Adopting DevSecOps in the Cloud-Native Playground
Security has become the utmost priority in the cloud-native world. Discover some pointers on how to tackle it and win the DevSecOps game.
Join the DZone community and get the full member experience.
Join For FreeEmbracing DevOps is essential, but keeping the software delivery and deployment pipeline safe has become more critical than ever. While attackers are keen on getting into your Docker containers or Kubernetes clusters, it is highly recommended to secure your images, pods, and clusters, which poses a nightmare to the attackers. Securing your artifacts, deployment workloads, and production environments is what is taking the limelight today. While we have many tools to get the job done, it is vital to understand DevSecOps and its related factors in the realm of cloud-native computing.
DevSecOps has become a mass movement today. Let us deep dive and see what makes it so important.
What Is DevSecOps?
DevSecOps addresses software development security with a mindset that everyone is responsible for security.
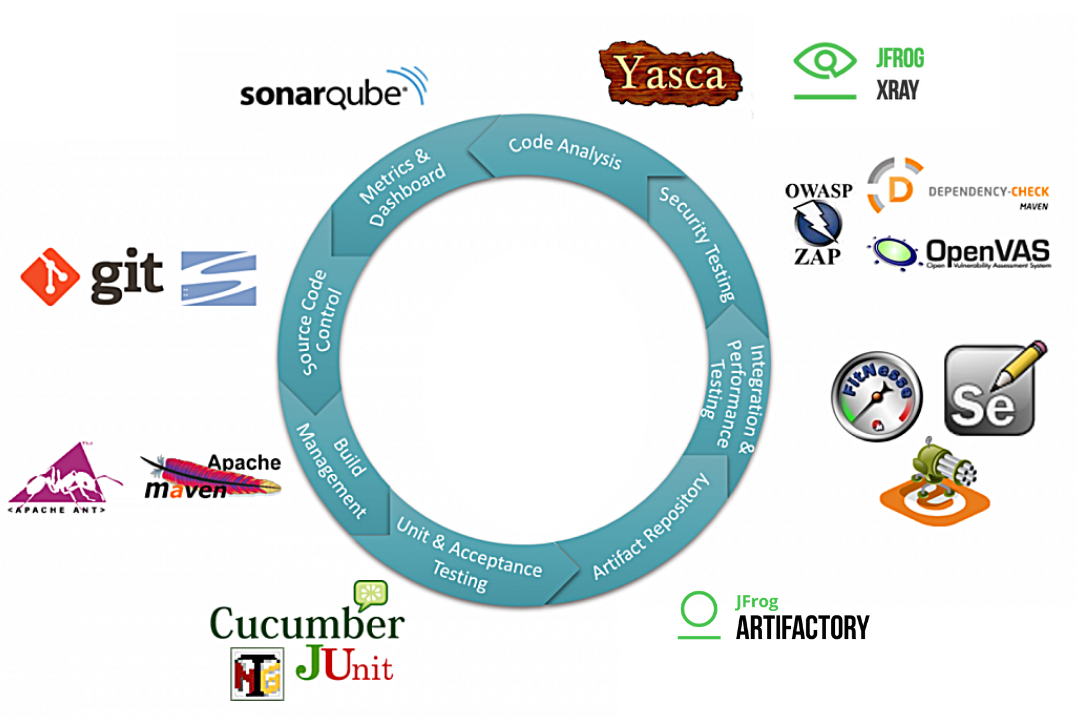
DevSecOps is a culture and an evolution where security is given the utmost priority in the software development life cycle. Security is everyone's responsibility, and the inspection is done at each stage of the development cycle; implementing a series of inspecting, scanning, and reviewing the code among developers at predetermined checkpoints to immediately tackle any identified bugs. One of the most challenging parts of the transition from DevOps to DevSecOps is building more open and communicative teams.
Why DevSecOps?
Using DevSecOps, security becomes an indispensable piece during the plan, code, build, test, deployment, and production stages. DevSecOps makes continuous testing a default task for developers and security professionals to deliver features faster to the market.
In many organizations, most dev, ops, or DevOps teams see security or security teams as a hurdle in getting things done faster and delaying features. In traditional DevOps, the security aspect was missing, and that is why the term DevSecOps was introduced not as a buzzword, but to stress the priority of security in DevOps.
