Hiding Application Properties in CloudHub
Keep your application properties safe with CloudHub.
Join the DZone community and get the full member experience.
Join For Free
Introduction
In CloudHub, for application deployment, we normally have requirements to hide or encrypt properties. It completely depends on your preference. CloudHub resolves the properties at runtime without exposing sensitive information.
Encryption of Mule application properties is another feature and one of the easiest ways to secure sensitive information.
Concept
Application properties are variables that act as placeholders in our Mule application and are set at runtime. When we deploy an application or update an existing application in the Runtime Manager console, Mule's runtime engine supplies the values for the property variables in the Runtime Manager console’s Properties tab.
You may also like: CloudHub Connector With Mulesoft.
Use Case
When someone needs to update an encrypted value, the Runtime Manager console does not have access to the secret key, so it is impossible to replace an encrypted value with a new encrypted value without changing source files and regenerating new, encrypted value. This process can quickly become cumbersome from a maintenance perspective.
Solution
The above problem can be eliminated by using this approach. This is another feature to secure the sensitive information in Mule by listing the application properties as secured properties. Once application properties are marked as secured properties in the Mule's app properties, then values will be hidden in the Runtime Manager just like encrypted properties. Also, one can safely replace the value with the new value in clear text without encrypting them.
Let's consider a simple example: We can configure a JDBC connector where the username is set to ${dbUsername}, and the password is set to ${dbPassword}. In the Runtime Manager console, you can set these two properties as application properties, as shown below.
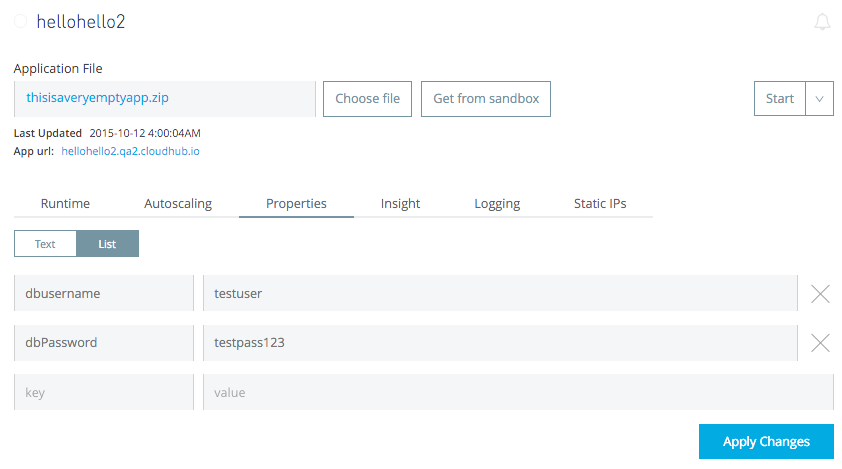
For sensitive information, we can flag these properties as hidden so that, after they are entered and saved in the Runtime Manager console, their values are neither visible in the console nor passed between the console and the CloudHub server.
Create Hidden Application Properties
Note: This tutorial will run on Mule 4.0 and later versions (at the time of writing).
Suppose you have the following properties in your application:
username: "Manish"
password: "testpass123"
birthdate: "01/01/2015"Now, in Mule application’s mule-artifact.json file, list the property names that you wish to safely hide under the secureProperties key as a comma-separated array. Here, we have to the hide password and birthdate.
{
"minMuleVersion": "4.2.1",
"secureProperties": ["password", "birthdate"]
}In Mule 3: We can place the properties in the mule-app.properties file under the secure.properties key
name=Manish
password=mypassword
birthdate=01/01/2015
secure.properties=password,birthdateOnce you are done with configurational changes, you can deploy the Mule application to CloudHub. We can enter our application properties after deployment.
Once you commit your deployment or update and your application is deployed, navigate to the Deployment tab and check the application properties. The values for all properties that you marked as safely hidden are now no longer visible to you or any other user.
In the example below, birthdate and password are safely hidden, but username is not.
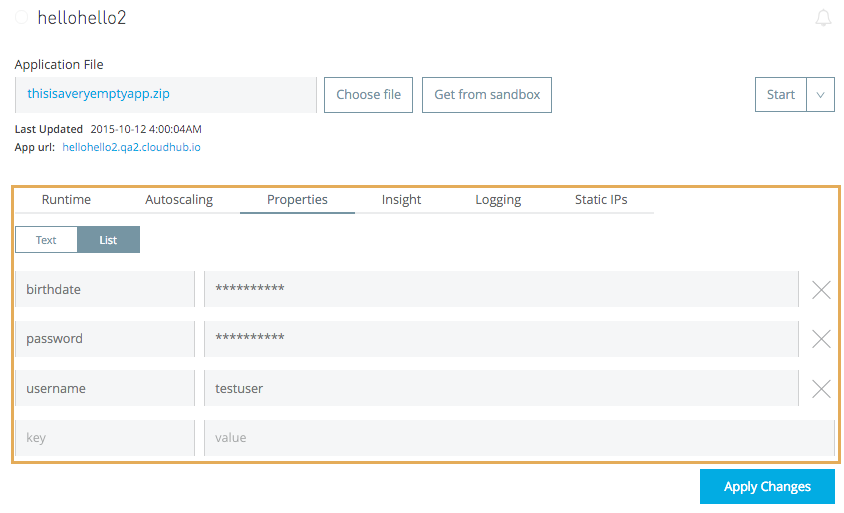
However, it can be overwritten with a new value. To safely pass the secret key into the Mule application, develop the Mule application with a property placeholder to represent the secret key value.
Encrypted Application Properties vs Safely Hidden Application Properties
Secure properties are encrypted using a secret key. It is recommended to never store the secret key inside your applications. Instead, we can safely pass in the secret key value at deployment time.
Mule applications, which are deployed in CloudHub, may not need to encrypt the properties. Instead, just use those properties as secured properties.
If we need to update the value, then one can directly enter the new value in the clear text.
Migrating the application from one environment to another, safely hidden application properties will not get copied to the new environment.
Bonus
Any encrypted property that is also marked as hidden in the Mule application’s secureProperties entry, you can safely replace any encrypted property with a clear-text value. This means that when you override a secure property in the CloudHub Properties tab for the application, the value doesn’t need to be encrypted.
Use the list view in the application’s Properties tab to update properties. If you use the text view to update properties, colons in property names must be escaped (for example: secure\:\:yourproperty).
Happy learning :)
Further Reading
Opinions expressed by DZone contributors are their own.

Comments