PGP Encryption and Decryption With Mule ESB
PGP security encryption protects sensitive information in emails, files, directories, and more. Learn how to encrypt and decrypt with PGP in Mule ESB.
Join the DZone community and get the full member experience.
Join For Free1.0 Overview
PGP (Pretty Good Privacy) encryption is used for encrypting, signing, and decrypting data like emails, text, files, directories, and whole disk partitions. It also increases the security of email communication and it can be used to authenticate digital certificates. Public and private keys play a vital role in PGP to encrypt and decrypt the data. Generally, a public key is used to encrypt the data and it is always shared with end users. The private key is used to decrypt the data and it is never shared with anyone.
2.0 How Does PGP Work?
The process of converting plaintext into ciphertext is known as encryption, and converting ciphertext into plaintext is known as decryption. Ciphertext is nothing but unreadable gibberish.
Encrypting an entire message can be time-consuming. PGP uses a faster encryption algorithm to encrypt the messages and then uses the public key to encrypt the shorter key that was used to encrypt the entire message. Both the encrypted data and the short key are sent to the receiver, who first uses the receiver's private key to decrypt the short key and then uses that key to decrypt the message.
For example, Alice will use the public key to encrypt the data and send it to Bob. Now, Bob will decrypt the data using the private key.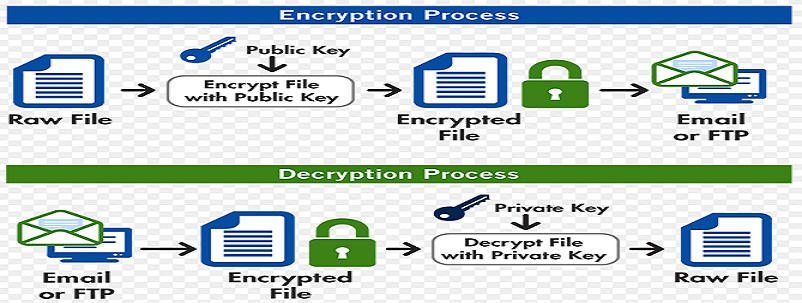
3.0 Advantages of PGP Security
Sensitive information can be protected; others cannot view it and cannot be stolen over the internet.
Information can be shared securely within a group of users or company departments.
Files are compressed to a smaller size before being sent over the network.
There is no need to purchase private key or certificates.
Secure mail and text cannot be infiltrated by hackers or infected and misused through email attacks.
Future-proof technology and complete compatibility with other applications.
In-built key manager to securely manage yours and others' keys.
Provides absolute assurance that data receives or sent has not been modified in transit.
Provides protection against viruses and the newest blended email threat.
4.0 Generating Private and Public Keys
There are many tools available to generate PGP private and public keys. In this article, we will use Kleopatra to generate the private and public keys.
4.1 Generate the Private and Public Keys
Go to File > New Certificate > Create a personal OpenPGP key pair.
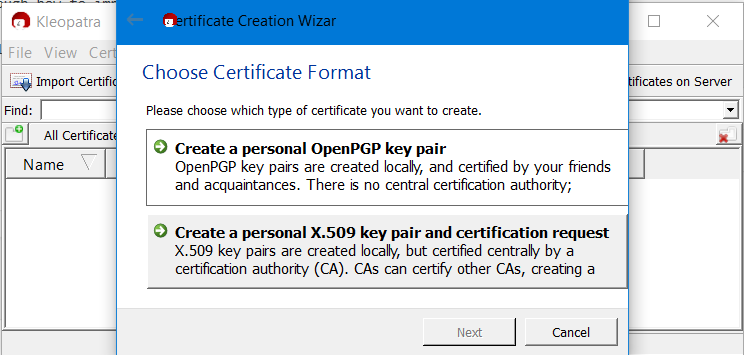 Provide Name and Email in the mandatory fields.
Provide Name and Email in the mandatory fields.
