A Comprehensive DevSecOps Guide: Key Considerations to Effectively Secure Your CI/CD Pipeline
Incorporating DevSecOps principles can result in advantages like early vulnerability identification, cost savings, and faster delivery times.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, The Modern DevOps Lifecycle: Shifting CI/CD and Application Architectures.
The era of digital transformation has brought about the need for faster, efficient, and more secure software development processes. Enter DevSecOps: a philosophy that integrates security practices into DevOps processes and aims to embed security into every stage of the development lifecycle — from the writing of code to application deployment in production. The incorporation of DevSecOps can lead to numerous benefits such as early identification of vulnerabilities, cost savings, and faster delivery times.
Shift-Left Principle
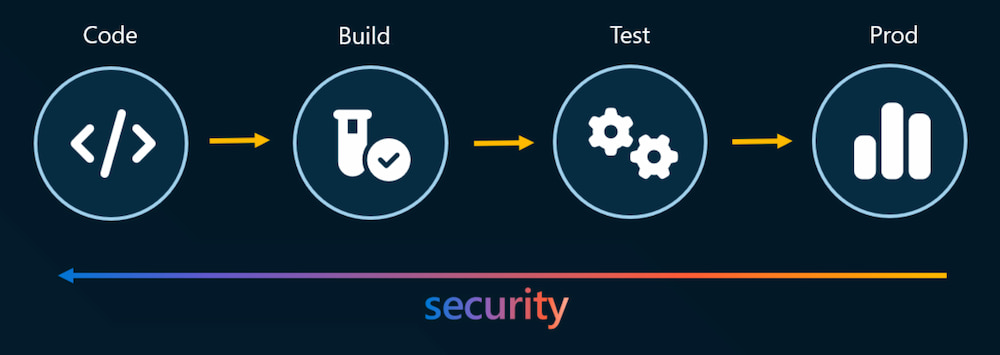
The term "shift left" refers to shifting the focus on security checks and controls toward the beginning, or "left," of the software development lifecycle (SDLC). Traditionally, security checks were performed toward the end, or "right," of the SDLC, often leading to vulnerabilities being detected late in the process, whilst the application is already deployed in production and such vulnerabilities are more expensive and time-consuming to fix.
The shift-left principle offers numerous benefits:
- Early detection of vulnerabilities – By integrating security checks earlier in the SDLC, vulnerabilities can be detected and addressed sooner. This reduces the risk of security breaches and ensures a more secure product.
- Reduced costs – Addressing security issues late in the development process can be costly. By shifting left, these issues are identified and repaired early, reducing the associated costs and resources required.
- Improved compliance – With security integrated from the outset, it's easier to ensure compliance with industry regulations and standards.
- Enhanced product quality – A product built with security in mind from the beginning is likely to be of higher quality with fewer bugs and vulnerabilities.
- Faster time to market – By reducing the time spent on fixing security issues at later stages, products can be delivered to the market faster.
This integration ensures that testing becomes an intrinsic part of the development organization's DNA, fostering a culture where software is meticulously crafted with quality considerations ingrained from the inception of the project.
Figure 1. Shifting security controls to the left
Key Considerations for DevSecOps Implementation
Implementing DevSecOps successfully requires careful consideration of key factors that contribute to a secure and efficient development pipeline. This integration of DevSecOps into the CI/CD pipeline allows for early detection of security issues, reducing the likelihood of vulnerabilities making their way into production while also allowing developers to quickly fix these issues and learn how to avoid reproducing them in the future.
Automated Security Testing Tools
Because applications come in different forms (e.g., mobile, web, thick client, containerized), you may need to set up different types of controls — and even different types of tooling to secure each component of your application. Let's review the main types of tests you should use.
Static Application Security Testing
Static application security testing (SAST) tools analyze an application's source code (the code written by your developers) for potential vulnerabilities without executing the program. By scanning the codebase during the development phase, SAST provides developers with insights into security flaws and coding errors. A good SAST tool can detect code smells as well as any bad practices that could lead to vulnerabilities such as SQL or path injection, buffer overflow, XSS, and input validation.
Software Composition Analysis
Software composition analysis (SCA) is critical for identifying and managing security risks associated with open-source components used in software development, generally coming from additional packages (e.g., NPM packets for JavaScript, NuGet for .NET, Maven, gems). Most developers load a package when they need one but never check if the package has a known vulnerability. An SCA tool will warn you when your application is using a vulnerable package as well as when a fix already exists but you are not using the fixed version of the dependency.
Dynamic Application Security Testing
Dynamic application security testing (DAST) tools assess applications in their running state, simulating real-world attacks to identify vulnerabilities. By incorporating DAST into the testing process, DevSecOps teams can uncover security weaknesses that may not be apparent during static analysis. A DAST tool will act like a fully automated penetration testing tool that will test for major known vulnerabilities (OWASP) and for a lot of other bad practices such as information leak/exposure.
Interactive Application Security Testing
Interactive application security testing (IAST) tooling is the combination of a DAST tool and a SAST tool because by allowing access to the source code ("gray boxing"), it will help the DAST perform better but also limit the number of false positives. IAST is super efficient but more challenging to set up because it tends to deeply test each application.
Container Scanner
Containers offer agility and scalability yet also introduce unique security challenges. For example, if your application is containerized, you must perform additional controls. Mainly, scanners will analyze your Dockerfile to check if the base image contains known vulnerabilities, and they will also look for bad practices such as running as root, using the "latest" tag, or exposing dangerous ports.
The following Dockerfile example contains at least three bad practices, and it may contain a vulnerability in the Node.js base image:
FROM node:latest
WORKDIR /usr/src/app
COPY package*.json ./
RUN npm install
COPY . .
