Challenges and Checklists While Migrating COTS Application to Cloud
This blog discusses the critical challenges and presents a checklist approach to use before one starts the COTS migration.
Join the DZone community and get the full member experience.
Join For FreeThe world is moving rapidly towards digitization with a cloud-native approach. The first step towards this journey is migrating the applications to the cloud, preferably with re-host and re-platform disposition. While custom applications are comparatively easier to migrate, a bigger challenge, analysis, and decision arises w.r.t to COTS (commercial off-the-shelf) applications. This blog discusses critical challenges and a checklist approach before one starts COTS migration. The term ‘modernization’ used here refers to replacing and enabling the legacy product with a cloud-compatible version.
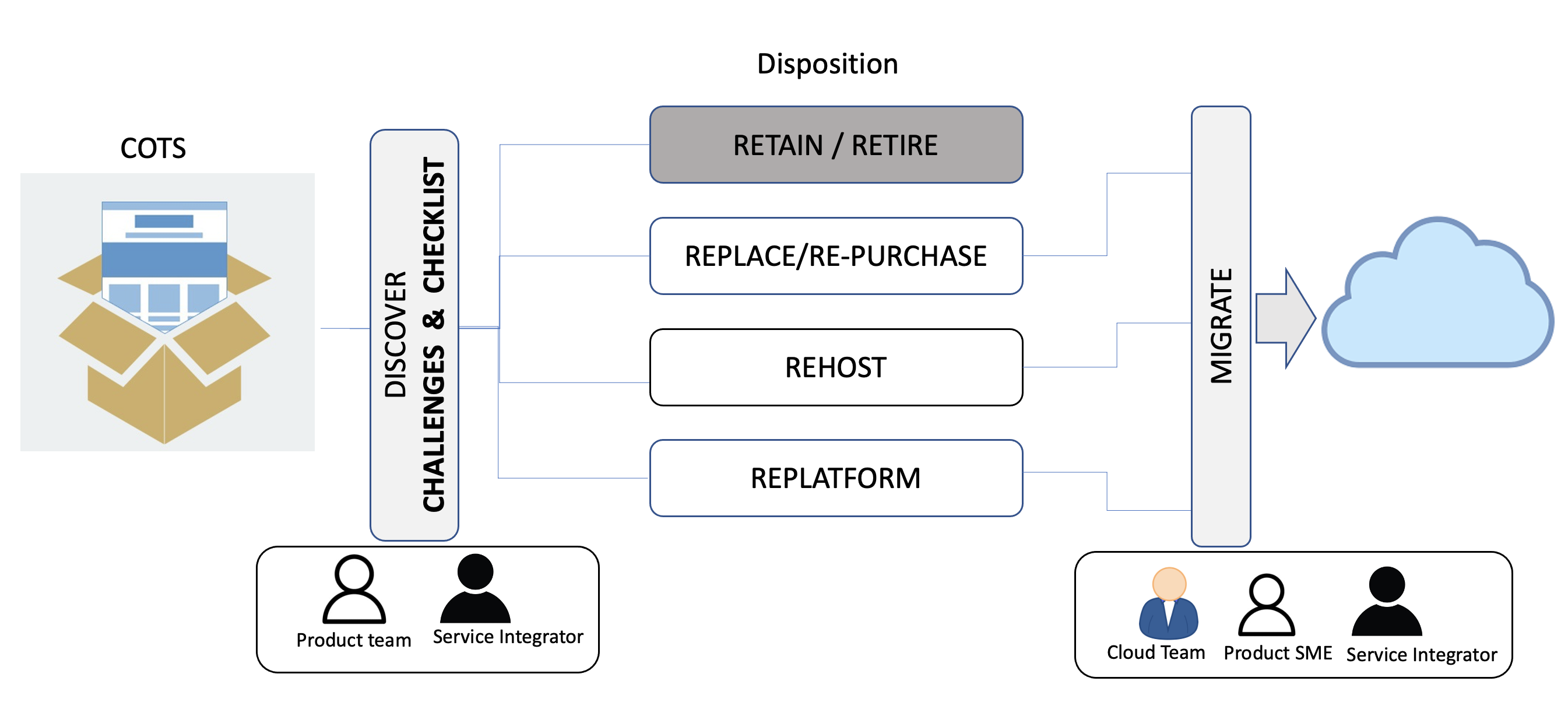
Challenges and Checklists
- Roadmap to retain/replace/retire the Product —Answers to the following queries may lead to retain/replace/retire the product and potential application consolidation and rationalization (to be run as a separate enterprise program, outside migration)
- Are business/end users using this product frequently as a business-critical application?
