12 Expert Tips for Secure Cloud Deployments
Explore essential strategies for securing cloud environments, focusing on IAM, encryption, automation, and proactive monitoring to mitigate cyber threats.
Join the DZone community and get the full member experience.
Join For FreeAccording to the Thales 2024 Cloud Security Study, 31% of cyberattacks prioritize SaaS applications, followed closely by 30% targeting cloud storage and 26% aimed at cloud management infrastructure. Cloud resources have become the prime targets for hackers — no surprise, considering the vast amount of data companies are now storing there. And these aren’t just small-scale incidents. In June 2023, Toyota Motor Corporation issued an apology for a major data breach due to a cloud misconfiguration, potentially exposing the information of millions of customers.
Whether you're managing sensitive customer data or operating critical business applications, securing your cloud deployment isn’t a luxury — it’s essential. This guide offers 12 cloud security tips for AWS, Google Cloud, and Azure to safeguard your environment.
The Key to Secure Cloud Development
With the rise in cloud-targeted data breaches, secure cloud development is more crucial than ever. As businesses depend more on cloud infrastructure, misconfigurations, weak access controls, and poor encryption practices create opportunities for attacks. Building a secure cloud environment from the start allows your business to take advantage of cloud scalability without compromising security.
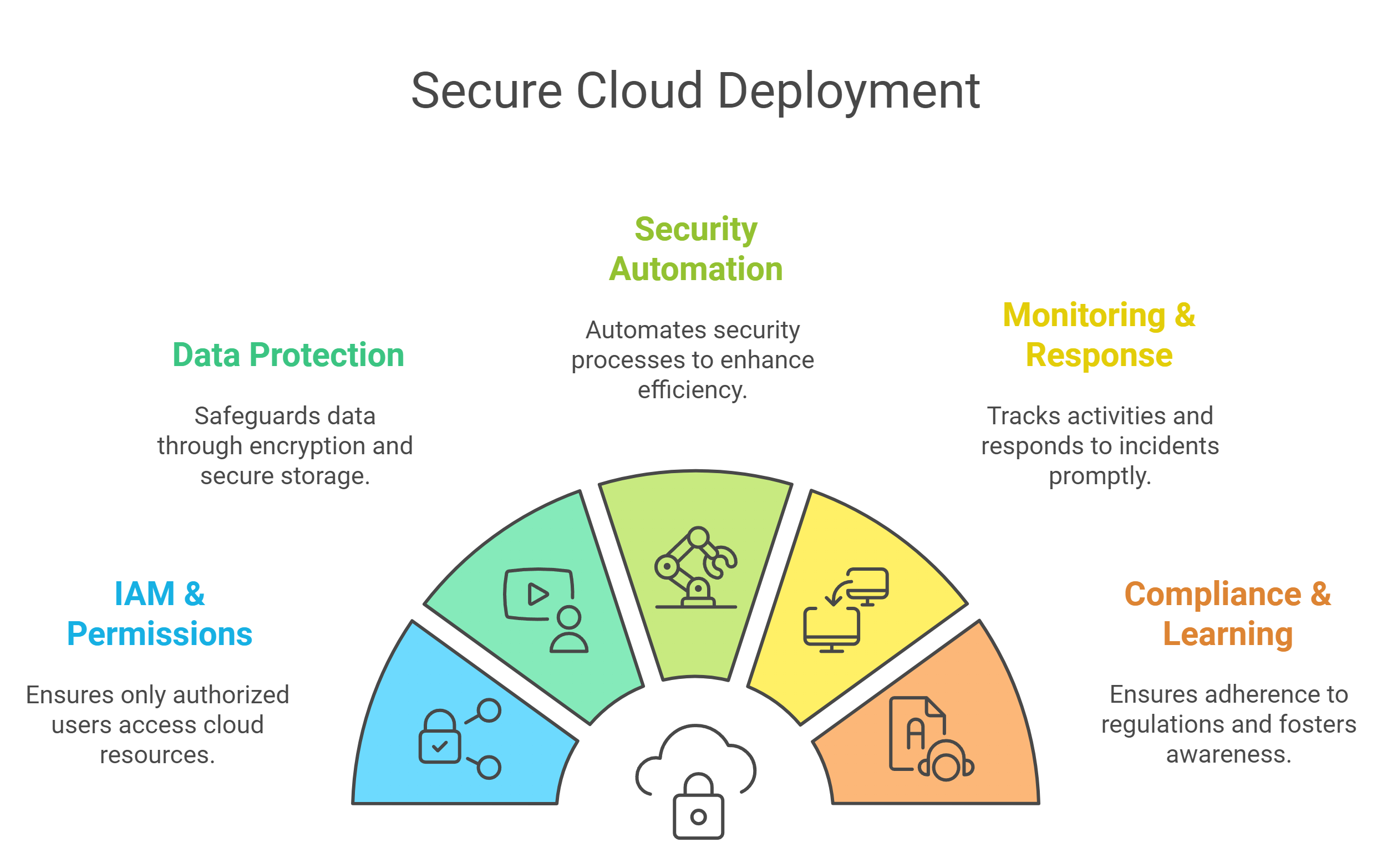
Lock Down the Cloud: 12 Best Practices for Secure Cloud Deployment
![Infographic showing five best practices for secure cloud deployment: data protection, IAM & permissions, security automation, monitoring & response, and compliance & learning]()
If you rely on cloud services, whether for storing customer data or running essential business apps, here are 12 practical and expert cloud security tips to secure your cloud deployments across the leading platforms: AWS, Google Cloud, and Azure.