EXPOSE 3000 22
HEALTHCHECK CMD curl --fail http://localhost:3000 || exit 1
CMD ["node","app.js"]Infrastructure-as-Code Scanner
Infrastructure as Code (IaC) allows organizations to manage and provision infrastructure through code, bringing the benefits of version control and automation to the infrastructure layer. IaC scanning ensures that infrastructure code undergoes rigorous security controls, such as validating configurations, following best practices, scanning for security misconfigurations, and enforcing security policies throughout the infrastructure deployment process.
Secrets Scanner
A secret (e.g., API key, password, connection string for a database) should be stored in the source code (hard-coded), or in a configuration file stored within the code repository, because a hacker gaining access to the code could then access production and/or other critical environments. Secrets scanners can detect 150+ types of secrets that developers could leave in the code, and once a secret has been stored in the code (commit), it should be considered "compromised" and revoked immediately.
Criteria to select the right third-party product:
- SAST
- Number of languages supported, ideally one tool for all code
- Accuracy of detection
- Dashboard to customize analysis with sets of rules
- SCA
- Number of packages recognized
- Automated remediation (can create a pull-request with the updated package)
- DAST
- Should be able to cover APIs as well as GUI apps
- Cover more than just OWASP
- IAST
- Capable of covering rich applications (e.g., with microservices)
- Offer remediation/advice to fix detected issues
- Container Scanner
- Up-to-date CVE database for the base image
- Can lint a Dockerfile and check best practices
- IaC Scanner
- Find issues in template files
- Supports the format of your cloud provider (e.g., ARM + Bicep for Azure, CloudFormation for AWS, Deployment Manager for Google Cloud) or Terraform if you are using it
- Secret scanner
- The number of credentials types recognized
- A dashboard that allows security teams to monitor detected secrets and ensure they have been revoked
- Custom rules to prevent false positives and/or add new formats
Establishing Security Gates in CI/CD Pipeline
Analysis tools are a good start, but they are useless if they are not part of a global governance. This governance must be built on well-defined security policies and on mandatory controls to ensure that the organization's data and systems are consistently protected against potential threats and vulnerabilities.
Defining and Enforcing Security Policies
Effective security in a CI/CD pipeline begins with the definition of clear and project-specific security policies. These policies should be tailored to the unique requirements and risks associated with each project. Whether it's compliance standards, data protection regulations, or industry-specific security measures (e.g., PCI DSS, HDS, FedRamp), organizations need to define and enforce policies that align with their security objectives.
Once security policies are defined, automation plays a crucial role in their enforcement. Automated tools can scan code, infrastructure configurations, and deployment artifacts to ensure compliance with established security policies. This automation not only accelerates the security validation process but also reduces the likelihood of human error, ensuring consistent and reliable enforcement.
Integration of Security Gates
In the DevSecOps paradigm, the integration of security gates within the CI/CD pipeline is pivotal to ensuring that security measures are an inherent part of the software development lifecycle. If you set up security scans or controls that users can bypass, those methods become totally useless — you want them to become mandatory.
Security gates act as checkpoints throughout the CI/CD pipeline, ensuring that each stage adheres to predefined security standards. By integrating automated security checks at key points, such as code commits, build processes, and deployment stages, organizations can identify and address security issues in a systematic and timely manner. These gated controls can be in different forms:
- Automated security controls (e.g., SAST, SCA, CredScan)
- Manual approval (e.g., code review)
- Manual testing (e.g., pen testing by specialized teams)
- Performance testing
- Quality (e.g., a query that monitors the number of defects opened in your quality tracking tool)
Figure 2. Standard DevSecOps pipeline with gated security controls

Continuous Monitoring and Feedback
In the fast-paced world of software development, the importance of real-time monitoring for security and quick fixing cannot be overstated because even with gated controls, vulnerabilities can be found after an application has been deployed in production.
Real-Time Monitoring for Security
Real-time monitoring allows teams to proactively detect and respond to security threats as they emerge. By leveraging automated tools and advanced analytics, organizations can continuously monitor their applications, infrastructure, and networks for potential vulnerabilities or suspicious activities. This proactive approach not only enhances security but also minimizes the risk of security breaches and data compromises. It gives the ability to gain comprehensive visibility across the entire technology stack. DevSecOps teams can track and analyze security metrics at every layer, from application code to production environments. This visibility enables quick identification of security gaps and facilitates the implementation of targeted remediation measures, ensuring a robust defense against evolving cyber threats.
Addressing Security Findings and Adapting Processes
Identifying security findings is only the first step; effective DevSecOps requires a proactive approach to address and remediate these issues promptly. When security findings are identified, cross-functional teams work together to assess the impact, prioritize remediation tasks, and implement corrective measures. This collaborative effort ensures that security is everyone's responsibility and not just confined to a specific silo within the organization. Adaptability is a core tenet of DevSecOps. Organizations must foster a culture of continuous learning, where security teams regularly update their knowledge, processes, and tools based on evolving threats and industry best practices. This adaptive mindset ensures that security measures remain effective in the face of new challenges, and that the DevSecOps pipeline is continually refined for optimal security outcomes.
Conclusion
As software development processes continue to evolve, the need for robust security measures within the CI/CD pipeline becomes more critical. Embracing a DevSecOps approach can help organizations create a secure, efficient, and reliable CI/CD pipeline. By prioritizing security from the get-go and implementing security gates, organizations can save resources, reduce risk, and ultimately, deliver better, safer products to the market.
Go and make security the foundation of your products!
This is an excerpt from DZone's 2024 Trend Report, The Modern DevOps Lifecycle: Shifting CI/CD and Application Architectures.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments