Running Mule Application In AWS
This article contains step-by-step information on running the Mule Application in AWS. We will be using complete automation and Terraform to provision AWS resources.
Join the DZone community and get the full member experience.
Join For FreeThis article contains step-by-step information on running the Mule Application in AWS. Here, Terraform will be used for provisioning AWS resources. Terraform code will help to create an EC2 instance with required inbound and outbound rules and a key pair for logging into the instance, then running script that will set up the run time environment for our Mule Application. Mulesoft has a runtime manager, i.e., CloudHub that can be used to deploy or manage the mule application in a more scalable way. Basically, CloudHub is using the AWS EC2 instance that they call workers in CloudHub to run client applications, though it offers really cool features like proxies, SLAs and etc. The purpose of this tutorial is just to show you an alternative way of running Mule application and After deploying to AWS, You will get a public endpoint for your application that can be tested with any rest client.
Requirements
2) AWS access key and secret key
Step-by-Step
Terraform will be used to create an Ubuntu instance containing Mule Standalone server 4.3.0 and then installing the openjdk-8-jdk, Maven, and Mule Standalone runtime on it. Once the environment setup is done then it will copy the application zip file into the apps folder of Mule_HOME.
Now, Create a main.tf file in a folder and append all the below code by changing the AWS credentials, local file key path, and some other changes as described in the Steps.
Step 1: Define your AWS access and secret key in main.tf file, Also the region you want to deploy your application.
x
##################################################################################
# PROVIDERS
##################################################################################
provider "aws" {
access_key = "YOUR_ACCESS_KEY"
secret_key = "YOUR_SECRET_KEY"
region = "ap-south-1"
}
Step 2: A key pair for making a remote connection to your AWS instance for installing the dependencies of the Mule application.
Set the path where you want to store your key in the "local file" resource on line number 17.
xxxxxxxxxx
# creating a key pair
variable "key_name" {}
resource "tls_private_key" "example" {
algorithm = "RSA"
rsa_bits = 4096
}
resource "aws_key_pair" "generated_key" {
key_name = var.key_name
public_key = tls_private_key.example.public_key_openssh
}
# saving key to local file
resource "local_file" "deploy-key" {
content = tls_private_key.example.private_key_pem
filename = "/home/FILE_PATH/tf_key.pem"
}
Step 3: A data source of Ubuntu AMI that will give an image ID which we will use in the instance resource.
x
##################################################################################
# DATA
##################################################################################
data "aws_ami" "ubuntu" {
most_recent = true
filter {
name = "name"
values = ["ubuntu/images/hvm-ssd/ubuntu-xenial-16.04-amd64-server-*"]
}
filter {
name = "virtualization-type"
values = ["hvm"]
}
owners = ["099720109477"] # Canonical
}
Step 4: Now, we will define the inbound and outbound rules for our security group in default VPC but you need to make sure that you should only use that inbound rule same as you configured in the HTTP listener of your mule project.
In my case, the Mule HTTP listener is listening on port number 8081 and port 22 is for SSH[remote login].
x
##################################################################################
# RESOURCES: VPC and Security Group
##################################################################################
#This uses the default VPC. It WILL NOT delete it on destroy.
resource "aws_default_vpc" "default" {
}
resource "aws_security_group" "allow_clients" {
name = "Mule_app"
description = "Allow ports for Mule_app"
vpc_id = aws_default_vpc.default.id
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 8081
to_port = 8081
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = -1
cidr_blocks = ["0.0.0.0/0"]
}
}
Step 5: In this step, The below code will create an AWS instance of size t2.small as Mule Standalone runtime required a minimum of 1 GB of RAM but if you use t2.micro instance then it won't work and you will get an error.
Also, You need to give the path of your project in the source of file provisioner on line number 13.
