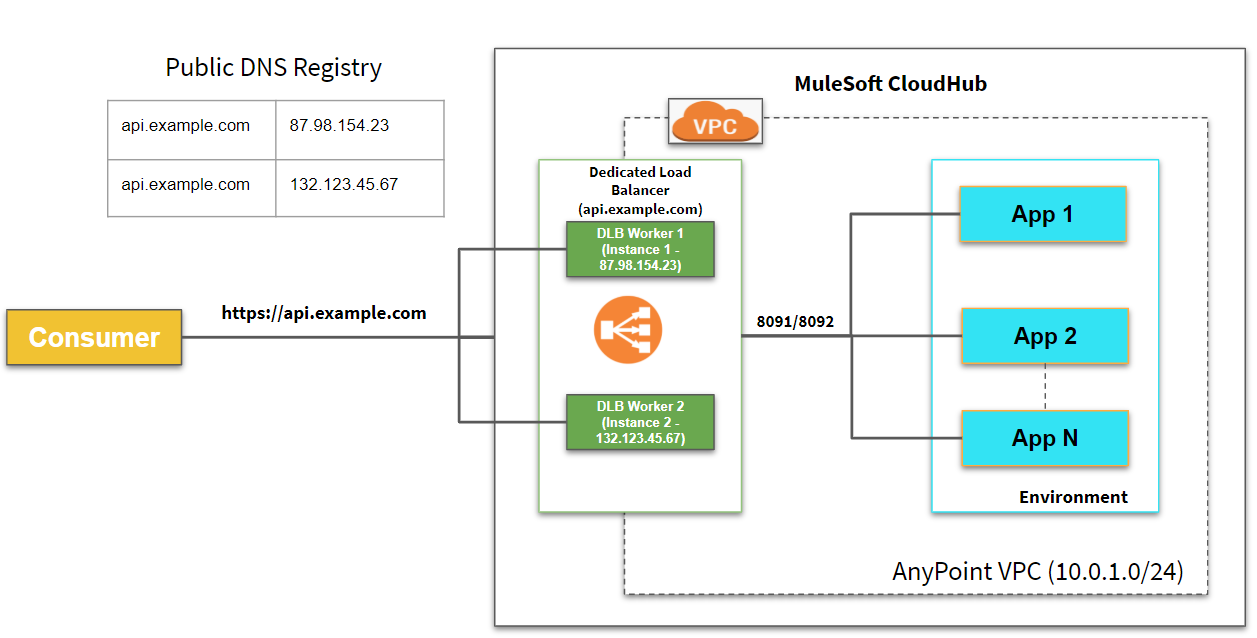
Note: IP Addresses used in the above pictures are just examples.
Shared Load Balancer V/S Dedicated Load Balancer
Shared Load Balancer
- Shared Load Balancer is available in all environments by default.
- Shared Load Balancer provided basic functionality like TCP load balancing.
- Shared Load Balancer doesn’t allow you to configure custom SSL certificates and proxy rules.
- Shared Load Balancers have lower rate limits and it is different for each region.
Application deployed to Cloudhub exceeds the rate limit for shared load balancers, it will return 503 - Service Unavailable.
Dedicated Load Balancer
- One of the limitations of SLB is the lower rate limit. To avoid that issue, you can use a dedicated load balancer.
- All applications can be hosted under a single domain.
- Custom SSL certificates can be configured on DLB and optionally two-way authentication can be enforced.
- Handle load balancing among the different CloudHub workers that run your application.
Setting Up Dedicated Load Balancer
For setting up a dedicated load balancer, you need to create VPC first and then create a dedicated load balancer within VPC.

Provider Name, select Target VPC, number of workers (generally 2 workers for HA), timeout.

HTTP Inbound Mode
- Off: Causes the load balancer to silently drop the request.
- On: Accepts the inbound request on the default SSL endpoint using the HTTP protocol.
- Redirect: Redirects the request to the same URL using the HTTPS protocol.
Other Configurations
- Disable Static IPs specifies to use dynamic IPs, which do not persist when the DLB restarts.
- Keep URL encoding specifies the DLB passes only the %20 and %23 characters as is.