The Importance of DevSecOps
Let’s take Uber's security breach in 2017, where the personal details and information of 57 million customers and over 600,000 drivers were exposed. Uber then had to pay $100,000 to hackers to request them to delete the breached data. This breach resulted because engineers failed to secure and update the credentials they were using on a GitHub site.
Similarly, in 2018, Tesla’s Cloud was hijacked and utilized to mine cryptocurrency, abusing a vulnerability in the company's Kubernetes cluster. A significant amount of FedEx data was also exposed, affecting 119,000 individuals.
Logz.io's annual DevOps Pulse 2020 survey identified that with over 1,000 respondents, Only 3% of respondents indicated their position as “DevSecOps,” giving us a hint about the rarity of DevSecOps adoption in the industry.
All these facts suggest the importance of security (DevSecOps adoption) in organizations.
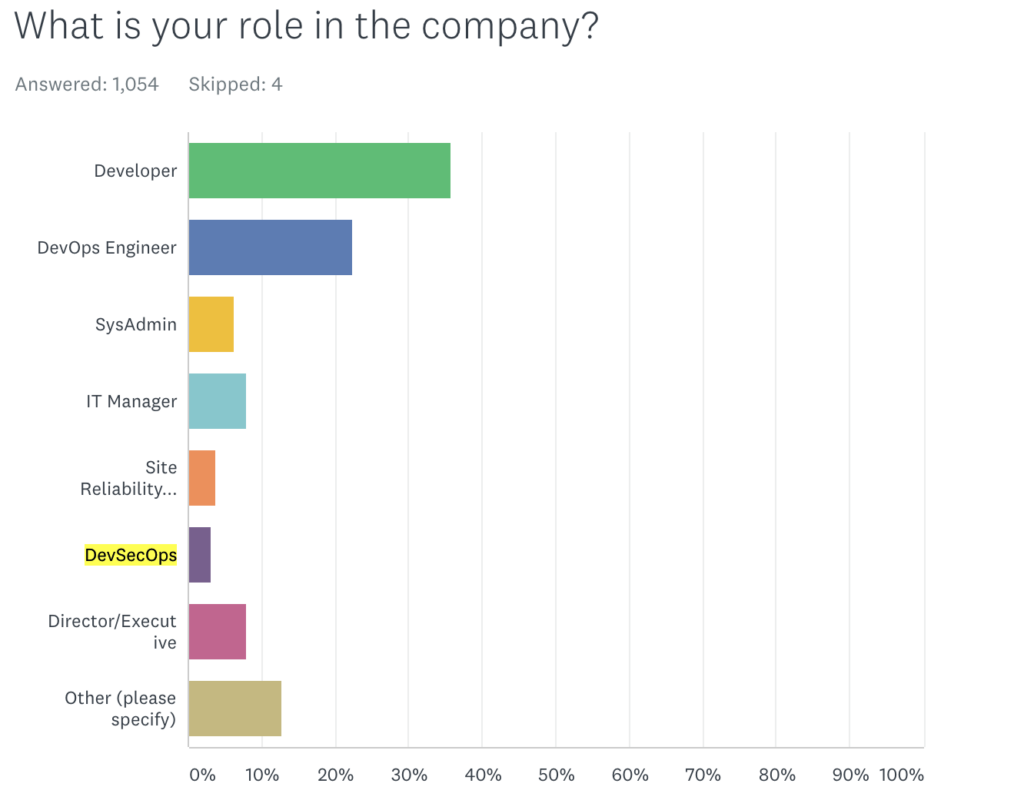
Image source: Logz.io
DevSecOps Best Practices for Cloud Native
Shift Left Approach
Shifting security left helps organizations secure each stage of the development life cycle. This refers to starting testing earlier in the SDLC. The goal here is to enhance quality, cut down long test cycles, and reduce the likelihood of unpleasant surprises at the end of the development cycle or in production.
Threat Modeling Mechanism
It is very essential to implement a threat modeling mechanism in the DevOps workflow since it helps developers and security professionals to view software from an attacker's perspective. It makes developers more careful while writing code by following the best code writing and review practices. Threat assessment or threat modeling will also help identify the potential vulnerabilities in the system design and architecture, which might sometimes have been missed before. Thus, threat modeling acts as a crucial part of successful security integration in software development.
