Application Security Checklist
Evaluating security controls with OWASP’s top 10 security tests
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2021 Application Security Trend Report.
In today’s technology landscape, organizations are supported by web applications that act as essential enablers to streamlining operations. While these applications enable automation, wider collaboration, and ease of sharing data, they also act as vectors that are prone to malicious attacks. Besides this, as modern applications rely on loosely connected components and services in constant communication, security becomes a complex, time-consuming challenge.
The Online Web Application Security Project (OWASP) Foundation seeks to help organizations develop secure applications by issuing guidelines on available tools, techniques, and documentation. The Application Security Checklist is one of OWASP’s repositories that offers guidance to assess, identify, and remediate web security issues. This article delves into various vulnerabilities of web applications and outlines OWASP’s guidance on testing to mitigate such vulnerabilities.
Selecting the Right Application Security Tests
OWASP’s application security testing checklist is an essential guide to promote repeatable and methodological testing for dynamic apps. The following section delves into the workflow and specific activities involved in web app security testing.
Application Testing Workflow
A typical application security testing strategy is based on a collection of several common steps:
- Gathering comprehensive information of the application and its platform to assess related technologies and vulnerabilities
- Exploiting the system to test the severity of discovered vulnerabilities
- Ranking vulnerabilities based on the outcome of exploits and risks
- Using vulnerability risk data to re-assess application security posture
- Successful exploitations to be escalated for required mitigation
Figure 1: A typical OWASP application security workflow
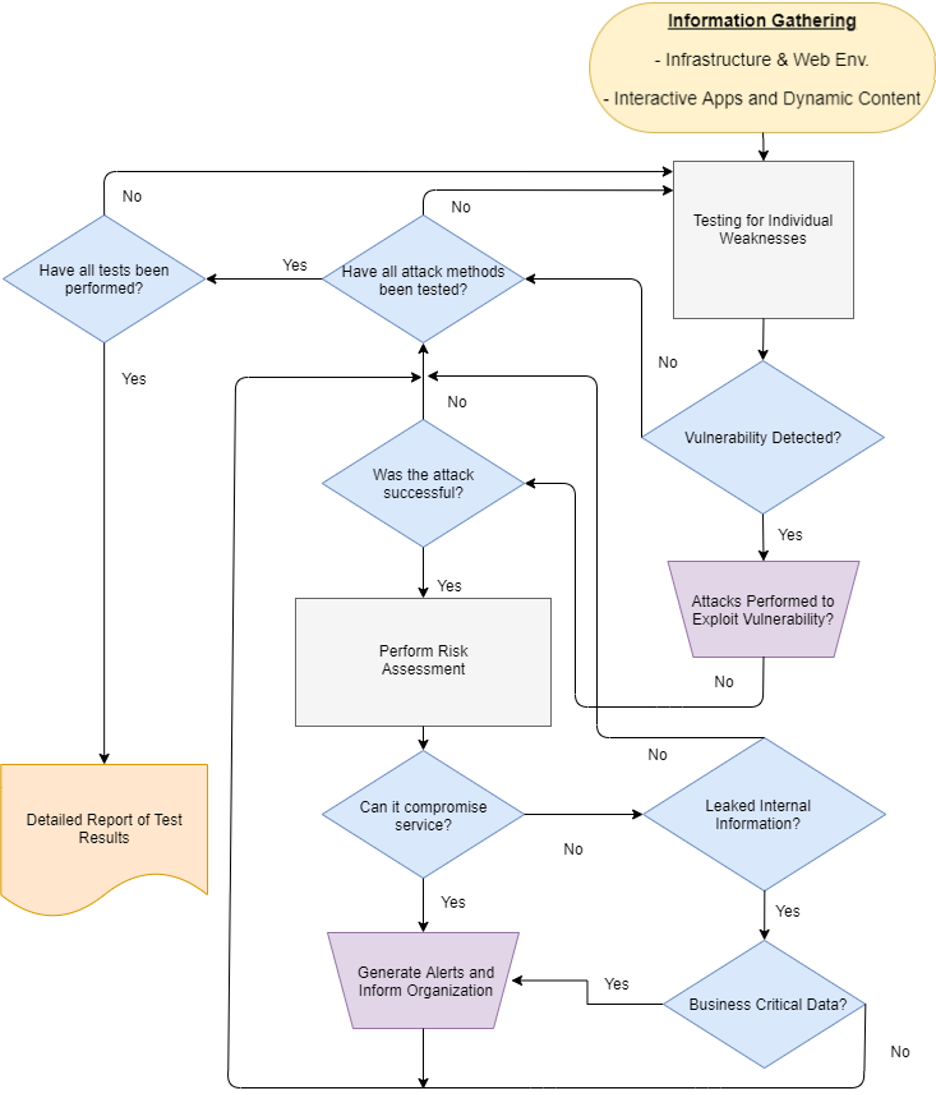
This is an excerpt from DZone's 2021 Application Security Trend Report.