If you deselect this option, the DLB decodes the encoded part of the request URI before passing it to the CloudHub worker.
Support TLS 1.0 specifies to support TLS 1.0 between the client and the DLB. - Upstream TLS 1.2 specifies to force TLS 1.2 between the DLB and the upstream CloudHub worker.
Dedicated Load Balancer Certificates
Configure SSL certificate to enable HTTPS (Public Key and Private Key). For two way authentication, you can configure Client Certificate and that is optional. The dedicated load balancer must be associated with at least a pair of one certificate.

Generally, we configure the certificates on Dedicated Load Balancer from CA authority. For testing purposes, you can use self-signed certificates.
xxxxxxxxxx
openssl req -newkey rsa:2048 -nodes -keyout test-private.pem -x509 -days 3000 -out test-public-crt.pem
The above command will generate Private Key and Public Key that can be configured on a dedicated load balancer. Alternatively, you can generate certificates bypassing .cfg file in OpenSSL command.
You can add below content in .cfg file and pass to OpenSSL command.
x
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
req_extensions = req_ext
prompt = no
[ req_distinguished_name ]
countryName = US
stateOrProvinceName = Arizona
localityName = Phoenix
organizationName = Test
commonName = example.com
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
DNS.1 = api-dev.example.com
DNS.2 = api-qa.example.com
OpenSSL Command
xxxxxxxxxx
openssl req -newkey rsa:2048 -nodes -keyout test-private.pem -x509 -days 3000 -out test-public-crt.pem -config test-com.cfg
Creating Wildcard Certificates
You can even create the wild card certificate to support subdomain requests.
x
[ req ]
default_bits = 2048
distinguished_name = req_distinguished_name
prompt = no
[ req_distinguished_name ]
countryName = US
stateOrProvinceName = Arizona
localityName = Phoenix
organizationName = Test
commonName = *.example.com
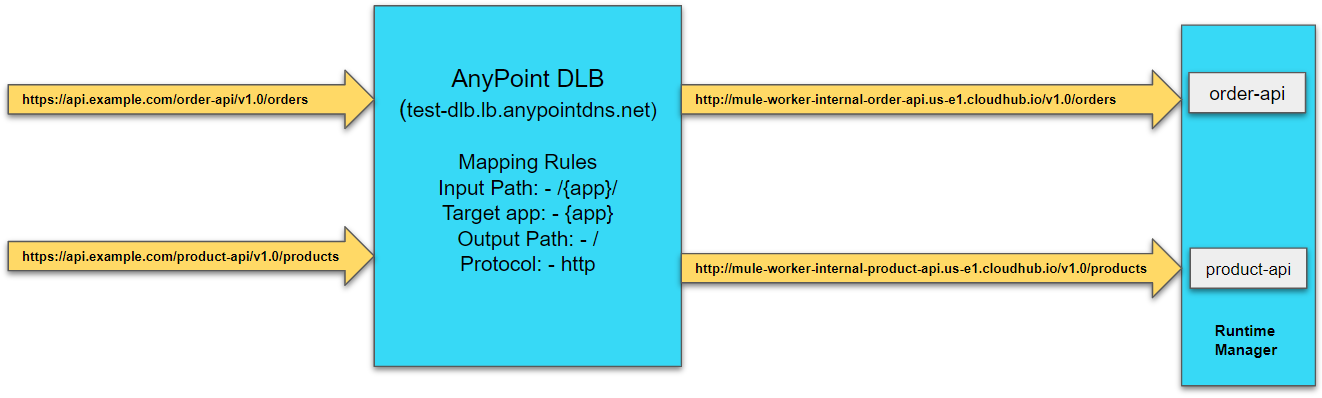
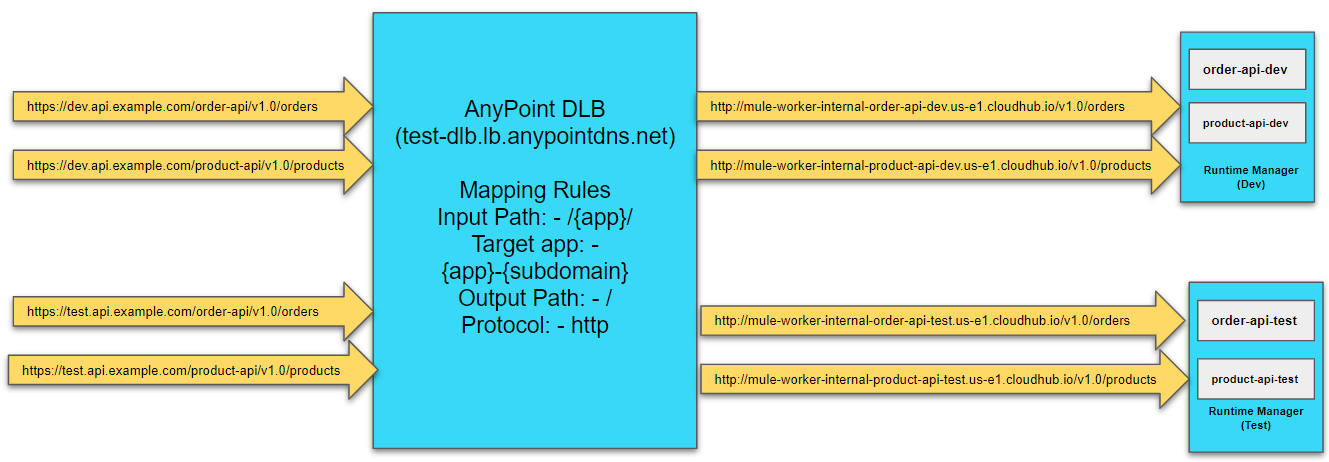
Dedicated Load Balancer Mapping Rules
Mapping rules are used on dedicated load balancers to translate input URI to call applications deployed on CloudHub. A pattern is a string that defines a template for matching an input text. Whatever value is placed within curly brackets ({ }) is treated as a variable. Variable names can contain only lowercase letters (a-z) and no other characters, including slashes.
For more details on dedicated load balancer mapping rules, please go through this article.
Input Path |
Target App |
Output Path |
Protocol |
/{app}/ |
{app} |
/ |
http |
/{app}/ |
org-{app}-{subdomain} |
/ |
HTTP |
