SAAS Security: 6 Best Practices and Strategies
The SaaS industry has reshaped the way companies are operating in the digital landscape, but it is important to consider the security aspects and develop a security plan.
Join the DZone community and get the full member experience.
Join For FreeThe rise of cloud computing and SaaS (Software as a Service) has dramatically reshaped the digital landscape, offering companies numerous benefits like scalability, cost-efficiency, and flexibility. In fact, the five largest SaaS companies in the U.S. have a combined market capitalization of $742.4 billion USD. The second largest SaaS company in the U.S. list, Salesforce serves over 150,000 customers across the globe, with customers from industries not limited to professional services, manufacturing, retail, banking, finance, media, life sciences, insurance, and real estate, to name a few. However, these benefits at this scale also come with a load of security challenges, making SaaS security an integral part of operations and IT. By following some best practices and strategies, organizations can better combat security risks and mitigate potential threats.
A recent incident that I discovered that created waves across the SaaS security landscape was the Salesforce data leaks earlier this year. An alarming number of companies, including banks, governmental agencies, and healthcare providers, were unwittingly leaking sensitive and private information due to a misconfiguration in public Salesforce Community websites. The security flaw allowed unauthenticated users to access records typically reserved for logged-in users. One such case was discovered in the state of Vermont, where at least five different Salesforce Community sites were found to expose sensitive data such as full names, Social Security numbers, addresses, phone numbers, emails, and bank account numbers of users and the general public. This was especially concerning for a Pandemic Unemployment Assistance program. Vermont's Chief Information Security Officer Scott Carbee stated that the flawed sites were hastily created in response to the COVID-19 pandemic and thus did not undergo a standard security review.
Understanding SaaS Security
In the modern digital ecosystem, many organizations utilize multiple cloud environments at the same time, sometimes making SaaS applications prime targets for cybercriminals due to their large repository of sensitive data. SaaS security encompasses the measures taken to protect these valuable assets in a SaaS architecture.
It is important to understand that the responsibility for SaaS security is shared between the customer and the provider, also known as the Shared Responsibility Model (SRM). With the rise of SaaS Security Posture Management (SSPM) systems, organizations can automate and regulate SaaS security more efficiently, offering a robust defense against potential security breaches.
The Importance of Prioritizing SaaS Security
While organizations may have experience managing security risks associated with Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS), the SaaS applications present unique challenges due to the complexity of SaaS apps, lack of transparent communication between security and business teams, and the need for ongoing collaboration.
According to a survey conducted by McKinsey, most companies have ramped up their focus on SaaS security due to these challenges. These organizations stress both their internal security capabilities and those of their SaaS providers (Shared Responsibility Model). However, many had expressed dissatisfaction with the lack of customer-centric security approaches and implementation delays from vendors.
Despite these hurdles, prioritizing SaaS security is non-negotiable due to the vast quantities of sensitive data that these applications often handle and what may be at risk if security is not prioritized.
Shared Responsibility and SaaS Security Challenges
The shared responsibility model for cloud security calls for cloud providers, product vendors, and customers to each assume responsibility for the security measures that fall under their control. With SaaS, the application provider is responsible for the physical infrastructure, network, OS, and application, while the customer is responsible for data and identity management.
However, the rapid growth of SaaS adoption has outpaced the ability of security teams to keep up with the new risks and vulnerabilities these applications bring. Out-of-the-box security settings may not comply with organizational standards, and customization makes security more challenging. A report by Oracle and ESG found that 66 percent of all organizations found the shared responsibility model for SaaS confusing, leading to potential risks to their data.
Let us look at six best practices and strategies that can help enhance SaaS security for organizations, particularly customers of SaaS providers.
1. Enhanced Authentication
Authentication can be handled in various ways by cloud providers, making it crucial for security teams to understand the authentication methods supported by each SaaS service in use. Single sign-on (SSO) tied to an organization's Active Directory (AD) is a good option if the SaaS provider supports it. This allows for uniformity between the account and password policies across all the SaaS applications. Again, care is needed here to ensure that the organization's employees and IT staff are briefed on the requirements continuously, as standardization of any kind is not a replacement for basic security knowledge that every employee should possess.
2. Data Encryption
Using Transport Layer Security (TLS) to protect data in transit and enabling encryption for data at rest are vital aspects of SaaS security. It is essential to research the security measures offered by each SaaS service and enable encryption where available. Some providers, like Amazon Web Services (AWS), provide APIs for their customers to integrate encryption and data protection with any of the services being developed or deployed in an AWS environment.