Developers Training
Training developers on the importance of security is one of the best practices. Each developer who writes code, tests, and deploys must understand that security is his/her job as well. Training the developers on security best practices, how to embed security, check for vulnerabilities, and use of security tools will definitely improve the overall knowledge of security and its importance within the organization.
Security Vulnerability Tools
A vulnerability is considered a flaw in the software/code. This flaw must be tracked as soon as it appears in the SDLC. Security vulnerabilities might be present in the code, application dependencies, external libraries, licenses used, or operating system (OS) packages. Famous security vulnerability tools such as JFrog Xray can help the development team find and address the bugs as early as possible in the development pipeline.
Bug Bounties
Bug bounty programs and rewards motivate external and as well as internal bug-finding security experts to experiment with the platform, analyze, think outside the box like an attacker/hacker, and report any major bugs and security flaws found in the platform.
Security as Code
Security as Code outlines the next revolution in DevOps, where security is embedded into the development processes.
It highlights the importance of implementing security in the early stage of its development. With security as code, developers will be able to find the parts in the code that can be identified as vulnerable ahead of time and add security checkpoints/measures to tackle such irregularities.
DevSecOps Tools
When we talk about DevSecOps, the software development cycle involves multiple checkpoints to identify bugs and any other vulnerabilities and resolve them so that the application works as designed. The aim is to deploy software with quality and confidence, and this is achieved by using various tools at different stages, as shown in the following diagram.
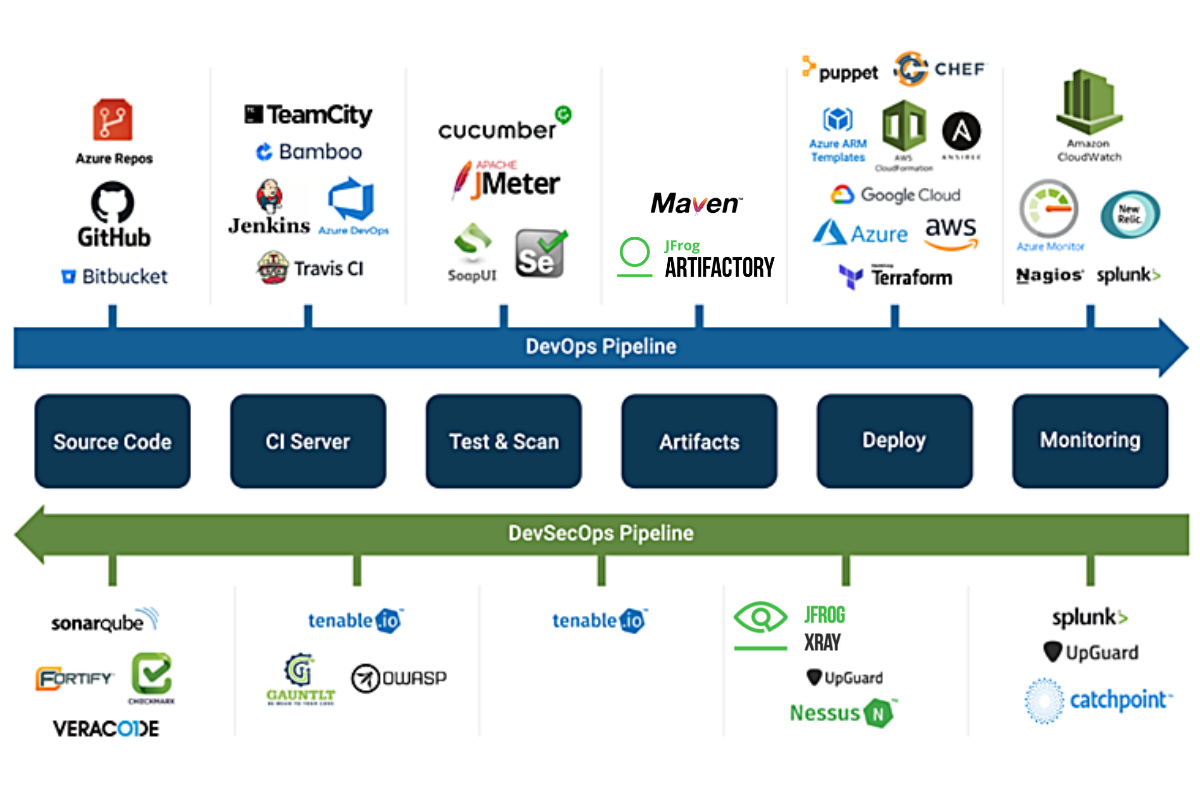
Image credits: CatchPoint
Let's now walk through these DevSecOps tools depicted in the above diagram. These tools help organizations/teams achieve security in their application and also keep the codebase secure.
