Custom Vulnerability Risk Scores: Prioritizing Threats With Precision
Learn how custom risk scores empower security teams to cut through the noise of vulnerability alerts and enable them to move with agility.
Join the DZone community and get the full member experience.
Join For FreeThe security landscape is riddled with vulnerabilities, leaving security teams with overwhelming choices. Prioritization is essential. How do you determine which vulnerabilities pose the greatest threat, balance remediation costs against risk, and explain your decisions to stakeholders? Vulnerability prioritization empowers security teams to answer these questions, methodically ranking vulnerabilities according to their potential damage and the urgency required for action.
Why Prioritization Matters
- Limited resources: You, like everyone, have finite time, budget, and personnel to tackle security issues. Prioritization lets you focus these resources on the areas that matter most.
- Overwhelming data: SCC can generate a vast number of findings. Prioritizing helps you cut through the noise and take targeted action.
- Risk reduction: Focusing on the most dangerous vulnerabilities lets you minimize potential harm from cyberattacks.
- Compliance adherence: Fixing vulnerabilities that violate key security standards allows you to demonstrate adherence and avoid possible penalties.
Common Methods for Prioritizing Vulnerability Remediation
Prioritizing vulnerability remediation involves evaluating and ranking them based on factors such as potential business impact, exploitability, and the importance of affected systems.
This table provides additional details about key factors:

Understanding CVSS
CVSS offers a universal language for assessing the technical severity of vulnerabilities. Scores range from 0 to 10, with higher scores indicating greater danger. CVSS considers factors like:
- Attack complexity: The difficulty of exploiting the vulnerability.
- Required privileges: The level of access an attacker needs.
- Impact: Potential damage to confidentiality, integrity, and availability of systems.
- Temporal metrics: Factors like exploit availability and remediation level.
- Environmental metrics: How the vulnerability might impact an organization based on its specific deployment.

The primary metrics within the CVSS, known as base scores, have gained widespread acceptance as a fundamental component. However, a common misconception arises, assuming that these base scores provide a comprehensive risk assessment. In reality, base scores only capture certain facets of risk, such as vulnerability exploitability, and severity.