- Is this product/application being used locally or globally (the same app/product is set up in different regions/countries and being used almost the same way)?
- Can the functionalities be addressed by another (existing) application with enhanced customization?
- Note: the above queries are best answered by the client's business team and the client's industry domain SME.
- Version Compatibility — Verify the Product Compatibility matrix and documentation w.r.t. technology stack, compliance with the cloud platform, and ensure those can be supported in the target cloud architecture. Each cloud follows a set of security standards and policies supported level of software/technologies. Similarly, the cloud also should support various regulatory compliance w.r.t. client’s industry domain. In general, the OS, middleware, etc., are supported up to N-1 level where N is the latest GA (general availability) release of system/software component.
- Vendor Support of Product — Check if the vendor has a roadmap for supporting the on-prem hosted product version. It also needs to be verified if the existing system requirements of the product are supported in the target cloud. This may lead to an upgrade before migration. Some vendors, as part of digital transformation, take multi-tenant and software-as-a-service approaches and may force customers to adopt the same for the product.
- SaaS-Adoption — Does the product has SaaS, and if so, is that acceptable to the client w.r.t Data Privacy and security? Also, one should do a cost evaluation compared to a hosted solution. Verify that SaaS offering support required integration with existing interfaces as well as user accessibility (authentication/authorization) and security.
- System Integration Landscape — The current product may use an integration style/protocol/port with internal/external systems. As the product is now planned to be on the cloud, the same protocol /port may not be supported as per security standards and may need a separate cloud-specific port. Sometimes, this may lead to a re-design of the product itself which is rare to achieve within the timeline. Most of the time, in this scenario, exceptional approval has been achieved from CSO (chief security office) for existing ports to be allowed over the cloud.
- Resource Optimization — For business-critical applications, it’s an important architecture decision to have a cost-effective approach towards scalability, availability, improved fault tolerance, and faster deployment. Moving to container will help in all these aspects; however, the COTS product image needs to be ‘lightweight’ and secured. So, one needs to check if the product can be hosted on a container and if has a secure image registered in an official registry approved by the product vendor. Migrating to a container-based approach require extensive integration effort and security/penetration testing.
- File-Based Integration — The existing and target configuration of file share depends on the protocol supported (SMB, NFS, DFS, etc.) and whether both systems (publisher and consumer of files) within the same network domain. In target, the domain of participating systems will be different networks by the underlying hypervisor. This also needs specific ports of communication to be opened between the cloud and on-prem.
- Migration Path — Any product migration can choose one of two paths —1) Migrate the new product to the cloud directly, 2) Upgrade the product on-prem and then migrate to the cloud. The first option poses a higher risk in terms of performance and integration as the newer/upgraded version is likely to have different interfacing, port, and technology. The initial upgrade, system, integration, required testing, and compatibility must be done on-premise with all ecosystems and get business approval. This will drastically reduce product testing and integration effort while migrating to the cloud.
- Implementation RACI — Once the target version of the product is decided for migration, it becomes critical to get the right SME and establish a RACI (Responsible, Accountable, Accountable, Informed) matrix. While setting up the infrastructure and required network can be done by SI (service integrator) and the cloud team, the installation, upgrade, product installation configuration, and integration need to be carried out by the product/COTS SME, who should be from the product vendor team. Generally, the SME has to be engaged from the initial conversation of the upgrade-migrate path and continue to be part of core implementation team. The SI, through the client, must raise a risk of SME availability and timeline and mitigate by the product team’s confirmation on this. For SaaS adoption of the product, the product SME must be included for integration as well as security architecture/design.
- Users Access Mechanism — The legacy version of many COTS products requires an older way of accessing the product — through additional security software like Citrix, F5, Array Network, FortiClients, etc. (a separate URL is used to access the application/product). This needs users' laptops/devices to install and maintain separate software, configuration, and distribution whenever required. We should look for adopting the modern version of the COTS now support https/WebAPI, which is secure and does not require an additional layer.
- Observability and Insight — As we take an application to the cloud, it is critical that the application generates the right level of traces, logs, and metrics so that cloud-native monitoring tools can capture and use for alerting and incident management. The product should be configurable to generate the right data, which will help building predictive algorithms (using AI/ML). This can provide actionable insight observability and will help taking proactive action to reduce downtime and ensure system health and uptime. So, it is important to adopt the suitable (easily configurable to send logs, set traces, levels, etc.) product version for migration/modernization target architecture.
Opinions expressed by DZone contributors are their own.

Comments