Preventing Account Takeover Through Open and Centralized Compromised Credential Index
Account Takeover frauds cause billions of dollars to people and companies. An open security standard could prevent this across software applications.
Join the DZone community and get the full member experience.
Join For FreeImagine if your car is parked in your driveway and someone tries to break into it and you catch that on your doorbell camera. The first thing you do is to alert your neighbors to make sure their cars are safe. This fairly common and safe practice is missing when it comes to online fraud where identity theft is rampant. This article proposes a possible solution to address this problem.
The Problem
Account Takeover (ATO) is a type of identity theft that occurs when a hacker uses social engineering to learn a user’s credentials and gains unauthorized access to someone’s online account for personal financial gain. According to Hacker News, ”A whopping 20 billion records were stolen in a single year, increasing 66% from 12 billion in 2019. Incredibly, this is a 9x increase from the comparatively 'small' amount of 2.3 billion records stolen in 2018.” Businesses also run the risk of being blocked by payment gateways such as Visa when high levels of fraudulent payment activity are detected on their platform. This often costs them millions of dollars in reimbursing the users and implementing measures to prevent fraud.
When the user learns of this theft, they take corrective measures by either resetting the password or contacting customer support, who will help them recover their account. Today, the story ends there.
It is fairly common practice for many internet users to re-use their login credentials across different applications. So when a set of credentials is compromised on an application, it is highly likely that the accounts on multiple applications are also compromised. A potential solution to this problem is to use password managers to generate and store passwords for different applications. However, this comes with additional overhead on the part of the user. Losing the password to the password manager itself will result in more overhead of resetting passwords across all different applications.
Possible Solution
A server-side solution to this problem could potentially alleviate this issue and prevent account takeovers across multiple applications. In this solution, a centralized index of compromised credentials (CICC) can be maintained. Different software applications can utilize this database to protect themselves against account takeover. Whenever a participating application processes a login request, it can look up the CICC to verify that the credentials are not compromised. If it finds that the credentials are indeed compromised, it can force the user into a two-factor authentication mechanism via text or mobile notification and make the user aware of the account takeover attempt so that they can take preventive measures before a hacker can exploit their account.
Here is an example of how this could play out:
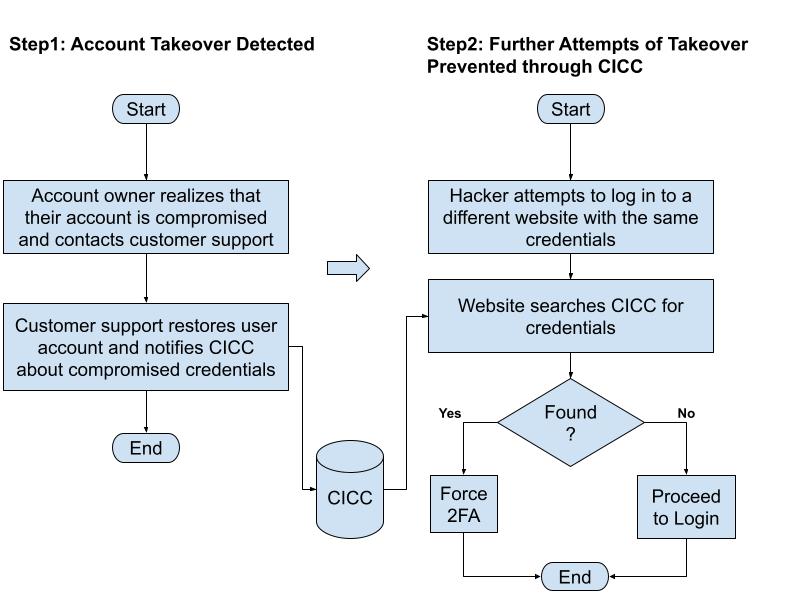
Step 1: Detection
A fraudster social engineers a user's login credentials for a software application and makes a purchase using the saved credit card information on the application. The user learns about the fraud from their credit card transaction report and reports the issue. Customer support reimburses the user and flags the credential compromise to CCIC.
Step 2: Prevention of a Repeat Occurrence
The fraudster attempts to log into a different software application using the same credentials. The application looks up CCIC and learns that it is compromised and challenges the fraudster with a second-factor authentication (one-time-password, verification code, mobile notification, etc.), preventing them from further exploitation.
Existing Solutions
Each major software application (Google, Facebook, etc.) has existing solutions to prevent ATO within the realm of their services through different two-factor authentication mechanisms. However, none exist across software applications.
A few for-profit cybersecurity firms implement this across their client network. However, this solution only extends the protection against account takeover to the cybersecurity firm’s client network.
Potential Future
A not-for-profit, centralized service-compromised credentials database must be created that is to be used by all software applications. This is akin to all websites using SSL (Secure Sockets Layer) to secure user data in flight. All software applications onboard to this service a tenant and pay their share of rent based on how frequently they use the service. The cost of maintenance is also to be borne by the participating applications prorated by their usage. It is important that this is not-for-profit because the true power of such a centralized service lies in the breadth of exposure to fraud it gains for itself through participating applications. A for-profit service will naturally attract competition, which leads to a fragmented dataset of compromised credentials, thereby reducing its effectiveness in detecting and preventing fraud.
In future iterations, this service can further advance in providing a deeper level of security by recording a hacker’s IP address and device information whenever it successfully identifies a fraudulent login activity. If the same IP address or device information is used to log in to different applications using multiple sets of credentials, each application can challenge each login attempt by the hacker with a two-factor authentication after querying the centralized service. This will prevent the hacker from not only exploiting different accounts of a given user but will also prevent them from exploiting any compromised accounts with the devices they own.
This service can further evolve to analyze the patterns employed by hackers through the help of machine learning and prevent takeovers much earlier.
Conclusion
While cybersecurity and IAM experts have many defensive mechanisms in place today to prevent hackers from gaining unauthorized access to their users' accounts such as limiting the number of login attempts per day and two-factor authentication, these mechanisms are mostly performed before a login event. Post-login identity security measures to detect, track, and prevent repeat offenses by a hacker that has managed to break through pre-login defenses are largely lacking in the digital realm. Implementing solutions such as the one mentioned in this article will enable cybersecurity and IAM experts to extend the cyber safety net beyond the current boundaries.
Opinions expressed by DZone contributors are their own.

Comments