Click Next and Create Key. Provide a Passphrase and don’t forget the passphrase. Finally, clicked on Finish. It will generate a public key and private key.
4.2 Exporting the Public Key
Right click on the certificate and Export Certificates. Save the public key in .gpg format to some folder location on your disk.
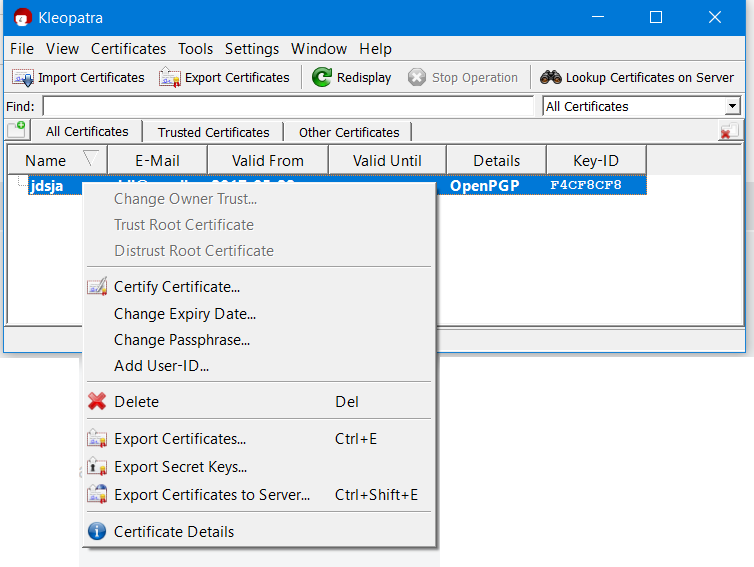
4.3 Exporting the Secret (Private) Key
Right click on the certificate and Export Secret Keys. Save the private or secret key in .gpg format to some folder location on your disk.
5.0 Implementing PGP With Mule ESB
Mule ESB provides PGP Security as part of its Enterprise Security. By default, Enterprise Security is not part of Anypoint Studio. You can download and install Enterprise Security using Anypoint Studio.
5.1 PGP Encryption
Place the File Connector in the message source region and configure it. Drag and drop the encryption component in the message processor region. Encryption is part of Enterprise Security.
Configure the encryption component. First, click on the plus sign to do the connector configuration. Under the General tab, select the default Encrypter as PGP_Encrypter.
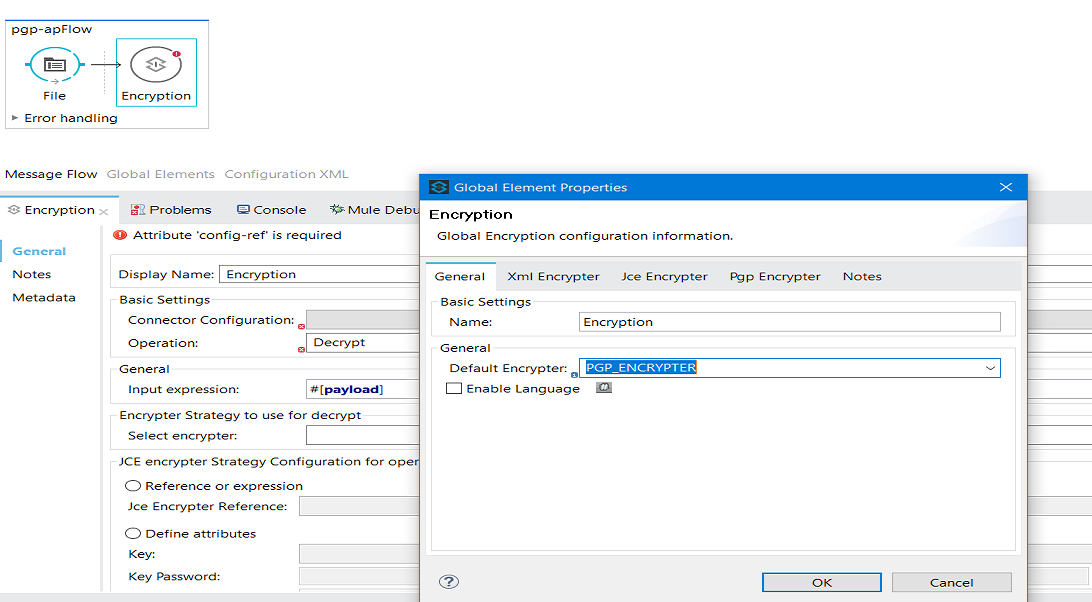
Now go to the PGP Encrypter tab and select the radio button to define attributes.
