Critical Infrastructure Protection in the Age of Cyber Threats
Safeguarding critical infrastructure from cyber threats is paramount. Robust defenses and proactive measures are essential for resilience in today's digital landscape.
Join the DZone community and get the full member experience.
Join For FreeCritical Infrastructure Protection is the need to safeguard a nation/region's important infrastructures, such as food, agriculture, or transportation. Critical infrastructures include transportation systems, power grids, and communication systems. Critical infrastructure protection is important to communities because any damage to these infrastructures is dangerous to global economies and the world.
A cyber or cybersecurity threat is a harmful act that seeks to steal data, damage data, or disrupt digital life. Cyber threat is also the possibility of a successful cyber attack that aims to gain prohibited access to damage, disrupt, or steal an information technology asset, computer network, intellectual property, or any other form of sensitive data. Critical infrastructure protection is important to communities because any damage to these infrastructures is dangerous to global economies and the world.
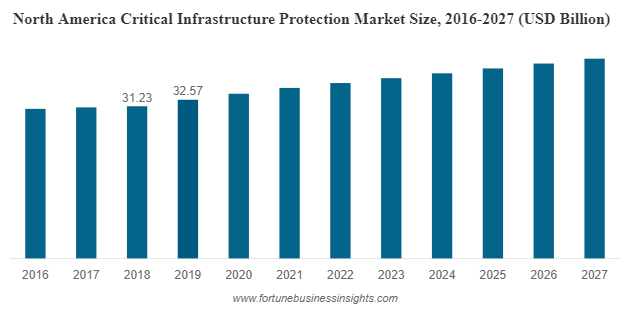
The global critical infrastructure protection market size was valued at USD 96.30 billion in 2019 and exhibited a CAGR of 6.2% during the forecast period. The market is expected to grow to USD 154.59 billion by 2027 and further expand to USD 196.64 billion by 2031.
Importance of Critical Infrastructure Protection
Critical infrastructure protection is important because it protects infrastructural systems like water, energy, and communication systems. It helps prevent interruptions that could prompt monetary misfortunes, compromise public well-being, and affect public safety. By securing critical infrastructure, we upgrade flexibility against natural disasters, cyber dangers, and different crises, encouraging strength and continuity in the face of challenges.
Key Components of Critical Infrastructure
- Risk assessment and management: Before utilizing protective measures, potential risks must be identified. One must conduct thorough risk assessments to understand vulnerabilities and prioritize areas needing immediate attention.
- Cybersecurity measures: With the rise in digitization of critical infrastructure, cybersecurity plays a crucial role. Robust firewalls, encryption, and continuous monitoring are essential to thwart cyber threats that could compromise the integrity of these systems.
- Physical security: It goes beyond the virtual realm to protect critical infrastructure. Physical security measures, such as surveillance systems, access controls, and perimeter defenses, are vital to prevent unauthorized access or sabotage. It goes beyond the virtual realm to protect critical infrastructure.
- Emergency preparedness and response: Building efficient emergency response plans ensures effective and swift actions in the face of disruptions. Regular drills and exercises help test these plans and ensure that responders are well-equipped to handle various scenarios.
- Collaboration and information sharing: Collaboration among government agencies, private sector entities, and international partners is significant for a unified approach to critical infrastructure protection. Sharing information about emerging threats and best practices enhances the collective resilience against potential risks.
Common Cyber Threats to Critical Infrastructure
Common cyber threats to critical infrastructure include malware attacks, DDOS (Distributed Denial Of Service) assaults, malware diseases, phishing endeavors, and advanced persistent threats (APT). These threats can take advantage of weaknesses in frameworks, prompting potential disruption, information breaks, or even sabotage of essential services.
Ransomware: Holding Systems Hostage
A situation of digital hostage is assumed to be ransomware, where cybercriminals encrypt a system's data and request a ransom before its release. In the context of critical infrastructure, this can disrupt operations, leading to critical consequences. Protecting against ransomware involves robust cybersecurity measures, regular backups, and employee education on recognizing potential threats. A situation of digital hostage is assumed to be ransomware.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: Overwhelming the System
Visualize a traffic jam on the internet – that's what DoS and DDoS attacks do to critical infrastructure. By overwhelming servers with traffic, these assaults disrupt services, causing downtime and potential damage. The art of defending against such threats requires investing in resilient infrastructure and implementing measures to detect and mitigate these attacks promptly.