SonarQube
SonarQube is a SAST (Static Application Security Testing) tool. This tool works in the early phases of SDLC by scanning the source code, binary code, and bytecode for vulnerability. It can also identify problematic coding patterns that are not compliant with best practices.
Tenable.io
Tenable cloud security can help your organization to take the cloud solution to the next level. Whether you are lifting and shifting apps and services to the cloud or building a new cloud-native app, Tenable is the go-to solution for your organizational cloud security needs.
OWasp
OWasp is a SCA (Software Composition Analysis) tool whose job is to detect publicly known vulnerabilities within a project or its dependencies.
JFrog
JFrog Artifactory is a tool used for controlling and monitoring binary flows right from the build phase to the production phase. It powers the entire software supply chain throughout the binary lifecycle management process. JFrog Artifactory is available for all the major cloud platforms like GCP, Microsoft Azure, and AWS.
UpGuard
UpGuard is a platform that allows the organization to manage cybersecurity risks. It offers tools and features for the DevOps team to analyze their current cyber risk score. The platform comes with the following additional features:
- Threat intelligence
- Data leak detection
- Reviewing third-party apps
Splunk
Splunk is a database system used for business analytics, compliance, and security. It uses an AI-driven analytics tool to automatically detect vulnerabilities in the system. Splunk can also correlate data from other databases, networks, and sensors.
Fortify
Fortify is also a SAST (Static Application Secure Testing) tool that helps to build secure applications faster. It detects the security issues in the early phases of the development lifecycle and fixes them at the speed of DevOps.
Veracode
Veracode is a cloud-based software application security platform that can scan hundreds of applications and web APIs simultaneously. It uses an advanced AI algorithm to scan for vulnerabilities across a large dataset of code. The tool performs both static and dynamic code evaluation. Static evaluation helps detect vulnerabilities in the code before deployment. it can even find vulnerabilities in the code that contain malicious code, cross-scripting attacks (XSS), and SQL injections.
More on DevSecOps Tools
Organizations can choose to use the security tools that best work for their needs. The security tools used as part of the DevSecOps pipeline become critical for detecting vulnerabilities in the application. Nevertheless, monitoring is also considered an integral part of this process because it lets us analyze and evaluate security vulnerabilities from the end user’s viewpoint.
DevSecOps Pipeline
While DevOps focuses on speed and agility, DevSecOps adds a layer of security throughout the software development life cycle. Without keeping security at the end of the DevOps pipeline, this pipeline (DevSecOps pipeline) adds security as an ongoing process. It is done by integrating security checkpoints, controls, policies, tools, and techniques at the start of the DevOps pipeline till the end. These will facilitate automated security controls at each stage of the software delivery pipeline.
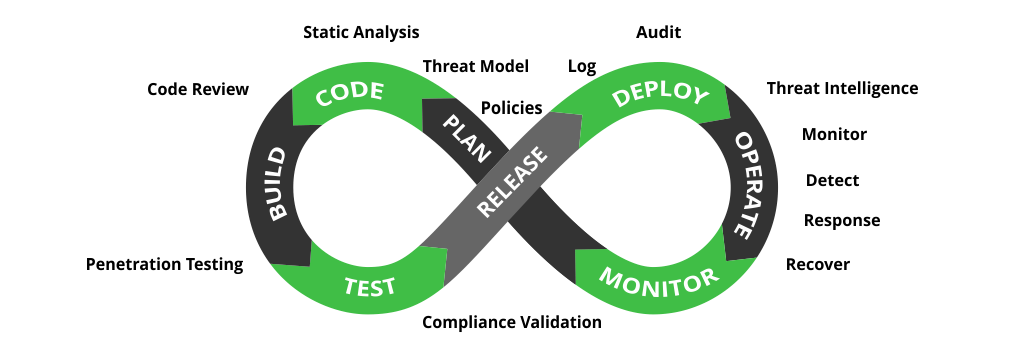
Image credits: JFrog
In the swampUP conference keynote "The Divine and Felonious Nature of Cyber Security," John Willis shared some valuable DevSecOps best practices, including:
- Treat security issues the same as software issues.