Identity and Access Management (IAM) and Permissions
Tip 1: Have Robust IAM Policies
Managing who has access to your cloud resources is the foundation of cloud security. Identity and Access Management (IAM) tools allow you to fine-tune permissions, ensuring that users only have access to what they need. Each cloud provider offers specific tools:
- AWS: AWS IAM allows fine-tuned permissions and uses IAM Roles to avoid hardcoded credentials.
- Google Cloud: Google Cloud IAM applies organization-wide policies, with predefined access roles.
- Azure: Microsoft Entra ID (formerly Azure Active Directory) offers Role-Based Access Control (RBAC) and Privileged Identity Management (PIM) for temporary elevated permissions.
Tip 2: Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds a crucial extra layer of data security. Instead of relying solely on passwords, MFA requires a second form of authentication, making unauthorized access much harder across Google Cloud, AWS, and Azure environments.
- AWS: AWS MFA supports virtual devices and hardware tokens for an extra layer of protection on sensitive accounts.
- Google Cloud: Google Cloud Identity offers 2-step verification, including security keys, to enhance account security.
- Azure: Microsoft Entra ID offers MFA based on user risk factors like location or device, adding flexibility to security controls.
Data Protection and Encryption
Tip 3: Encrypt in Transit and at Rest
Ensuring that your data is encrypted at all stages is vital for protecting sensitive information. Each cloud provider offers tools to handle this seamlessly:
- AWS: AWS uses Key Management Service (KMS) for data at rest and SSL/TLS for secure data transfer across its services.
- Google Cloud: Google Cloud automatically encrypts data at rest with Cloud KMS and uses SSL/TLS for data in transit, similar to AWS.
- Azure: Azure secures data at rest with Azure Key Vault and encrypts data in transit using SSL/TLS protocols.
Tip 4: Secure Sensitive Data
Extra safeguards like encryption, tokenization, and masking are essential when dealing with personal or financial information.
- AWS: AWS offers Secrets Manager and S3 Object Encryption to protect confidential data, ensuring it’s stored securely and access is tightly controlled.
- Google Cloud: Google Cloud uses Data Loss Prevention (DLP) to detect and mask sensitive data, combined with encryption through Cloud KMS.
- Azure: Azure provides Azure Information Protection (AIP) for labeling and protecting sensitive data, along with encryption and key management through Azure Key Vault.
Security Automation and Configuration
Tip 5: Automate Security With Infrastructure as Code (IaC)
Infrastructure as Code (IaC) allows you to automate the setup and security of cloud environments, ensuring consistent configurations and reducing human error.
- AWS: AWS CloudFormation offers tools to automate infrastructure deployment, with built-in security best practices like security groups and IAM roles.
- Google Cloud: Google Cloud Deployment Manager automates infrastructure and integrates with security policies to ensure secure deployments.
- Azure: Azure Resource Manager (ARM) Templates automate the deployment of resources while enforcing security and compliance standards.
With IaC security, configurations are consistent and scalable across your cloud infrastructure.
Tip 6: Secure APIs
APIs can be vulnerable entry points if left unsecured. Implementing strong authentication and rate-limiting controls are keys to securing cloud infrastructure.
- AWS: Use AWS API Gateway with authentication methods like IAM Roles and Lambda authorizers to secure API endpoints.