Example 1
Example 2
Dedicated Load Balancer Whitelisted CIDRs
To allow dedicated load balancers must be used by a set of IP addresses or single IP addresses, you need to add those IP addresses in the form of CIDR notations (e.g. 192.168.1.0/24).

By default, the CIDR mask is 0.0.0.0/0 which means all IP addresses are allowed to access dedicated load balancer.
Anypoint Dedicated Load Balancer [Video]
What Is Anypoint VPN?
VPN stands for Virtual Private Network and Anypoint VPN creates a secure connection between CloudHub and On-Premise data centers.
- AnyPoint VPN supports site-to-site internet protocol security (IPSec) connections.
- Each Anypoint VPN connection consists of two tunnels that enable you to connect to a single public IP address at a remote location. To connect additional remote locations, create another VPN.
- The physical or software appliances, called VPN endpoints, are terminators on your side of the connection.
- The MuleSoft side of the connection is an implementation of a virtual private gateway (VGW). The MuleSoft VGW is associated with a single MuleSoft VPC but can support up to 10 VPN connections.
- The MuleSoft VGW implementation supports a maximum throughput of 1.25 Gbps.
Types of VPN Routing
Anypoint VPN supports dynamic or static routing for VPN connections.
- Dynamic routing - Your device uses the Border Gateway Protocol (BGP) to advertise routes to Anypoint VPN. Use BGP routing if your device supports this protocol.
- Static routing - requires you to specify the routes (subnets) in your network that are accessible through Anypoint VPN.
| Static Routing | Dynamic Routing (BGP) |
| Static routing is also known as non-adaptive routing which doesn't change the routing tables unless the administrator modified or updated it manually. |
Dynamic routing is also known as adaptive routing as routing tables are updated automatically if any changes happen in the network topology. |
| Static routing is implemented in smaller networks. | Dynamic is implemented in complex or bigger networks. |
| Static routing is highly secure. | Dynamic routing is less secure. |
| Static routing doesn't follow any specific protocols. | Dynamic routing supports BGP, RIP, EIGRP protocols. |
| Static routing doesn't use any complex routing algorithms to figure out the shortest path. | Dynamic routing uses complex routing algorithms to figure out the shortest path. |
Anypoint VPN IPSec Tunneling
VPN IPSec tunnel is a set of protocols or standards to establish a connection with an on-premise datacenter. IPSec tunnel is applied at the IP layer and it allows us to connect the entire network instead of a single device.