Provide a Public Key Ring File Name (public key path), Secret Key Ring File Name (private key path), the Passphrase that you provided while generating the certificate, the Principal (a combination of your name and email you provided while generating the certificate, e.g. jdsja <sjdj@gmail.com>), and Secret Alias Id. It's a bit tricky as it is not provided while generating the certificate, so provide some dummy value.
Whenever you deploy the application, it will fail and you can see the available Secret Alias Id in the error logs. Configure correct Secret Alias Id and deploy it again.
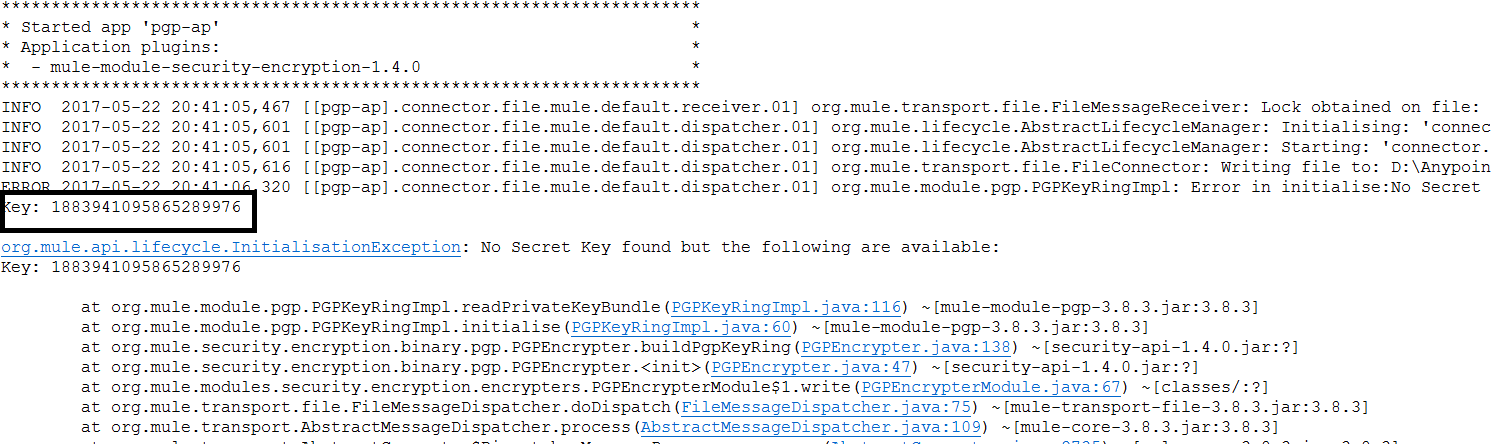 Make sure you have copied the private key and public key in your application folder src/main/resources.
Make sure you have copied the private key and public key in your application folder src/main/resources.