3. Complex and Customized Configurations
Mid-sized enterprises typically use over 185 SaaS applications, each with unique, adjustable controls and settings to cater to specific organizational needs. However, managing these configurations manually is a daunting task for security teams due to the sheer volume and lack of uniformity. Striking a balance between functionality and security becomes a complex task. Customizing a SaaS app for optimal value often compromises the default security settings, potentially conflicting with an organization's security and compliance requirements. Furthermore, interactions between SaaS apps and internal systems complicate the detection of anomalies and weak configurations. The 2020 Cloud Security Report by Cybersecurity Insiders identified the misconfiguration of cloud platforms as the top security threat, with a lack of qualified staff as the main obstacle to securing these environments. This combination can lead to avoidable breaches if proper security configurations are not implemented.
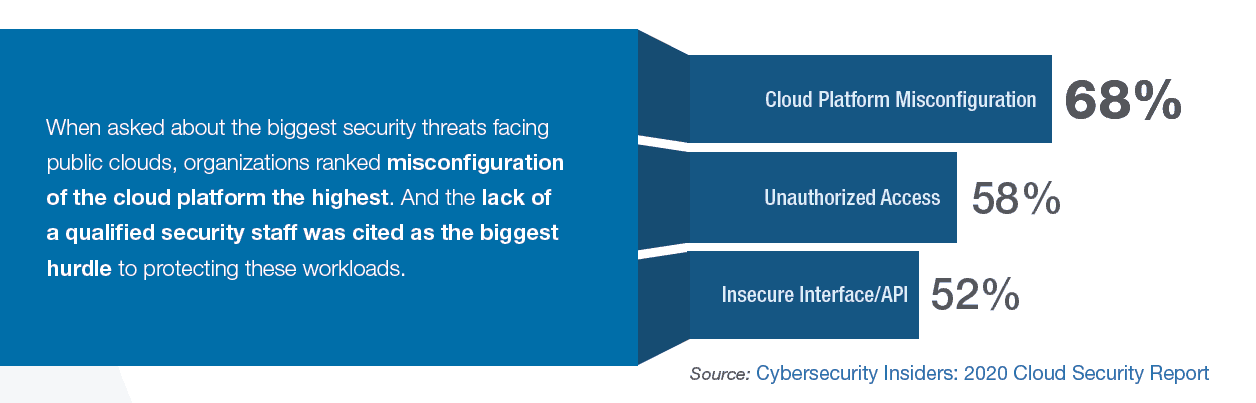
Image Credit: Cybersecurity Insiders
4. Discovery and Inventory
Keeping track of SaaS usage can be a challenge, especially when applications are rapidly deployed. Employ manual data collection techniques along with automation tools to maintain an up-to-date inventory of all services in use and who is using them. Another recommendation would be to either have an in-house or a subscription-model dashboard(s) to holistically monitor, observe and control access throughout the organization to ensure no unauthorized access is allowed.
5. Use of CASB Tools
Sometimes, Cloud Access Security Broker (CASB) solutions can be a powerful addition to your SaaS security arsenal, especially when a SaaS provider does not offer an adequate level of security. CASB allows you to add controls not natively supported by SaaS providers. Most SaaS providers these days, especially larger providers like Salesforce, however, offer add-on options for enhanced security.
6. Situational Awareness
Keeping track of SaaS usage and data from CASB tools, along with data and logs provided by the SaaS provider, can provide valuable insights. Adopting systematic risk management measures ensures that SaaS is used safely and securely. Largely, this plays to an overall organizational culture that is built around security and situational awareness, a key aspect that is often overlooked, especially in smaller organizations.
Leveraging SaaS Security Posture Management (SSPM)
SSPM solutions, like the one offered by Cynet, can greatly enhance SaaS security. SSPM systems monitor SaaS applications continuously, identifying any gaps between stated security policies and the actual security posture. This allows automatic identification and rectification of security risks in SaaS assets, prioritizing risks and misconfigurations by severity.
Conclusion
As the digital landscape continues to evolve and SaaS applications become increasingly prevalent, SaaS security is becoming more crucial than ever. By following these best practices, organizations can secure their SaaS applications effectively, ensuring a safe and robust digital ecosystem. Companies should remember that SaaS security is a shared responsibility between them and their provider, and both must take necessary steps to maintain the integrity and security of the data.
Opinions expressed by DZone contributors are their own.

Comments