Note: IP Addresses used in the above pictures are just examples.
Anypoint VPC Peering
VPC peering connects two VPCs. In this case, it pairs your private Amazon VPC directly to your Anypoint VPC. This enables you to route traffic between the two VPCs so they can communicate as though they are in the same network.
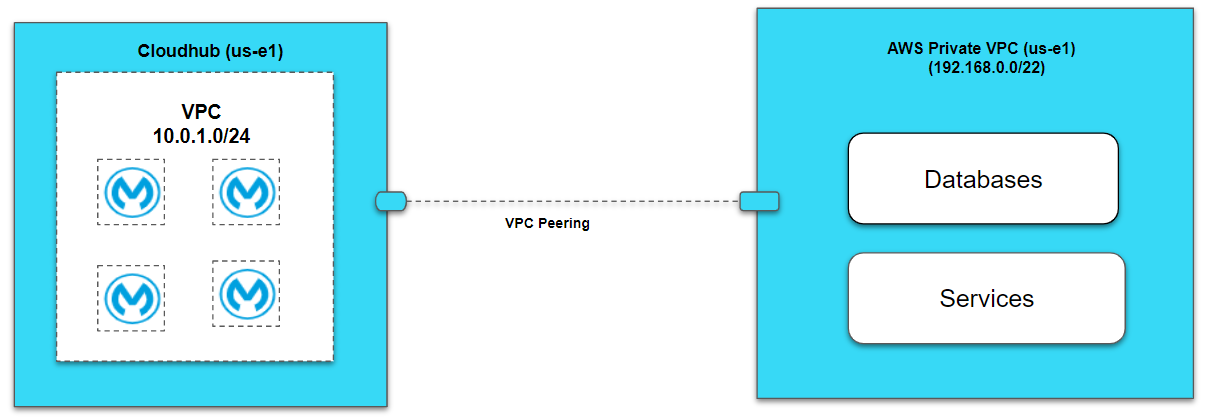
Note: IP Addresses used in the above pictures are just examples.
Setting Up Anypoint VPN IPSec Tunneling
For Setting Up VPN, you navigate to Runtime Manager ⇒ VPN.
Name: Provide name of VPN
VPC: Select the VPC from the drop-down for which you need to create a VPN.
Remote IP Address: Enter Remote IP Address of your VPN Endpoint or VPN device.
Selecting the routing type Dynamic or Static
Dynamic Routing
Select Dynamic routing in case your VPN device supports BGP.
Enter Remote ASN (64512–65534) and the default is 65001. You can use an existing ASN in your network or a private ASN that is not assigned to your network.
Enter Local ASN (64512-65534) and the default is 64512. Use Private ASN and that should not be assigned to your network. This ASN is for MuleSoft.

Static Routing
Select Static routing and enter the CIDR range, that needs to be accessible through the VPN (e.g. 192.168.0.0/22).
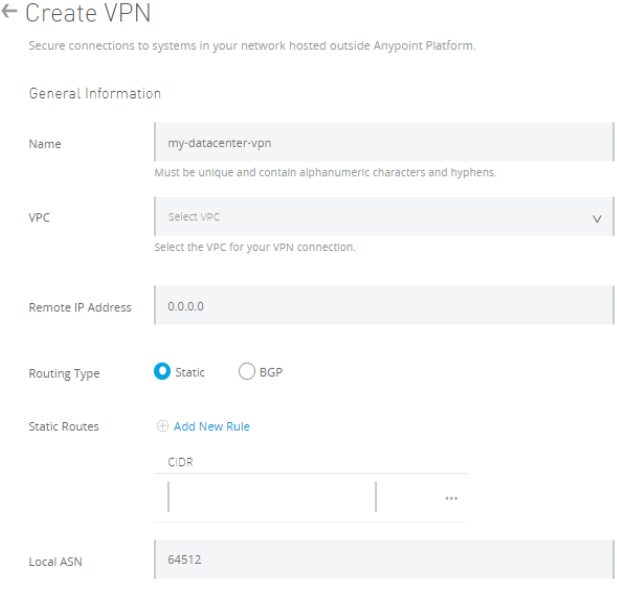
You can add more CIDR range using Add New Rules in static routes and up to 95 subnets can be added.
