Threat Modelling Tools Analysis 101
Key DevSecOps solutions available and their benefits and pitfalls through a series of evaluating different tools for Technical Architects and Engineering Teams.
Join the DZone community and get the full member experience.
Join For FreeAbstract
An interconnected world with an increasing number of systems, products and services relying on the availability, confidentiality, and integrity of sensitive information is vulnerable to attacks and incidents. Unfortunately, the threat landscape expands and new threats, threat agents and attack vectors emerge at all times. Defending against these threats requires that organizations are aware of such threats and threat agents. Threat modeling can be used as part of security risk analysis to systematically iterate over possible threat scenarios.
The motivation for this research came from the constantly growing need to acquire better tools to tackle the broad and expanding threat landscape. One such tool which help to categorize and systematically evaluate the security of a system, product or service, is threat modeling.
Problems With Shifting Left in Designing Secure Applications
It is believed that secure systems are a corollary indicator of high-quality systems and hence it adds value to catch these defects early in the system design and development stages. However, every Engineering team and Technical Architect is always trying to find a solution to implement threat modelling into their existing DevOps Ecosystem.
The key challenge is finding ways to adopt a security framework for designing robust enterprise applications, as it is becoming difficult to stay updated with ever changing attack surfaces and threat and vulnerabilities.
Available Solutions, Benefits, Pitfalls, and Recommendations
As a DevSecOps practitioner and Security Architect I will like to share some of the key solutions available and their benefits and pitfalls through this series of evaluating different tools. I used hands on assessments and used a parameterized technical analysis and rating system for this evaluation using business cases from the emerging techs and industries.
The key factors considered into this analysis is given in the table below. I tried to conduct and in-depth analysis and recommendation and find that it is going to be useful for teams who are planning or in the process of shifting left in their organizations or projects towards DevSecOps. The Key Audience for this report is Developers, Technical Architects, Business Analysts, IT and Operations Teams of different experience levels.
Parameters |
Score 3 |
Score 2 |
Score 1 |
Learning Curve and time to create a model |
If the learning curve is small and time to create a model is less than an hour it is user friendly for majority of target audience. |
If is learning curve is medium and time to create a model is more than 1 Hr. but less than 3 Hrs. and it can be used by 30-40% of target audience. |
If it is difficult to learn and time to create a model is exponentially large use by the target audience. |
Ease of creating Threat Model (UX) |
If the user experience is high and it is easy to create and understand the threat models created by other team |
If the UX is okay, but different teams are able to understand the design created by other team. |
If created by someone but the threat model is difficult to understand |
Provision for pre-built templates |
If many templates are available |
If a few templates are available |
If no templates are available |
No. of Threat Modelling Frameworks Supported |
More than 3 Frameworks |
1 0r 2 Two frameworks |
No Framework support |
Design View |
Availability of stencils and option to add stencils or upgrade stencils |
Availability of stencils but no option or difficult to customize |
Standard Stencil |
Available Documentation |
Available and continuously updated documentation |
Available documentation but hard to follow through |
Zero Documentation or basic documentation. |
Analysis View |
Thorough Analysis with remediation. |
Analysis only with no suggested remediation |
No Analysis only Design |
Regular Updates |
Continuous and Frequent Updates |
Regular or Periodic updates but large intervals |
No Updates since in last 6 months |
Cost |
Open Source/ Pay-Per-Use/ User based Licensing |
Open Source/User Licensing/Paid (other model) |
Paid |
Integration in CI/CD Pipeline |
Possible and plugins available |
Possible but hard to integrate |
Not Possible |
Microsoft Threat Modelling Tool 2017
We started off from evaluating the two common and most easily available Threat Modelling Tool. In this series I am presenting my opinion on MSMT 2017. I tried to develop and execute a threat model for an IoT Data Flow to study the usability to identify the Threats, Vulnerabilities and Remediation proposed by these tools below.

I tried to create the data flow using Microsoft Threat Modelling Tool and below is my personal finding and opinion on the benefits and pitfalls of using the tool.
Microsoft uses Microsoft Security Development Life Cycle (SDL) to identify threats, attacks, vulnerabilities, and countermeasures that could affect your application. The Microsoft Threat Modelling Tool (MTMT) provides a standard notation for visualizing system components, data flows, and security boundaries.
The tool provides a design view to add models. You can use the canvas space to drag and drop elements from the sidebar. Drag and drop is the quickest way to build models. However, I found certain challenges in designing the model in Design View.
I was able to create a similar data flow diagram but I also wanted to create flow boundaries. The stencil allowed me to add the same however, I was not able to easily modify the size or expand the boundary. This can lead to leaving more vulnerabilities in the application when we move forward to the analysis view. There are not a lot of stencils available in default download. However, you can add more templates from GitHub specifically targeted for Azure environments.
