Threat Modeling: Navigating Cybersecurity Challenges
This analysis delves into the intricacies of threat modeling, exploring its mechanisms, methodologies, real-world applications, benefits, and challenges.
Join the DZone community and get the full member experience.
Join For FreeIn an era where digital threats are constantly evolving, understanding and mitigating these risks is crucial for organizations of all sizes. Threat modeling emerges as a pivotal process in this landscape, offering a structured approach to identify, assess, and address potential security threats. This analysis delves into the intricacies of threat modeling, exploring its mechanisms, methodologies, real-world applications, benefits, and challenges.
What Is Threat Modeling, and Why Is It Important?
Threat modeling is a proactive approach in cybersecurity, where potential threats and vulnerabilities within an information system are identified and analyzed. It involves a systematic examination of an application, system, or business process to highlight security weaknesses and the potential impact of different threat scenarios.
How Does Threat Modeling Work?
The process of threat modeling typically follows these steps:
- Defining security objectives and establishing what needs to be protected
- Creating an architecture overview, mapping out the system or application architecture
- Identifying threats and using various techniques to pinpoint potential threats
- Determining vulnerabilities and assessing where the system might be exploited
- Documenting and managing risks, as well as developing strategies to mitigate identified risks
Threat Modeling Adoption and Implementation
The successful adoption of threat modeling within an organization hinges on several critical steps.
- Initially, it is imperative to focus on training and awareness. This means dedicating time and resources to educate the development team, security personnel, and stakeholders about the significance of threat modeling and the various techniques used to conduct it. A thorough understanding of threat modeling's role in identifying and preempting security vulnerabilities is essential for cultivating a security-conscious culture within the team.
- Another key aspect is integrating threat modeling into the development lifecycle. By incorporating this process from the early stages of software development, organizations can ensure that security considerations are not an afterthought but a fundamental component of the development process. Embedding threat modeling early on helps to identify potential security issues when they are generally easier and less costly to address.
- Lastly, the nature of cybersecurity demands that threat models are not static. With the ever-evolving landscape of cyber threats and the ongoing development of software systems, regular reviews are essential. These reviews should be scheduled to update and refine threat models, ensuring they accurately reflect the current threat environment and any changes within the system itself. By regularly revisiting and updating the threat models, organizations can maintain a robust and responsive security posture that adapts to new challenges as they arise.
Incorporating these practices into an organization's security strategy is not a one-time task but a continuous effort that requires commitment and adaptability. As threats evolve and systems grow more complex, the processes of training, integrating, and reviewing must also progress to keep pace with the dynamic nature of cybersecurity. DZone’s previously covered how to implement Oauth2 security in microservices.
Threat Modeling Methodologies
Several methodologies serve as the backbone for the threat modeling process, each with its unique focus and structure to guide security experts in identifying and mitigating potential threats. These methodologies provide frameworks that outline how to approach the complex task of threat analysis, ensuring a systematic and thorough examination of security risks. These include, but aren’t limited to:
- STRIDE identifies threats based on steps designed to identify what can go wrong on an application, system, IT landscape, or business process being threat modeled. It categorizes threats into six distinct types — Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege — providing a clear lens through which to view potential vulnerabilities.
- PASTA (Process for Attack Simulation and Threat Analysis) is a risk-centric methodology that always ties back to the business process while simulating and testing the viability of threats. It adopts a risk-centric approach, prioritizing threats based on their likelihood and potential impact.
- TRIKE is an open-source requirement-modeling methodology focused on defining acceptable levels of risk while assigning levels of risks to determine if the risk is acceptable to assigned stakeholders. It focuses on defining acceptable risk levels and aligning security efforts with them.
These methodologies often incorporate elements of asset identification, threat enumeration, and vulnerability mapping, alongside strategies for mitigation and risk management. By following these established guides, organizations can create comprehensive threat models tailored to their specific systems, applications, and operational contexts. The choice of methodology depends on various factors, including the type of system under review, the resources available, and the expertise of the team responsible for the threat modeling exercise. Related Article: Importance of learning java for cybersecurity.
Threat Modeling Examples
In the digital realm, where threats loom large over various sectors, real-world applications of threat modeling are both diverse and critical. For e-commerce platforms, threat modeling plays a key role in identifying and mitigating risks such as data breaches and payment fraud. These platforms handle a wealth of sensitive customer information and financial details, making them a prime target for cybercriminals. Through threat modeling, e-commerce businesses can foresee potential attack vectors, such as SQL injection or cross-site scripting, that could lead to unauthorized access to customer data or financial theft. By preemptively recognizing these threats, e-commerce sites can implement robust encryption, secure payment gateways, and continuous monitoring systems to protect both their assets and customer trust.