Select Tunnel Configuration 1.) Automatic 2.) Custom
In the case of Automatic, no other configuration required and it will automatically create a tunnel for your Anypoint VPN and which can be visible after creation.
In the case of Custom, you need to provide PSK (8-64 characters) and point-to-point CIDR. You can specify a size /30 CIDR block from the 169.254.0.0/16 range.
The CIDR block must be unique across all VPN connections. CIDR block not supported.
- 169.254.0.0/30
- 169.254.1.0/30
- 169.254.2.0/30
- 169.254.3.0/30
- 169.254.4.0/30
- 169.254.5.0/30
- 169.254.169.252/30


Once VPN is created, you can download VPN config and share it with your network administrator to perform configuration on VPN devices.

| Status | Tunnel 1/2 | Description |
| Pending | Down/Down | A VPN connection is created and actions pending in the background. |
| Available | Down/Down | VPN is successfully created but the remote side is not configured. |
| Available | Up/Up or Up/Down | VPN is successfully created and remote connection is established in Active/Active mode or Active/Passive mode. |
| Failed | Down/Down | A VPN connection is not created. You need to delete and try again. |
AnyPoint VPN [Video]
Anypoint VPC, VPN, and DLB Architecture
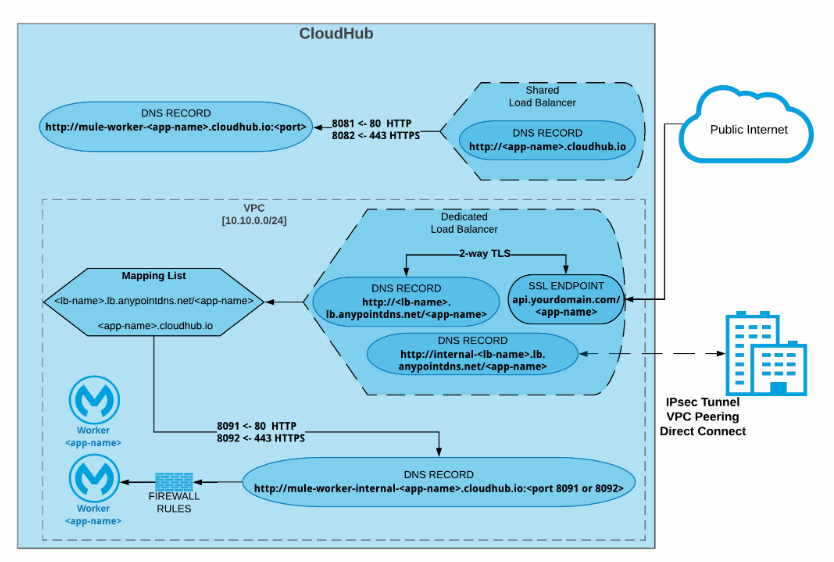
Accessing Application within VPC
For accessing applications within VPC, you can use the below URLs.
Port 8091: http://mule-worker-internal-<appname>.region.CloudHub.io:8091/
Port 8092: https://mule-worker-internal-<appname>.region.CloudHub.io:8092/
Creating AnyPoint VPC, VPN and DLB is the self-service but you can request MuleSoft to create VPN IPSec tunneling, VPC Peering, or AWS Direct Connect by filling AnyPoint VPC discovery template.
Important Points
- Once a VPC is created, to modify the name, CIDR mask, you need to delete and recreate the VPC which may lead to downtime of your applications.
- Always select the higher range of the CIDR mask. So you have enough IP addresses available.
VPC Use Cases
- To run the integration or API's within secure networks or private subnets, you can deploy API within the VPC. For example, you have system APIs that are accessing backend databases and those APIs must be deployed within a secure or private network in CloudHub, so it is accessible by the applications deployed within the same VPC.