Relying solely on CVSS base scores to prioritize vulnerabilities often presents a daunting challenge. A glance at recent data reveals the staggering volume of vulnerabilities classified as "critical." Within the last year, 30,296 vulnerabilities were reported, with over half, precisely 16,425, rated 7 or higher on the 9-point scale, according to CVE Details. Faced with such a multitude of critical vulnerabilities, developers inevitably confront the pressing question: "How can we effectively manage this overwhelming number?"
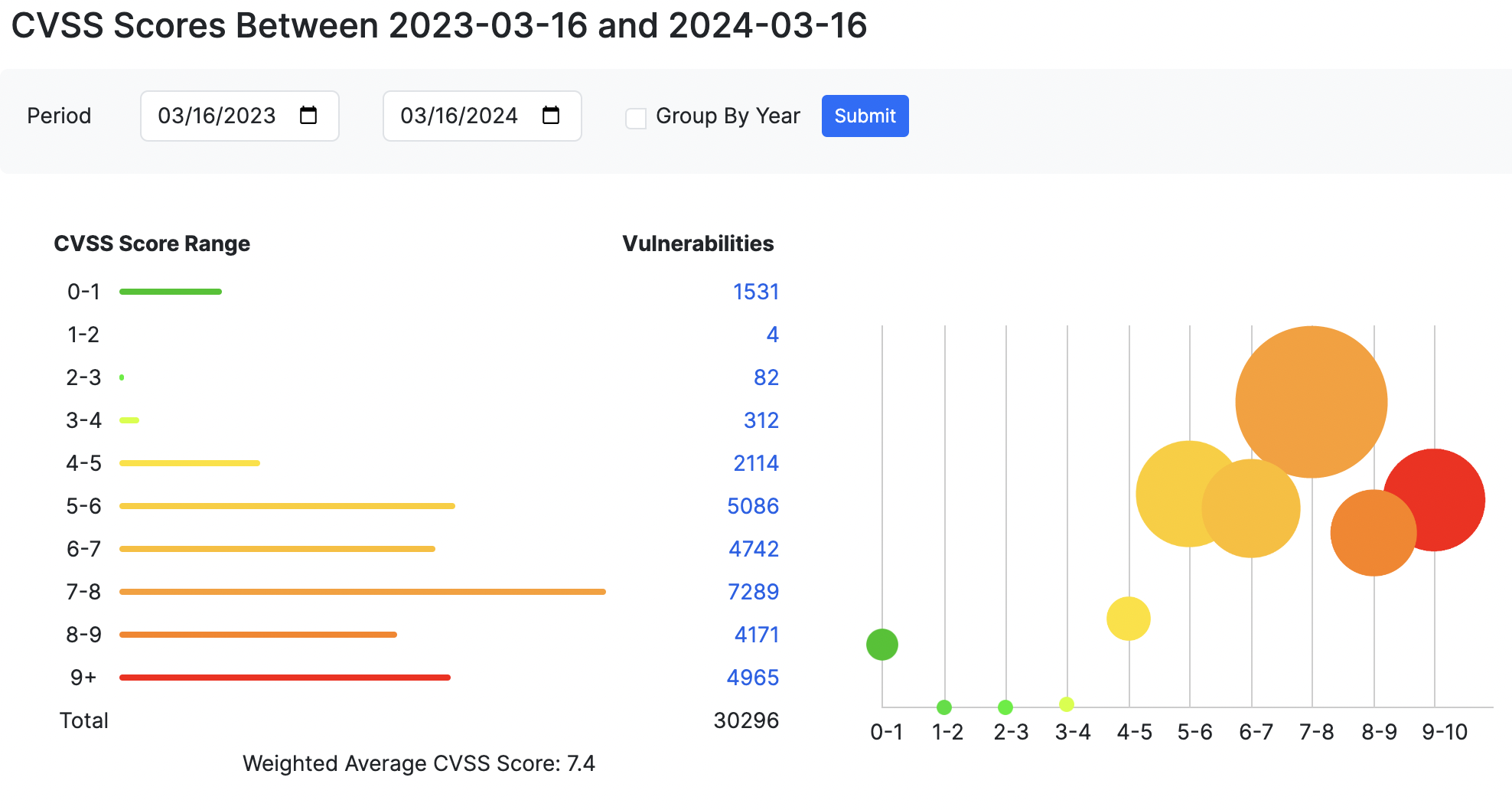
Leveraging EPSS
EPSS, or the Exploit Prediction Scoring System, stands out as a specialized vulnerability scoring framework meticulously crafted to gauge the probability of a vulnerability being exploited. Its methodology revolves around aggregating published exploit data sourced from diverse channels, including IDS/IPS systems, host-based agents, and repositories housing exploit code like Exploit-DB and Metasploit. Through this comprehensive data gathering, EPSS assimilates crucial information regarding the vulnerability's specific characteristics, thereby facilitating a more accurate estimation of its exploit likelihood. Of the 30,296 CVEs published in the last year, only 652 have an EPSS score of over 1%.
Why EPSS Matters
- Limited resources necessitate efficient vulnerability prioritization.
- EPSS helps focus efforts on vulnerabilities with the highest real-world risk of exploitation, even if their severity score isn't the highest.
Limitations of EPSS
- Predicts the future, which is inherently uncertain.
- Doesn't replace CVSS, as it doesn't factor in severity.
- Only works with known CVEs
- Needs additional business context for true risk-based decision-making.
The Power of Customization
While CVSS and EPSS provide valuable insights into vulnerability severity and exploit likelihood, custom scoring is essential for organizations looking to tailor their risk management approach to their specific needs, achieve a more comprehensive risk assessment, enhance prioritization, and maintain agility in the face of evolving threats.
- Asset criticality: How crucial the affected asset is to your core business operations and sensitive data.
- Exploit availability: Whether known, easily accessible exploits exist.
- External exposure: Whether the vulnerable system or component faces the internet.
- Mitigating controls: The strength of existing protections (e.g., firewalls, intrusion prevention, patching).
