Empowering Secure Access: Unleashing the Potential of Microsoft Entra ID Application Proxy
Azure Entra ID Application Proxy can seamlessly integrate with your on-premises workload to redefine how enterprises manage and secure their applications.
Join the DZone community and get the full member experience.
Join For FreeIn today's dynamic digital landscape, secure and efficient access management is paramount for organizations navigating the complexities of remote work and diverse application landscapes and going through the digital transformation. Previously, the security plan for safeguarding on-prem/internal resources from attackers and enabling remote user access was centralized in the DMZ or VPN or having reverse proxy gateways. However, the VPN and reverse proxy solutions in the DMZ are not well-suited for the cloud environment due to their hardware costs, maintaining security (patching, monitoring ports, firewalls, etc.), authenticating users at the edge, and web servers and user tracking etc. Azure Entra ID Application Proxy emerges as a powerful solution, seamlessly integrating with your on-premises workload to redefine how enterprises manage and secure their applications.
Introduction To Azure Entra ID Application Proxy
Azure Entra ID Application Proxy serves as a bridge between on-premises applications and the cloud, enabling organizations to extend secure access to their applications to users outside the corporate network. This innovative solution simplifies connectivity, enhances security, and facilitates a seamless user experience.
Application Proxy works with:
- Web applications that use Integrated Windows authentication for authentication.
- Web applications that use form-based or header-based access.
- You can use an Application Proxy with web APIs exposed to rich apps on different devices.
- Applications hosted behind a Remote Desktop Gateway.
- Rich client apps that are integrated with the Microsoft Authentication Library (MSAL).
- SAML-based single sign-on is supported for applications that use either SAML 2.0 or WS-Federation protocols.
Key Features and Capabilities
1. Secure Remote Access
Azure Entra ID Application Proxy ensures secure remote access to on-premises applications without the need for complex VPN setups. Users can connect from any location, promoting flexibility and productivity. Application proxy also allows you to configure single sign-on (SSO) and enable multi-factor authentication across devices, resources, and apps in the cloud and on-premises.
Furthermore, the pre-authentication feature of this application proxy serves as a barrier against all anonymous cyberattacks aimed at your organization's network. This cybersecurity measure enables secure and protected remote connections to your network's applications.
2. Simplified Setup and Configuration
Setting up Azure Entra ID Application Proxy is streamlined and user-friendly. The straightforward configuration process enables organizations to quickly extend access to applications hosted on their premises.
3. Integrating With Azure Services
Explore how Azure Entra ID Application Proxy seamlessly integrates with other Azure services, such as Azure Active Directory, Azure Monitor, Azure Security Center, and Microsoft Defender for Cloud Apps, creating a holistic and robust access management solution.
4. User Tracking and Conditional Access
Through Application Proxy, Microsoft Entra ID monitors users requiring access to web apps published both on-premises and in the cloud. It serves as a centralized management hub for these applications. With Conditional Access, you can define restrictions on the traffic that you allow to hit your networks and backend application and also restrict traffic based on the location, the strength of authentication, and user risk profile.
5. Traffic Termination
All traffic to the backend application is terminated at the Application Proxy service in the cloud while the session is re-established with the backend server. This means that your backend servers are not exposed to direct HTTP traffic and are better protected against targeted DoS (denial-of-service) attacks because your firewall is not exposed.
With Application Proxy, there’s no need to open inbound connections to your corporate network. The Application Proxy connectors only use outbound connections to the Application Proxy service in the cloud over ports 80 and 443, which in turn eliminates the need to open firewall ports for incoming connections or components in the On-Prem Networks.
6. Cost Benefit
The Application Proxy is included in the Microsoft Entra ID P1/P2 license, so you don't need to pay extra for the feature. It also removes the necessity for infrastructure expenses related to security, VPN, reverse proxy, Application gateways, WAF, etc., which would have been required to expose on-premises applications to the internet in the absence of the Application Proxy.
How Azure Entra ID Application Proxy Works
Building Blocks
- Microsoft Entra ID: Microsoft Entra ID performs the authentication using the tenant directory stored in the cloud. To enable the Microsoft Entra application proxy, you must have a Microsoft Entra ID P1 or P2 license.