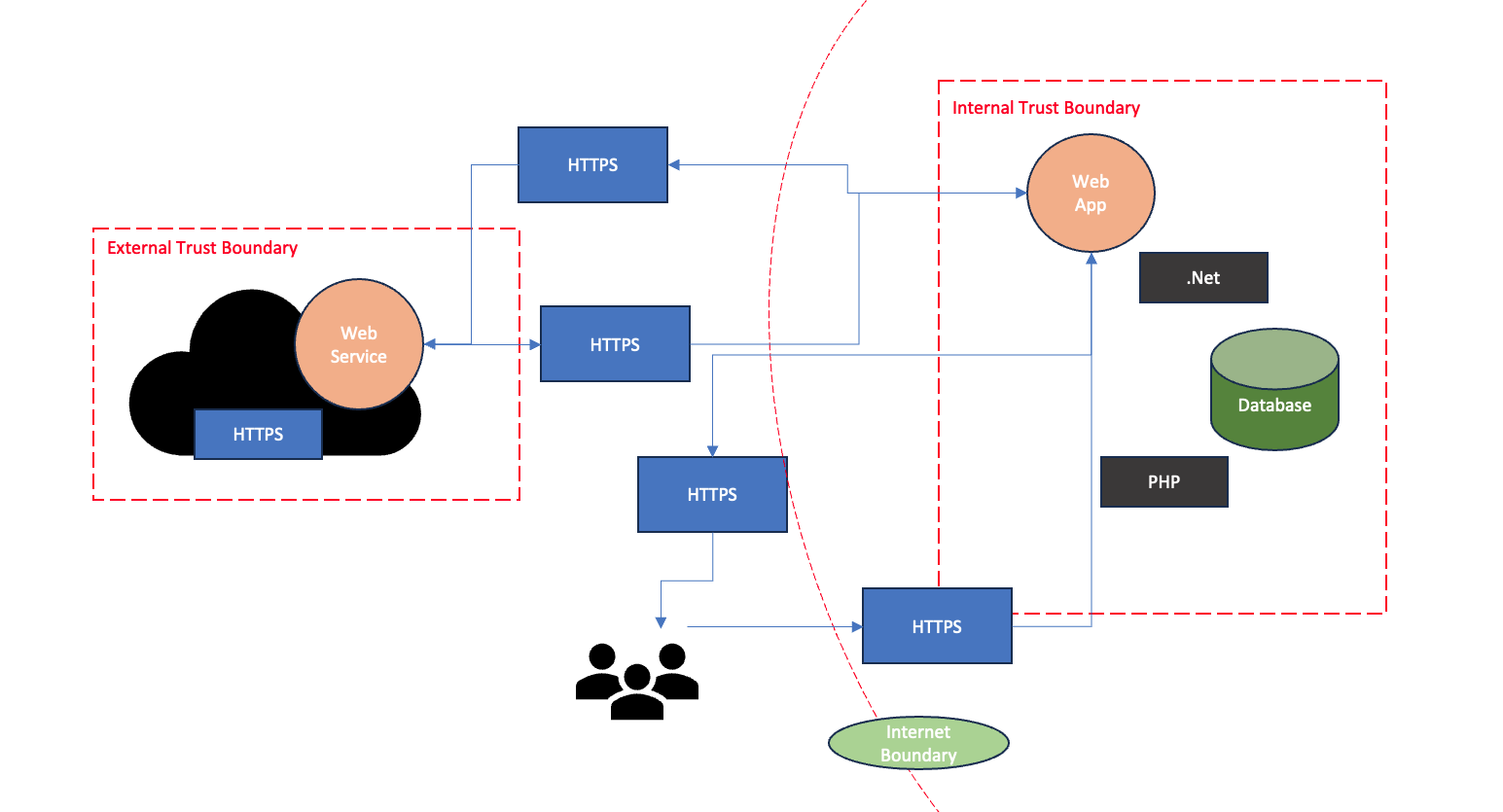
Image 1: Example of retail threat model
Financial systems also greatly benefit from threat modeling, with a sharp focus on transaction security and data integrity. The financial industry is under constant threat from sophisticated attack methods aimed at intercepting transactions or manipulating data for fraud. Threat modeling helps financial institutions map out the flow of sensitive data and pinpoint weaknesses that might be exploited by attackers to alter transaction details or siphon funds. These insights are crucial for developing layered security measures, establishing strict authentication protocols, and ensuring the integrity of financial transactions from start to finish.
Healthcare applications, on the other hand, must address not only the security of sensitive health information but also compliance with stringent regulations such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Threat modeling in healthcare can reveal how personal health information might be exposed or compromised through various channels, whether through insider threats, unsecured endpoints, or third-party services. By understanding these potential threats, healthcare providers can implement controls like access management, data encryption, and regular audits to ensure that patient data is handled securely and in compliance with legal and ethical standards. In this way, threat modeling is indispensable for upholding the confidentiality, availability, and integrity of health information systems.
Threat Modeling Benefits and Challenges
Threat modeling has significant benefits and challenges, the following table demonstrates some of these and how they correspond to each other.
| Benefit | Challenge |
|---|---|
|
Proactive Security Posture: Helps in anticipating and mitigating potential threats |
Resource Intensive: Requires time, expertise, and often specific tools |
|
Informed Decision Making: Provides a framework for making security-related decisions |
Evolving Threat Landscape: Keeping the threat model updated with emerging threats creates challenges. |
|
Compliance and Trust: Assists in meeting regulatory requirements and building customer trust |
Complexity in Large Systems: More complex in larger, more intricate systems and organizations |
Conclusion
Threat modeling is an essential component in the arsenal of modern cybersecurity strategies. While it comes with its set of challenges, its benefits in identifying and mitigating risks are invaluable. As cyber threats continue to evolve, so too must our approaches to understanding and combating them. Whether for a cybersecurity professional or an organization striving to fortify its digital defenses, understanding threat modeling is a step toward a more secure operational environment.
Opinions expressed by DZone contributors are their own.

Comments