Sending a Message to Azure Service Bus Queue/Topic Using TIBCO BW 6.x
In this article, we will walk through how to send messages on an Azure Service Bus queue/topic.
Join the DZone community and get the full member experience.
Join For FreeIn this article, we will walk through how to send messages on an Azure Service Bus queue/topic.
Basic Prerequisites
- Create an Azure Service Bus queue/topic: For this, you can refer to the Microsoft Azure docs to understand what is Azure queue/topic and how we can create them in the Azure portal. Here's a link you can refer to Create Azure ServiceBus queue/topic. Or, you can refer to another Dzone Article by Jitendra Bafna where he has explained the same: Jitendra Article.
- Get these below details (which you will be already having after following above step) using which we will create Shared Access Signature (SAS) for our Service Bus queue/topic:
- Namespace name: In my case it's (testazurenamespace)
- Key name: By default, it is (RootManageSharedAccessKey)
- Key-value: This will be your primary key
Shared Access Signatures
Shared Access Signature(SAS) is the primary security mechanism for service bus messaging. They act as an authorization mechanism for accessing a service bus queue/topic. For more detail, on SAS you can refer to the following Microsoft Azure link SAS Azure doc
Creating SAS Token
There are many ways to create SAS token for accessing Azure service bus queue/topic. In this article, we will be using a basic Java program that will help us to create SAS token
xxxxxxxxxx
package com.rudra.sastokengenerator;
import java.io.UnsupportedEncodingException;
import java.net.URLEncoder;
import java.security.InvalidKeyException;
import java.security.NoSuchAlgorithmException;
import java.util.Base64;
import java.util.Base64.Encoder;
import javax.crypto.Mac;
import javax.crypto.spec.SecretKeySpec;
import java.util.*;
("unused")
public class SASTokenGenerator {
static String finalToken;
private static String result;
public static String main(String s){
setResult(finalToken);
return finalToken;
}
public SASTokenGenerator() {
}
public static String GetSASToken(String resourceUri, String keyName, String key)
{
long epoch = System.currentTimeMillis()/1000L;
int week = 60*60*24*7;
String expiry = Long.toString(epoch + week);
String sasToken = null;
try {
String stringToSign = URLEncoder.encode(resourceUri, "UTF-8") + "\n" + expiry;
String signature = getHMAC256(key, stringToSign);