xxxxxxxxxx
##################################################################################
# RESOURCES: AWS Instance
##################################################################################
resource "aws_instance" "Mule" {
ami = data.aws_ami.ubuntu.id
instance_type = "t2.small"
key_name = aws_key_pair.generated_key.key_name
vpc_security_group_ids = [aws_security_group.allow_clients.id]
provisioner "file" {
source = "/home/YOUR_PROJECT_PATH/test.jar"
destination = "/home/ubuntu/test.jar"
connection {
type = "ssh"
user = "ubuntu"
private_key = tls_private_key.example.private_key_pem
host = self.public_dns
}
}
provisioner "remote-exec" {
inline = [
"export MULE_HOME=/opt/mule",
"export MULE_VERSION=4.3.0",
"sudo apt-get -y update",
"sudo apt-get -y install maven",
"sudo apt-get -y install openjdk-8-jdk",
"cd /opt",
"sudo curl -k -o mule-4.3.0.zip http://s3.amazonaws.com/new-mule-artifacts/mule-ee-distribution-standalone-4.3.0-20210119.zip",
"sudo apt -y install unzip",
"sudo unzip mule-4.3.0.zip",
"sudo mv mule-enterprise-standalone-$MULE_VERSION-20210119 mule",
"sudo mv /home/ubuntu/* /opt/mule/apps/",
"sudo /opt/mule/bin/mule start"
]
connection {
type = "ssh"
host = self.public_dns
user = "ubuntu"
private_key = tls_private_key.example.private_key_pem
}
}
tags = {
Name = "terraform-mule"
}
}
Step 6: Use the public DNS to access your mule application by specifying the port and resource that you used in your mule project.
x
##################################################################################
# OUTPUT
##################################################################################
output "aws_instance_public_dns" {
value = aws_instance.Mule.public_dns
}
Once you put all the code in main.tf file then you need to run a few terraform commands to deploy your application on AWS EC2.
Initialize Terraform Directory
When you create a new configuration then you need to initialize the directory with terraform init.
It will download all the terraform dependencies of the project in .terraform folder.
$ terraform init Initializing the backend... Initializing provider plugins... - Reusing previous version of hashicorp/aws from the dependency lock file - Reusing previous version of hashicorp/tls from the dependency lock file - Reusing previous version of hashicorp/local from the dependency lock file - Installing hashicorp/aws v3.37.0...
Create Application Infrastructure
Run terraform apply in the same directory as the main.tf file you created, You should see an output similar to the one shown below.
Note: Terraform 0.11 and earlier versions require running terraform plan before terraform apply. You can use terraform version to confirm your running version.
Note: You can use this command terraform apply --auto-approve. If you do not want to see the actions below or if you are sure what changes Terraform is going to make to your AWS account.
$ terraform apply
var.key_name
Enter a value: mule
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# aws_default_vpc.default will be created
+ resource "aws_default_vpc" "default" {
+ arn = (known after apply)
+ assign_generated_ipv6_cidr_block = (known after apply)
+ cidr_block = (known after apply)
+ default_network_acl_id = (known after apply)
+ default_route_table_id = (known after apply)
+ default_security_group_id = (known after apply)
+ dhcp_options_id = (known after apply)
+ enable_classiclink = (known after apply)
+ enable_classiclink_dns_support = (known after apply)
+ enable_dns_hostnames = (known after apply)
+ enable_dns_support = true
+ id = (known after apply)
+ instance_tenancy = (known after apply)
+ ipv6_association_id = (known after apply)
+ ipv6_cidr_block = (known after apply)
+ main_route_table_id = (known after apply)
+ owner_id = (known after apply)
+ tags_all = (known after apply)
}
{.............................
...................}
Plan: 6 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
After completing the provisioning, You will get a public dns as an output:
Outputs: aws_instance_public_dns = "ec2-52-66-199-206.ap-south-1.compute.amazonaws.com"
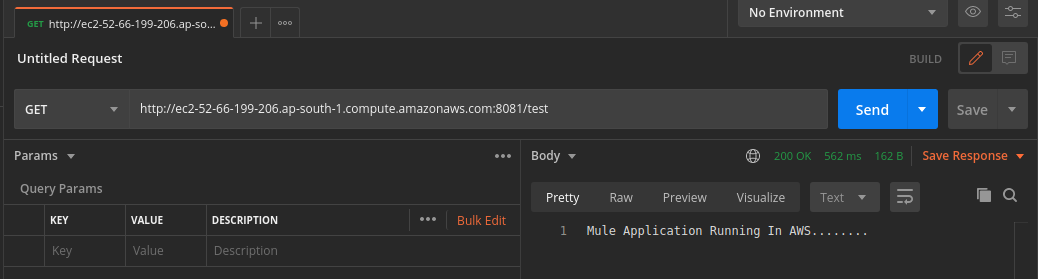
Testing Mule Application
Test your Application by hitting the URL on the postman.
Note: My application is running on port 8081 with resource name test.
Hope this helps!
Thanks.
Keep learning.
Opinions expressed by DZone contributors are their own.

Comments