Simplifying IAC Using Terraform, Terragrunt, and Atlantis
In this article, we discussed integrating Terraform with Terragrunt and how to automate terraform operations with Atlantis.
Join the DZone community and get the full member experience.
Join For FreeBefore we start on simplifying the Infra as Code(IAC), let's learn about what it is and the best practices of coding for our Infra.
What Is Infra as Code(IAC)?
IaC is a method of templating your infrastructure configuration in a version-controlled system and automate the provisioning and destruction of application environments. Adapting IAC helps in enabling self-service for developers, reducing bottlenecks, errors, and time-consuming rollbacks.
In short, we need a framework that can provision our infrastructure that includes virtual servers, network policies, roles and permissions, VPC, Databases, inbound-outbound rules, etc.
After provisioning, we install applications, dependent software and specific scripts to be added, etc. Then we need some tools to test the stability of our Infra.
So, we can achieve this completes task using a different set of open source tools, some of them widely used are Ansible, Chef or puppet, Salt, etc. but not limited to this. There are multiple approaches IT infra management teams are using across different organizations.
We use IAC because it saves our time and cost, we can focus and collaborate on application development rather than managing infra. No more worries about setup the same infra architect for different environments like Dev, Qa, and Prod. We can create as many no. of instances/VM and set up applications as per the requirement and our traffic. This is the major benefit of using IAC.
Understanding the Anatomy of Infra as Code
Source Control: Iac starts with a repository that provides capabilities for versioning, branching, and merging of the code. Also better visual on commit and collaboration history.
Governance: Managing the user and service accounts in the form of a template is easy and ensures compliance. Enable the admin to keep track of passwords, policies, IAM roles, secrets and provide greater visibility for audit control.
Templates: Define the templates as purpose-driven to reduce complexity, allow the user to follow the architecture patterns with a defined limit of resources, and avoid creating a unique template for different applications this makes IAC Consistent. Also, include the variables to make the template reusable.
Testing: Good IAC starts with rigorous testing principles, terraform allows you to validate templates with terraforming validate, Apply static checks with tflint , Security checks with tfsec, and manage multi env with TFenv.
Best Practices to Follow
- Make code your single source of truth.
- Version control all of your configuration files and infra.
- Versioning enables an Auditing trail for changes.
- Use little documentation for your infrastructure specifications.
- Use encrypted secrets and passwords.
How we set up the Elastic Kubernetes Service (EKS) Infra using Open-source tools which provide consistency for managing multiple cloud providers from a single versioned template. We have used the below tools to achieve this.
Terraform: Is Used for infrastructure as code used to define the provisioning of infra (Servers, ELB, Networks, VPC, Database), terraform uses high-level configuration language developed by Hashicorp. We also used terraform for deploying K8 Cluster deployments, daemon sets, cronjobs and used for managing k8 Api resources (RBAC, Cluster roles) as a part of infra setup.
Terragrunt: This is used as a thin wrapper for terraform modules and keeps the terraform configurations DRY (Don't Repeat Yourself), It allows versioning and reusability of modules also enable us to manage the remote state of different cloud or infra.
Atlantis: We used this to automate terraform plan and apply it directly from Terraform pull requests. Atlantis makes use of webhook secrets so clients can verify that the webhooks came from them. Terraform plan is run using GitHub webhooks and without exposing the credentials. You can also use Bitbucket, GitLab, or GitHub here.
PowerfulSeal: Used for Validation and quality check of applied infra after the infra is provisioned. this is an advanced Python tool for injecting various scenarios into K8 clusters to create a choes env and check the consistency of infra.
The Setup and Working of this Project
We have separate Modules for Dev/QA/Prod as follows:
- Module subdirectory can have code for the VPC layer and networking for different regions.
- Different module or same for k8 provisioning for dev/qa/prod.
![]()
After Using terraform:
- Add the terragrunt.hcl file in the root module.
- Define backend only once in the root terragrunt file.
- Define variables once in Child modules.
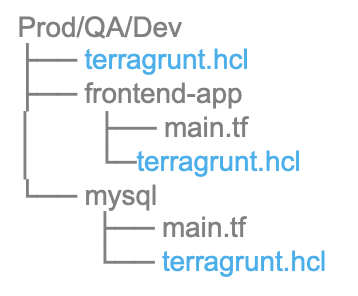
- Each Module Dev/QA/Prod can have its own set of IAM roles and permission.
- Separate permission for dev and prod admin to terragrunt plan and apply.
- Config atlantis.yaml file to use terragrunt from atlantis.
- Atlantis.yaml is a repo-level file.
The Benefits of Using this Approach
Terrafrom:
- Use the same configuration language to provision the infrastructure and to deploy applications into it.
- Using terraform you can focus on the more granular parts of infra and changes can be saved in versioned-control.
- Incremental updates are easy with granular changes.
- Large infra management is easy, not limit to hardcoded values.
- Versioning of terraforming modules helps in auditing and rollback is easy.
Terragrunt:
- Terragrunt makes management easier, multiple values and backend need to be defined only once.
- Using terragrunt defines remote backend config only once in root location and inheriting that configuration in all child modules.
Atlantis:
- Defining Workflow is easy, terraform or terragrunt.
- Custom scripts can be applied without doing any change in terraform.
- Execute Terraform commands on multiple modules at once.
- Visibility to terraform applied infra.
- Using Webhooks Credentials is safe.
PowerfulSeal:
- Proactive testing on infra setup
- Monkey testing as per your application.
Testing your Infra consistency:
- Various Chaos tools are available in OpenSource for testing K8 infra.
- This unlocks the powerful ability to test your infrastructure just like you test your code.
- We need chaos testing because the codebase contains many units and integration.
- To verify that the code’s logic is correct.
- These tools are pod killers.
Tool for Testing
PowerfulSeal:
- Advanced Python tool for injecting various problems into K8 clusters.
- Several operations modes for conducting chaos experiments.
- It Supports multiple cloud providers (AWS, Azure, GCP, OpenStack), Also can be run in local env.
- Users can define the strategies in the policy.yaml file.
- Application pods can be defined with labels for chaos testing.
- Eliminate the bad news that “something isn’t working right.” Instead, you’ll be able to deploy with confidence that your systems will work as expected.
Thanks for reading!
Opinions expressed by DZone contributors are their own.


Comments