- For creating the dedicated load balancer, we need to create a VPC.
- For creating VPN IPSec tunneling, AWS Direct Connect, or VPC peering, we need to create a VPC.
There are many other use cases where we have the requirements of VPC.
Accessing Application Over Public Internet When Deployed Within VPC
There are various ways that you can API's over the public internet when an application is deployed within the VPC.
- Deploy the application on port 8081 (http.port) or 8082 (https.port), as per the above firewall rule these ports are accessible anywhere. So this APIs can be access using http://<appname>.region.CloudHub.io/ or https://<appname>.region.CloudHub.io/
- In case an application deployed on port 8091 (http.private.port) or 8092 (https.private.port), as per the above firewall rule these ports are accessible within VPC. So these APIs can be accessed on our public internet using a dedicated load balancer if your IP Address is whitelisted in DLB configurations.
Accessing Application via SLB Deployed Within VPC
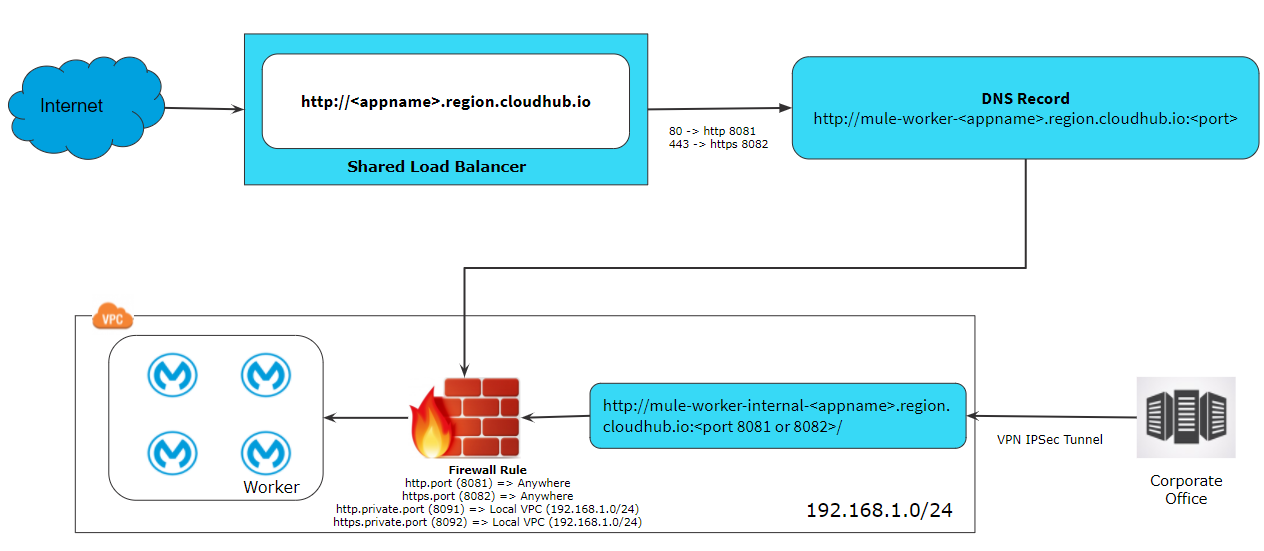
Accessing Application via DLB Deployed Within VPC
Complete Video Playlist - Anypoint VPC, DLB and VPN With Live Demonstration
https://www.youtube.com/playlist?list=PL5GwZHHgKcuDQ6vWarTLgVbrPEQipzbOM
References
- https://docs.mulesoft.com/runtime-manager/vpc-architecture-concept
- https://docs.mulesoft.com/runtime-manager/virtual-private-cloud
- https://docs.mulesoft.com/runtime-manager/vpn-about
- https://docs.mulesoft.com/runtime-manager/dedicated-load-balancer-tutorial
- https://dzone.com/articles/what-is-cidr-classless-inter-domain-routing-in-mul
- https://dzone.com/articles/implementing-mapping-rules-with-mulesoft-dedicated
Now, you know the architecture and components of Anypoint VPC, VPN, and DLB.
Opinions expressed by DZone contributors are their own.


Comments