- Adopt a “security as code” approach to enable the automation of security.
- Build security controls and vulnerability detection into CI/CD pipelines.
- Automate security testing as part of the build process.
- Proactively monitor the security of production deployments.
Real-World Examples
DevSecOps Adoption at Fitch
Adopting DevSecOps in a 100-year-old company like Fitch was not easy.
Initially, when the services started slowly growing, they didn’t understand what was going on in the production. They started noticing so many outages; that there was a lack of traceability and inefficient collaboration across the pipeline. One incident used to cause a chaotic situation, and nobody was aware of what and how to handle such an incident.
The standard procedure followed was to simply reboot the database service.
The development teams at Fitch had poor knowledge of security and hence affected the collaboration and individual responsibility. Then, they decided to push the security defects to the top of the priority list.
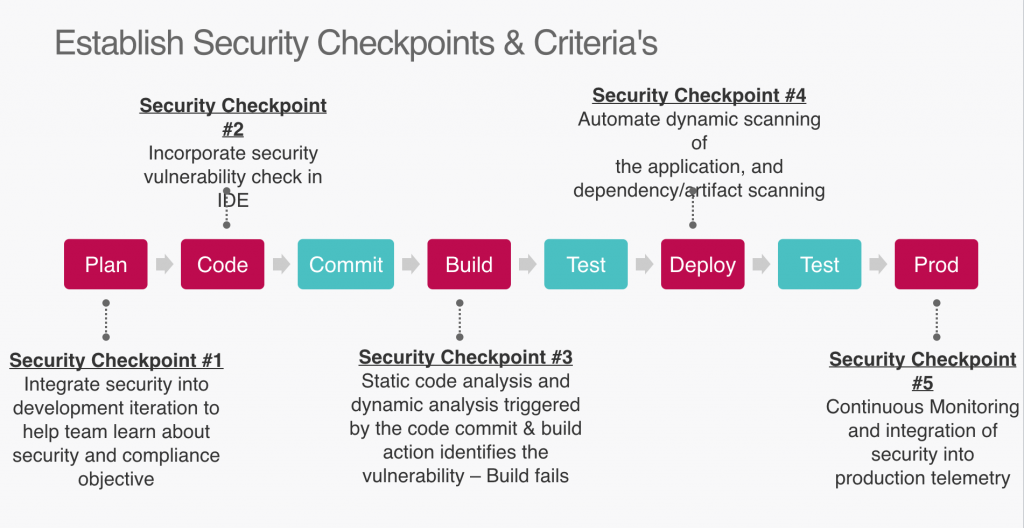
Image source: TheNewStack
The management team then hired security experts and made them join each development team to break down the silos and make security the utmost priority. They established security checkpoints and criteria at each stage of the DevOps pipeline.
Next, they decided on the best-in-breed security tools and used them in the SDLC.
DevSecOps Adoption at the Department of Defense
The DoD has created a DevSecOps reference design to address the security aspects of their software development pipeline. According to them, releases that took three to eight months can now be achieved within a week.
The DevSecOps initiative was driven by Nicolas M. Chaillan, chief software officer of the U.S. Air Force, and Peter Ranks, deputy chief information Officer for Information Enterprise (DCIO IE), DoD CIO.
According to them, DevSecOps is a combination of automation tools, practices, standards, and services that enable secure and flexible deployments with confidence.