- Business impact: The potential financial, operational, reputational, or compliance-related damage stemming from a successful exploit.
Developing Your Custom Scoring Model
Developing a customized scoring model for vulnerability management requires a holistic understanding of your organization's assets and associated risks. Here's a refined guide, supplemented with examples, emphasizing the importance of maintaining an asset inventory to identify risk factors effectively:
Maintain asset inventory: Begin by establishing and maintaining a comprehensive inventory of your organization's assets. For instance:
- Business criticality: Identify assets critical to revenue generation, such as customer-facing web applications or payment processing systems.
- System complexity: Recognize complex systems like legacy infrastructure or interconnected network devices, which may present elevated risks due to intricate configurations.
- Data sensitivity: Highlight assets that handle sensitive data, such as customer personally identifiable information (PII) or financial records.
- Public facing: Flag assets exposed to the internet, such as web servers or remote access gateways, which are prone to exploitation by external threats.
- Compliance scope: Identify assets subject to regulatory requirements, such as healthcare data governed by HIPAA or financial transactions regulated by PCI DSS.
- Customer category: Assess the impact of vulnerabilities on different customer segments, such as retail customers versus enterprise clients, to prioritize remediation efforts accordingly.
- Develop scoring methodology: Integrate your asset inventory and risk factors into a scoring methodology that combines CVSS and EPSS metrics with contextual information. For example:
- Formula: Calculate vulnerability scores using a formula that incorporates CVSS base scores, EPSS predictions, and weighted risk factors.
- Qualitative matrix: Map vulnerability severity levels and exploit likelihood to qualitative ratings (e.g., low, medium, high) based on weighted risk factors.
- Conditional logic: Implement conditional statements to adjust vulnerability scores based on specific risk factors or threshold values.
Sample Code
This code provides a framework for calculating custom vulnerability risk scores. It does this by combining traditional CVSS scores with additional factors important to your organization, such as asset criticality and data sensitivity.
class Asset:
def __init__(self, name, criticality, sensitivity, compliance_scope):
