Securing a MuleSoft Application Properties File
In this article, see a tutorial on how to secure a MuleSoft application properties file.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
It is very important to store the confidential and sensitive data in properties file encrypted. MuleSoft provides capabilities where you can encrypt single property or entire file. From MuleSoft documentation:
"Create a secure configuration properties file."
"Define secure properties in the file by enclosing the encrypted values between the sequence ![value]."
"Configure the file in the project with the Mule Secure Configuration Properties Extension module. The file must point to or include the decryption key."
MuleSoft provides a utility (secure-properties-tool.jar) that can be downloaded from here. This jar file is used to encrypt or decrypt the string or file.
You might also like: Property File Handling in Mule 4
Attributes
Before we create the properties file, let's understand some important attributes:
Attribute Name |
Description |
Name |
A unique name for your global secure configuration properties. |
Key |
A word or phrase that you specify to unlock the properties value. |
File |
The location of the file that the key unlocks. |
Encoding |
Encoding of the file that the key unlocks. The default value is UTF-8. |
File Level Encryption |
Set to true if the file itself is entirely encrypted. Default value is false. |
Algorithm |
The type of algorithm you use to encrypt the content of the property. |
Mode |
The procedure that allows the Mule runtime engine to repeatedly use a block cipher with a single key. |
Setting Up Mule Secure Configuration Property Extension
By default, you will not find the Mule Secure Configuration Property extension in Anypoint Studio. You can install it from Exchange into your Anypoint Studio.
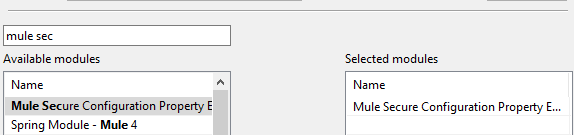
Create a Secure Configuration Properties File
The first step is to create a secure properties file. It can be .properties or .yaml file. MuleSoft recommends using a YAML configuration file because it allows the addition of type validations and auto-completion. The Mule Secure Configuration Properties Extension module enables you to configure these .yaml or .properties file types.
You can create secure configuration properties files either in src/main/resources in your Mule project or by using absolute paths.
Example YAML Properties File
xxxxxxxxxx
smtp
email
port"587"
host"smtp.gmail.com"
username"no.reply@gmail.com"
password"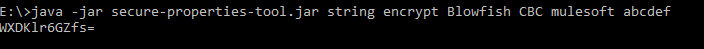
The encrypted value needs to be added to the properties file as shown below:
![encryptedpassword]
This will tell the runtime that this particular value needs to decrypt.
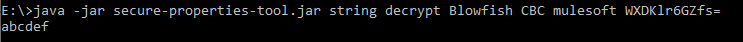
We need to use the same key, algorithm, and mode for decrypting the data.
java -jar secure-properties-tool.jar string decrypt Blowfish CBC MuleSoft WXDKlr6GZfs=
Create Secure Configuration Property in Global Configuration
To create Secure Properties Config, you can use Global Configuration.
Provide the Properties File location, Key (can be used to encrypt and decrypt the text), Algorithm (can be Blowfish), and Mode to CBC.
Accessing Secure Property in MuleSoft Components
Secure property can be accessed in connector, DataWeave, etc.
To access property, we can use ${secure::propertyName}.
Supported Algorithms
AES (default), Blowfish, DES, DESede, RC2, and RCA.
The following algorithms can be used only if you configure a Java Cryptography Extension (JCE) Provider that adds support for them:
Camellia, CAST5, CAST6, Noekeon, Rijndael, SEED, Serpent, Skipjack, TEA, Twofish, XTEA, RC5, and RC6.
Supported Modes
CBC (default), CFB, ECB, and OFB.
Best Practices
- It is recommended to keep separate properties file for each environment (eg. appName-dev.yaml, appName-test.yaml, appName-prod.yaml).
- It is recommended to use a .yaml file instead of a .properties file.
- It is recommended to declare a global property for the environment (eg. mule.env).
- Do not change mule.env property to prod or test but instead, pass as argument in the CI/CD pipeline maven command.
mvn deploy -DmuleDeploy -Dmule.env=prod
- All sensitive and confidential data like passwords and keys need to be encrypted before storing them in the property file.
- Keep all connections and other properties in global.xml.
Now you know how to encrypt the sensitive and confidential data before storing it to Mule Properties File.
Further Reading
Mule: Load Properties as per the Environment (With Default Properties File)
Opinions expressed by DZone contributors are their own.

Comments