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns:encryption="http://www.mulesoft.org/schema/mule/encryption" xmlns:file="http://www.mulesoft.org/schema/mule/file" xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation"
xmlns:spring="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans-current.xsd
http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/file http://www.mulesoft.org/schema/mule/file/current/mule-file.xsd
http://www.mulesoft.org/schema/mule/encryption http://www.mulesoft.org/schema/mule/encryption/current/mule-encryption.xsd">
<encryption:config name="Encryption" defaultEncrypter="PGP_ENCRYPTER" doc:name="Encryption">
<encryption:pgp-encrypter-config publicKeyRingFileName="F:\Mulesoft\Anypoint_Latest\workspace\pgp-encrypt\src\main\resources\0DEBD68E4D53984A525DB7911A251A71F4CF8CF8.gpg" secretKeyRingFileName="F:\Mulesoft\Anypoint_Latest\workspace\pgp-encrypt\src\main\resources\privatekey.gpg" secretAliasId="00320083882388" secretPassphrase="123456789" principal="jdsja <sjdj@gmail.com>"/>
</encryption:config>
<flow name="pgp-encryptFlow">
<file:inbound-endpoint responseTimeout="10000" doc:name="File" path="src/test/resources/in"/>
<encryption:encrypt config-ref="Encryption" using="PGP_ENCRYPTER" doc:name="Encryption">
<encryption:pgp-encrypter principal="jdsja <sjdj@gmail.com>"/>
</encryption:encrypt>
<file:outbound-endpoint path="src/test/resources/out" responseTimeout="10000" doc:name="File"/>
</flow>
</mule>
5.2 PGP Decryption
To decrypt the data, you have a similar configuration and just change the operation to Decrypt.
<?xml version="1.0" encoding="UTF-8"?>
<mule xmlns:encryption="http://www.mulesoft.org/schema/mule/encryption" xmlns:file="http://www.mulesoft.org/schema/mule/file" xmlns="http://www.mulesoft.org/schema/mule/core" xmlns:doc="http://www.mulesoft.org/schema/mule/documentation"
xmlns:spring="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans-current.xsd
http://www.mulesoft.org/schema/mule/core http://www.mulesoft.org/schema/mule/core/current/mule.xsd
http://www.mulesoft.org/schema/mule/file http://www.mulesoft.org/schema/mule/file/current/mule-file.xsd
http://www.mulesoft.org/schema/mule/encryption http://www.mulesoft.org/schema/mule/encryption/current/mule-encryption.xsd">
<encryption:config name="Encryption" defaultEncrypter="PGP_ENCRYPTER" doc:name="Encryption">
<encryption:pgp-encrypter-config publicKeyRingFileName="F:\Mulesoft\Anypoint_Latest\workspace\pgp-encrypt\src\main\resources\0DEBD68E4D53984A525DB7911A251A71F4CF8CF8.gpg" secretKeyRingFileName="F:\Mulesoft\Anypoint_Latest\workspace\pgp-encrypt\src\main\resources\privatekey.gpg" secretAliasId="00320083882388" secretPassphrase="123456789" principal="jdsja <sjdj@gmail.com>"/>
</encryption:config>
<flow name="pgp-encryptFlow">
<file:inbound-endpoint responseTimeout="10000" doc:name="File" path="src/test/resources/in"/>
<encryption:decrypt config-ref="Encryption" using="PGP_ENCRYPTER" doc:name="Encryption">
<encryption:pgp-encrypter principal="jdsja <sjdj@gmail.com>"/>
</encryption:decrypt>
<file:outbound-endpoint path="src/test/resources/out" responseTimeout="10000" doc:name="File"/>
</flow>
</mule>
6.0 PGP Encryption and Decryption With Mule ESB [Video]
7.0 Conclusion
PGP security is widely used for securing the sensitive data in emails, documents, and files; it secures the information from various cyber threats or hackers when sending data over the network. PGP doesn't just secure your data, it also compresses the data while sending it over the network. Mule ESB has added PGP as a part of Enterprise Security and it is very easy to implement PGP security within the Mule flow. PGP security in Mule ESB can be achieved by doing some configuration as has been discussed in the above article.
Now you know how easy to implement PGP encryption and decryption with Mule ESB.
Opinions expressed by DZone contributors are their own.

Comments