- Google Cloud: Google Cloud Endpoints ensures API security with features like OAuth 2.0 and API keys for authentication and rate limiting.
- Azure: Azure API Management offers secure API access with OAuth 2.0, IP filtering, and rate limiting to prevent abuse.
Monitoring, Logging, and Incident Response
Tip 7: Rely on Continuous Monitoring and Logging
Monitoring and logging are essential for tracking activity and identifying threats in your cloud environment in real-time. These tools ensure you catch potential security risks before they escalate:
- AWS: Use AWS CloudWatch and CloudTrail to monitor and log activity, with alerts for suspicious behavior.
- Google Cloud: Google Cloud Logging collects and analyzes logs from all services, integrating with Cloud Monitoring for real-time tracking.
- Azure: Azure Monitor provides full visibility into your environment, while Azure Security Center identifies threats and logs critical activities.
Tip 8: Have a Cloud-Native Incident Response Plan
A well-structured incident response plan is essential for mitigating security breaches quickly and efficiently. With these tools, you can respond to cloud security incidents swiftly and minimize damage:
- AWS: AWS GuardDuty detects and analyzes potential threats, while AWS Systems Manager helps automate remediation processes.
- Google Cloud: Security Command Center provides real-time threat detection and allows you to respond rapidly with automated workflows.
- Azure: Azure Security Center integrates with Azure Sentinel for detecting and responding to threats, offering automated playbooks for incident management.
Compliance and Scalability
Tip 9: Ensure Compliance
As your cloud environment grows, it is important to ensure that it remains compliant with industry regulations like GDPR, HIPAA, and PCI-DSS. These tools allow you to align with security regulations effortlessly:
- AWS: Use AWS Artifact to access compliance reports and automate checks using AWS Config rules.
- Google Cloud: Compliance Manager helps you monitor and automate compliance with built-in regulatory frameworks.
- Azure: Azure Policy allows you to enforce compliance standards and automatically audit resources for adherence.
Tip 10: Scale Securely
As your cloud environment grows, maintaining security can become more challenging. Automating security during scaling helps keep vulnerabilities at bay.
- AWS: Use auto-scaling with integrated IAM roles and security groups to maintain secure, scalable environments.
- Google Cloud: Google Kubernetes Engine (GKE) ensures secure scaling with built-in policies and network controls.
- Azure: Azure Autoscale integrates with Azure Security Center to monitor and secure expanding workloads.
Continuous Learning and Security Awareness
Continuous learning and security awareness are often overlooked but critical aspects of cloud security. This involves keeping your team educated and aware of the latest best practices to ensure your cloud environment stays secure, even as new risks emerge.
Tip 11: Have Regular Security Training
Ongoing security training is essential to keep teams up to date with the latest cloud threats and best practices. Continuous training helps build a security-aware culture that stays ahead of evolving threats.
- AWS: Leverage AWS Training and Certification programs, including the Certified Security Specialty course, to stay current.
- Google Cloud: Offer your team Google Cloud’s Professional Security Engineer certification for hands-on expertise in securing cloud environments.
- Azure: Use Azure’s Security Engineer Certification to ensure your team is proficient in protecting Azure deployments.
Tip 12: Prepare for Emerging Threats
Cloud environments face new threats every day, and leveraging AI and machine learning can help detect and prevent these threats.
- AWS: Amazon Macie uses machine learning to discover and protect sensitive data, detecting anomalies and risks.
- Google Cloud: Security Command Center integrates AI-driven tools for advanced threat detection and analysis.
- Azure: Azure Sentinel uses AI to predict, detect, and respond to security incidents in real time.
Final Thoughts
At the end of the day, securing cloud computing means being proactive. With the growing complexity of potential vulnerabilities, it's crucial to stay vigilant and integrate security into every part of your cloud deployment. Whether you're using AWS, Google Cloud, or Azure, following best practices like strong IAM policies, comprehensive data encryption, and automating your infrastructure through Infrastructure as Code (IaC) are essential for maintaining your organization’s security posture.
To perfect your approach to secure cloud deployment, you need to make cloud server security a priority by embracing new tools like AWS Macie, Google Cloud's Security Command Center, and Azure Sentinel that can automate threat detection and response securing your deployments from modern threats.
It is also crucial to embed security into every layer of your cloud environment to scale your operations without compromising security. So, whether you're in the middle of continuous deployment or scaling up your infrastructure, always prioritize security — it’s the foundation of a successful, secure cloud strategy.
Opinions expressed by DZone contributors are their own.

Comments