- Application proxy service: This runs in the cloud and is managed by Microsoft Entra ID. It passes the sign-on token from the user to the Application Proxy Connector. Application Proxy forwards any accessible headers on the request and sets the headers to the client IP address as per its protocol.
- Application proxy connectors: Application Proxy Connectors are what make Microsoft Entra application proxy possible. They are the lightweight agents that sit on-premises and facilitate the outbound connection to the Application Proxy Service. They should be deployed in the same network as that of on-premises applications. You have the ability to organize the connectors into groups and assign connectors based on data center location, isolated networks, etc.
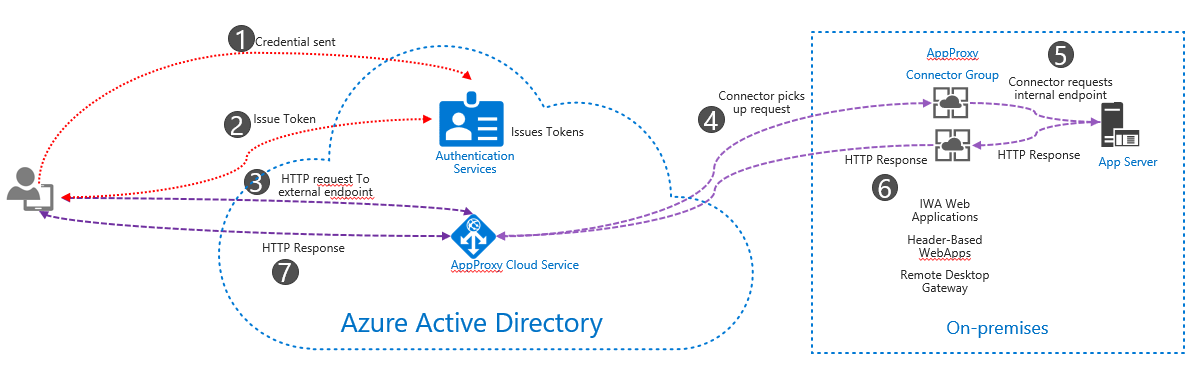
Architecture and Workflow
![architecture and workflow]()
Diagram Source: Azure
- The user browses the endpoint, and the application proxy directs them to the Microsoft Entra sign-in page. If you configure conditional access policies, it checks certain conditions, ensuring the user complies with the security requirements of your organization.
- After a successful sign-in, Microsoft Entra ID sends a token to the user's client device.
- The client sends the token to the Application Proxy service, which retrieves the user principal name (UPN) and security principal name (SPN) from the token.
- Application Proxy forwards the request, which is picked up by the Application Proxy connector.
- The connector performs any additional authentication required on behalf of the user (Optional, depending on the authentication method), requests the internal endpoint of the application server, and sends the request to the on-premises application.
- The response from the application server is sent through the connector to the Application Proxy service.
- The response is sent to the user from the Application Proxy service.
Best Practices and Optimization
- Allocate Connector groups for applications by network or location. Ensure that you have a minimum of two or more connectors per group to provide high availability and scaling.
- Avoid all forms of inline inspection on outbound TLS communication between the connectors and Azure to reduce the degradation of the communication flow.
- Enhance application performance by incorporating Traffic Manager for user-based location optimization and Azure Front Door for geo acceleration.
- Avoid using Application Proxy for internal users on the corporate network. Internal users who unnecessarily use Application Proxy can introduce unexpected and undesirable performance issues.
- Set timeouts for the backend applications for applications that require more than 75 seconds to complete the transaction.
- Use appropriate cookie types and set HTTP-OnlyCookie to mitigate exploits such as cross-site scripting. Secure Cookie needs to be enabled to mitigate the risk of being compromised over the clear text channels.
Conclusion
Azure Entra ID Application Proxy emerges as a game-changer in the realm of access management, offering a secure, flexible, and scalable solution for organizations embracing digital transformation. By seamlessly bridging on-premises applications with the cloud, it empowers enterprises to navigate the complexities of the modern digital landscape with confidence.
In conclusion, as organizations continue to prioritize secure and efficient access to applications, Azure Entra ID Application Proxy stands as a beacon, guiding them toward a future where connectivity is seamless and security is paramount.
Opinions expressed by DZone contributors are their own.

Comments