https://github.com/AzureArchitecture/threat-model-templates
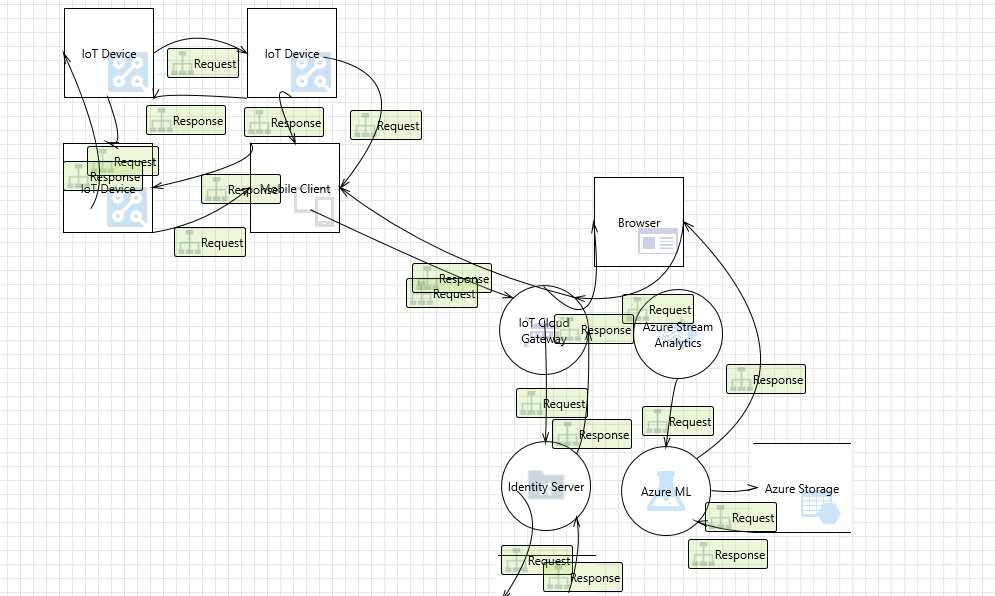
When I further moved into the analysis view, we found the following analysis based on STRIDE Framework which is configured within the application and is one of the popular Threat Modeling Frameworks.
In order to add new framework, the tool provides a create your own stencils and templates.
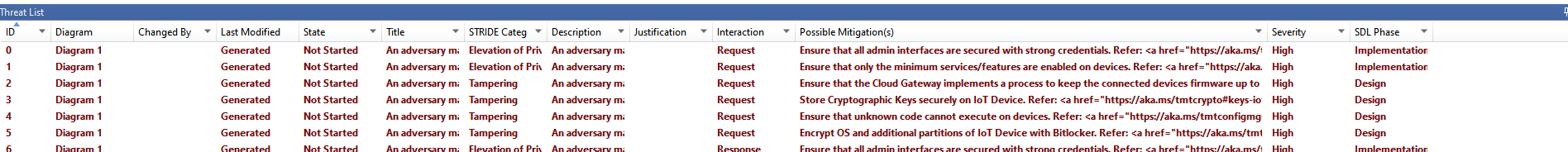
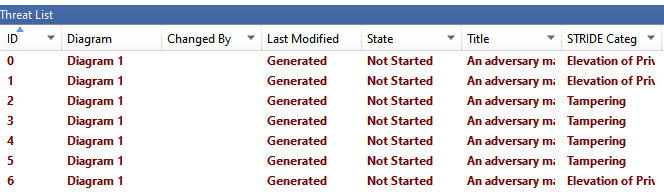
A detailed view of the Threats identified by the tool and the elements involved. You can click to see the details in the property box below the table.
It also provides the mitigation guidance and the SDL phase Impacted with the Threat along with its severity.
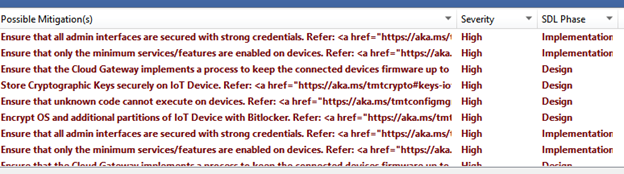
I found the following outcome from my analysis of using the tool.
Key Benefits
- Drawing a Diagram Quickly – The drag and drop elements provides a quick way to add elements to the data model.
- STRIDE per Element: Guided analysis of threats and mitigations
- Reporting: Security activities and testing in the verification phase
- Marking Out of Scope: The ability to mark certain elements out of scope adds value for incremental threat analysis or when different teams are involved in Threat Modelling. Teams can choose their area of scope.
Pitfalls
- No integration with CI/CD Pipeline.
- Boundary Definitions did not work properly which can create more issues to look at than the actual to mitigate.
- Usability of the available stencils as they were primarily designed for DFD’s.
- The graphical representation does not have many customizations for presentation to different audience.
Here is my final Scoring for the Microsoft Threat Modeling tool.
Parameters |
Highly Rated |
Good To Use |
No Value Add |
Learning Curve |
Yes |
||
Ease of creating Threat Model (UX) |
Yes |
||
Provision for pre-built templates |
Yes |
||
No. of Threat Modelling Frameworks Supported |
Yes |
||
Design View |
Yes |
||
Available Documentation |
Yes |
||
Analysis View |
Yes |
||
Regular Updates |
|||
Cost |
|||
Integration in CI/CD Pipeline |
My conclusion, to begin with, and gaining experience in Threat Modelling this is a good tool to use to initially capture some definite security requirements which can be added to your PBI’s and can be taken care of during the sprints.
We continue to focus and strive to build solutions for the most critical development and operations for the product and engineering teams and will continue to bring you across the next 101 on OWASP Threat Modelling Tool.
Opinions expressed by DZone contributors are their own.

Comments