self.name = name
self.criticality = criticality
self.sensitivity = sensitivity
self.compliance_scope = compliance_scope
# Example assets
web_server = Asset("Web Server", "High", "High", "PCI DSS")
database = Asset("Database Server", "Medium", "High", "HIPAA")
# Define weights for risk factors
risk_weights = {
"Criticality": {"High": 0.3, "Medium": 0.2, "Low": 0.1},
"Sensitivity": {"High": 0.4, "Medium": 0.3, "Low": 0.2}
}
# Automated vulnerability scoring process
def calculate_vulnerability_score(asset):
# Code to fetch CVSS base score and EPSS prediction
cvss_base_score = fetch_cvss_base_score(asset)
epss_prediction = fetch_epss_prediction(asset)
# Calculate vulnerability score
vulnerability_score = cvss_base_score + epss_prediction + (business_criticality_weight * 0.5) + (sensitivity_weight * 0.5)
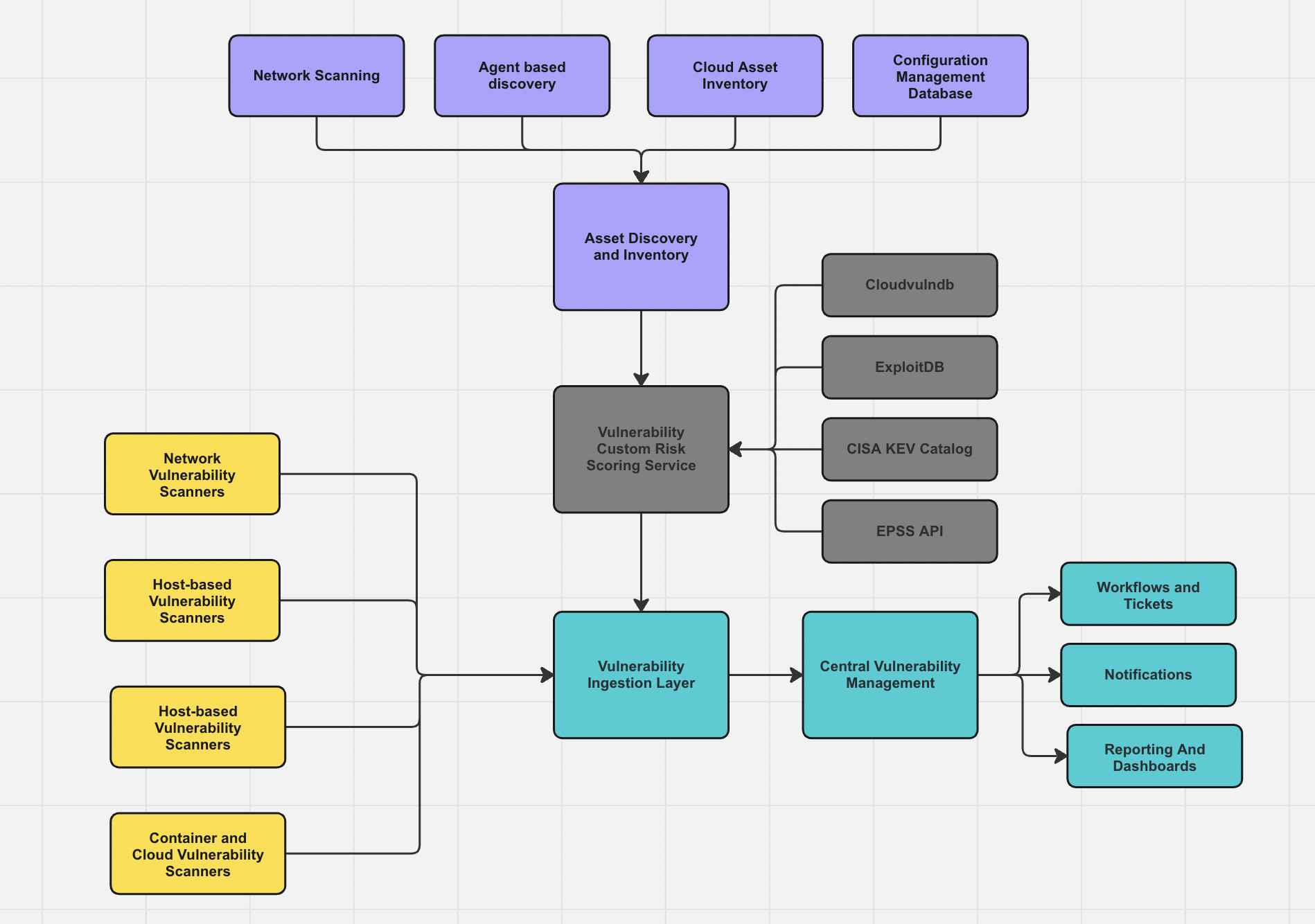
return vulnerability_scoreCustom Vulnerability Risk Management System Overview
This system enhances vulnerability prioritization by combining asset discovery, vulnerability scanning, and a custom risk-scoring engine. The Python code above defines how to model assets (criticality, sensitivity) and calculate risk scores, integrating CVSS with organizational priorities. A central vulnerability management platform consolidates data, calculates custom risk scores, and provides dashboards, notifications, and remediation workflows.
Benefits of Custom Risk Scores
- Laser-focused prioritization: Zero in on the vulnerabilities that truly jeopardize your business operations.
- Optimized resource allocation: Ensure security teams and budgets focus on the most pressing risks.
- Data-driven decisions: Justify actions with quantifiable risk data.
- Adaptability: Regularly review and refine your model to reflect changes in your technology stack, business priorities, and the threat landscape.
Conclusion
Custom risk scores represent a game-changer in cybersecurity, equipping security teams with the tools they need to navigate the complex landscape of vulnerabilities with confidence and agility. By providing a tailored assessment of risk that considers the organization's unique context and objectives, custom risk scores empower security teams to prioritize effectively and respond swiftly to emerging threats. As organizations continue to face an ever-evolving array of cyber risks, custom risk scores will play an increasingly vital role in enhancing security resilience and mitigating potential threats.
Opinions expressed by DZone contributors are their own.

Comments