For more:
Read the Report
Application Security Testing Checklist
The OWASP Application Security Testing checklist helps achieve an iterative and systematic approach of evaluating existing security controls alongside active analysis of vulnerabilities. Below is a list of key processes and items to be reviewed when verifying the effectiveness of application security controls:
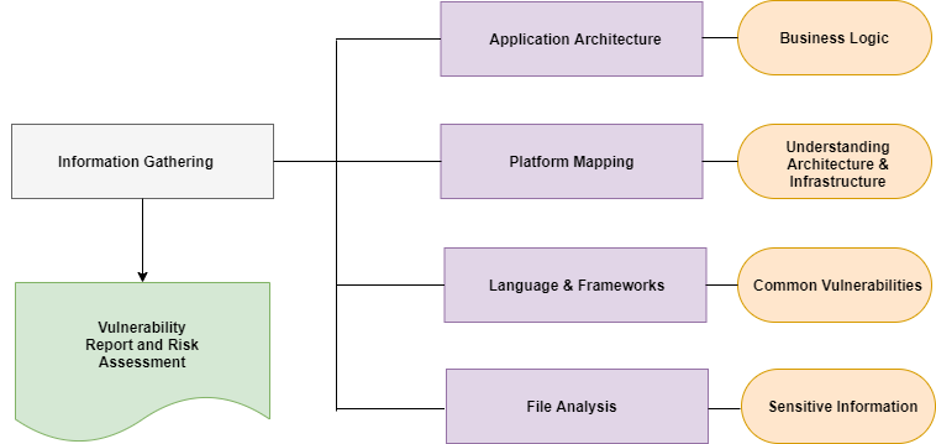
1. Information Gathering
A successful web application security strategy fundamentally begins with an understanding of the interactions between the web server, users, and applications. While application deployment platforms vary, key vulnerabilities in infrastructure configuration act as a common weak link for threat actors to initiate an attack.
Some key application security information gathering activities include:
▢ Manual site exploration
▢ Crawling for hidden content
▢ Checking for files that store and expose content
▢ Scanning caches on search engines of public sites
▢ Web application fingerprinting
▢ Identification of user roles
▢ Identification of application entry points
▢ Identifying related applications
▢ Identifying ports and hostnames
▢ Identifying third-party hosted content
Figure 2: The OWASP Information Gathering Model
2. Configuration Deployment and Management
A web server ecosystem is intrinsically complex with highly connected, heterogeneous services and components working together. Reviewing and managing the configuration of the server is, as a result, a very crucial aspect for maintaining robust security across multiple layers of an application.
Securing various configuration items of an application involves:
▢ Checking for commonly used URLs
▢ Testing network infrastructure configuration
▢ Enumerating administrator interfaces
▢ Checking supported HTTP methods and Cross-Site Tracing (XST)
▢ Reviewing old unreferenced and backup files for sensitive information
▢ Testing for Strict-Transport-Security
▢ Testing file permissions
▢ Testing for non-production data in live environments, and production data in dev/test environments
▢ Testing for content security
▢ Evaluating subdomain takeover
▢ Analyzing client-side code for sensitive data
3. Identity and Access Management (IAM)
Securing organizational data involves defining appropriate access privileges and roles of the application’s users/administrators. Each individual (user, app, or device) gets a single digital identity (also referred as tokens) that can be monitored, maintained, and modified throughout their data access sessions. Assessing the robustness of IAM for application security typically involves testing the following:
▢ Role definitions
▢ User registration processes
▢ Account provisioning processes
▢ Account enumeration and guessable user accounts
▢ Weak or unenforced username policies
4. Authentication Testing
Authentication enforces application security by enabling the web server to verify that a network entity is who they claim to be. As attackers tend to develop unique techniques to bypass authentication schemes, not every authentication method guarantees effective security controls, and requires a continuous assessment process. Assessing authentication security involves the regular testing of:
▢ Default credentials
▢ Vulnerabilities of the “Remember Password” feature
▢ Browser cache vulnerabilities
▢ Weak password policies
▢ Credentials transported over an unencrypted channel
Testing for sensitive information sent via unencrypted channels involves checking whether credentials are encrypted or encoded, and sent as HTTP headers using a curl command of the form:
$ curl -kis http://darwin.com/restricted/
HTTP/1.1 401 Authorization Required
Date: Fri, 28 Aug 2021 00:00:00 GMT
WWW-Authenticate: Basic realm="Restricted Area"
Accept-Ranges: bytes Vary:
Accept-Encoding Content-Length: 162
Content-Type: text/html
<html><head><title>401 Authorization Required</title></head>
<body bgcolor=white> <h1>401 Authorization Required</h1> Invalid login credentials!
