Location Privacy: What and Why?
Growing usage of location-based services requires investment to build an ecosystem of trust and transparency with users and service providers. Learn more here.
Join the DZone community and get the full member experience.
Join For FreeWith modern GPS-aware devices, location data is widely collected and used for applications like traffic monitoring, route planning, friend-finding, advertisement deals, emergency services, etc. Location Based Service (LBS) is a service that is offered to users based on their location information. It is a convergence of technologies such as smartphones, the internet, and GIS that makes LBS possible. It is accessed by users from their mobile device, through the mobile internet available on the device while sharing their geographical location (and other required information) with the service provider.
The quality of service provided by the LBS depends on the type of service, underlying architecture, and the accuracy of the data collected. Highly precise data is collected for location-based services, which is either a single location update or continuous location updates depending on the kind of service. Analysis of such highly precise spatiotemporal data, when collected over an interval of time, can lead to the identification of individuals, estimation of trajectories (identification of popular source/destination points), and eventually their behavior. A lot of information about a person’s beliefs, preferences, religion, and health can be inferred by analyzing the location data.
For example:
- It could be determined that an individual visits a doctor (hospital) for how long and with what frequency. This information can be used by insurance providers to discriminate or force higher premiums.
- The location of an individual’s home, office, friends, and family can be used by people with harmful intent to follow his or her activities and send personal threats.
- Identification of the location of stores/shopping centers an individual visits can lead to the identification of his or her shopping frequency/pattern and can also indicate socioeconomic status.
Location privacy is the ability of an individual to control the access of his current or past location information. It is the right of an individual or group to control when, how and how much of their personal location data is being shared or revealed to a third party (Krumm et al, Kulik et al).
The loss of location privacy can lead to the following type of issues:
- Inference Attacks: An individual’s location can be linked together to make a range of inferences about his political views, religion, sexuality, friends, and family. This information can be used to influence, target, or threaten them.
- Location-based advertising (LBA) is to spam an individual with offers depending on the physical location collected using mobile phones. LBA can not only irritate the mobile user with useless messages but also disrupt his relationship with his surroundings (Wicker et al).
- Threats to personal safety: Stalking or physical attacks
Challenges
The challenges to implementing location privacy are:
- Location privacy requirements: The location privacy requirements differ for individuals based on their understanding and need for the same. It also varies for the same user at different places and at different times.
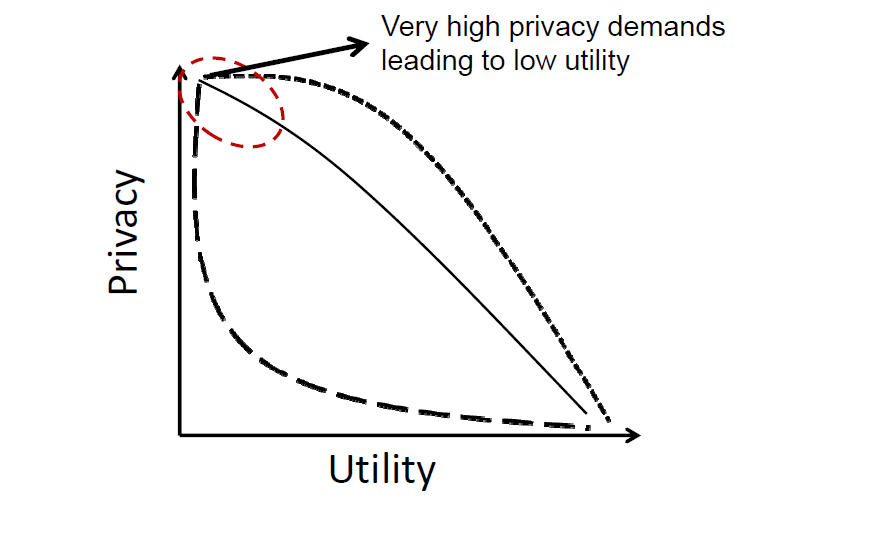
- Privacy vs utility trade-off: Location information is useful for providing and enhancing services while unauthorized access to such information can reveal a lot of sensitive information about an individual. The best quality of services that can be achieved for a required level of privacy is also application dependent.
Phases of Location Data Extraction
There the three phases of location information extraction:
1. Data Collection
Location data is collected by a service provider or organization. For example, when you request a routing service, your current location keeps getting updated to the service provider.
2. Data Analysis
These location updates can be collected and analyzed to enhance the service or for data mining purposes. For example, the route-finding service collects the historical movement data of an individual and uses that to determine his driving behavior to suggest personalized routes in the future.
3. Data Publishing
The collected data or some statistics of the data can be published and that should not leak an individual’s private information.
User’s Privacy Goals
Also, the privacy goals may vary by the selection of the model and implementation technique.
Users could require:
- User location privacy: Users want to hide their location information and in most cases, the query content.
- User query privacy: Users want to hide their query content, but revealing location information is not a concern (i.e., a query regarding the nearest bar location).
- Trajectory privacy: Users want to avoid revealing enough information (Spatio-temporal points) that can be linked together to form a trajectory.
Methods for Ensuring Location Privacy
Other than privacy laws and policies, the methods for ensuring location privacy are as follows.
Anonymity
Anonymity is when the location information is separated from the identity of the user.
Pseudoanonymity
One of the simplest techniques to achieve anonymity would be to replace the user ID with a pseudonym, thereby separating the identity from the location information. An individual is therefore anonymous but has a persistent identity. However, in the case of location data, pseudonymity does not work, as the pseudonyms can be linked for location information. This could be reverse geo-coded to infer the identity of the user (identity inferred over a period of time from home/work locations).