sasToken = "SharedAccessSignature sr=" + URLEncoder.encode(resourceUri, "UTF-8") +"&sig=" +
URLEncoder.encode(signature, "UTF-8") + "&se=" + expiry + "&skn=" + keyName;
} catch (UnsupportedEncodingException e) {
e.printStackTrace();
}
return sasToken;
}
public static String getHMAC256(String key, String input) {
Mac sha256_HMAC = null;
String hash = null;
try {
sha256_HMAC = Mac.getInstance("HmacSHA256");
SecretKeySpec secret_key = new SecretKeySpec(key.getBytes(), "HmacSHA256");
sha256_HMAC.init(secret_key);
Encoder encoder = Base64.getEncoder();
hash = new String(encoder.encode(sha256_HMAC.doFinal(input.getBytes("UTF-8"))));
} catch (InvalidKeyException e) {
e.printStackTrace();
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
} catch (IllegalStateException e) {
e.printStackTrace();
} catch (UnsupportedEncodingException e) {
e.printStackTrace();
}
return hash;
}
public static String getResult() {
return result;
}
public static void setResult(String result) {
SASTokenGenerator.result = result;
}
}
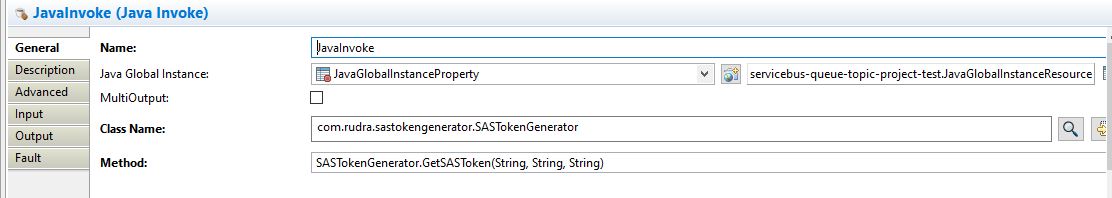
In the above program we will be calling GetSASToken function which accepts 3 parameters whose composition will look like below:
- resourceUri : {Namespace}.servicebus.windows.net/{queue_name} , example (testazurenamespace.servicebus.windows.net/testazurequeue)
- keyName : RootManageSharedAccessKey
- key: primary key value obtained
Before we move on to the actual TIBCO BW code, we will be generating a certificate for our REST Azure service bus queue/topic endpoint that we will be hitting. In my case, the endpoint is: https://testazurenamespace.servicebus.windows.net/testazurequeue/message
In the end, the "/message" URI is mandatory to be used in any Azure endpoint
To generate a certificate from URL you can refer the following link generate a certificate from the endpoint
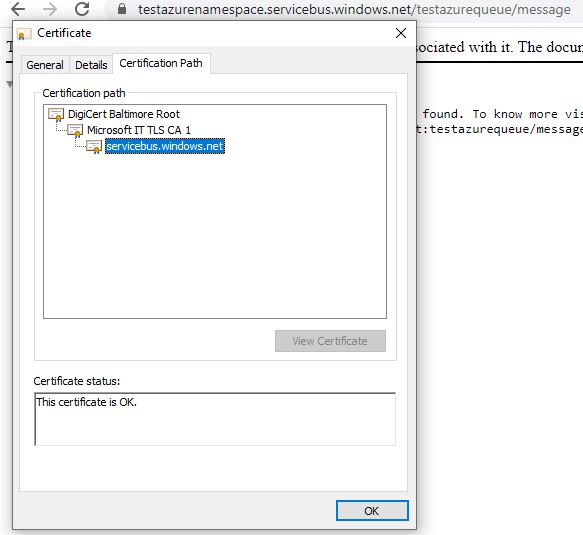
In my case, I got 3 .cer files which I combined in a single .jks file to be used in my code.
Finally, Our TIBCO BW Process Will Look Like
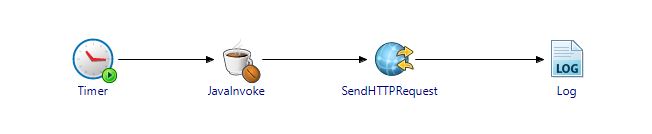
JavaInvoke Activity Will Refer to the Java Program as Below
Input tab will have our details as below:
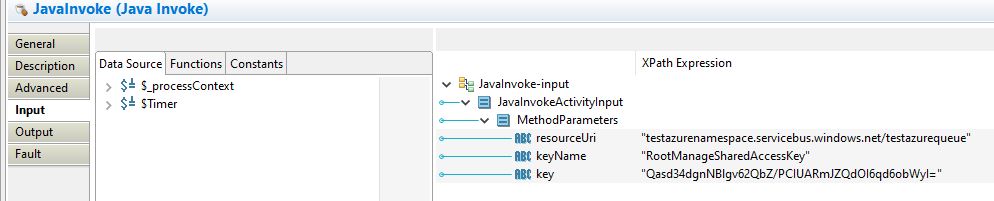
I have altered the key value for security reason, you have to use your Primary Key value here.
The output of JavaInvoke activity will be our SAS token that we will be further using in SendHTTPRequest for authorization purposes to send messages.