</body></html>5. Session Management
Once a user is authenticated, their interaction with the server is managed within a session. Improperly managed sessions open doors for attackers to compromise access mechanisms by assuming those to be identities of legitimate users. More so, such compromised accesses are often taken advantage of by attack vectors that escalate privileges and penetrate deeper into the system. To avoid vulnerabilities within a session, the following processes are recommended to be tested as a best practice:
▢ Analyzing session tokens for cookie flags
▢ Checking session cookie durations
▢ Examining termination after a relative timeout
▢ Testing for the possibility of single-user multiple sessions
▢ Testing for consistent session management
▢ Testing cookies for randomness
6. Cryptography
Cryptography ensures the secure exchange of information by using algorithms that transform human-readable data into a ciphertext-encrypted output. While doing so, the process establishes trust between the web server and network entities using security keys, making it an important mechanism for maintaining application security. Testing cryptography for maintaining application security involves:
▢ Checking for sensitive, unencrypted data
▢ Testing for the usage of wrong algorithms
▢ Testing algorithm strength
▢ Analyzing functions for randomness
▢ Checking for the appropriate usage of salting
7. Client-Side Testing
Since full-blown attacks carried out on the perimeter are usually challenged by effective organizational security efforts, threat actors tend to favor smaller, repeated attacks to gain initial access to web servers. To mitigate such approaches, client-side or internal testing involves examining vulnerabilities on applications installed on an endpoint that communicates with the web server. Client-side testing reveals weak points that can be exploited using the access rights of authorized users, and includes testing the following:
▢ Cross-Site Scripting (XSS)
▢ JavaScript execution
▢ Client-side URL redirects
▢ Cross-Site Flashing (XSF)
▢ Web sockets and web messaging
▢ Cross-Site Script Inclusion (XSSI)
8. Error Handling
OWASP encourages developers to include error handling mechanisms and messages that enable them to fix issues of user access. Improper error handling can expose sensitive information such as database dumps, error codes, and stack traces that can be exploited by attack vectors to gain access.
Testing error handling mechanisms can be done through:
▢ Testing server behavior for resource requests that are unavailable
▢ Testing HTTP RFC for breaking ambush requests
▢ Observing server behavior when requested for files/folders that do not exist
▢ Identifying the application’s data entry points
▢ Listing and understanding the services configured to respond with error messages
9. Data Validation
Any information entering a web server’s network edge should be tested and verified to ensure that it is in an acceptable format. Data validation testing includes:
▢ Examining special files
▢ Testing file upload validation mechanisms
▢ Testing for rich user content validation
▢ Assessing content security policy
▢ Evaluating the list of regular expressions
10. Business Logic
Hackers mostly leverage an application’s original programmed flow to orchestrate breaches and penetration attacks. As a result, it is recommended to assess the business and application’s configuration to identify vulnerabilities in code or business logic that could be used for potential exploits.
Business logic testing includes:
▢ Testing for feature misuse
▢ Testing for non-repudiation
▢ Testing trust relationships
▢ Testing data integrity
▢ Testing for duty segregation
Conclusion
While administering robust security is of utmost importance, OWASP updates its checklist based on the changing security landscape and mistakes of organizations that caused vulnerabilities. The OWASP Top 10 Application Testing Checklist offers a repository of potential vulnerabilities for developers to help enforce security across all layers of a workflow’s pipeline. The project includes multiple resources and activities that aid organizations to ensure web applications and their underlying components don’t serve as a gateway for malicious actors. The checklist also helps teams formalize their web application security efforts, while minimizing the scope of risk in case of an attack.
| Sudip Sengupta, Technical Writer at Javelynn @ssengupta3 on DZone | @ssengupta3 on LinkedIn | www.javelynn.com Sudip Sengupta is a TOGAF Certified Solutions Architect with more than 15 years of experience working for global majors such as CSC, Hewlett Packard Enterprise, and DXC Technology. Sudip now works as a full-time tech writer, focusing on cloud, DevOps, SaaS, and cybersecurity. When not writing or reading, he’s likely on the squash court or playing chess. |
Opinions expressed by DZone contributors are their own.

Comments