Cloaking (Spatial and Temporal)
An important technique for anonymization is cloaking which could be spatial or Spatio-temporal. In spatial cloaking, the user location is represented as a bigger region that includes the exact user location. Temporal cloaking reduces the frequency of temporal information by delaying a query until enough users are present in the region (Gruteser et al). However, anonymity-based approaches do not work for applications that require authentication or offer personalization (Langheinrich et al).
Obfuscation
Location obfuscation is defined as the deliberate degradation of the quality of location information (by being imprecise, inaccurate, or vague) in order to protect an individual’s location privacy. Location obfuscation is complementary to the concept of anonymity. Unlike anonymity-based techniques where the identity is anonymized and the user is "one in many," in obfuscation-based techniques, the user identity is known, and the quality of location information is degraded (Kulik et al).
Imprecision
Imprecision is when the user location information is imprecise, as instead of providing a single location, the user provides a bigger set that includes the user location.
Inaccuracy
This is defined when the user location information is not present in the location information set provided to the service provider. The greater the distance of the user’s real location to this set, the higher the achieved level of privacy.
Vagueness
A user’s description of the location information is vague such that exact boundaries are not defined; for example, the use of phrases such as "near-far," "close," and "within five minutes of walking" to describe a location.
System Architectures for Location Privacy
Different system architectures can be applied to implement a privacy-preserving LBS using the location of privacy methods described above. Below are discussed the issues of obtaining high quality of service and anonymization for different system architectures for privacy-preserving LBS.
Client Server Architecture
This is the centralized architecture where the users communicate directly with the server. There are inaccurate or false position-based approaches. Kido et al present a false dummies-based approach where the user sends n-1 false dummies or locations along with his or her true location information. The server returns an answer set that contains the answer to the true location as well. The user then computes the exact required answer from the set. Hong et al present a landmark-based approach where the space is divided into Voronoi cells based on certain POIs. The user sends the location of his or her nearest landmark to the server to get an answer. In these approaches either the quality is service is low by getting approximate solutions or the server load is very high when the server responds for multiple locations for every single query.
Centralized Trusted Third Party Architecture (TTP)
In this architecture, there is a centralized trusted third party that is responsible for implementing privacy. The trusted party, also known as the location anonymizer, is between the users and the LBS provider. The users communicate their exact location to the trusted third party which then anonymizes and sends the query to the query server. The response is sent back to the location anonymizer which then forwards it to the corresponding user. It is usually assumed that the communication channels between the users and the anonymizer are secure while the communication channels between the anonymizer and the service provider can be public. Many approaches have been designed using this architecture based on cloaking, k-anonymity, and obfuscation (Gruteser et al, Gedik et al). However, as with any centralized system, this system has the disadvantage of having the location anonymizer as a single point of failure and also a potential bottleneck. Also, the system privacy is zero if the third party itself gets compromised.
Peer-To-Peer Architecture
Peer-to-peer (P2P) is a decentralized architecture and eliminates the need for a centralized trusted third party to meet privacy requirements. The mobile users communicate directly with each other using P2P communication technologies such as 802.11 and Bluetooth to work cooperatively with other users and form cloaked spatial regions. The querying user discovers peers either via single-hop or multi-hop communication to form a cloaked region that satisfies his or her k-anonymity or privacy area requirements. P2P architecture does not have the shortcomings of the centralized TTP-based architecture. However, it has other design and implementation challenges. Mokbel et al discuss the challenges and research issues in implementing P2P architecture for LBS. The challenges in peer searching include defining the hop distance to find k-1 peers and estimation of trustworthiness of peers. The challenges in forming a spatial cloaked region include movement uncertainty since the peers keep moving and the cloaked region needs to be adjusted accordingly. Finally, the limitations of the mobile environment including battery power and network disconnection are also present.
People’s Perception of Location Privacy
As discussed, the ability of any location-based service to collect location data raises privacy concerns for individuals. However, the question remains to what extent people care about location privacy. Although earlier studies seem to indicate that people are less concerned about privacy, more recent work indicates the opposite.
Researchers at the University of Cambridge conducted a (fictional) study with 74 undergraduate computer science students to collect their precise location information (via mobile phone) for one month. They found that the students set a median price of £10 to reveal their personal location tracks for research purposes. The median set price doubled if the data was going to be used for commercial purposes.
After conducting group interviews with 55 people from different backgrounds, researchers found that the people were not worried about their privacy using location-aware services. However, they noted that: "It did not occur to most of the interviewees that they could be located while using the service.”
Researcher John Krumm conducted a GPS survey with 219 people from Microsoft to provide recorded GPS data for two weeks for a 1 in 100 chance of winning a $200 MP3 player. 97 of them were asked if the data could be used outside Microsoft and only 20% denied this. It may be that the implications of sharing location data were not well understood by the participants.
A survey was conducted as part of the Data Privacy Day (held annually on January 28) to understand people’s concerns about location privacy and awareness about the use of location-based services. The survey reported that 52% of people expressed strong concern about sharing their location with other people or organizations. A clear majority of respondents expressed concern about sharing their location without consent (84%), having personal information or identity stolen (84%), and overall loss of privacy (83%).
Conclusion
The growing usage of location-based services requires us to invest in building an ecosystem of trust and transparency with users and service providers. Privacy does not have to be an afterthought after collecting all data, it needs to start at the system design and architecture level itself. The service providers need to be explicit in what data they are collecting and how long and how they will use the data. The users need more granular control of their data with consent that also emphasizes and educates about how the data will be collected and used.
Opinions expressed by DZone contributors are their own.

Comments