Insider Threats: The Trojan Horse Within
Not all threats come from external sources. Sometimes, organizations have some malicious actors who operate within them, posing an insider threat. Employees with access to critical infrastructure systems must undergo thorough vetting, and organizations should implement monitoring systems to detect any suspicious activities.
Outdated Software and Lack of Patching: Weak Links in the Chain
Imagine locking your front door but never updating it. The same principle applies to software and systems within critical infrastructure. Cybercriminals exploit vulnerabilities through outdated software. Regular updates and patching are essential to closing these digital doors to potential threats. Cybercriminals exploit vulnerabilities through outdated software.
Supply Chain Attacks: Infiltrating Through the Back Door
Critical infrastructure relies on a vast network of suppliers and vendors. A supply chain attack involves compromising a smaller, less secure link in this chain to gain access to the larger infrastructure. To mitigate this risk, organizations must thoroughly vet their suppliers, ensuring they meet robust cybersecurity standards.
Strategies for Critical Infrastructure Protection
Critical infrastructure protection involves protecting fundamental frameworks and resources. Strategies include cybersecurity measures, gamble evaluations, carrying out network protection, guaranteeing actual security, leading customary reviews, and cultivating joint effort among partners for a thorough methodology. Customary preparation and drills can upgrade readiness while staying updated on emerging threats are essential for adapting security measures.
Collaboration and Communication: Building Stronger Networks
Team effort is needed in critical infrastructure protection. Sharing information and effective responses to potential threats, private companies, government agencies, and communities must work together. Regular communication is crucial to identifying vulnerabilities and implementing preventative measures. In sharing information and effectively responding to potential threats, private companies, government agencies, and communities must work together.
Risk Assessment: Identifying Weak Links
Assuming your home has multiple doors, each representing a potential vulnerability. Examining those doors to acknowledge where a threat could enter is conducting a risk assessment. Identifying vulnerabilities in critical infrastructure allows for targeted efforts to strengthen those areas and reduce risks.
Investing in Technology
Technology can be our ally in protecting critical infrastructure. Defenses against cyber threats and physical attacks can be fortified by encouraging creative solutions such as cybersecurity measures and advanced monitoring systems. It's like upgrading your home security system to meet modern challenges.
Education and Training: Empowering the Frontlines
Just as we teach fire safety at home, giving proper education to those responsible for critical infrastructure is vital. Frequent training sessions ensure that personnel are well-prepared to handle emergencies, spot potential threats, and take immediate action. Knowledge is power in safeguarding our essential services.
Resilience Planning: Bouncing Back From Disruptions
There is no way we can always prevent disruptions, but we can always have a way to fight them back quickly. Creating strong strategies involves preparing for various scenarios, from natural disasters to cyberattacks. Even if power goes out, it’s like having a backup plan to keep your phone running.
Public Awareness: Everyone Plays a Role
Just as you lock your doors at home, critical infrastructure can be protected by everyone in society. Being vigilant of potential attacks and reporting suspicious activities can make a significant difference. It’s a collective safety having millions of eyes watching out for us.
Regulatory Measures: Setting Standards for Security
Imagine safety regulations being practiced in every society. Similarly, Standards are set through regulatory measures for critical infrastructure protection. These guidelines ensure that organizations practice the best procedures, reducing the risk of vulnerabilities and creating a baseline for security. Standards are set through regulatory measures for
International Cooperation: A Global Effort
Threats know no borders in our interconnected world. A united front can be created with the help of international cooperation against global challenges. By sharing information and resources across nations, we can strengthen our defenses collectively, just as neighbors might help each other in times of need. A united front can be created with the help of international cooperation against global challenges.
Conclusion
Critical infrastructure protection in the age of cyber threats is vital for public safety. Strong cybersecurity measures, persistent danger knowledge, and joint effort among government and private sectors are important to defending vital systems and mitigating potential risks. As technology develops, a proactive and versatile methodology is urgent to remain in front of rising digital dangers and ensure the resilience of critical infrastructure.
Opinions expressed by DZone contributors are their own.

Comments