SendHTTPRequest Activity Will Have the Following Configuration
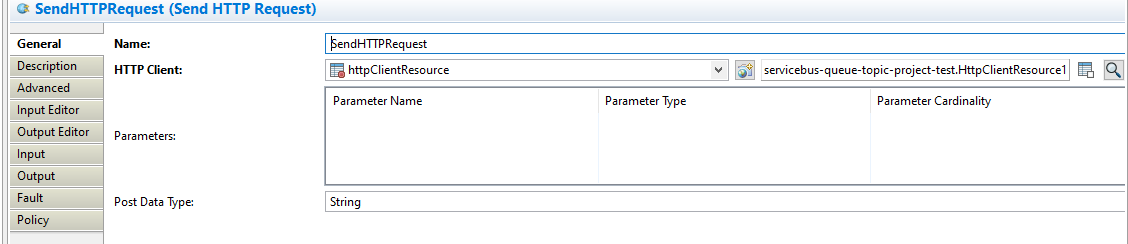
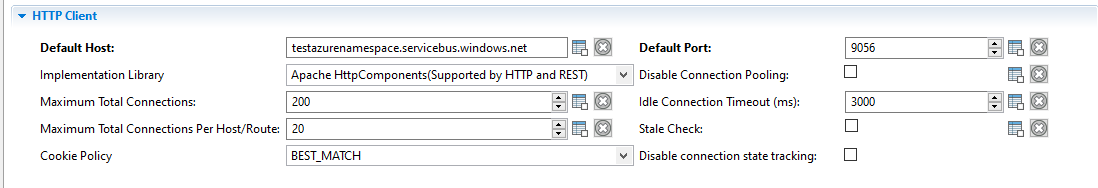
The HTTP Client will be used to configure the certificate as below:
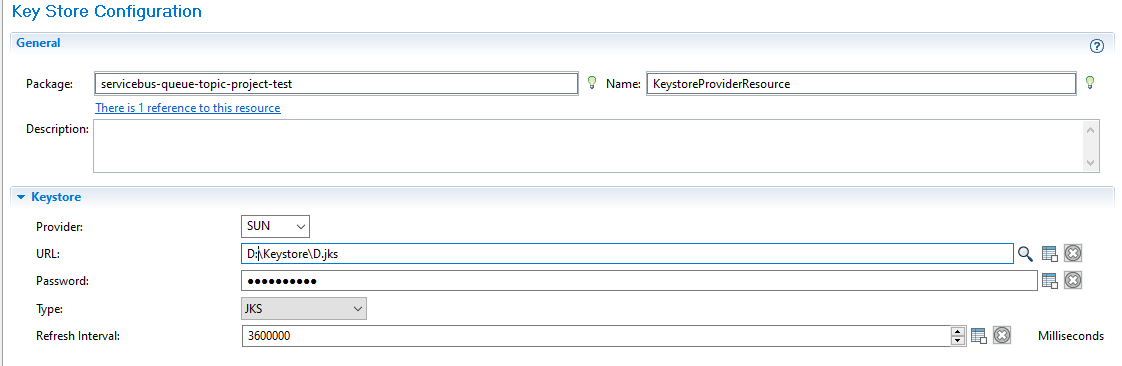
KeyStore will finally have the certificate configured as below:
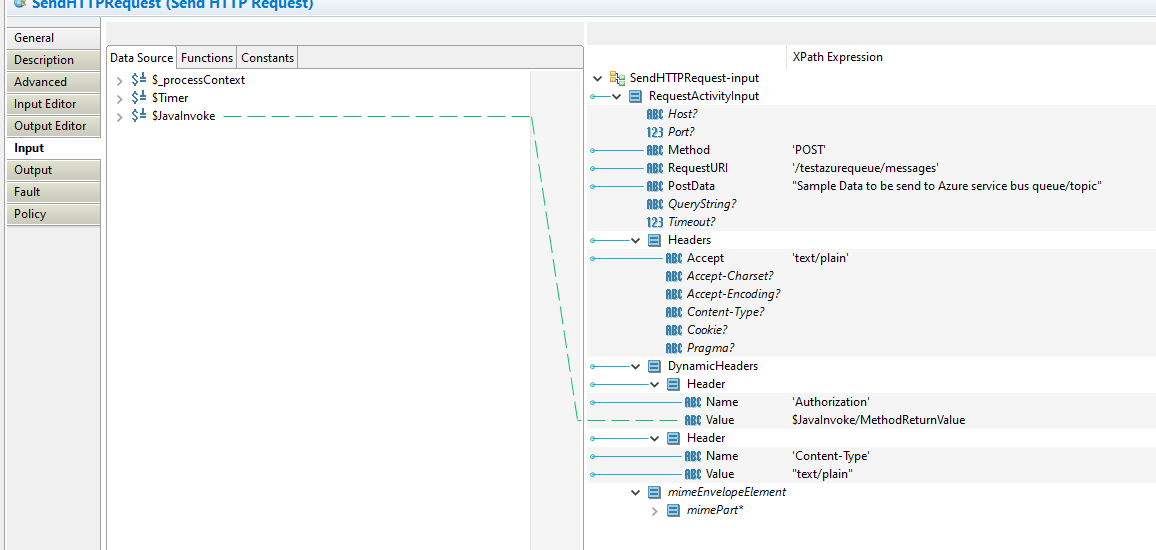
Finally when we will proceed with providing the inputs in the Input tab of SendHTTPRequest as below:
Opinions expressed by DZone contributors are their own.

Comments