The DoD Enterprise DevSecOps Technology Stack looks like the following:
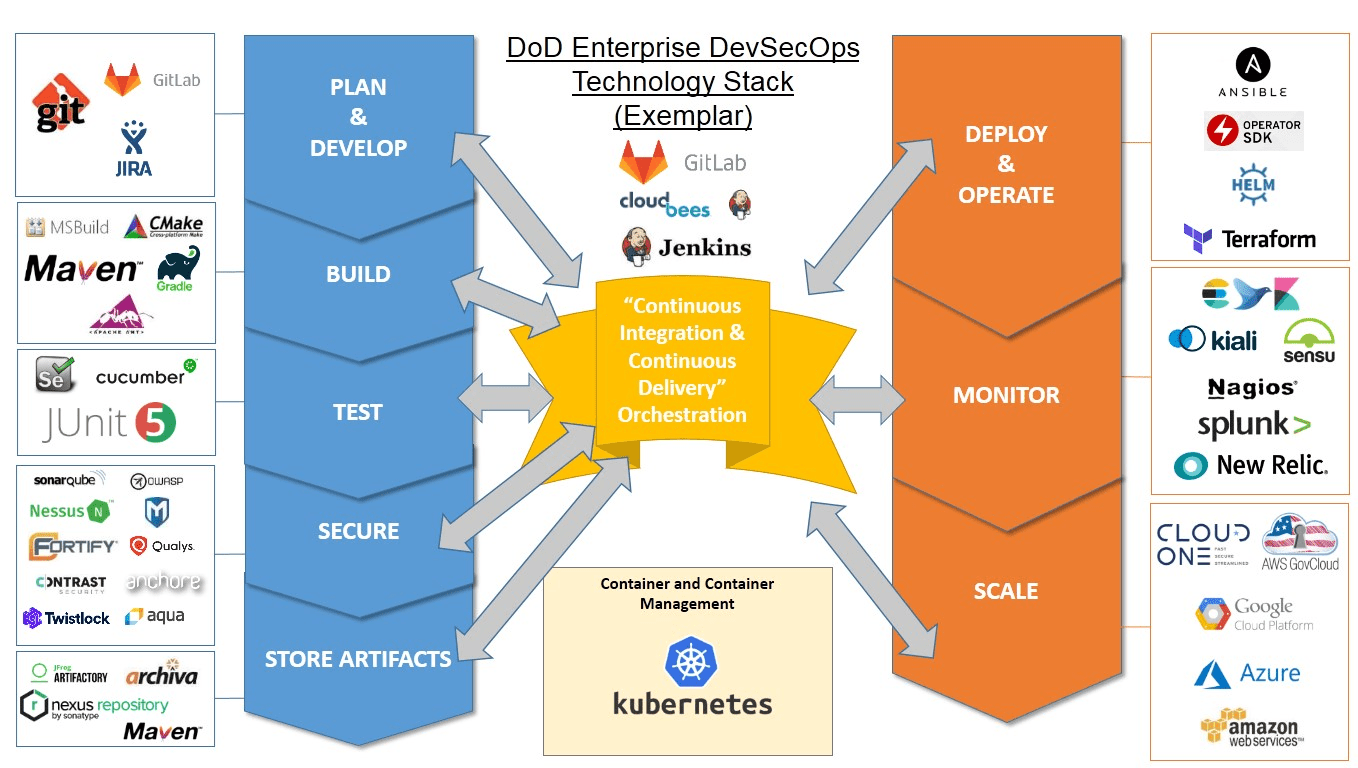
Image source: InfoQ
DoD's DevSecOps Technology Stack
In the DoD tech stack, continuous integration and continuous delivery are at the core. Then around that, they incorporated the set of tools which are required to build and operate the application.
The layers traverse from the application layers of the development teams to the infrastructure layer.
The foundational layer employs Kubernetes for orchestration purposes with security checkpoints at each stage of the software delivery pipeline. Envoy was used to handle the efficiency of the microservice architecture while Istio was implemented to handle the security aspects of Kubernetes.
Then, DevSecOps layers were placed that include continuous monitoring and infrastructure as code.
Two teams were formed to streamline the IT capabilities across the enterprise. Cloud One team provided cloud infrastructures with the necessary security features involved. Platform One team took charge of the CI/CD pipelines and other development operations strategies. The efficacy brought by these two teams eventually leads to a reduction in the software release cycle.
DoD used a sidecar container security stack to ensure security. The stack does continuous monitoring, alerting, and detecting behavior changes. For container security, they use the Anchor tool for detecting changes in the Docker files.
That's how DoD designed the DevSecOps methodology to help them build reliable and secure software systems. The DevSecOps aims to make security an integral part of the software development process, rather than an afterthought.
Takeaways
Security has become the focal point; it is not just about speed but about safety and confidence. Embedding security earlier in your software development life cycle will yield bug-free features and satisfied customers. Have security checkpoints at each stage and make sure the developers know the importance of security and make it their responsibility too (make security everyone’s job/responsibility). Managing your software and building artifacts, scanning, and securing them is very important. Make sure to use security DevSecOps tools along with the security guidelines set by your security experts.
Published at DZone with permission of Pavan Belagatti, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments