Mulesoft Code Review Automation Using SonarQube
The code review process is very critical for project success and below are some pointers on why one should include a code review process.
Join the DZone community and get the full member experience.
Join For FreeThe code review process is very critical for project success and below are some pointers on why one should include a code review process:
- Consistent design and implementation
- Minimizing your mistakes and their impact
- Ensuring project quality and meeting requirements
- Improving code performance
- Sharing new techniques
SonarQube
SonarQube is an open-source code review tool for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on various programming languages.
Each language plugin comes with a predefined, built-in profile (called “Sonar way”) having a set of predefined rules and it will be used as a default profile during analysis for projects. We can create our Profile and add rules to it.
Sonar Installation
Install the latest SonarQube distribution, use SonarQube 7.7.
Start the SonarQube server: StartSonar.bat
Log in to http://localhost:9000 with administrator credentials (admin/admin).
Configuration
Setting Rules
SonarQube analyzes the code against the rules added to the active profile.
As MuleSoft codes are written in XML, the focus in this article will be on XML rules and Xpath expressions.
To add a rule follow the below steps:
- Log in as a Quality Profile Administrator and go to the rule page
- Select XML Language to create the XPath rule
- Select Template criterion and click on "Show Templates Only"
- Add XPath rules in “Track breaches of an XPath rule” template:
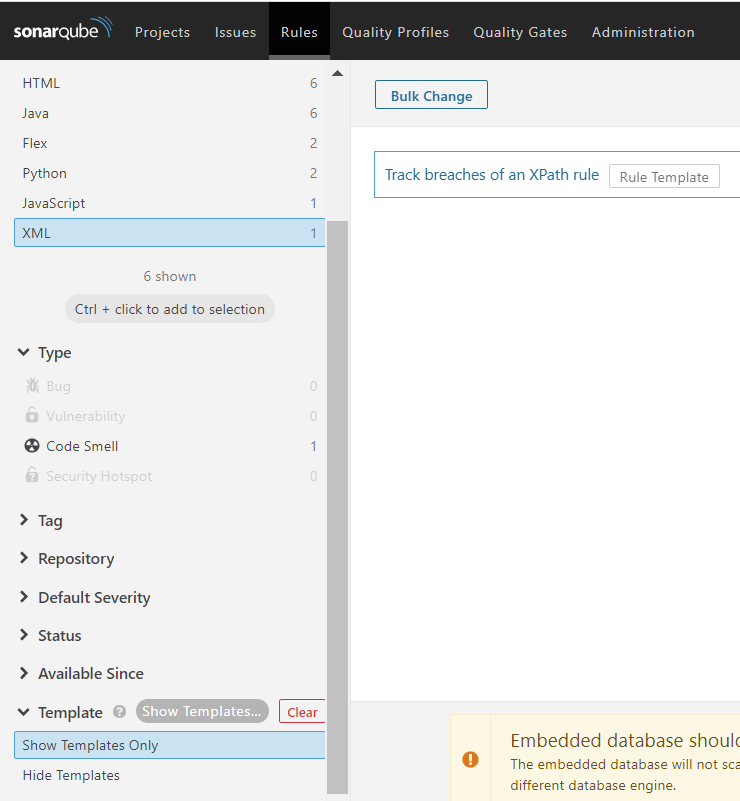
- Create a custom rule:
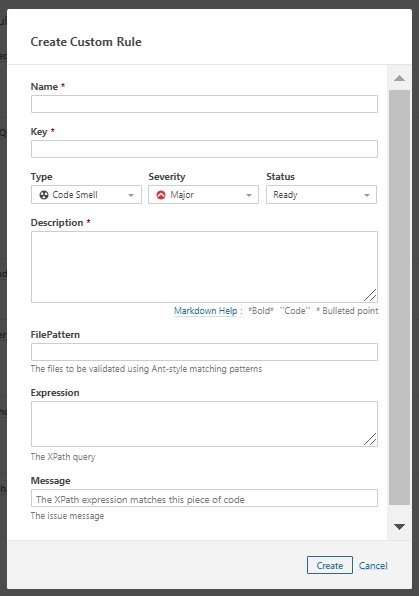
- Write the XPath query in the expression tab (it should comply to XPath 1.0)
- Activate the recently added rule by clicking on XML (Sonar way) in the Quality Profile and run an analysis.
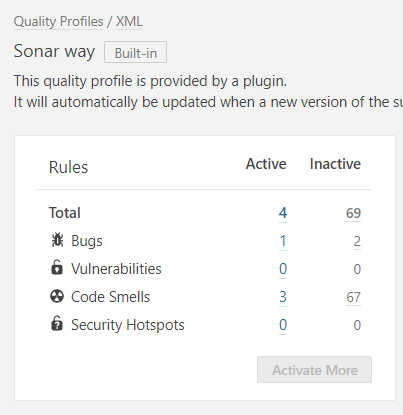
- Click on the activate more button to activate specific rules.
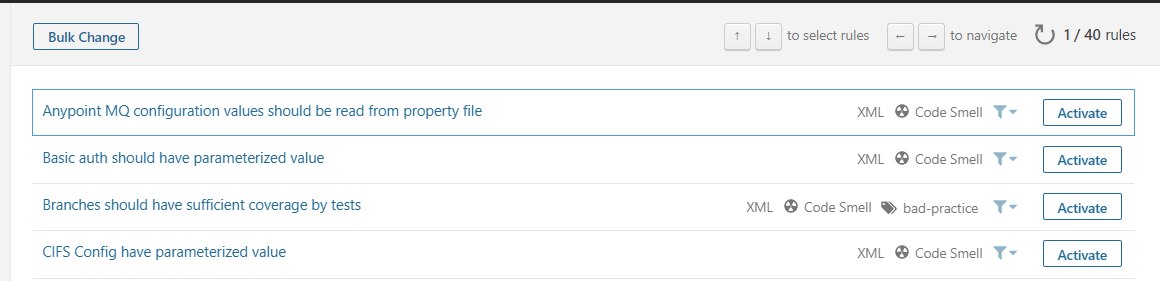
Quality Gates
A quality gate is a set of conditions and a set of projects to be checked against these conditions. It can be defined as a set of threshold measures set on your project like Code Coverage, Technical Debt Measure, Number of Blockers/Critical issues, Security Rating/ Unit Test Pass Rate, and more.
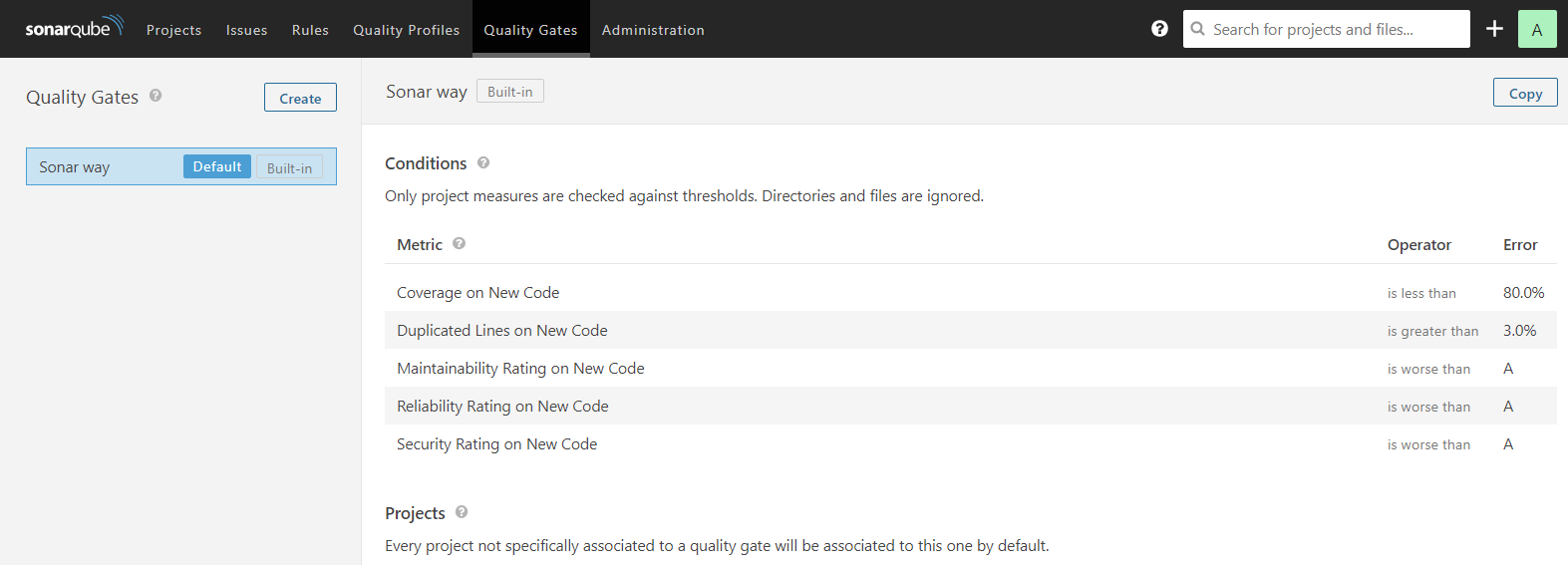
Based on your projects, you can set up the metrics in your Quality Gate to explicitly throw a Warning or Error when the code crosses a threshold.
Mule 4 Application Rules
The below Xpath rules will give a brief idea of how one can write rules for a Mule 4 application:
Validate re-connection strategy for HTTP Requester
Expression:
//*[local-name()='request-connection' and
namespace-uri()='http://www.mulesoft.org/schema/mule/http']
[not(*[local-name()='reconnection'])]
Below is the highlighted element used with local-name() function:
<http:request-connection host="${https.requestor.host}" port="${https.requestor.port}" connectionIdleTimeout="${https.requestor.timeout.connection}" protocol="HTTPS" usePersistentConnections="false">
<reconnection>
<reconnect frequency="${https.requestor.reconnection.frequency}" count="${https.requestor.reconnection.attempts}" />
</reconnection>
</http:request-connection>
- No Exception Strategy set
Expression:
filePattern: **/*error.xml
Expression : not(/*/error-handler)
Below is the highlighted element used:
<error-handler name="errorError_Handler"
doc:id="68f0db07-a3ea-4f1e-a4a5-83a45c22ee28"/>
Once you create all rules, you can add them to the SonarQube as explained in the “Setting Rules” step.
Mule Project Code Review Automation
Add below profile in settings.xml in maven/conf/settings.xml
xxxxxxxxxx
<profile>
<id>sonar</id>
<activation>
<activeByDefault>true</activeByDefault>
</activation>
<properties>
<sonar.host.url>http://localhost:9000</sonar.host.url>
<sonar.sources>src/main/mule,src/main/resources,pom.xml</sonar.sources>
</properties>
</profile>
<activeProfiles>
<activeProfile>sonar</activeProfile>
</activeProfiles>
Run the below command to generate a sonar report
mvn clean sonar:sonar -Dsonar.login=username
-Dsonar.password=password
(default username:password is admin:admin)
Report Generation
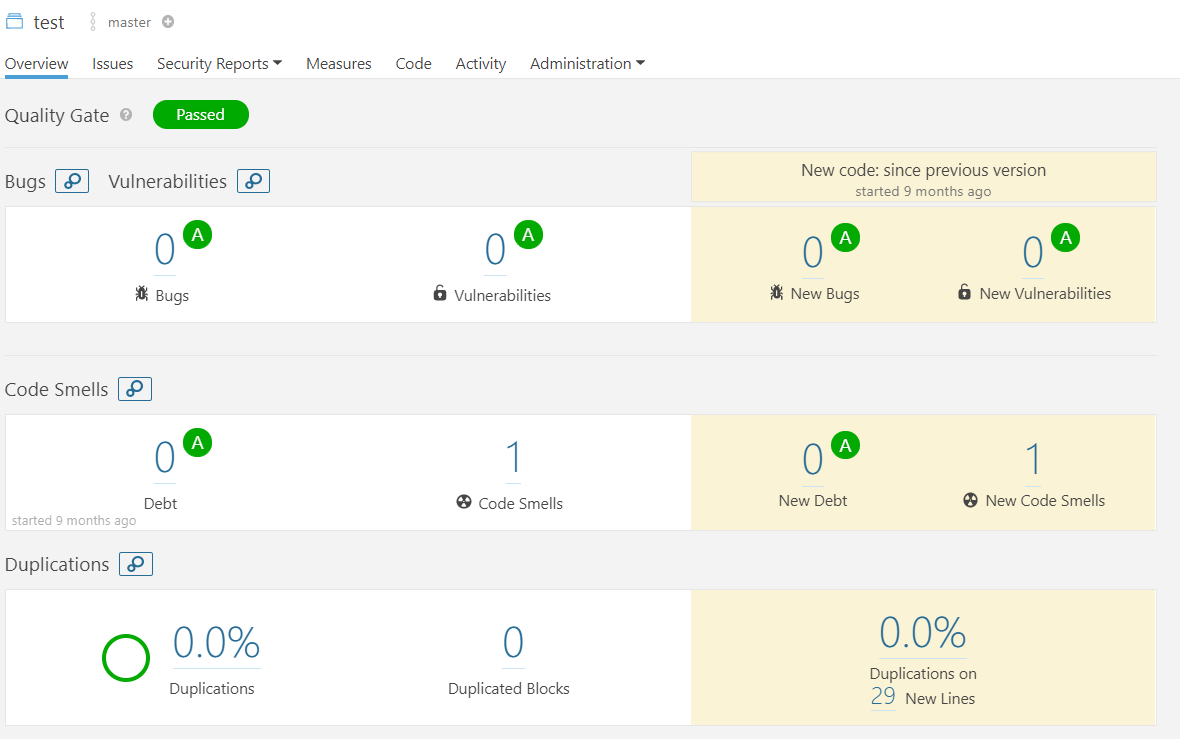
- Once the analysis is complete, you can log in to the SonarQube GUI to check the project snapshot as shown in the image below.
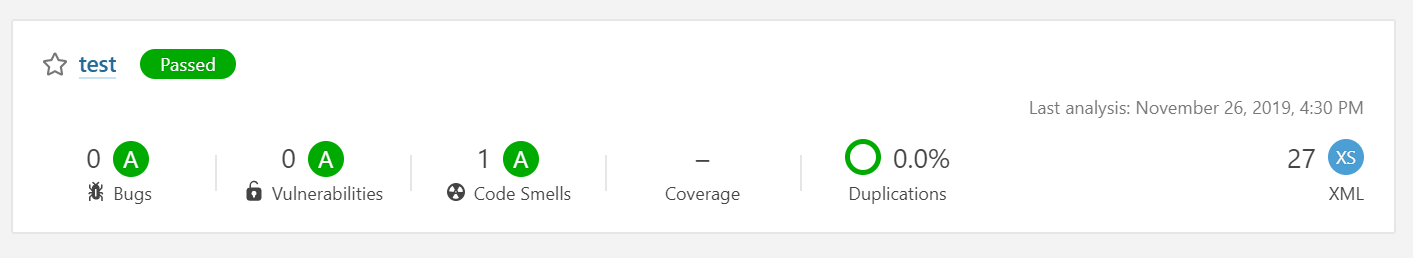
- Click on the project name to go to the Project overview page
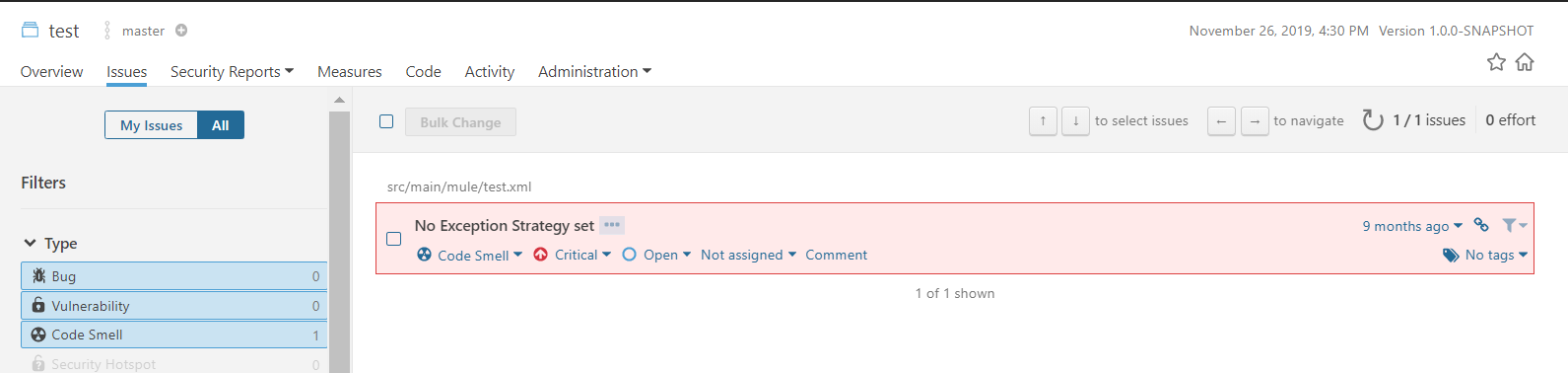
- Click on the Issues tab to look at all the code violations in the project(s) scanned. As shown in the image below, each issue has description with a recommendation to fix, followed by Activity/Path where the issue occurred along with the configuration name/value where the issue occurred.
Conclusion
Automating the code review process reduces the delivery time and human error and SonarQube is a good fit for the Mulesoft Automated Code Review tool as it sets a collection of rules to analyze your source code at compile time to identify potential vulnerabilities, bugs, anti-patterns, refactoring, and poor coding practices.
Opinions expressed by DZone contributors are their own.

Comments